Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Biters Bit: Hackers Hack Themselves
Threat intelligence firm Hudson Rock has built a cybercrime intelligence database consisting of over 14.5 million computers infected by infostealers. Using this database, they analyzed 100 of the leading cybercrime forums, finding an amazing 120,000 infected computers, many of them belonging to hackers, which had credentials associated with cybercrime forums.
Let that sink in: these were computers, belonging to hackers, which were infected by infostealers - either unintentionally by the hackers themselves, by associates, or who knows? Bear in mind that hackers can't resist luring in would-be hackers and script kiddies with trojaned hacking tools - download something from a disreputable site like a cybercrime forum, and the phrase caveat emptor should be tattooed on your forehead. The Hudson Rock researchers were probably inspired by a previous example of this, in which an initial access broker called "La_Citrix" accidentally infected his own computer with an infostealer he was using to gather corporate credentials for Citrix and RDP servers.
Infostealers typically enumerate a lot of information, such as system information, credentials (usernames, email addresses and plaintext passwords), browser data including session and authentication cookies and even form autofill data such as names, addresses and phone numbers. It is this information that allows the real identities of the hackers to be discovered.
The biggest single group of infected users - over 57,000 of them - came from the "Nulled.to" forum; "Cracked.io" and "Hackforums.net" were in second and third place, respectively. Analyzing password strength, Hudson Rock found that cybercrime forum users generally use stronger passwords than those used on government web sites.
It also seems that the most effective infostealer for gathering information from cybercriminals is Redline, followed by Raccoon and Azorult.
Hudson Rock, 100,000 Hackers Exposed from Top Cybercrime Forums, blog post, 14 August 2023. Available online at https://www.hudsonrock.com/blog/100-000-hackers-exposed-from-top-cybercrime-forums.
NIST Drafts Major Update to Cybersecurity Framework, Adds Governance Function
The US National Institute of Standards and Technology (NIST) has had a major success on its hands for almost a decade, in the form of its Framework for Improving Critical Infrastructure Cybersecurity. As the name suggests, this framework was originally developed for critical infrastructure like the energy grid as well as financial and telco networks - but its logical structure, coupled with the fact that it was freely downloadable let to it rapidly becoming popular across a range of organizations, right down to small and medium enterprises, both inside the US and internationally. Perhaps as a consequence, it has become better known just as the Cybersecurity Framework (CSF).
While most users were able to adapt 2018's version 1.1 of the CSF to their needs - after all, it is a framework, meaning that it provides a conceptual organizing structure and principles while actually referencing a range of other informative standards - it became obvious that the next revision would have to have a broader scope. Accordingly, the recently-released draft of version 2.0 is now officially titled "The Cybersecurity Framework", and its scope has explicitly been expanded to apply to all organizations regardless of type or size.
In order to direct this update, NIST issued a request for information in February 2022. "Many commenters said that we should maintain and build on the key attributes of the CSF, including its flexible and voluntary nature", said Cherilyn Pascoe, lead developer of the framework. "At the same time, a lot of them requested more guidance on implementing the CSF and making sure it could address emerging cybersecurity issues, such as supply chain risks and the widespread threat of ransomware. Because these issues affect lots of organizations, including small businesses, we realized we had to up our game".
As a consequence, the five principal functions of the Framework - Identify, Protect, Detect, Respond and Recover - have been augmented by a new sixth: Govern. This covers have an organization can establish its own approach to developing and supporting a cybersecurity strategy, setting cybersecurity risk alongside other senior leadership concerns such as legal, financial, operational and other types of risk.
The draft also introdiices the concept of profiles, which tailor and refine the Framework for specific industry sectors and use cases, such as manufacturing industry, elections, the smart grid and extreme fast charging infrastructure for EV's. Following the release of this draft in a few weeks will be a CSF 2.0 reference tool which will allow browsing, searching and export of the CSF core data in both human- and machine-readable formats. A later version of the tool will provide the informative references which link to Standards and other resources.
NIST, NIST Drafts Major Update to Its Widely Used Cybersecurity Framework, news release, 8 August 2023. Available online at https://www.nist.gov/news-events/news/2023/08/nist-drafts-major-update-its-widely-used-cybersecurity-framework.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Bulletproof Hosting Service Shut Down, Five Admins Arrested
In a joint operation, US and European agencies have seized all the servers of, and closed down, a bulletproof hosting service which was being used by cybercriminals to launch attacks across the world.
