Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
ACSC, CISA, NSA Joint Advisory on Web Application Access Control Abuse
The Australian Cyber Security Centre, US Cybersecurity & Infrastructure Security Agency and the US National Security Agency have released a joint cybersecurity advisory to address the risks posed by insecure direct object reference (IDOR) vulnerabilities. The advisory is aimed primarily at designers, architects and developers of web applications.
IDOR vulnerabilities are often easy to spot, which makes them attractive to threat actors. When you see something like this in the URL bar of your browser:
https://www.bigcorp.com/account/statement?acctid=320345465423
then you are looking at a likely IDOR. The object in question is your account with BigCorp, and the direct reference is the account ID or number appearing as a URL argument. The question that should immediately pop into the mind of a security-aware observer is: if the acctid was set to a different number, would the page display someone else's account statement? If it would, then that is an insecure direct object reference.
Of course, insecure direct references need not appear in the URL - they could equally well be hidden or visible form fields
The fact is, there is no need for this direct reference at all. In most cases, you have but one account with BigCorp, and 'you' are identified by a session token generated when you logged in and passed between server and browser in the form of a secure cookie (if you didn't need to log in, then the IDOR is not your biggest problem!). Since the server knows who you are, it also knows your account number, and there is no need for the client to pass it back, whether in the HTTP header of a POST request or in the URL of a GET request.
If you do have multiple accounts - for example, with a bank where the customer has a mix of cheque, savings, credit card and other accounts - then they can be referenced indirectly, for example by an index into an array of account references maintained within the server-side code, or even better, via a mapping which uses a cryptographically strong random value.
In practice, the presence of IDOR vulnerabilities signals deeper problems within a web application such as missing function level access control or even broken authentication and session management. The latter is near-inexcusable; every web developer should be familiar with good authentication and session management techniques, but in practice even that is not strictly necessary since many projects are based on platforms (such as WordPress, Joomla, etc.) and frameworks that provide the required code.
In my courses, I teach that web development projects should start with the selection of a suitable access control model; for many web applications this will be role-based access control (RBAC). And again, many platforms provide the required functionality in the form of flexibly-defined permissions which can be associated with roles and then allocated to users. Attendees at our CISSP Fast Track Review course have access to a basic relational database schema for RBAC and PHP code which will perform an access check on every user request, only allowing the code to run if that user occupies a role with the required permissions.
The joint advisory delves into more detail for developers, with a useful list of suggested mitigations:
- Implement secure-by-design and -by-default principles and practice in development methodologies
- Follow secure coding practices
- Test code to identify vulnerabilities
- Coduct role-based training for developers
- Exercise due diligence when selecting third-party platforms, frameworks or libraries
- Establish a vulnerability disclosure program
End-user organizations are offered a similar list:
- Exercise due diligence when selecting web applications
- Apply software patches for these applications as soon as possible
- Configure web applications to log and generate alerts from tampering attempts
- Create, maintain and exercise a basic cyber incident response plan and related crisis communications plan
- Conduct regular, proactive penetration testing
- Use dynamic application security testing tools and vulnerability scanners
- Use a web application firewall to filter, monitor and block malicious traffic
- Use a data loss prevention tool
- Immediately report detected vulnerabilities to the vendor or developer
- Consider establishing a vulnerability disclosure program
For each of these points, the advisory provides additional explanatory detail.
CISA, Preventing Web Application Access Control Abuse, cybersecurity advisory, 27 July 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-208a.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Linux Variant of P2PInfect Uses Different Initial Access Vector
A couple of weeks ago we covered a new worm which was spreading between systems running the Redis NoSQL database. A Windows version of P2PInfect was discovered by Palo Alto's Unit 42, who established that it was exploiting CVE-22-0543, a Lua sandbox escape vulnerability with a CVSS 3 score of 10.0. P2PInfect got its name because it builds a peer-to-peer command and control network, and we pointed out that this "would make it much more difficult to sinkhole and bring down, especially if it can grow further". And, as expected, it is growing further.
Researchers at Cado Security Labs have discovered a Linux variant of P2PInfect, which uses a different vector for initial access.
An important feature of Redis is its support for replication, which allows nodes configured as followers to acts as replicas of a leader, with the goal of high availability and failover. P2P exploits this capability by connecting to an Internet-exposed Redis instance and issuing the SLAVEOF command to make it a replica of their malicious leader. The attacker can then use the MODULE LOAD command to load a malicious .so (shared object - the Linux equivalent to a DLL) file which creates a reverse shell, allowing remote command execution on the compromised host. From there, it connects its C2 server to retrieve and install the primary payload.
P2PInfect also attempts initial access via a cron unauthenticated RCE mechanism - but this is less successful than the SLAVEOF technique.
The main payload is a backdoor, written in a combination of C and Rust. It then sets about reconfiguring the system, installing an additional SSH public key to allow persistent access, renaming binaries so that their use will escape detection, and adding firewall rules to allow it to join the threat actor's botnet. The botnet itself is well designed, serving payloads via HTTP, and using TLS for command and control via signed messages, with certificates for both server and client ends of a connection. And although some of the payload filenames suggest cryptomining, there was no evidence of cryptomining activity, although this may be started at a later date.
The Cado Security Labs blog provides a full analysis of the worm code, as well as IOC's and a YARA rule for detection.
Bill, Nate and Matt Muir, Cado Security Labs Encounter Novel Malware, Redis P2Pinfect, blog post, 31 July 2023. Available online at https://www.cadosecurity.com/redis-p2pinfect/.
