Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
New Phone? No More Google Authenticator Blues. . .
For those of us who use Google Authenticator, getting a new phone has heralded a tedious task, not to mention occasional pain. You see, Google Authenticator, a software time-based one-time password token generator which generates a new authentication code every minute, stored its seed values on the phone - hopefully in the secure element - which meant that a new phone meant re-seeding the various tokens in the Authenticator app.
For some accounts, this simply meant using the camera phone to scan a QR code off a PC screen, in order to replace the current token with a new one and store the seed values in the new phone. But for some accounts, it meant getting administrators to revoke the current one-time codes so that we can enrol the new phone - a tedious process that could take some time.
Fortunately, Google has now updated the Authenticator app to store the token data in the user's Google account, allowing accounts to be transferred between phones with relative ease. In fact, version 6.0 and later for both Android and iOS will synchronize Authenticator codes across multiple devices and will automatically restore them to any new device you use.
Of course, this has implications for lost and stolen devices, especially if the device is not locked using some secure mechanism. And if the Google account itself can be compromised . . . But then, an attacker would need the Authenticator codes to do that, wouldn't they?
Brand, Christian, Google Authenticator now supports Google Account synchronization, blog post, 24 April 2023. Available online at https://security.googleblog.com/2023/04/google-authenticator-now-supports.html.
Google Rolls Out Generative AI for Security
Sticking with other Google news, the firm has announced a number of related new capabilities which bring AI to the field of infosec. The key one seems to be Google Cloud Security AI Workbench, a do-everything 'platform' which is based on a specialized large language model for security called Sec-PaLM.

(Image credit: Google)
Sec-PaLM seems to take feeds from a number of sources: the MITRE frameworks, obviously, as well as OSSVDB, VirusTotal and threat intelligence from Mandiant, which is now owned by Google. The product will also draw on selected data from Google partners; the first of these will be Accenture, who will integrate Security AI Workbench with their Managed Extended Detection and Response service.
In addition, Sec-PaLM is also being added into two other products. Firstly, VirusTotal will use it to power a new automated malware analysis feature called Code Insight, which can analyze files to improve the detection of actual threats, reducing false positives. The code is already analyzing PowerShell scripts uploaded to VirusTotal. Secondly, Mandiant is integrating Sec-PaLM into the Chronicle SIEM/SOAR suite, in the form of Mandiant Breach Analytics for Chronicle.
This is a large product announcement with lots of implications. We can expect to see further integration of AI into incident response tools, improving the signal/noise ratio for human analysts and perhaps helping to close the skills gap.
Potti, Sunil, Supercharge security with generative AI, blog post, 25 April 2023. Available online at https://cloud.google.com/blog/products/identity-security/rsa-google-cloud-security-ai-workbench-generative-ai.
Open-Source Large Language Model Launched
And while we're on the subject of AI, Stability.ai has launched the first of its open-source StableLM language models; the alpha version of the model is available in 3 billion and 7 billion parameter versions, with 15 billion to 65 billion parameter versions to follow.
Developers can freely inspect, use and adapt the base models for commercial or research purposes, under the terms of the Creative Commons BY-SA-4.0 license. The models are now available in the firm's GitHub repository.
Uncredited, Stability AI Launches the First of its StableLM Suite of Language Models, blog post, 19 April 2023. Available online at https://stability.ai/blog/stability-ai-launches-the-first-of-its-stablelm-suite-of-language-models.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
NSO's Pegasus - Still a Thing
Just over a week ago, we brought you news of Citizen Lab's discovery of new amrtphone implants produced by Israeli spyware firm QuaDream. This kind of implant is commonly used by governments to spy on journalists and civil rights activists - a market that was pioneered by another Israeli company, NSO Group. We hadn't heard from NSO Group in some time, suspecting that intense publicity had caused them to put the brakes on their activities.
Not so, it seems, according to a new report from Citizen Lab, who have discovered three new zero-click exploit chains against Apple iOS 15 and 16 which seem to have been developed by NSO Group during 2022. The Toronto researchers' investigation started with the discovery of infections on the phones of human rights defenders from Centro PRODH, which represents victims of military abuses in Mexico.
This led to the uncovering of PWNYOURHOME, which was deployed against iOS 15 and 6 starting in October 2022, and appears to be a novel two-step zero-click exploit - the first step targets HomeKit and the second target iMessage. Working backwards, FINDMYPWN was deployed against iOS 15 from June 2022, and is also a two-step exploit - stage one targets the iPhone's "Find My" feature, while stage two targets iMessage. Using information shared by Citizen Lab, Apple released fixes for HomeKit in iOS 16.3.1.
Having identified FINDMYPWN and PWNYOURHOME, the Citizen Lab researchers discovered traces of NSO Group's first 2022 zero-click, LATENTIMAGE, which may also have exploited the iPhone "Find My" feature.
The Citizen Lab report provides a full run-down on the technical aspects of these exploits, as well as the socio-political targeting, and suggested mitigation using Apple's Lockdown Mode.
Marczak, Bill, John Scott-Railton, Bahr Abdul Razzak and Ron Deibert, Triple Threat: NSO Group’s Pegasus Spyware Returns in 2022 with a Trio of iOS 15 and iOS 16 Zero-Click Exploit Chains, technical report, 18 April 2023. Available online at https://citizenlab.ca/2023/04/nso-groups-pegasus-spyware-returns-in-2022/.
GhostToken Vulnerability Hides Malicious Google Cloud Applications
A recently-patched vulnerability in Google Cloud Platform potentially exposed millions of Google accounts to access via an invisible, undeletable OAuth2 access token. The vulnerability, called GhostToken by the Astrix Security researchers who discovered it, was notified to Google on 19 June 2022. So deep in Google's processes was the vulnerability located that it took the cloud provider over nine moths to deploy a fix, in early April, allowing disclosure of the vulnerability by Astrix.