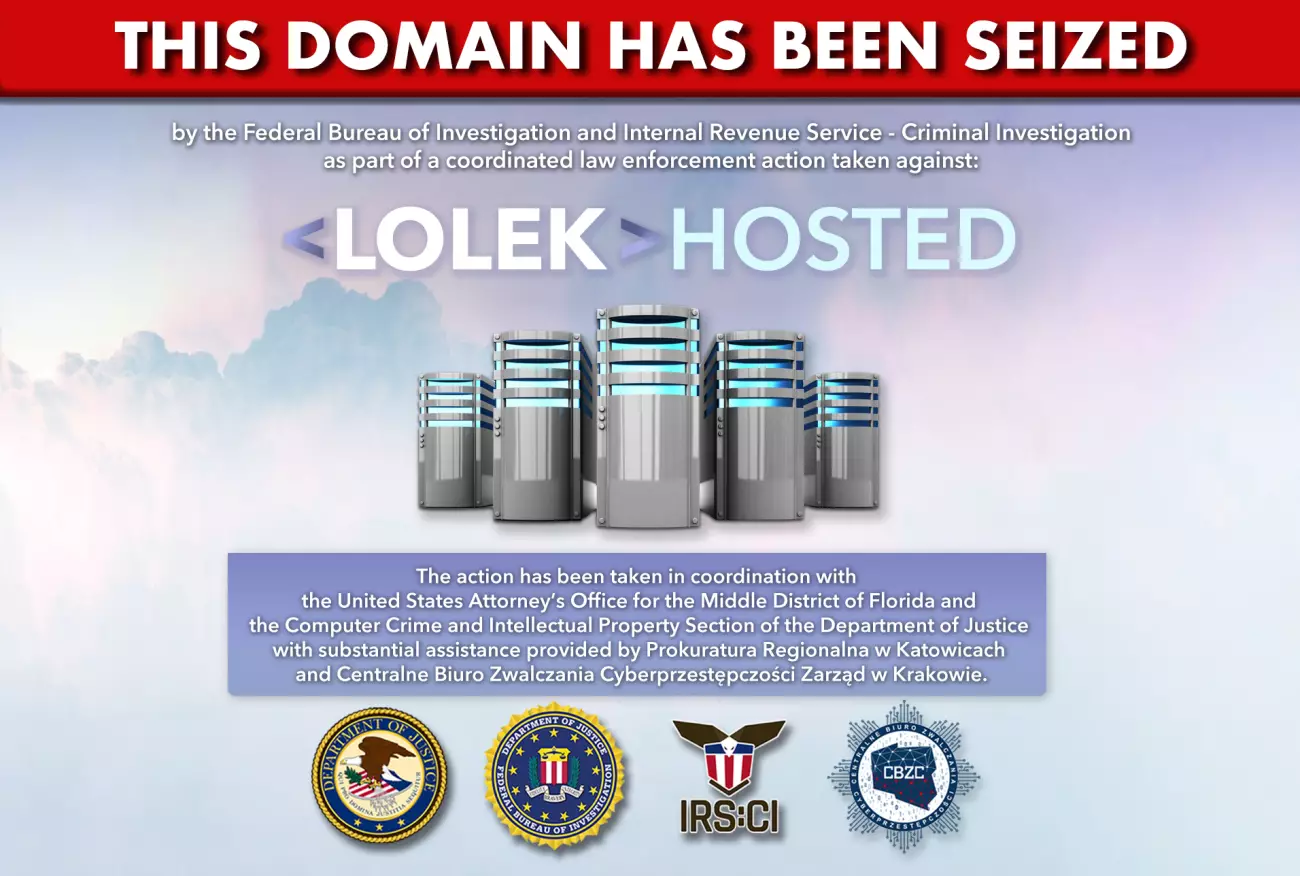
Image credit: Europol
According to court documents unsealed in Tampa, Florida, last week, Artur Karol Grabowski, 36, operated a web hosting company named LolekHosted, which offered secure web hosting intended to facilitate a variety of cybercrime activities, including ransomware, brute-forcing and phishing. The site allowed its clients to register using false information, making payments via cryptocurrencies. Its systems did not maintain logs of its clients' server IP addresses and in fact, frequently changed them; it also ignored abuse complaints made by third parties, and notified clients of any enquiries received from law enforcement agencies. Grabowski advertised that the site was "bulletproof", provided "100% privacy hosting" and allowed clients to host "everything except child porn."