Yet Another WordPress Plugin Is Vulnerable
One massive benefit of using WordPress as a content management system is its rich ecosystem of plugins which make it an easy platform for customization. But along with these plugins comes the need to secure code from developers who, or may not, be fully up to speed on secure web coding techniques.
Specialist WordPress security firm Patchstack has disclosed multiple vulnerabilities in the Ninja Forms plugin:
CVE-2023-37979 - a POST-based reflected cross-site scripting (XSS) vuln that allows privilege escalation (CVSS 3 score: 7.1)
CVE-2023-38386 - a broken access control vuln in the form submissions export feature affecting Subscriber role
CVE-2023-38393 - a broken access control vuln in the form submissions export feature affecting Contributor role
For those who are interested, the Patchstack blog post provides an analysis of the vulnerable code, but users - and there are over 900,000 active installations - should update the Ninja Forms plugin to at least version 3.6.26.
Muhammad, Rafie, Multiple High Severity Vulnerabilities in Ninja Forms Plugin, blog post, 27 July 2023. Available online at https://patchstack.com/articles/multiple-high-severity-vulnerabilities-in-ninja-forms-plugin/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Novel Backdoor Exploits Barracuda Email Gateways
Security appliance vendor Barracuda has had a torrid few months, starting with their May disclosure than a particularly aggressive and skilled threat actor had targeted their Email Security Gateway appliance by exploiting CVE-2023-2868, a remote command execution 0-day vulnerability. The threat actor, tracked as UNC4841 and likely of Chinese origin, used this to install a reverse shell and then, in turn, deploy a persistent backdoor called SEASPY.
So potent and persistent was SEASPY that Barracuda took the unprecendented step of offering customers a replacement device (or a virtual appliance) as they could not be confident that a firmware update could completely eradicate the malware.
Now comes news of yet another backdoor for the Barracuda ESG appliance. SUBMARINE is a novel persistent backdoor which runs with root privileges and lives in an SQL database on the device. It consists of multiple artifacts - an SQL trigger, shell scripts and a loaded library for a Linux daemon - that together enable persistence, command and control and cleanup.
According to a malware analysis report, the US Cybersecurity & Infrastructure Security Agency obtained seven malware samples containing the backdoor, as well as "associated Multipurpose Internet Mail Extensions (MIME) attachment files from the victim. These files contained the contents of the compromised SQL database, which included sensitive information". CISA also warns that this malware "poses a severe threat for lateral movement".
CISA has released three malware analysis reports detailing the original reverse shell and SEASPY backdoor, as well as the SUBMARINE backdoor. The reports provide a detailed analysis of each exploit, based on multiple malware samples, with hash values for all files, behavioural IOC's, YARA rules and other detections. Affected customers are urged to use these to check for indications of exploitation and lateral movement to other systems. They should also discontinue use of any compromised appliance and contact Barracuda support to obtain a new appliance.
Barracuda, Barracuda Email Security Gateway Appliance (ESG) Vulnerability, legal notice, 28 July 2023. Available online at https://www.barracuda.com/company/legal/esg-vulnerability.
CISA, CISA Releases Malware Analysis Reports on Barracuda Backdoors, cybersecurity advisory, 28 July 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/07/28/cisa-releases-malware-analysis-reports-barracuda-backdoors.
Larsen, Austin, et. al., Barracuda ESG Zero-Day Vulnerability (CVE-2023-2868) Exploited Globally by Aggressive and Skilled Actor, Suspected Links to China, blog post, 15 June 2023 (updated 28 July 2023). Available online at https://www.mandiant.com/resources/blog/barracuda-esg-exploited-globally.
Google Analyzes 0-day Exploits
Google has published its fourth annual year-in-review analysis of 0-day vulnerabilities exploited in the wild, extracting the major trends and lessons. Key findings include:
- Long patching delays on Android mean 0-days continue to work long after initial disclosure
- Mitigations in browsers have driven threat actors to shift from 1-click to 0-click exploits
- Over 40% of 0-days were variants of previously-reported vulnerabilities
- Attackers are independently discovering and exploiting the same vulnerabilities
The last point provides some reason for optimism; when an exploit is discovered and a fix released, there's an increasing chance that it will mitigate not only the original exploit but also others.
However, the news for Android users is not so good. The problem is the length of the Android supply chain, between the original device manufacturers, through Google, to the mobile device manufacturers. A good example is CVE-2022-38181, a vulnerability in the ARM Mali GPU kernel driver, which was reported to the Android security team in July 2022. While the Android team labeled the issue "Won't Fix" because it was device-specific, they referred it to ARM, who released a new driver version in October. However, in November Google's Threat Analysis Group discovered an exploit in the wold - yet it was not until April 2023 that a fix was incorporated in Android itself - that is, 9 months after the initial report.
There are similar delays affecting Android implementations from mobile device vendors - for example, in December 2022, the Threat Analysis Group discovered an exploit targeting the latest version of the Samsung Internet browser, which at that time was running on Chromium 102, released 7 months earlier in May 2022. This delay meant that the attackers could use CVE-2022-3038, which had been fixed in Chrome 105 of June 2022. The attack chain also used CVE-2022-22706, another ARM Mali GPU kernel driver vulnerability which had been fixed by ARM in January 2022 but did not appear in the Android Security Bulletin until June 2023 - 17 months after the patch was released and it was publicly known to be actively exploited in the wild.
This paints a rather depressing picture; threat actors don't need to research vulnerabilities themselves in order to produce 0-day exploits - instead, they can simply watch for them to be disclosed publicly, then use the information to work up n-day exploits which will produce results for months to come.