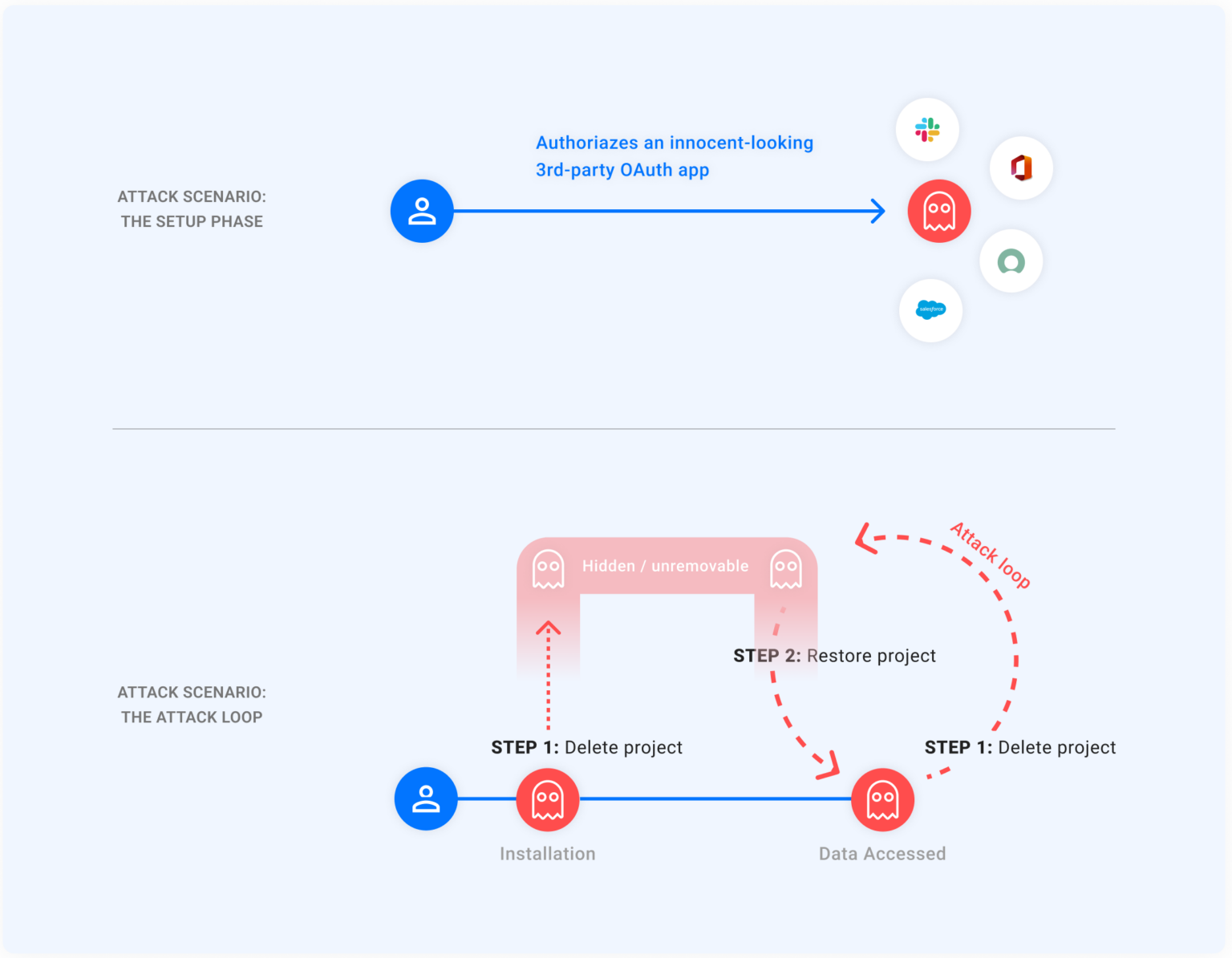
(Image credit: Astrix)
A hypothetical attack would work by getting the victim to naively grant access, via the OAuth 2.0 protocol, to their Google account by an apparently trustworthy app. The attacker then replaces the app code with a malicious version and - here's the GhostToken trick - deletes the Google Cloud Platform project associated with the OAuth2 authorization. This causes the project to go into a "pending deletion" state, which removes the app from the user's app permissions page at https://myaccount.google.com/permissions and preventing the victim from removing access.
However, the project will not be really deleted for another 30 days, allowing the attacker to restore it, use the access token to copy the victim's data, and then delete the project once more. Just what data the attacker can access depends upon the permissions granted by the victim, but could include access to Gmail, Google Drive, Docs and other application data.
The Google fix simply updates the app permissions page to include apps that are in a pending deletion state, so that the user can revoke access.
Uncredited, GhostToken – Exploiting GCP application infrastructure to create invisible, unremovable trojan app on Google accounts, blog post, 20 April 2023. Available online at https://astrix.security/ghosttoken-exploiting-gcp-application-infrastructure-to-create-invisible-unremovable-trojan-app-on-google-accounts/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Class Action Launched Against Optus
Class action law firm Slater and Gordon has launched an action against Optus, representing 100,000 customers whose data was compromised by an attack some six months ago. The suit alleges Optus breached privacy, telecommunications and consumer laws as well as - perhaps more troubling - the company's own internal policies.
According to Slater and Gordon's class actions practice group leader, Ben Hardwick:
"The type of information made accessible put affected customers at a higher risk of being scammed and having their identities stolen, and Optus should have had adequate measures in place to prevent that.
"Concerningly, the data breach has also potentially jeopardised the safety of a large number of particularly vulnerable groups of Optus customers, such as victims of domestic violence, stalking and other crimes, as well as those working in frontline occupations including the defence force and policing."
In general, privacy laws require data controllers or custodians to take 'reasonable steps' or implement 'reasonable safeguards' to protect personal data, and a possible line of defence could be the argument that it is not reasonable to expect even the best security professionals to foresee, and have the resources to protect against, every possible attack - this is why we perform risk management in order to prioritize our defences.
However, if the suit specifically alleges that the breach was due to Optus staff not complying with its own policies, that suggests that this class of attack was foreseen and a reasonable safeguard - by Optus' own definition - should have been in place to prevent it. It also implies a lack of audit and testing to detect the absence of the appropriate control. There are suggestions that customer data was exposed while testing an API or via a now-unused API; the use of real customer data for testing is a fundamental no-no, but the breach could also have been due to improper web API asset management or excessive data exposure.
With almost ten million Optus customers affected, the plaintiff class should grow substantially, and as this action plays out many CISO's and commentators will be watching closely.
Knight, Ben, Optus data breach class action launched for millions of Australians caught up in cyber attack, ABC News, 21 April 2023. Available online at https://www.abc.net.au/news/2023-04-21/optus-hack-class-action-customer-privacy-breach-data-leaked/102247638.
May, Natasha, Optus sued by 'vulnerable' victims of data breach, The Guardian, 21 April 2023. Available online at https://www.theguardian.com/australia-news/live/2023/apr/21/australia-news-live-renewables-superpower-clean-energy-summit-jim-chalmers-nsw-liberals-leadership-indigenous-voice-cost-of-living-interest-rates-drug-reform.