Among the ransomware variants hosted by LolekHosted was NetWalker, which was deployed on approximately 400 networks of roughly 50 victims including municipalities, hospitals, law enforcement and emergency services, school districts, colleges, and universities, resulting in payment of over BTC 5,000 (with a current value of approximately $US146 million). One of these victims was located in the Middle District of Florida, which is why the US District Court there issued a seizure warrant for the domain registration of Lolekhosted.net - see the new banner above.
Meanwhile, the Polish Central Cybercrime Bureau (Centralne Biuro Zwalczania Cyberprzestępczości) under the supervision of the Regional Prosecutor's Office in Katowice (Prokuratura Regionalna w Katowicach) took action, seizing all the servers and arresting five administrators. It is not clear whether Grabowski was one of those arrested, but if so, and extradited to the US, he will face charges of computer fraud conspiracy, wire fraud conspiracy, and international money laundering which will attract a sentence of up to 45 years in prison.
Europol, 5 arrested in Poland for running bulletproof hosting service for cybercrime gangs, news release, 11 August 2023. Available online at https://www.europol.europa.eu/media-press/newsroom/news/5-arrested-in-poland-for-running-bulletproof-hosting-service-for-cybercrime-gangs.
US DoJ Office of Public Affairs, Administrator of 'Bulletproof' Webhosting Domain Charged in Connection with Facilitation of NetWalker Ransomware, press release, 11 August 2023. Available online at https://www.justice.gov/opa/pr/administrator-bulletproof-webhosting-domain-charged-connection-facilitation-netwalker.
DHS Plans Review of Cloud Security Practices
Last month, we brought you news of a number of attacks on Microsoft 365 (Outlook Online) which affected a number of US and European government agencies, which which were attributed by Microsoft to a Chinese state-affiliated threat actor which they track as Storm-0558. The attacks were accomplished by forging authentication tokens for Outlook Web Access in Exchange Online and Outlook.com using an acquired Microsoft Managed Service Account (MSA) consumer signing key.
In response to this intrusion, the Department of Homeland Security's Cyber Safety Review Board (CSRB) has announced plans for an in-depth review on the malicious targeting of cloud computing environments, focusing on the approaches which government, industry and cloud service providers should employ to strengthen identity management and authentication in the cloud. The intention is to develop actionable recommendations that will advance security practices for both cloud service providers and their customers.
"Organizations of all kinds are increasingly reliant on cloud computing to deliver services to the American people, which makes it imperative that we understand the vulnerabilities of that technology", said Secretary of Homeland Security Alejandro N. Mayorkas. "Cloud security is the backbone of some of our most critical systems, from our e-commerce platforms to our communication tools to our critical infrastructure. In its reviews of the Log4j vulnerabilities and activities associated with Lapsus$, the CSRB has proven itself to be ready to tackle and examine critical and timely issues like this one. Actionable recommendations from the CSRB will help all organizations better secure their data and further cyber resilience".
Once completed, Secretary Mayorkas will provide a report to the Cybersecurity and Infrastructure Security Agency and thence ultimately to President Biden. The CSRB has previously reported on the log4j vulnerability and its most recent report, publicly released only last week, examined the recent attacks by the extortion-focused Lapsus$ ransomware group, finding that Lapsus$ leveraged simple techniques to evade the industry-standard security tools used by most enterprises.
Department of Homeland Security, Department of Homeland Security’s Cyber Safety Review Board to Conduct Review on Cloud Security, press release, 11 August 2023. Available online at https://www.dhs.gov/news/2023/08/11/department-homeland-securitys-cyber-safety-review-board-conduct-review-cloud.
Cyber Safety Review Board, Review of the Attacks Associated with Lapsus$ and Related Threat Groups, technical report, 24 July 2023. Available online at https://www.cisa.gov/resources-tools/resources/review-attacks-associated-lapsus-and-related-threat-groups-report.
CISA Releases Vulnerability Summary for Week of 7 August
The Cybersecurity & Infrastructure Security Agency has released its weekly summary of new vulnerabilities culled from NIST's National Vulnerability Database. It includes the usual array of issues, some with CVSS scores of 9.8 and 9.9. As always, worth a look.