Stone, Maddie, The Ups and Downs of 0-days: A Year in Review of 0-days Exploited In-the-Wild in 2022 , blog post, 27 July 2023. Available online at https://security.googleblog.com/2023/07/the-ups-and-downs-of-0-days-year-in.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
CISA Releases Analysis of Critical Infrastructure Sectors
The US Cybersecurity & Infrastructure Security Agency has released an analysis and infographic summarising 121 risk and vulnerability assessments (RVA's) conducted across multiple critical infrastructure sectors in fiscal year 2022 (FY22).
The analysis provides a sample attack path, based loosely on 11 of the MITRE ATT&CK framework's 14 tactics, which threat actors could leverage to compromise an organization using weaknesses identified in the RVA's. It discusses the possible techniques used to achieve each tactic, from Initial Access through Execution, Persistence, Privilege Escalation, Defense Evasion and others to Lateral Movement, Collection, Command and Control and, finally, Exfiltration.
The infographic highlights the most successful techniques for each tactic that the RVA's documented, displayed as a pie chart with the size of each slice proportional to that technique's success rate.
While the RVA's, and consequently the analysis and infographic, are specific to critical infrastructure, they nonetheless provide useful awareness information for enterprises more generally.
CISA, CISA Releases Analysis of FY22 Risk and Vulnerability Assessments, cybersecurity advisory, 26 July 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/07/26/cisa-releases-analysis-fy22-risk-and-vulnerability-assessments.
CISA Vulnerability Summary
Speaking of CISA, the agency has released its summary of new vulnerabilities recorded in the NIST National Vulnerability Database (NVD) for the week of 17 July.
CISA, Vulnerability Summary for the Week of July 17, 2023, bulletin, 24 July 2023. Available online at https://www.cisa.gov/news-events/bulletins/sb23-205.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Australian Government Cheaps Out on Identity Management, Loses Half a Billion
For many years now, the Australian Government has been prone to placing faith in technology without really understanding it. We have seen this with debacles like the near-useless COVIDSafe contact-tracing app, which cost over $A20 million in total, and identified two (2) COVID-positive cases. We saw it with the Robodebt disaster, which was not only illegal but caused misery and even deaths. We saw it in the cancellation of the Australian Apprenticeship Management System.
To this viewer outside the Canberra bubble, it has seemed as though politicians, especially Ministers, had been captured by consultants with a surfeit of political connections over technical ability. In particular, previous governments have been resistant to sound principles of identity management, such as the development of a cryptographically-based or biometric personal identity for use by citizens transacting government business. Instead, they have relied on awkward schemes based on passwords, out-of-band verification using the PSTN (mTAN's) - in other words, six-digit numbers sent as a text message - and knowledge of identifiers such as the tax file number. These schemes are weak, deprecated (see NIST SP 80063B S5.1.3.3) or just plain silly.
By contrast, many European countries have implemented electronic identity cards which carry not only biometric data but also store a private key and certificate which can be used for authentication as well as to sign and verify documents and transactions. Why did the nation which wanted to become "one of the top three digital governments in the world ... that other nations can look to for guidance and inspiration" fall so far behind? (That was a rhetorical question.)
The IAM pigeon has come home to roost rather spectacularly with reports that more than half a billion dollars has been fraudulently claimed from the Australian Taxation Office (ATO), by criminals exploiting glaring loopholes in the linkage between the hokey MyGov system and taxpayer ATO accounts.
The fraud begins with a criminal creating a fake MyGov account, and then linking the new account to a genuine taxpayer's ATO account using easily-acquired identity information such as their tax file number (TFN) or date of birth. Some of this information is available cheaply on the dark web, obtained from previous data breaches or can be obtained by social engineering. The phone number in the ATO account is then changed so that mTAN's are sent to the fraudster, not the taxpayer, and the bank and email addresses are similarly changed. The fraudster then submits fake Business Activity Statements (BAS) and tax refund claims - which are paid to the changed bank account.
In the 2021/22 financial year, more than 7,500 accounts were compromised with over $A237 million paid, while in the 2022/23 financial year, the scam netted $A320 million from 8,100 compromised taxpayer accounts. That's a total of $A557 million.
It's past time for the ATO to pension off its hokey approaches to identity and access management and start doing things properly. And it's well past time for our politicians to look outside the Canberra bubble and find some competent consultants to advise them.
Charette, Robert N., Australia’s Digital Transformation Stumbles Badly: A new report finds a “litany of failures” in Australia’s attempt to digitize government services, IEEE Spectrum, 6 July 2018. Available online at https://spectrum.ieee.org/australias-digital-transformation-stumbles-badly.
Curnow, Sarah and Dan Oakes, ATO reveals more than $557 million claimed by fraudsters exploiting security loophole, ABC News, 26 February 2023. Available online at https://www.abc.net.au/news/2023-07-26/ato-reveals-cost-of-mygov-tax-identity-crime-fraud/102632572.
US SEC Tightens Cyber Governance, Risk Management and Incident Disclosure Requirements
The US Securities and Exchange Commission has adopted new rules requiring public companies to disclose material cybersecurity incidents and to annually provide information on their cybersecurity risk management, strategy and governance. In particular, reports of material incidents must now be made within four days, and will require a description of the material aspects of the incident's nature, scope and timing as well as its likely or actual impact on the company. The rules will require comparable disclosures by foreign share issuers.
An incident disclosure will be made in a new Item of Form 8-K and will require the following information:
- When the incident was discovered and whether it is ongoing;
- A brief description of the nature and scope of the incident;
- Whether any data were stolen, altered, accessed, or used for any other unauthorized purpose;
- The effect of the incident on the registrant’s operations; and
- Whether the registrant has remediated or is currently remediating the incident.