Ransomware Attacks Poorly-Secured Microsoft SQL Servers
South Korean security firm AhnLab has discovered a relatively new type of ransomware now being used to compromise poorly-secured Microsoft SQL Server database servers. The Trigona malware first appeared in late 2022, and Palo Alto Networks' Unit 42 has also detected it being deployed against a range of industries in the US, Italy, France, Germany, Australia and New Zealand.
The threat actor monitored by AhnLab's Security Emergency response Center (ASEC) achieves initial compromise of the SQL Servers via either brute force or dictionary attacks, indicating that the servers a) are directly exposed to the Internet - tsk, tsk! - and b) have weak passwords on either admin or service accounts. Another problem is the installation of SQL Server on desktop and even laptop machines as part of some ERP and vertical-market applications - the author remembers installing the software for a TV tuner card on his desktop PC and being amazed to discover a complete installation of SQL Server, just to maintain the electronic program guide (EPG) when a smidgin of XML would have done the job!
Having achieved initial access, the actor installs CLR Shell, a backdoor which is written in assembler for the .NET common language runtime. This backdoor - similar to a webshell - can accept commands to enumerate system information as well as achieving privilege escalation by editing the registry and rebooting the system to change the SQL service account to LocalSystem. Having done this, the actor installs a dropper, svcservice.exe, which will create and launch the Trigona ransomware, svchost.exe, as well as a batch file which edits registry keys to ensure Trigon runs after every reboot, then deletes volume shadow copies and disables the system recovery feature. The batch file the invokes a copy of the Trigona svchost.exe for each possible drive letter from C:\ to Z:\ before finally deleting the svcservice.exe dropper and its related files.
As the ransomware runs, it leaves a ransom note, under the filename how_to_decrypt.hta, in every directory. This instructs the victim to download the Tor browser and go to a specific address - embedded in the file via JavaScript - for instructions on how to make payment. Unusually, Trigona is written in Delphi (the contemporary descendant of the old Turbo Pascal). Another unusual characteristic of this threat actor is that it requests payment in Monero, rather than the more popular Bitcoin.
Sanseo, Trigona Ransomware Attacking MS-SQL Servers, blog post, 17 April 2023. Available online at https://asec.ahnlab.com/en/51343/.
Lee, Frank and Scott Roland, Bee-Ware of Trigona, An Emerging Ransomware Strain, blog post, 16 March 2023. Available at https://unit42.paloaltonetworks.com/trigona-ransomware-update/.
How To Host User-Controlled Content?
Most security professionals, and some web developers, are aware of the challenges of hosting user-generated or -controlled content in their applications. This can include simple cases like user-uploaded photos or graphics, through to more sophisticated cases which might involve the use of HTML tags. If user uploads are ruthlessly sanitized, the result can be cross-site scripting, cross-site request forgery and a range of other attacks.
The classic solution is to separate untrusted, user-controlled content from trusted site content by using sandbox domains. You may have noticed Google doing this, for example - while their own trusted content is hosted at google.com, the untrusted user-controlled content is downloaded from googleusercontent.com. Many other sites work the same way.
A new article from Google Security provides a useful tutorial on more modern techniques which are both easier and more secure, and work by taking advantage of HTTP header fields that many developers simply are not aware of. The article describes two basic use cases.
The first is serving completely passive user content, such as images and file downloads. The basic technique here is to set the Content-Type header to a well-known MIME type this is supported by all browsers and guaranteed not to contain active content. If in doubt, application/octet-stream is a safe choice. However, in addition, a number of other response headers, such as Cross-Origin-Resource-Policy and Content-Security-Policy, should also be set to ensure that the browser fully isolates the response.
However, some user-controlled content, such as HTML or scalable vector graphics (SVG files), needs to be interpreted by the browser. Here, the basic technique is to use the Content-Security-Policy: sandbox header, but once again, there are advanced twists, such as adding a sandbox domain to the public suffix list, and developing specialised handlers that convert the user-controlled content into a pre-rendered blob (binary large object).
Dworkin, David, Securely Hosting User Data in Modern Web Applications, blog post, 18 April 2023. Available online at https://security.googleblog.com/2023/04/securely-hosting-user-data-in-modern.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Consumers Ready for Passkeys - Once They Know About Them
A new survey conducted by password manager vendor 1Password indicates that consumers are ready for a passwordless future using passkeys - but they don't know about them.
Passkeys were developed by the FIDO Alliance (specifically, the Client-to-Authenticator Protocol [CTAP]) and the World Wide Web Consortium (the Web Authentication specification). This passwordless (yay!) authentication system effectively works the same way as the SSH public-key authentication familiar to security professionals - during site registration, the protocol automatically generates a public/private key pair and uploads the public key to the user's new account on a web site. From that point on, the user need only unlock their authenticator - which could use biometrics on a smartphone, so just a tap would be required - and that will select the correct private key and complete the authentication process.
Unsurprisingly, 1Password's survey revealed that almost two out of every three people say that they are open to using any new technology that will make their lives simpler. However, only one in four has heard the term 'passwordless', indicating that they are not seeing it on the web sites they use or in mainstram media coverage.
However, once shown a description and an example of passkeys in operation, 75% of respondents say they are open to using them.
Since Google, Microsoft and Apple have all announced passkey support in their browsers, the bottleneck to adoption probably lies with the developers of popular web development platforms. Consumers have shown a preference for federated identity management solutions where appropriate and available, and would almost certainly switch rapidly to passkeys once they are widely accepted.
Uncredited, Preparing for a passwordless future, report, 18 April 2023. Available online at https://1password.com/resources/passwordless-future-report.
The Billion Dollar Scam
Following Monday's ABC Four Corners documentary on ransomware group REvil, we have stumbled across another interesting doco from a national broadcaster. In this one, BBC investigative reporter Simona Weinglass has led a wide-ranging investigation into a criminal network which is believed to have scammed more than one billion dollars through investment scams all over the world.
While Chinese gangs are notorious for running 'pig butchering' scams in SE Asia, this particular group runs a similar operation targeting European and US victims from call centers - in Kyiv until the war began, followed by a rapid relocation to Tbilisi in Georgia. Perhaps most fascinating is the way the ringleaders distance themselves from the front-line workers, behaving and appearing in almost all respects as legitimate businessmen - not to mention the regret felt by some of the call center workers when they realise their well-paying jobs are not with a legitimate investment fund, but actually a criminal organization.