CISA, Vulnerability Summary for the Week of August 7, 2023, bulletin, 14 August 2023. Available online at https://www.cisa.gov/news-events/bulletins/sb23-226.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
US Aims to Further Secure Open Source Software
There was a time, twenty years or so ago, when large software firms, particularly in the US Pacific North-West, were highly dismissive of open source software. However, in today's world, its importance cannot be over-stated - the vast majority of software stacks are either completely or partially based on open source. In fact, by some estimates, open source underpins 96% of the world's software and is a major public good, not to mention a major foundry for innovation.
However, open source is not without its risks - who can forget the Heartbleed vulnerability in OpenSSL, or the log4j vulnerability of late 2021? Both of these highlight the exent to which commercial vendors are highly reliant on open source projects, yet contribute little or nothing to the costs of development and maintenance. OpenSSL was deployed by virtually every commercial UNIX vendor, yet they contributed nothing to its maintenance - a situation which, fortunately, changed dramatically following the adverse publicity generated, while the log4j vulnerability was first reported by a software engineer at Alibaba - a corporation with market capitalization of $US348 billion at the time - which had contributed nothing to the Apache Foundation's maintenance costs.
As a result, there are increasing concerns that the current open source development model may not be sustainable, with a number of codebases relying on open source projects that had no development activity and no user updates in the preceding two years - suggesting that these projects are no longer being maintained at all.
Earlier this year, the National Security Advisor to the White House, Jake Sullivan, hosted a one-day meeting of major software industry companies to discuss initiatives to improve open source security, and now the Cybersecurity and Infrastructure Security Agency, the Office of the National Cyber Director, the National Science Foundation, the DoD's Advanced Research Projects Agency and the Office of Management and Budget have announced a Request for Information, seeking industry input on where the US government should prioritize efforts to secure open source software. This initiative will integrate the National Cybersecurity Strategy's focus on open source with CISA's Secure by Design efforts.
Over the last year, the interagency Open Source Software Security Initiative (OS3I) working group has identified several focus areas, such as reducing the proliferation of memory unsafe programming languages (which we have seen bear fruit with the incorporation of support for Rust in the Linux kernel and elsewhere); designing implementation requirements for secure and privacy-preserving security attestations; and identifying new focus areas for prioritization. The RFI is intended to further that last area by identifying areas most appropriate to focus government priorities, and addressing critical questions such as:
- How should the Federal Government contribute to driving down the most important systemic risks in open-source software?
- How can the Federal Government help foster the long-term sustainability of open-source software communities?
- How should open-source software security solutions be implemented from a technical and resourcing perspective?
The RFI process will engage with interested parties in three phases:
- Phase I - Addressing Respondent Questions About this RFI (which can be sent to OS3IRFI@ncd.eop.gov by 18 August 2023)
- Phase II - Submission of Responses to the RFI by Interested Parties, which will conclude on 10 October 2023
- Phase III - Government Review
The RFI provides additional guidance for potential respondents, including questions which they should address and a list of potential areas and sub-areas of focus.
In the CISA news release, the authors make the point that "The federal government is one of the largest users of open source software in the world, and we must do our part to help secure it. This requires widescale efforts to help uplift the level of security in the open source ecosystem." They then go on to compare this effor to President Eisenhower's Federal Aid Highway Act of 1956, which authorized $US25 billion of funding to build 41,000 miles of highways over the next decade; the result, according to one report, was that "every $1 spent returned more than $6 in economic productivity".
The scale of this effort may be smaller, but considering the contribution of open source software projects to the global economy and the current level of losses due to cyber-attacks, the return on investment may be even higher. And the authors do not expect the government to carry the economic can, pointedly remarking that, "We envision an ecosystem in which creating secure open source code and regularly assessing the security of existing open source code is the norm rather than an added burden. As part of this, software manufacturers that consume open source software should contribute back to the security of the open source software they depend upon".
Goldstein, Eric and Camille Stewart Gloster, We Want Your Input to Help Secure Open Source Software, news release, 10 August 2023. Available online at https://www.cisa.gov/news-events/news/we-want-your-input-help-secure-open-source-software.
Office of the National Cyber Director, Open-Source Software Security: Areas of Long-Term Focus and Prioritization, Request for Information (RFI), 10 August 2023. Available online at https://www.regulations.gov/document/ONCD-2023-0002-0001.