Annual reports will now require more consistent and informative disclosure of firms' approach to risk management, including a description of policies and procedures for the identification and management of cyber threats. Firms will also have to describe how the board and management oversee cyber risk:
- Whether the entire board, specific board members, or a board committee is responsible for the oversight of cybersecurity risks;
- The processes by which the board is informed about cybersecurity risks, and the frequency of its discussions on this topic; and
- Whether and how the board or board committee considers cybersecurity risks as part of its business strategy, risk management, and financial oversight.
Companies will also have to disclose whther they have a CISO and where the CISO reports, whether other management positions or committees are responsible for measuring and managing cyber risk and the processes by which they do so.
Annual reports will also require additional details of the cybersecurity expertise, if any, of board members, including prior work experience and certifications, as an aid to investors in making both investment and voting decisions. However, the Commission has also proposed a safe harbor providing that any directors identified as cybersecurity experts would not be deemed experts for liability purposes but also clarifying that the duties, obligations and liabilities of non-expert directors are not decreased, either.
Although these new rules only apply to companies traded on US exchanges, we can expect this approach to spread more widely, with other countries likely adopting similar requirements and liabilities of board members of private companies being similarly tightened. For CISO's, it means more formalisation of both risk management and incident response programs and a lot more communication with boards.
Securities and Exchange Commission, SEC Adopts Rules on Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure by Public Companies, press release, 26 July 2023. Available online at https://www.sec.gov/news/press-release/2023-139.
Securities and Exchange Commission, 17 CFR Parts 229, 232, 239, 240, and 249: Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure, final rule, 26 July 2023. Available online at https://www.sec.gov/rules/final/2023/33-11216.pdf.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
What Identity Theft Can Look Like
A cautionary tale for privacy professionals; we tend to lose sight of the impact of a privacy breach on the individual in favour of the size of ransom demands and the sheer number of records exfiltrated. Australian Broadcasting Corporation (ABC) News brings us the story of a woman who was caught up in last year's Medibank data breach and initially shrugged it off. When she received an email referring to the sale of counterfeit Adidas products under her name, she assumed it was simply a related scam attempt and ignored it.
But things got very real when she was electronically served with papers from the US District Court for Florida outlining the Adidas case against her, followed by similar charges files by the National Basketball Association in the District Court for Illinois. Adidas and the NBA were given leave to run ex parte cases - that is, without the defendant being present - resulting in default judgements against her for $US1 million and $US200,000 respectively.
Sarah Luke, a single mother of four from Byron Bay in northern NSW, is now struggling to come to grips with her situation. In early December, her PayPal account was taken over in a credential stuffing attack and used to make hundreds of fraudulent transactions. However, Medibank states that none of its customers' passwords were compromised in its breach and it is therefore not liable for what happened to Ms. Luke. She has been forced to engage a US intellectual property lawyer on a retainer of $US10,000 and worries that if the judgements cannot be overturned she may lose her house and savings.
The complexities of this case have defeated the various agencies she has turned to. Unpicking the exact mechanism by which the PayPal account breach was accomplished, and whether either PayPal or Medibank is to any extent liable, will require a detailed forensic investigation, liikely without much cooperation from either company. Similarly, it may prove difficult for her to demonstrate that she had no involvement with the counterfeit Adidas sales.
The implications for consumers are clear - do everything you can to safeguard key accounts such as PayPal, eBay, bank accounts, email accounts and the like: unique, moderately complex, passwords for each account, stored in a password safe if necessary, coupled with a second authentication factor, preferably a security key or a time-based one-time token app like Authy, Google Authenticator or similar.
Ross, Hannah, Byron Bay breach victim told to pay Adidas, National Basketball Association $US1.2m by US courts, ABC News, 25 July 2023. Available online at https://www.abc.net.au/news/2023-07-25/byron-bay-data-breach-victim-adidas-nab-us-court-action-damages/102575726.
Australian Department of Home Affairs Exposes Data of Survey Respondents
In a story that combines elements of hubris, mea culpa and schadenfreude, the personal information of over 50 respondents to a small business survey on cybersecurity has been exposed by the Department of Home Affairs.
The names, business names, phone numbers and emails of the survey respondents were published on the Parliament web site in response to a question on notice posed by the shadow cyber security and home affairs, James Paterson, during May's budget estimates hearing. Among the responses to the question was a research report from 89 Degrees East which contained the unredacted names, business names, phone numbers and emails of respondents who indicated they wanted to learn more about the 'cyber wardens' program offered following last year's Optus and Medibank breaches.
However, this may be a case of the pot calling the kettle, etc., as last year a web site belonging to James Paterson had to be hastily taken down after it was found to be overrun by bots inserting thousands of ads for dubious or illegal products.
It can happen to the best of us, James.
Taylor, Josh, Home affairs cyber survey exposed personal data of participating firms, The Guardian, 25 July 2023. Available online at https://www.theguardian.com/technology/2023/jul/24/home-affairs-cyber-survey-exposed-personal-data-of-participating-firms.
Robertson, James and Matthew Elmas, James Paterson’s cyber hard line undermined as website is overrun by bots, The New Daily, 2 November 2022. Available online at https://thenewdaily.com.au/news/politics/2022/11/02/james-paterson-cyber-security-embarrassment/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
OpenSSH ssh-agent RCE Vulnerability
A tricky vulnerability for systems administrators to contemplate: a newly-discovered vulnerability in the ssh-agent component of OpenSSH can allow an attacker who has access to a remote server to then execute code on the administrator's workstation. The vulnerability, CVE-2023-38408, was discovered by Qualys researchers while 'browsing through ssh-agent's source code'.