Weinglass, Simona, The Billion Dollar Scam, documentary program, 14 April 2023. Available online at https://www.youtube.com/watch?embed=no&v=w6JXZ3GzSCQ.
Vaastamo CEO Given (Suspended) Jail Time
Our course attendees and regular readers will be familiar with the case of Finnish mental healthcare provider Vaastamo, which suffered a ransomware breach in September 2020, encrypting their patient records. When the company's CEO, Ville Tapio, refused to pay a ransom, the firm discovered that the ransomware had also performed data exfiltration, as the hackers released sensitive patient records on a Tor network server. And when the CEO still refused to pay the ransom, the hackers turned to extorting payments from the individual patients, predictably leading to a class action.
Investigations revealed that the company's software was only minimally secured and did not comply with Finland's regulations for healthcare records systems. The CEO was terminated and the company subsequently liquidated.
On Tuesday, the Helsinki District Court handed down its judgement in a criminal prosecution of former Vaastamo CEO Ville Tapio for a data protection offence. The court found that he did not fulfil the EU's GDPR (General Data Protection Regulation) requirements to pseudonymise and encrypt patient data handled by the company.
The court characterised Tapio's actions as particularly reprehensible, due to both the size of the breach and the sensitivity of the information involved. In the sentencing statement, the court found that, "Taking into account the long period of time, the district court finds that this act cannot be reconciled with fines, but that Tapio must receive a prison sentence for the act". However, considering that Tapio had no previous criminal record, the court imposed a three month suspended sentence.
Tapio had claimed ignorance of the company's poor security, blaming the breach on two former IT staff. However, governance law and regulations in most jurisdictions makes boards and executive management liable for the management of cybersecurity risk, so that defence was never going to fly.
Incidentally, the alleged perpetrator of the breach, Aleksanteri Kivimäki, was apprehended back in late February and will face a range of charges in due course.
YLE News, Hacked therapy centre's ex-CEO gets 3-month suspended sentence, news report, 18 April 2023. Available online at https://yle.fi/a/74-20027665.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
APT28 Exploited Known Vulnerability in Cisco IOS
The US Cybersecurity & Infrastructure Security Agency, the UK National Cyber Security Centre, NSA and FBI have released a joint advisory, detailing the tactics, techniques and procedures used by APT28 in its exploitation of Cisco routers, mainly back in 2021 APT28 is perhaps better known as Fancy Bear, Sofacy or STRONTIUM, although it is officially the Russian General Staff Main Intelligence Directorate (GRU) 85th special Service Centre (GTsSS) Military Intelligence Unit 26165.
The group was able to exploit CVE-2017-6742, which was fixed back in June 2017 (several years before the exploitation). This vulnerability affects Cisco's implementation of SNMP (Simple Network Management Protocol) v2 in its routers - SNMP v2 has long been known to have weak authentication and in many cases, all that is required is the default community string value of 'public' to be able to query the management information base on a network device.
So, the threat actors simply scanned for routers with weak community strings, and upon discovering one, used CVE-2017-6742 to inject their malware directly into the memory of the router. This means that the malware - called Jaguar Tooth - is non-persistent, but can easily be reinjected whenever required. Once resident in memory, Jaguar Tooth grants telnet access to existing local accounts, and also creates a process called 'Service Policy Lock' which runs a number of show commands, exfiltrating the results over the TFTP protocol:
- show running-config
- show version
- show ip interface brief
- show arp
- show cdp neighbors
- show start
- show ip route
- show flash
The lessons are obvious. First, network devices are an increasingly popular target for threat actors as they allow interception of inbound and outbound traffic; furthermore, they often receive far less scrutiny and monitoring than computers and cannot run the endpoint detection and response tools available for popular operating systems. Hence, the first mitigation has to be a policy of proactive patching - the exploited routers should have been updated four years earlier.
SNMP v1 and v2 should be replaced with more secure protocols, such as NETCONF or RESTCONF, for remote management (and telnet should be disabled!). The joint advisory, coupled with the UK NCSC's two reports, provide a lot more detail.
CISA, APT28 Exploits Known Vulnerability to Carry Out Reconnaissance and Deploy Malware on Cisco Routers, cybersecurity advisory, 18 April 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-108.
NCSC, APT28 exploits known vulnerability to carry out reconnaissance and deploy malware on Cisco routers, advisory, 18 April 2023. Available online at https://www.cisa.gov/sites/default/files/2023-04/apt28-exploits-known-vulnerability-to-carry-out-reconnaissance-and-deploy-malware-on-cisco-routers-uk.pdf.
NCSC, Jaguar Tooth, malware analysis report, 18 April 2023. Available online at https://www.ncsc.gov.uk/static-assets/documents/malware-analysis-reports/jaguar-tooth/NCSC-MAR-Jaguar-Tooth.pdf.
New Device Advances Quantum Key Distribution
While much hype surrounds the potential of quantum computers, especially for breaking existing public-key cryptography algorithms, other quantum developments continue to provide solutions to the problem. One of these areas is quantum key distribution, which solves the key distribution problem by providing a form of key transfer which is immune to eavesdropping.
The key distribution problem can be simply stated. Alice and Bob wish to communicate over an insecure channel - one on which Eve can eavesdrop. Alice and Bob can solve their problem by encrypting their communication using an algorithm like AES, but in order to do that, they each need to have the same key. If Alice comes up with a random key and sends it to Bob over their insecure channel, Eve will simply intercept the key, and they will be no better off - so how can they exchange or agree on a key without Eve getting hold of it?
Current systems mostly solve this problem using public-key cryptographic algorithms like having Alice 'wrap' the random key using Bob's RSA public key and sending it to him; since Eve does not have Bob's private key - only Bob has that - she cannot learn the key. Or Alice and Bob can use Diffie-Hellman key agreement. But these are the techniques that quantum computers may well break in the not-too-distant future.
Much attention has focused on the use of polarized photons to send a key over a fiber optic cable. Since they only way to figure out the polarization of a photon is to pass it through a polarized filter and detect what comes out, any attempt by Eve (or Mallory, the man-in-the-middle) to do this will either change the polarity of many photons or block them completely, rendering the attack obvious to Alice and Bob. Using a protocol called BB84 with privacy amplification, this technique has already been commercialized and rack-mount devices for quantum key distribution are already available.