Synopsis Inc., 2023 Open Source Security and Risk Analysis Report, technical report, 16 February 2023. Available online at https://www.synopsys.com/software-integrity/resources/analyst-reports/open-source-security-risk-analysis.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Phishing Email Infection Chain Uses Rusty Injector
A phishing campaign analysed by FortiGuard Labs researchers has revealed the use of a new injector as part of its infection chain. The injector, which is written in the Rust programming language, allows the attackers to base64-encode its shellcode payload and then encrypt it with their choice of AES, RC4 or LZMA in order to evade detection.
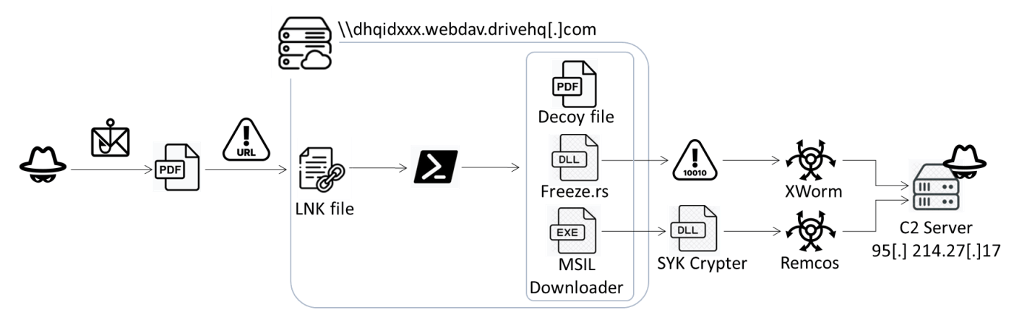
The infection chain - the injector is derived from the "Freeze.rs" Red Team tool. (image credit: FortiGuard Labs)
The attack is delivered via a malicious PDF attachment to a phishing email; the PDF uses a blurred image to lure the victim into clicking a button, which reads "View Document on Desktop", in front of it. Clicking the button causes the victim's system to download a malicious HTML file; rather than simply using JavaScript to download a malware payload - an action that could easily be spotted by EDR tools - the file uses the search-ms protocol to trigger a search for a specific file on a remote cloud storage server provided by DriveHQ.
While this file displays a PDF file icon, it is actually a .LNK file which executes a PowerShell script. This, in turn, uses regsvr32 to launch the injector from a file called doc.dll. The injector starts by displaying a decoy file, T.pdf, which contains the unblurred text the user expects, executes AA.exe and then force-closes all File Explorer windows.
The doc.dll injector creates a notepad.exe process, then decompresses or decrypts and base64-decodes the shellcode, injecting it into that process; this mirrors the behaviour of a red team tool called "Freeze.rs", which was only launched in May, not long before this campaign started. The shellcode uses code to bypass the Windows Antimalware Scan Interface (AMSI) and Windows Lockdown Policy (WLDP) before executing XWorm, a .NET remote access trojan which is capable of enumerating device information, keystroke logging, screenshot capture and remotely controlling the victim system.
The other file, AA.exe, is a downloader programmed in Microsoft Intermediate Language (MSIL) which downloads an obfuscated SYK Crypter carrying a payload which is ultimately decrypted and injected into a process to run the Remcos RAT (actually, a legitimate remote access utility). The AA.exe downloader also remains persistent, by being copied into the "Startup" folder.
Given the extensive detection evasion techniques employed in this campaign, it will prove difficult for anti-malware and EDR tools to respond to it. As always, we have to rely on the user as the last line of defence, alerting them to the use of a button in front of a blurred image to lure them into download the malware. Genuine business documents, such as purchase orders and invoices, simply do not work this way - so don't fall for the lure!
Lin, Cara, Attackers Distribute Malware via Freeze.rs And SYK Crypter, blog post, 9 August 2023. Available online at https://www.fortinet.com/blog/threat-research/malware-distributed-via-freezers-and-syk-crypter.