OpenSSH is widely used for command-line administration of remote hosts; the ssh-agent is particularly useful, as it caches the admins' private keys, eliminating the need for constant retyping of passwords, especially when remote commands are invoked from within scripts (remember, scripting and automation is the holy grail for admins).
And in complex environments, especially cloud, it can be useful to enable agent forwarding; this allows an admin - say, Alice - to log into a remote host (Bob) and then connect from it to yet another host behind Bob (Carol) without having to load a private key on Bob. Instead, the authentication challenge from Carol to Bob is automatically forwarded to Alice, for the ssh-agent to handle. This eliminates the need for private keys to live on Internet-facing hosts, and also eliminates the need for yet more password typing. The result is the ability for scripts on Alice to invoke scripts on Bob which can, in turn, invoke commands on Carol, Dave, etc. Bliss! I have used this in the past to achieve automated remote backups through an intermediate firewall, for example.
However, the Qualys researchers' interest was piqued by a comment in the ssh man page:
Agent forwarding should be enabled with caution. Users with the ability to bypass file permissions on the remote host ... can access the local agent through the forwarded connection. ... A safer alternative may be to use a jump host (see -J).
Based on their reading of the ssh-agent source code, they found that a remote attacker, who has access to the remote server to which Alice's ssh-agent is forwarded, can load (via dlopen()) and unload (via dlclose()) any shared library in /usr/lib* on the Alice workstation, via the forwarded ssh-agent (if it is compiled with ENABLE_PKCS11, which is the default).
From there, they were able to develop a proof-of-concept which achieves remote code execution by exploiting the side-effects of loading and unloading the shared libraries of some standard Linux distribution packages - and while they started with only one approach in mind, they came up with six other cominations of shared libraries that may well work. This work was done using Ubuntu Desktop 22.04 and 21.10, but other distributions and OS's are quite probably vulnerable.
The Qualys blog post provides basic information, but their full security advisory digs deeper and makes a fascinating read for Linux sysadmins and developers. The researchers submitted their findings, along with an initial patch, to the OpenSSH project, who refined the patch and released a fix on 19 July. This should be rolling out to the various Linux distributions in the coming days.
Abbasi, Saeed, CVE-2023-38408: Remote Code Execution in OpenSSH’s forwarded ssh-agent, blog post, 19-24 July 2023. Available online at https://blog.qualys.com/vulnerabilities-threat-research/2023/07/19/cve-2023-38408-remote-code-execution-in-opensshs-forwarded-ssh-agent.
Uncredited, CVE-2023-38408: Remote Code Execution in OpenSSH's forwarded ssh-agent, security advisory, 19 July 2023. Available online at https://www.qualys.com/2023/07/19/cve-2023-38408/rce-openssh-forwarded-ssh-agent.txt.
Detailed Rundown on Cl0p
A longish blog post from Fortiguard Labs Threat Research provides a comprehensive high-level analysis of the operations of the Cl0p ransomware gang. Cl0p is significant as it is the most successful of the current ransomware gangs, in part due to its focus on large enterprises which could pay large extortion demands - resulting in a median ransom payment of close to $US2 million.
According to the Fortiguard researchers, Cl0p has been more active this year than in 2021/22, in part due to the arrest of some members in June 2021 perhaps causing a hiatus. As of 15 July, the Cl0p ransomware data leak site lists 419 victims, primarily in the US. The group also appears to have shifted from holding encrypted files ransom to exfiltrating data which they threaten to make public if an extortion demand is not met. In the case of their recent exploitation of the MOVEit Transfer SQL injection vulnerability, the Cl0p ransomware was not deployed at all - this was purely an information exfiltration attack.
However, the group claims "We have never attacked hospitals, orphanages, nursing gomes, charitable foundations, and we will not . . . If an attack mistakenly occurs on one of the foregoing organizations, we will provide the decryptor for free, apologise and help fix the vulnerabilities". Their goodwill does not extend to pharmaceutical firms, though.
Imano, Shunichi and James Slaughter, Ransomware Roundup - Cl0p, blog post, 21 July 2023. Available online at https://www.fortinet.com/blog/threat-research/ransomware-roundup-cl0p.
Apple Threatens to Pull FaceTime, iMessage from UK
As the UK government seeks to update the Investigatory Powers Act (IPA) 2016, Apple has fought back, threatening to withdraw services such as FaceTime and iMessage from the UK rather than weaken their security.
The IPA allows the Home Office to demand that security features, such as end-to-end encryption and authentication, are disabled without any notification to the public, in order to permit surveillance by police and intelligence agencies. This has long been a goal of governments - the UK, in particular, targeted Facebook for its decision to enable encryption in Facebook Messenger, relying heavily on the argument that improved encryption would hamper efforts to tackle child exploitation online (the same argument used by the US government against PGP in the 1980's).
The fact is that this legislation is only going to weaken the security of legitimate users while not achieving the intended goal - the cryptologic cat is well and truly out of the bag, with many third-party secure messaging services available. For this and other reasons, proposals by governments to weaken device security have long been opposed by the academic and industrial cryptologic community (Abelson et. al., 2015).
The most recent UK government is also opposed by WhatsApp and Signal, and comes as Google - and undoubtedly others- move to adopt the IETF's Message Layer Security Protocol (RFC 9420), which will provide end-to-end encryption across multiple platforms (Hogben, 2023). Google will implement MLS into Google Messages (its Android SMS app) and open-source its implementation in the Android codebase.