However, there's another promising technique waiting in the wings that is completely unobservable by Eve and Mallory, based on quantum entanglement - a phenomenon that Einstein could never come to terms with, calling it "spooky action at a distance". When two subatomic particles are entangled, any change to one of the particles happens to the other, no matter how far apart the particles are, and with no apparent communication between them. In other words, there is nothing for Eve or Mallory to intercept.
Already, scientists in China have demonstrated satellite-based distribution of entangled photon pairs to two locations over 1,000 km apart via two satellite-to-ground downlinks [1]. However, this technique is expensive and still highly experimental; optical fiber will likely remain cheaper for shorter distances. In both cases, the cost of the equipment for generation of entangled photons remains a barrier.
However, a new paper [2] reveals the first photonic device that puts all the circuitry on one chip, combining an optical amplifier built out of indium phosphide - effectively a semiconductor laser that can generate a stream of photons - with a second section containing progressively smaller 'microring resonators', made of silicon nitride, which filter out noise and eventually produce a pair of entangled photons.
The chip, which draws only 3 watts of power, can generate 8,200 pairs of entangled photons per second, at the wavelengths commonly used for fiber optic cables. Although there are still some challenges in the complexity of the manufacturing process and the chip's performance, the fact that it reduces the size of the quantum light source by a factor of 1,000 could accelerate the use of quantum entanglement out of the laboratory and into real-world applications.
The original papers below are, of course, incredibly technical, but the IEEE Spectrum article is much more accessible for the layman.
[1] Yin, J., Cao, Y., Li, Y.-H., Liao, S.-K., Zhang, L., Ren, J.-G., Cai, W.-Q., Liu, W.-Y., Li, B., Dai, H., Li, G.-B., Lu, Q.-M., Gong, Y.-H., Xu, Y., Li, S.-L., Li, F.-Z., Yin, Y.-Y., Jiang, Z.-Q., Li, M., … Pan, J.-W. (2017). Satellite-based entanglement distribution over 1200 kilometers. Science, 356(6343), 1140–1144. https://doi.org/10.1126/science.aan3211.
[2] Mahmudlu, H., Johanning, R., van Rees, A., Khodadad Kashi, A., Epping, J. P., Haldar, R., Boller, K.-J., & Kues, M. (2023). Fully on-chip photonic turnkey quantum source for entangled qubit/qudit state generation. Nature Photonics, 1–7. https://doi.org/10.1038/s41566-023-01193-1.
Gent, Ed, Entangled Photons Produced Entirely On-Chip: Quantum photonic technology reduced to the size of a coin, IEEE Spectrum, 17 April 2023. Available online at https://spectrum.ieee.org/quantum-entanglement.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Four Corners Cybercrime Doco Drops
As we predicted, the Australian Broadcasting Commission has made available the latest episode of its flagship current affairs program, Four Corners, on YouTube so that it is available to international viewers. The documentary deals with the nexus between cybercrime and cyberwarfare, and covers attacks in Australia - most notably on Medibank - and in Ukraine.
Four Corners, Cyber Gangs Cracked Open, documentary film, 17 April 2023. Available online at https://www.youtube.com/watch?embed=no&v=4m6Ydx0TGMY.
Alleged Criminals Challenge Evidence From 'Secure' Messaging Service
In a case that could have implications for the use of evidence obtained via implants on smartphones, around 50 alleged criminals are challenging the admissibility of evidence obtained in the Australian Federal Police's Operation Ironside.
Ironside was the Australian end of a joint operation with the FBI (who called it Trojan Shield) and Europol's Task Force Greenlight. The FBI had obtained the 'cooperation' of a developer who had been working on an encrypted messaging device called ANOM for use by criminal networks; in exchange for a reduced sentence he agreed to finish the development and make it available to his criminal customers. However, the customers did not know that the service's proxy servers were copying all messages, along with the related private keys, to FBI-controlled servers, and the FBI was sharing some of these with the AFP.
In this week's Sydney committal hearing, barristers for the defendants will challenge the validity of evidence obtained via these messages. The AFP claimed that they had been granted a "court order to legally monitor the ANOM devices of the individuals in Australia or with a clear nexus to Australia". However, magistrate Robert Williams will now have to decide whether that evidence was legally intercepted. Much hinges on the question of where duplication of of messages took place and whether the devices were connected to a telecommunications network at that time, based on technical testimony by an expert witness who has examined some of the ANOM source code.
In a similar challenge heard before the Supreme Court of South Australia, Justice Adam Kimber held that the Operation Ironside intercepts were legally conducted.
Parkes-Hupton, Heath, Why accused criminals are challenging evidence in Sydney from one of the world's biggest police stings, ABC News, 18 April 2023. Available online at https://www.abc.net.au/news/2023-04-18/accused-criminals-challenge-an0m-app-evidence-in-supreme-court/102107344.
Former FIN7 and Conti Members Join Forces
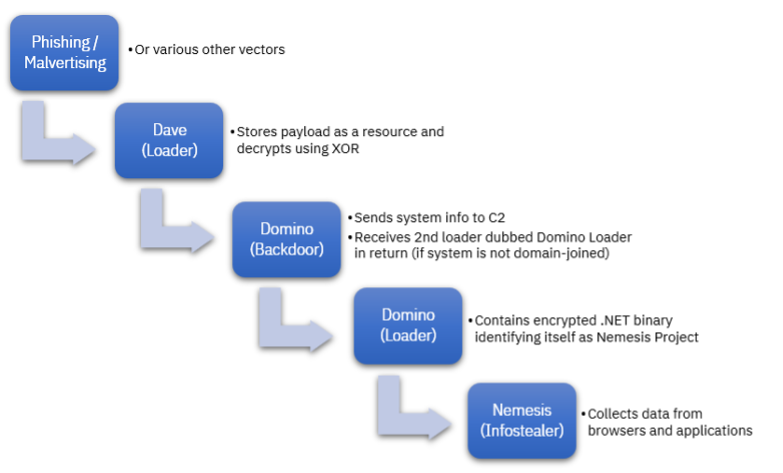
A report from IBM Security X-Force reveals that developers from the FIN7 gang have developed a new backdoor family called (by X-Force) Domino. The Domino code overlaps with the older Lizar malware which cames from the same source. But what makes recent campaigns particularly interesting is that Domino is being deployed using the Dave Loader, suggesting that the campaigns are being run by former members of the Conti ransomware syndicate. Conti fragmented into several factions, including Quantum, Royal, BlackBasta and Zeon.