Citizen Lab Uncovers Classic Crypto Vulnerability in Tencent Sogou Input Method
While this particular vulnerability only exists in a virtual keybard for inputting Chinese ideographic characters on Windows, Android and iOS, it carries a lesson for all of us. An analysis of the Tencent Sogou Input Method conducted by University of Toronto's Citizen Lab turned up a classic vulnerability in its "EncryptWall" home-spun encryption system. Given that Sogou Input Method - a predictive keyboard which uses the Wubi 5-stroke character model - has over 455 million monthly active users and accounts for 70% of Chinese input method users, the security of its encryption system is important for users who wish to avoid surveillance.
The Citizen Lab researchers discovered that the EncryptWall system uses its own home-spun method to encrypt requests which are sent to the EncryptWall API endpoints over conventional HTTP protocol. In other words, rather than using HTTPS, which operates using the TLS protocol to encrypt its entire payload - both headers and bodies - Encryptwall tunnels its encrypted traffic over unencrypted HTTP POST requests. The encryption is performed using 256-bit AES (probably 128-bit AES would be fine) with the AES key protected using 1024-bit RSA (probably not strong enough) with PKCS#1.5 padding.
The major vulnerability is in the implementation of AES, which is done using cipher block chaining (CBC) mode. The way this is done renders it vulnerable to a padding oracle attack - an attack which was discovered back in 2002 by Vaudenay. In this attack - a type of chosen ciphertext attack - the attacker is able to send datagrams to a system and examine the returned error codes or messages to see whether they indicate a decryption error or a padding error - and thereby discover the correct key and then the message contents.
It turns out that the iOS implementation of EncryptWall is not vulnerable, for the simple reason that its POST requests are all sent over TLS, which fixed the padding oracle vulnerability several versions ago. However, both the Windows and Android versions are vulnerable.
The lesson for users is obvious: since the researchers disclosed the vulnerability to Tencent, a fix is available and users should update to version 13.7 for Windows, 11.26 for Android and 11.25 for iOS. For software developers, the lesson is an old one: don't try to roll your own cryptographic schemes! It would have been much simpler for the Tencent developers to simply encapsulate their API traffic in TLS, since they would not have had to develop their own crypto implementation - but it would have been more secure, too, since TLS fixed the problem only a year or so after it was discovered, i.e. in 2003.
Knockel, Jeffrey, Zoë Reichert and Mona Wang, “Please do not make it public”: Vulnerabilities in Sogou Keyboard encryption expose keypresses to network eavesdropping, technical report, 9 August 2023. Available online at https://citizenlab.ca/2023/08/vulnerabilities-in-sogou-keyboard-encryption/.
Vaudenay, Serge, Security Flaws Induced by CBC Padding: Applications to SSL, IPSEC, WTLS..., Advances in Cryptology - EUROCRYPT 2002, pp. 534–545. Available online at http://link.springer.com/chapter/10.1007/3-540-46035-7_35.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Health, Education Sectors Targeted by New Ransomware
The ransomware world seems to be somewhat conflicted over whether or not to exploit the healthcare sector; a few groups disavow attacks on sensitive and non-profit sectors such as education and healthcare, while others, such as Cl0p, have unabashedly run highly-targeted campaigns against the healthcare industry - 77% of Cl0p's 2021 attack attempts were on the sector, according to HC3.