Abelson, Harold, Ross Anderson, Steven M. Bellovin, Josh Benaloh, Matt Blaze, Whitfield Diffie, John Gilmore, et al., Keys Under Doormats: Mandating Insecurity by Requiring Government Access to All Data and Communications. Technical Report, CSAIL Technical Reports, Cambridge, MA: MIT, July 6, 2015. Available online at http://dspace.mit.edu/handle/1721.1/97690.
Hogben, Giles, An important step towards secure and interoperable messaging, Google Security blog, 19 July 2023. Available online at https://security.googleblog.com/2023/07/an-important-step-towards-secure-and.html.
Kleinman, Zoe, Apple slams UK surveillance-bill proposals, BBC News, 21 July 2023. Available online at https://www.bbc.com/news/technology-66256081.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Stolen Microsoft Key - It Could Have Been a Lot Worse
A couple of weeks ago, we brought you news of an attack on Microsoft 365 which affected several US government agencies, and which was believed to be the work of a Chinese APT identified as Storm-0558. The attack was accomplished by forging authentication tokens for Outlook Web Access in Exchange Online and Outlook.com using an acquired Microsoft Managed Service Account (MSA) consumer signing key.
Now, an analysis by Wiz security researcher Shit Tamari indicates that the impact could have been a lot worse. According to the Wiz team, the compromised MSA key could have allowed the threat actor to 'forge access tokens for multiple types of Azure Active Directory applications, including every application that supports personal account authentication, such as SharePoint, Teams, OneDrive, customers’ applications that support the “login with Microsoft” functionality, and multi-tenant applications in certain conditions'.
The breach highlights the importance of identity providers' signing keys in making hard trust decisions. This has long been (sort-of) recognised in the world of TLS certificates - compromising a web site's private key could allow an attacker to masquerade as that site, while compromising the certificate authority's signing private key would allow masquerading as any site using a certificate issued by that CA. But the same concern applies to federated identity management systems which authenticate users via protocols, such as OAuth 2.0 and OpenID, and then trust those users.
The Wiz blog post details how the researchers identified the compromised Microsoft key and then found that it was also able to sign OpenID V 2.0 tokens for multiple types of Azure Active Directory applications.
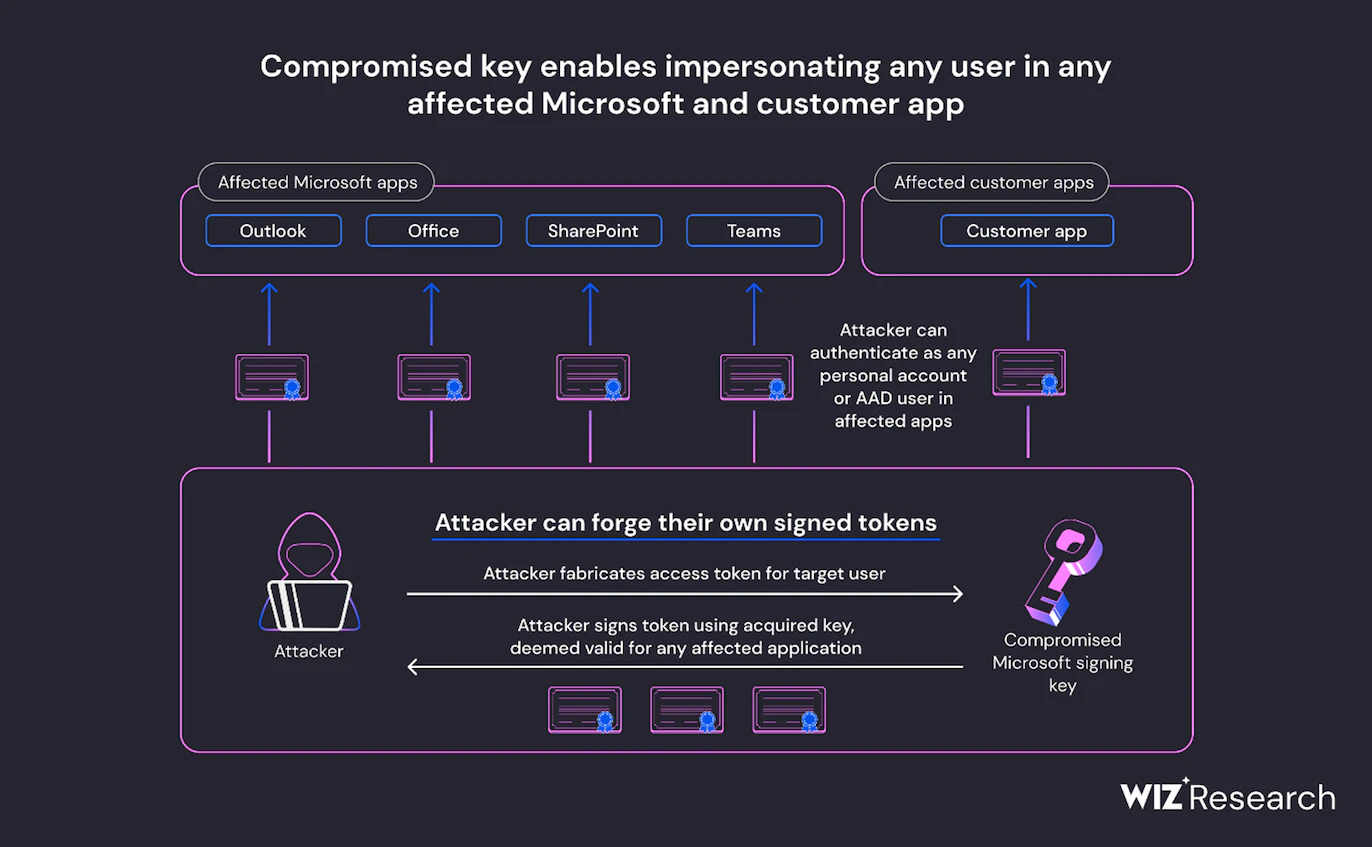
The capabilities of a compromised OpenID signing key (image credit: Wiz Research)
The Wiz blog post clearly outlines the affected applications and provides recommendations for Azure users, including how to detect the compromised key in customer environments.