These factions have used Dave Loader to deliver Cobalt Strike payloads, as well as IcedID and Emotet, which are both used as initial access vectors for subsequent ransomware operations. However, the payload of some recent Dave Loader samples was Domino Backdoor, a DLL which performs basic system enumeration (system name, user names, running processes), sending this back to the group's C2 server. The server will respond with a command which triggers download of a second loader which shares code with Domino (hence, Domino Loader) which in turn decrypts an internal payload which turns out to be a .NET infostealer called Nemesis Project.
(Image credit: IBM Security X-Force)
However, if the victim machine is a domain member, Domino Backdoor contacts a different C2 server, possibly to download a more capable backdoor such as Cobalt Strike which can then be used to pivot against other systems.
The combination of tools in this campaign indicates the fluid nature of cybercrime operations, with groups fracturing and members collaborating to form new syndicates.
Hammond, Charlotte and Ole Villadsen, Ex-Conti and FIN7 Actors Collaborate with New Domino Backdoor, blog post, 14 April 2023. Available online at https://securityintelligence.com/posts/ex-conti-fin7-actors-collaborate-new-domino-backdoor/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cozy Bear Targets NATO, EU in Cyberespionage Campaign
The Polish Military Counterintelligence Service and the CERT Polska team have reported a widespread cyber-espionage campaign targeting foreign ministries and diplomatic entities in NATO member states, the European Union and, to a lesser extent, Africa. Many of the TTP's observed are consistent with the previous activities of APT 29, a.k.a. Cozy Bear or Nobelium, which operates on behalf of the Russian SVR. However, this campaign, which is still ongoing, utilises new software tools.
In all observed cases, the threat actor utilised spear-phishing tactics, with emails carrying invitations to meetings or collaborative documents, apparently from the embassies of European countries. In each case, the email or attached document contained a link to a compromised website containing the ENVYSCOUT script, which uses HTML smuggling to decode a downloaded file to the victim's device. While previous APT 29 campaigns have used .ZIP or .ISO files to package the malware payload and avoid its being stamped with the Mark of the Web, this time .IMG files were also used. A variety of techniques were used to entice the user into running the malware - such as adding lots of spaces to the filename so that its .EXE filetype would not be visible.
The actor's tool delivery flow (Image: CERT.PL)
Three new tools were observed:
- SNOWYAMBER – a tool first used in October 2022, abusing the Notion service to communicate and download further malicious files. Two versions of this tool have been observed.
- HALFRIG – used for the first time in February 2023. This tool is distinguished from the others by the embedded code that runs the COBALT STRIKE tool.
- QUARTERRIG – a tool first used in March 2023, sharing part of the code with HALFRIG. Two versions of this tool were observed.
SNOWYAMBER and QUARTERRIG are downloaders which perform some basic enumeration and, if the victim machine seemed to be of interest, download and run either Cobalt Strike or Brute Ratel. HALFRIG, however, is a loader which contains Cobalt Strike and runs it automatically.
The Polish Military Counterintelligence Service and CERT.PL recomend a number of configuration changes to defend against this and similar campaigns:
- Blocking the ability to mount disk images on the file system. Most users doing office work have no need to download and use ISO or IMG files.
- Monitoring of the mounting of disk image files by users with administrator roles.
- Enabling and configuring Attack Surface Reduction Rules.
- Configuring Software Restriction Policy and blocking the possibility of starting-up executable files from unusual locations (in particular: temporary directories, %localappdata% and subdirectories, external media).
gov.pl, Espionage campaign linked to Russian intelligence services, knowledge base article, 13 April 2023. Available online at https://www.gov.pl/web/baza-wiedzy/espionage-campaign-linked-to-russian-intelligence-services.
Australians Lose $A3.1 Billion to Scams
The latest Targeting Scams report from the Australian Competition and Consumer Commission has revealed that Australians lost a record $A3.1 billion to scams in 2022 - an 80% increase on the previous year. The report, which compiles data reported to the ACCC's Scamwatch, ReportCyber, the Australian Financial Crimes Exchange (AFCX), IDCARE and other government agencies, shows that the highest loss category was investment scams ($A1.5 billion) followed by remote access/tech support scams ($A229 million) and payment redirection scams ($A224 million).
The financial loss is only one dimension; since many victims lose significant amounts - their entire life savings, in some cases - they, their families and their businesses may suffer emotional distress and life disruption.
Although Scamwatch received a lower number of reports this year, the total financial losses increased significantly, with the average loss rising to almost $20,000. Scams are also increasingly difficult to detect, with more sophisticated tactics such as impersonating of official phone numbers, email addresses and websites to the insertion of scam texts in legitimate conversation threats.
ACCC, Targeting scams: Report of the ACCC on scams activity 2022, technical report, 17 April 2023. Available online at https://www.accc.gov.au/about-us/publications/serial-publications/targeting-scams-report-on-scams-activity/targeting-scams-report-of-the-accc-on-scams-activity-2022.
REvil Hacker Breaks Cover, Chats to Reporters
In an intriguing report produced by the Australian Broadcasting Corporation, journalists have chatted to a hacker who claims to be part of the REvil ransomware gang which is believed to be responsible for last year's Medibank data breach. Medibank refused to pay the demanded ransom, and in response the hackers released the medical records of around 2,000 people on their site.
The hacker, who uses the handle, "Kerasid", claims that "Australians are the most stupidest humans alive, and they have a lot of money for no reason - alot of money and no sense at all". When a reporter messaged him, "The medibank hack caused distress to millions of Australians. Does this concern you? ", he replied, "I could not care less" and later stated, "it isn’t wrong in my eyes ".
The chat was part of an investigation undertaken by ABC current affairs program, Four Corners, the report from which will air on ABC TV tonight, 17 April 2023, at 8:32 PM AEST. (Four Corners episodes are often reposted on the ABC News In-depth YouTube channel, and we will post a link in due course.)
The history of the REvil and Conti ransomware gangs is long and murky - both groups appear to have fractured, with new groups inheriting parts of their code base and recruiting new affialiates and initial access brokers. The article, and the TV program, provide an insight into the groups' structures and operations.
Longbottom, Jessica, John Lyons and Jeanavive McGregor, Chatting with a hacker, ABC News, 17 April 2023. Available online at https://www.abc.net.au/news/2023-04-17/cybercrime-hacker-chats-about-medibank-revil-russia-ukraine/102179776.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
It's World Quantum Day!