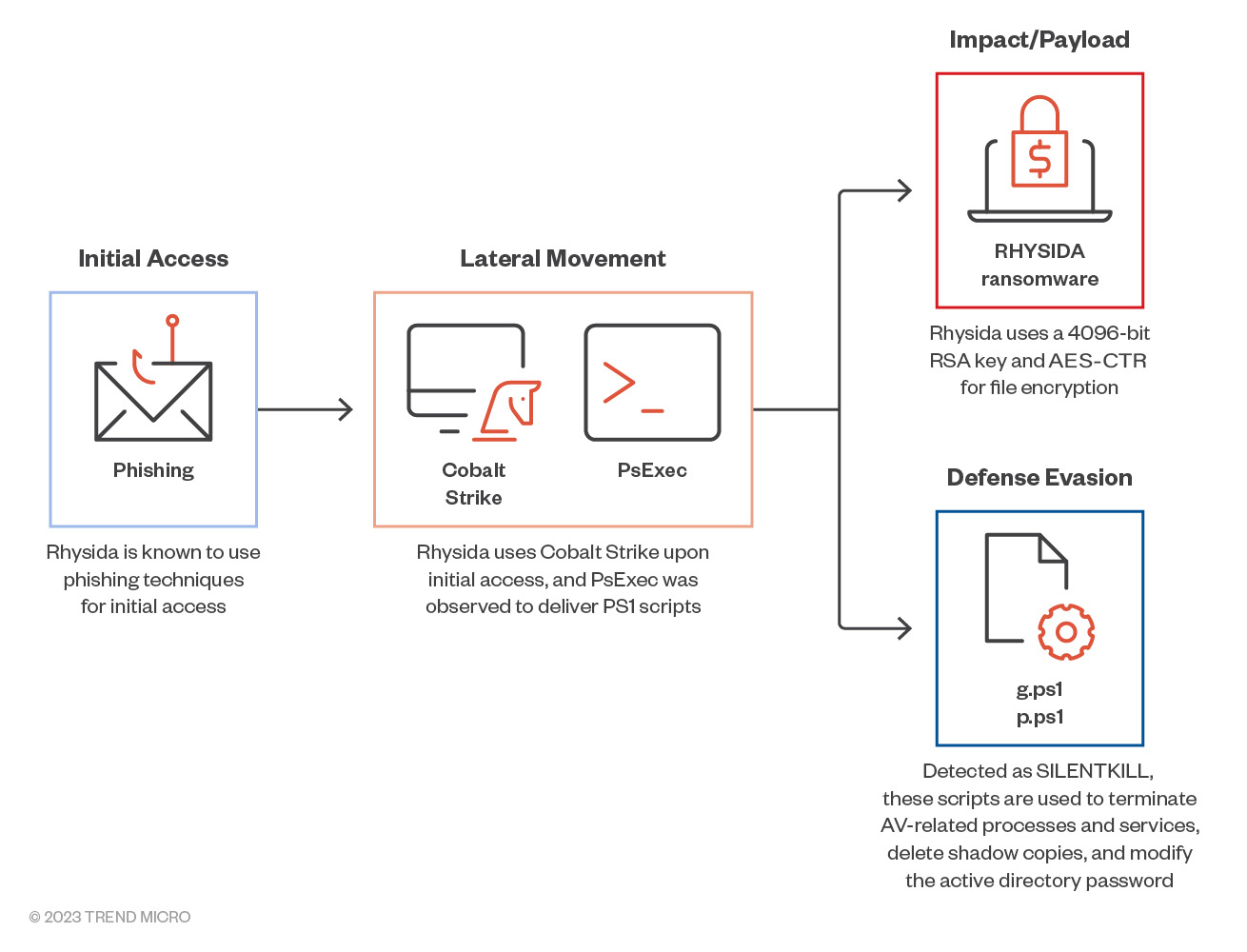
The Rhysida ransomware infection chain (image credit: Trend Micro)
Now the Health Sector Cybersecurity Coordination Center (HC3) has released a sector alert on a new ransomware-as-a-service (RaaS) group which has emerged since May of this year, utilizing phishing attacks and the Cobalt Strike post-exploitation framework to deploy their ransomware, which is known as Rhysida (for a genus of centipede which the group seems to use as their logo). The use of phishing, followed by Cobalt Strike for lateral movement and dropping payloads into victim networks, is a similar TTP to those Black Basta and FIN7 have previously used.
Rhysida encrypts victims' files using the ChaCha20 algorithm, with the key secured by 4096-bit RSA encryption, but seems to lack some basic ransomware functionality, such as disabling the volume shadow copy service and ensuring its persistence through multiple mechanisms. After performing encryption, Rhysida drops a ransom note in each directory, in the form of a PDF document - which suggests that the group is not targeting command-line-oriented servers as these would not be able to display the PDF ransom note.
Victims are threatened with public distribution of exfiltrated information, and instructed to contact the attackers via their Tor-based 'support' site, to make payment of a ransom via Bitcoin.
The group targets a number of industries - mostly in the education and manufacturing sectors, although its TTP's indicate that it is likely to turn to the healthcare sector. Most of its victims to date have been in Western Europe, North and South America and Australia; the fact that it seems to avoid the CIS countries suggest a Russian affiliation.
Trend Micro researchers have also been tracking this group, and their analysis indicates a perhaps slightly later variant of the ransomware, using AES in counter mode for encryption, and with the addition of defense evasion techniques such as deletion of volume shadow copies and termination of antivirus processes and services. In short, this malware seems to be evolving fairly rapidly.