Tamari, Shir, Compromised Microsoft Key: More Impactful Than We Thought, blog post, 22 July 2023. Available online at https://www.wiz.io/blog/storm-0558-compromised-microsoft-key-enables-authentication-of-countless-micr.
Get Ready for CVSS Version 4.0
Readers are doubtless familiar with the Common Vulnerability Scoring System (CVSS) which allocated a score to vulnerabilities, based on a number of factors, such as whether the attacker needs physical access to the target machine or can run an exploit across the LAN or from the Internet, the attack complexity, and whether the vulnerability will allow the attacker to then pivot to attack other targets. The CVSS score is a key factor in deciding the urgency with which a vulnerability must be patched, along with other factors such as the impact on the specific information asset and the presence of compensating controls such as multiple levels of network segmentation, web application firewalls or an endpoint detection and response product.
Now, FIRST (the Forum of Incident Response and Security Teams) has released the first preview of CVSS 4.0, which is intended to offer finer granularity in base metrics, remove downstream scoring ambiguity, simplify threat metrics and enhance the effectiveness of assessing environment-specific security requirements and compensating controls.
CVSS 4.0 eliminates the somewhat confusing "temporal" metrics of 3.1, instead incorporating a "threat" metric group and also adding two new base metrics: Attack Requirements (AT) and User Interaction (UI) - which can be either Passive (P) or Active (A).
Another important enhancement is new nomenclature to distinguish between the base score and the additional scores:
- CVSS-B: CVSS Base Score
- CVSS-BT: CVSS Base + Threat Score
- CVSS-BE: CVSS Base + Environmental Score
- CVSS-BTE: CVSS Base + Threat + Environmental Score
For some users, the most important change will be the addition of Safety metrics and values to the Supplemental and Environmental metric groups, making CVSS 4.0 more directly applicable to Operational Technology, Industrial Control Systems and IoT environments.
A summary of the changes, along with a highly informative presentation from FIRSTCon23, can be found at https://www.first.org/cvss/v4-0/index.html.
McNulty, Paula, New Common Vulnerability Scoring System (CVSS) set to be cyber sector game-changer, news release, 13 July 2023. Available online at https://www.first.org/newsroom/releases/20230713.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
(ISC)2 Board Election Controversy Continues
ISC)2 has announced that its open call for nominations to stand for the Board of Directors has closed - I confess, I did not even know it was open. This year, the current Board has recommended a slate of seven candidates for four open seats on the Board. However, three of the recommended seven are current Members, and many current certification holders do not feel that this is sufficient choice.
Accordingly, three experienced people are attempting to get onto the ballot via petition. They are:
- Stephen Mencik (US) - a 40-year security professional with both government and private sector experience
- Sami Koskinen (Finland) - over 20 years experience as a CISO, CIO and consultant
- Diana Contesti (Canada) - a past Chair of the Board and winner of the James R. Wade Award for service to (ISC)2
I have 'known' them all - in an online sense - since I became a CISSP back in 2002, as they have all been regular contributors to the CISSP Forum, and commend them for your consideration. If you are a member in good standing, then please support their petition by going to https://jsweb.net/isc2/election.html and providing your name, email address and (ISC)2 candidate number.
RIP Kevin Mitnick
Black hat? White hat? Whatever your opinion of Kevin Mitnick, it is now moot, as the great leveller has claimed him in the end.
Uncredited, Kevin David Mitnick, obituary, 19 July 2023. Available online at https://www.dignitymemorial.com/obituaries/las-vegas-nv/kevin-mitnick-11371668.
Worm Infects Linux, Windows Servers Via Redis Lua Vulnerability
Back in early December last year, we brought you news of a backdoor which was able to infect systems running a vulnerable version of the Redis NoSQL database. Redis is widely deployed on web servers, particularly for page caching, although it has many other applications where a high-performance non-relational database is required. The backdoor was installed by exploiting CVE-2022-0543, a very nasty - CVSS score 10.0, and it doesn't get any worse than that - vulnerability in the library for the Lua scripting language which allows an attacker to escape the Lua sandbox, permitting remote code execution.
Now Palo Alto Unit 42 researchers have identified a worm which is using the same vulnerability to infect both Linux and Windows servers. The worm, dubbed P2PInfect, is written in Rust (the backdoor mentioned above was written in Go), and although this vulnerability was disclosed over a year ago, the researchers have identified almost one thousand servers which still remain vulnerable.
P2PInfect exploits CVE-2022-0543 for intial access, and then drops a payload which establishes an initial connection to a peer-to-peer command and control network. Once it has done this, it then downloads additional binaries, including scripts specific to the victim OS as well as scanning software; after this has been done, the infected victim then fully joins the P2P network in order to share these scripts and binaries with future compromised victims.
Building a C2 network this way would make it much more difficult to sinkhole and bring down, especially if it can grow further. There is no attribution for this worm; nor is it clear what its purpose is - although the word "miner" appears several times in its binaries, there is no evidence of any cryptomining code. However, its C2 protocol appears to allow its operators to push new payloads into the network which could add new capabilities.