April 14th is World Quantum Day - an annual celebration promoting public understanding of quantum science and technology around the world. The World Quantum Day web site at https://worldquantumday.org lists 200 events in over 193 cities and 44 countries, so there's bound to be something for everyone.
For cybersecurity and infosec wonks, this is as good a day as any, and better than most, to once again push the need for cryptographic agility - that is, the need to design and implement our systems so that we will be able to replace those public-key crypto algorithms which may (or already have) fallen due to the ability of quantum computers to break them in polynomial time. That's essentially all of the currently-utilised algorithms based on trapdoor problems in involving factorization or the computation of logarithms in a finite field: RSA, ElGamal, Diffie-Hellman Key Agreement, DSA, and their elliptic curve derivatives.
Bear in mind that if somebody already has a quantum computer, they are not going to reveal that fact as it confers a tremendous advantage. And even if "they" don't yet have a quantum crypto-breaking capability, "they" can store away intercepted traffic until they do, at which point they will be able to retrospectively read encrypted traffic, some of which will still be valuable (in so-called "harvest now, decrypt later" (HNDL) schemes. So the only prudent course of action is to assume this is going to be a problem sooner rather than later, and start switching to post-quantum, or quantum-resistant, cryptographic algorithms.
The US Government is already pushing this, with the Quantum Computing Cybersecurity Preparedness Act, which mandates the migration of Federal Government systems to post-quantum crypto algorithms. And the longer we leave it, the faster the change will have to be accomplished - hence the plea for cryptographic agility, which at least lays the groundwork.
Clancy, Charles and Teresa H. Shea, Why the US Needs Quantum-Safe Cryptography Deployed Now, Dark Reading, 14 April 2023. Available online at https://www.darkreading.com/dr-tech/why-the-us-needs-quantum-safe-cryptography-deployed-now.
More Israeli Implants Revealed by Citizen Lab
The Citizen Lab researchers at the University of Toronto's Munk School of Global Affairs and Public Policy have a long track record of sterling work in revealing the activities of state-sponsored and other actors who conduct surveillance and other attacks on journalists and civil rights campaigners. In their latest report, they describe the exploits developed by Israeli spyware vendor QuaDream.
Smartphones are an excellent platform for secure (encrypted, confidential and sometimes anonymized) communications by journalists, civil rights campaigners and NGO workers. Because the traffic generated by smartphone messaging applications are encrypted, usually with reasonably well-designed key exchange protocols, it is effectively impossible for the traditional wire-tapping schemes to work - the traffic can be intercepted but not decrypted, leaving only traffic analysis as a means of attack (and sometimes, not even that).
The only way to intercept communications therefore is by means of an implant - essentially a software keystroke or other logger which is able to capture communications before it is encrypted or after it is decrypted. And so a number of firms - primarily Israeli, for some reason (most notably NSO Group) - specialize in developing such implants which can hook into the iOS and Android mobile OS's in undetectable ways. They also develop exploits which can either trick a victim into installing them - a big hurdle when the targets are sensibly paranoid and security aware - or, better still, infect a system with no user interaction at all: so-called zero-click exploits.
One such company is QuaDream, which markets its "Reign" spyware to government clients, including Singapore, Saudi Arabia, Mexico and Ghana. The company maintains an exceptionally low profile, with no web site and essentially no press coverage. It it wasn't embroiled in a legal dispute with its international marketing partner InReach, requiring the lodging of documents with a court in Cyprus, the company would be essentially invisible.
Microsoft Threat Intelligence recently captured two samples of iOS spyware which they call KingsPawn and attribute, with high confidence, to QuaDream. They passed these samples to Citizen Lab, who analysed them and determined that the first was a loader, intended to exfiltrate basic device information and then download and execute a second payload. The second sample appears to be a full featured spyware payload. The two share common code, indicating they come from the same development team.
The spyware payload has a wide range of surveillance functionality:
- Record audio from calls
- Record from the microphone ("hot mic")
- Take pictures using front & back cameras
- Exfiltrate and remove keychain items
- Generate iCloud 2FA passwords
- Search through device files and databases
- Clean up its own traces
- Track location
Detailed analysis also led to QuaDream's iOS 14 zero-day, zero-click exploit, called ENDOFDAYS. Citizen Lab identified two cases where this was used against targets in North America and Central Asia. It appears that the ENDOFDAYS exploit works by using an XML escape vulnerability in the iCloud calendar; if this is correct, it only requires the attacker to add a calendar event which injects XML data into the target's phone.
Citizen Lab were also able to devise fingerprints and identify over 600 command and control servers and 200 domain names which appear to have been linked to QuaDream's spyware between late 2021 and early 2023, and in several cases trace them back to their operators, suggesting that these systems were operated from the following countries:
- Bulgaria
- Czech Republic
- Hungary
- Ghana
- Israel
- Mexico
- Romania
- Singapore
- United Arab Emirates (UAE)
- Uzbekistan
Several of these countries have what can at best be described as a patchy track record with respect to surveillance of citizens, especially human rights advocates and journalists.
Marczak, Bill, et. al., Sweet QuaDreams: A First Look at Spyware Vendor QuaDream’s Exploits, Victims, and Customers, technical report, 11 April 2023. Available online at https://citizenlab.ca/2023/04/spyware-vendor-quadream-exploits-victims-customers/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
VPS's Replace IoT for DDoS Attackers, Says Cloudflare
In its first DDoS threat report for 2023, web acceleration and DDoS mitigation company Cloudflare reports a shift away from the use of compromised Internet of Things devices by attackers. Instead, the threat actors are making use of virtual private servers (VPS's) hosted by cloud computing service providers. The reason is simple: IoT devices are typically low-powered and connected to low-bandwidth consumer networks, while VPS's, located in large data centers, are much more powerful devices and are connected to the Internet by fat pipes.
The threat actors take over these servers by compromising unpatched servers and also hacking the management consoles using leaked API credentials. Cloudflare has been addressing this by setting up a free botnet threat feed for cloud service providers which will alert the firms to attacks originating within their own networks, so that they can be brought down promptly.
In other highlights from the DDoS threat report:
- The year began with a series of campaigns against Western targets such as banking, airports, healthcare and universities, mostly led by the pro-Russian Telegram-organized group Killnet and more recently by AnonymousSudan
- Hyper-volumetric attacks increased significantly, with the largest one peaking at over 71 million requests per second (the previous world record was 'only' 46 million rps)
- 16% of Cloudflare customers reported a Ransom DDoS attack - holding steady in comparison with the previous quester, but a 60% year-on-year increase
- The most-targeted country for HTTP DDoS traffic is Israel, which displaced the US from the top spot (followed by Canada and Turkey).
- The most-targeted country for network-layer DDoS attack traffic was China, closely followed by Singapore.
Yoachimik, Omer and Jorge Pacheco, DDoS threat report for 2023 Q1, blog post, 11 April 2023. Available online at https://blog.cloudflare.com/ddos-threat-report-2023-q1/.
Don't Charge from Public USB Outlets, Says FBI
The FBI's Denver office has tweeted a warning against the use of free USB charging stations:
Avoid using free charging stations in airports, hotels or shopping centers. Bad actors have figured out ways to use public USB ports to introduce malware and monitoring software onto devices. Carry your own charger and USB cord and use an electrical outlet instead.
We'd generally agree, but also add that a USB condom - an inline connector which connects only the power lines and blocks data transfer - is a useful alternative, especially for international travelers who want to avoid carrying lots of power adapters. However, they may disable the fast charging capabilities of some devices. In any case, leaving your high-end phone plugged in on a shelf while you queue for a coffee nearby is an invitation to theft. Better to carry a power pack and recharge inside your locked hotel room (but even then . . .).
FBI Denver, Avoid using free charging stations ..., tweet, 6 April 2023. Available online at https://twitter.com/FBIDenver/status/1643947117650538498.
New Google API Helps to Secure the Supply Chain
Google has announced a new online API - the deps.dev API - which provides free access to a dataset of security metadata including dependencies, licenses, advisories and other security-related infor for over 50 million open source software package versions. The dataset is continuously updated from a range of sources, including package registries, the Open Source Vulnerability Database, development repositories such as GitHub and GitLab, and the packages themselves. There are over 5 million packages from the Go, Maven, PyPI, npm, and Cargo ecosystems.
The API will allow the development of tools which will support analyses of software packages and the updating of configuration management databases. This will allow operations and security staff to answer questions such as
- What dependencies does this package have?
- What are the licences for the packages this application uses?
- Will moving to the latest version of this package change dependencies or the licences?
- What versions of what packages contain this file?
The impact of vulnerabilities such as Log4Shell has really brought home the lesson that we need tools that can answer these and even more basic questions, such as "A new vulnerability is being exploited - are we affected?".
Sarnesjo, Jesper and Nicky Ringland, Announcing the deps.dev API: critical dependency data for secure supply chains, blog post, 11 April 2023. Available online at https://security.googleblog.com/2023/04/announcing-depsdev-api-critical.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Russian GRU Officer Doxxed
In a classic 'man bites dog' reversal of the usual order, a Ukrainian hacktivist group called Cyber Resistance has been able to hack the email of a high-ranking officer of the Russian Main Intelligence Directorate of the General Staff of the Russian Army, otherwise known as the GRU. Even 'better', he is the head of the 85th Main Special Service Center of the GRU, military unit 26165, more commonly known as APT 28, a.k.a. Fancy Bear.
APT 28 is one of the most agressive Russian threat actors, known to have run cyberattacks against government agencies and critical infrastructure in Ukraine, the US, the Netherlands, Poland, Latvia, Germany, the Czech Republic and elsewhere. Back in 2018, the US Justice Department formally indicted 12 GRU employees for breaching the email systems of the US Democratic National Committee and attempting to interfere in the 2016 US elections. Among those indicted is the victim of this breach: Lieutenant Colonel Sergey Alexandrovich Morgachev.

(Image credit: Cyber Resistance / InformNapalm)
Among the emails retrieved by the hackers was one from Apple, warning Morgachev that the FBI had requested, and been granted, information regarding his Apple account. The Cyber Resistance hackers were also able to obtain his address details, his passport, the registration of his car (a Toyota RAV4) as well as his employment records, such as a medical certificate required for his security clearance. All of this was passed to the InformNapalm site, which has published it.
Uncredited, Hacked: Russian GRU officer wanted by the FBI, leader of the hacker group APT 28, news article, 10 April 2023. Available online at https://informnapalm.org/en/hacked-russian-gru-officer/.
It's That Day of the Month Again
It's Patchday again - that day when we install a large batch of Windows patches and reboot.
This month, the Windows 11 KB5025239 cumulative update contains fixes for 97 vulnerabilities in various Microsoft products. Key among these is a fix for CVE-2023-28252, a privilege escalation vulnerability in the Windows Common Log File System (CLFS) Driver, which the Cybersecurity & Infrastructure Security Agency has today added to its Known Exploited Vulnerabilities Catalog. The vulnerability is being exploited in ransomware attacks.
The update also adds a number of other fixes and enhancements.
Microsoft Security Response Center, April 2023 Security Updates, web page, 11 April 2023. Available online at https://msrc.microsoft.com/update-guide/releaseNote/2023-Apr.
CISA, CISA Adds One Known Exploited Vulnerability to Catalog, alert, 11 April 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/04/11/cisa-adds-one-known-exploited-vulnerability-catalog.
Guidance for Dealing with BlackLotus
Microsoft has also provided a step-by-step guide for organizations investigating whether users have been targeted by threat actors exploiting CVE-2022-21894 using the UEFI (Unified Extensible Firmware Interface) bootkit, BlackLotus. This bootkit is able to bypass the Windows Secure Boot process and deploy malware files to the EFI System Partition.
Microsoft Security, Guidance for investigating attacks using CVE-2022-21894: The BlackLotus campaign, blog post, 11 April 2023. Available online at https://www.microsoft.com/en-us/security/blog/2023/04/11/guidance-for-investigating-attacks-using-cve-2022-21894-the-blacklotus-campaign/.
Fortinet Product Vulnerability Advisories
Fortiguard Labs has released its monthly Vulnerability Advisories for a range of Fortinet products. Perhaps the most significant is one which allows remote unpassworded access to the redis and mongodb subsystems in FortiPresence, and which rates a CVSS score of 9.3. However, a wide range of products also make the list, including FortiOS and FortiProxy, FortiSandbox/FortiDeceptor, FortiClient for both Windows and Mac, FortiADC, FortiAnalyzer and others.
Uncredited, April 2023 Vulnerability Advisories, PSIRT monthly advisory, April 2023. Available online at https://www.fortiguard.com/psirt-monthly-advisory/april-2023-vulnerability-advisories.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.