The obvious mitigation is to update vulnerable Redis installations - but given that this vulmerability is over a year old, it seems likely that the administrators of vulnerable systems are not getting the message.
Gamazo, William and Nathaniel Quist, P2PInfect: The Rusty Peer-to-Peer Self-Replicating Worm, blog post, 19 July 2023. Available online at https://unit42.paloaltonetworks.com/peer-to-peer-worm-p2pinfect/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cyber Insurance and Ransomware
The cyber insurance landscape is changing rapidly, partly in response to changes in the ransomware market. Premiums are rising in response to rising claims, making insurance a much more expensive way to share cyber risk. And as we reported last week, the most sophisticated ransomware operators are now engaging in 'big game hunting' - targeting larger corporations with deeper pockets, and demanding a larger ransom to make up for increasing number who simply refuse to pay.
Another complicating factor was last year's decision by Lloyds of London to ask its cyber insurance clients to amend their policies, starting from March 2023, to exclude coverage for attacks sponsored by government entities. This followed a 2021 New Jersey Superior Court Ruling which found in favour of pharma giant Merck after ther insurer refused coverage for the NotPetya attack, claiming it was an act of war (a standard exclusion in most policies). The court found that while cyber-attacks can be acts of war, Ace American had not
updated the exclusion clause to reflect this, and that Merck therefore
had every right to anticipate that the exclusion policy applied only to
traditional forms of warfare. The Lloyds decision makes this quite explicit - and with increasing activity from state-sponsored and state-affiliated threat actors, some victims may be in for a rude shock when they claim on their policies.
There is also some research to suggest that cyber insurance introduces a moral hazard effect on ransomware, as insurance companies often recommend paying the ransom, rather than having to pay higher costs of complex recoveries. This frustrates any attempt to disrupt the ransomware operators' business model - in fact, their massive revenues are funding the development of even more sophisticated malware - and also drives premiums higher.
A 2022 Forrester report estimated that a typical data breach would lead to $US2.4 million in incident response costs (with detection, analysis and eradication requiring a median of 27 days, and a further 10 days for recovery). However, a survey of 450 security professionals in North America, by BlackBerry and insurer Corvus, revealed that only 55% have cyber insurance, and less than 20% have coverage in excess of $600,000, which was the median ransomware demand in 2021 - now consider that the median ransomware payment obtained by Cl0p - the most successful ransomware operator - was almost $US2 million.
The BlackBerry/Corvus study found that only 10% of all businesses surveyed have ransomware coverage limits above the 2021 median ransomware demand amount (of $600,000), while only 14% of SMB's with fewer than 1,500 employees had a higher limit.
Looking at these figures, we can only suggest that it would be smart to invest into defensive controls - principally application safelisting, but also MFA, EDR and SETA - to avoid falling victim to a ransomware attack, rather than sinking the money into cyber insurance premiums, which are bound to rise even further in the coming months.
Specops Software, Strengthening Password Security may Lower Cyber Insurance Premiums, Bleeping Computer (sponsored content), 18 July 2023. Available online at https://www.bleepingcomputer.com/news/security/strengthening-password-security-may-lower-cyber-insurance-premiums/.
Adobe ColdFusion Vuln Exploits in the Wild
Yesterday, we covered security updates from several firms, including Adobe, which had released updated for several versions of ColdFusion. Only a day later comes a new security bulletin featuring three new vulnerabilities:
- CVE-2023-38204, an insecure deserialization vulnerability with a CVSS score of 9.8
- CVE-2023-38205, an access control vulnerability which can lead to remote code execution (CVSS score: 7.5)
- CVE-2023-38206, a second access control vulnerability (CVSS score: 5.3)
The result is yet another update for the vulnerable versions of ColdFusion. Adobe's security bulletin reveals that the firm is aware of limited attacks in the wild, attempting to exploit CVE-2023-38205; fortunately, the more serious CVE-2023-38204 is so far not in play. If you were holding back on this update, don't! And if you updated yesterday, it's time to do it all over again.😠
Adobe, Security updates available for Adobe ColdFusion, security bulletin APSB23-47, 14 July 2023. Available online at https://helpx.adobe.com/security/products/coldfusion/apsb23-47.html.
Wicked Panda Spies on Android
A report from cloud security vendor Lookout attributes two long-standing pieces of surveillance malware, called WyrmSpy and DragonEgg, to the Chinese state-sponsored APT Wicked Panda, also known as APT41, Wicked Spider, Double Dragon, BASIUM and Winnti. The firm has been tracking the spyware since 2020, with the latest example found in April 2023.
Wicked Panda has been active since 2012 and engages in a surprisingly wide range of activities. It is known to target both governments and tech companies, engaging in cyber-espionage on behalf of the Chinese Communist Party, using malware unique to the Chinese government. However, it also engages in cybercrime for profit, attacking online gaming sites in particular, and essentially funding itself. This raises an interesting question - how would an insurance company respond to a claim for an attack by this group?
The FBI has placed five members of Wicked Panda on its 'most wanted' list, following indictments for a range of charges, including unauthorized access to protected computers, aggravated identity theft, racketeering, fraud, money laundering, wire fraud and access device fraud.
While Wicked Panda has historically target Internet-facing web sites, the fact that they are exploiting end-user mobile devices indicates the value of the data that they can disclose.
Balaam, Kristina and Justin Albrecht, Lookout Attributes Advanced Android Surveillanceware to Chinese Espionage Group APT41, blog post, 19 July 2023. Available online at https://www.lookout.com/threat-intelligence/article/wyrmspy-dragonegg-surveillanceware-apt41.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.