Both the HC3 and Trend Micro reports provide suggested mitigations and a mapping to the MITRE ATT&CK framework; the Trend Micro report also contains IOC's.
Health Sector Cybersecurity Coordination Center (HC3), Clop Allegedly Targets Healthcare Industry in Data Breach, sector alert, 22 February 2023. Available online at https://www.hhs.gov/sites/default/files/clop-allegedly-targeting-healthcare-industry-sector-alert.pdf.
Health Sector Cybersecurity Coordination Center (HC3), Rhysida Ransomware, sector alert, 4 August 2023. Available online at https://www.hhs.gov/sites/default/files/rhysida-ransomware-sector-alert-tlpclear.pdf.
Trend Micro Research, An Overview of the New Rhysida Ransomware Targeting the Healthcare Sector, blog post, 9 August 2023. Available online at https://www.trendmicro.com/en_us/research/23/h/an-overview-of-the-new-rhysida-ransomware.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
It's That Day Again . . .
It's Microsoft Patchday - the second Tuesday of the month (Wednesday for those of us on the leading side of the International Date Line) - and the Redmondites have served up a major update this month, fixing 74 CVE's and two advisories and requiring a heart-stoppingly-long no-video-out reboot of my Windows 11 machine.
The first of the two advisories is termed a 'defense-in-depth' update for Office which prevents exploitation of a remote code execution vulnerability leading to the Windows Search security feature bypass vulnerability (CVE-2023-36884) which was being actively exploited in the wild. The other fixes a missing resource section for a module of the hypervisor-protected code integrity tool (hvciscan_amd64.exe and hvciscan_arm64.exe).
There are also fixes for four vulnerabilities with CVSS 3.1 base scores of 9.8:
- a privilege escalation vulnerability in Exchange Server (CVE-2023-21709)
- a remote code execution vulnerability in MSMQ (CVE-2023-35385)
- another remote code execution vuln in MSMQ (CVE-2023-36910)
- a third (!) remote code execution vulnerability in MSMQ (CVE-2023-36911)
You know what to do . . .
MSRC, August 2023 Security Updates, security update guide, 9 August 2023. Available online at https://msrc.microsoft.com/update-guide/releaseNote/2023-Aug.
Adobe Releases Security Updates, Too
While you're updating, Adobe has released a number of updates to address multiple vulnerabilities. The relevant security bulletins are:
- Adobe Acrobat and Reader: APSB23-30
- Adobe Commerce: APSB23-42
- Adobe Dimension: APSB23-44
- Adobe XMP Toolkit SDK: APSB23-45
Adobe Commerce is, of course, based on the open-source Magento e-commerce merchant server, so users of that protidct should plan to update too.
UK Voter Information Leaked
The UK's Electoral Commission has disclosed a massive breach which occurred almost two years ago - and then wasn't discovered for a year. The attack was discovered in October 2022 and was reported almost immediately to the Information Commissioner's Office and the National Crime Agency. For a year prior, the still-unidentified threat actor had access to the names and addresses of 40 million voters in the UK who were registered from 2014 onwards.
However, the breach was only publicly disclosed this week, and has done enormous damage to the reputation of the Electoral Commission, although it would not have affected vote-counting, which remains a manual, paper-based process. On the other hand, if the responsible threat actor was associated with a nation state, the information gained could conceivably have been used in influence campaigns.
Asked why it took so long to disclose the breach, an Electoral Commission spokesperson said the Commission had needed to "remove the actors and their access to our system, assess the extent of the incident, liaise with the National Cyber Security Centre and ICO, and put additional security measures in place before we could make the incident public", adding that the attack "used a sophisticated infiltration method, intended to evade our checks" - which explains why it had evaded detection for so long, and reinforces suggestions of a state-affiliated advanced persistent threat.
Mason, Rowena and Hibaq Farah, Electoral Commission apologises for security breach involving UK voters’ data, The Guardian, 9 August 2023. Available online at https://www.theguardian.com/technology/2023/aug/08/uk-electoral-commission-registers-targeted-by-hostile-hackers.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cryptominer Targets Linux Systems Via Redis
A new and 'improved' variant of the SkidMap malware has been detected by Trustwave, using a honeypot in Central Europe. SkidMap was first reported by Trend Micro almost four years ago; its primary function is cryptomining, although it could be turned to other objectives by its operator.
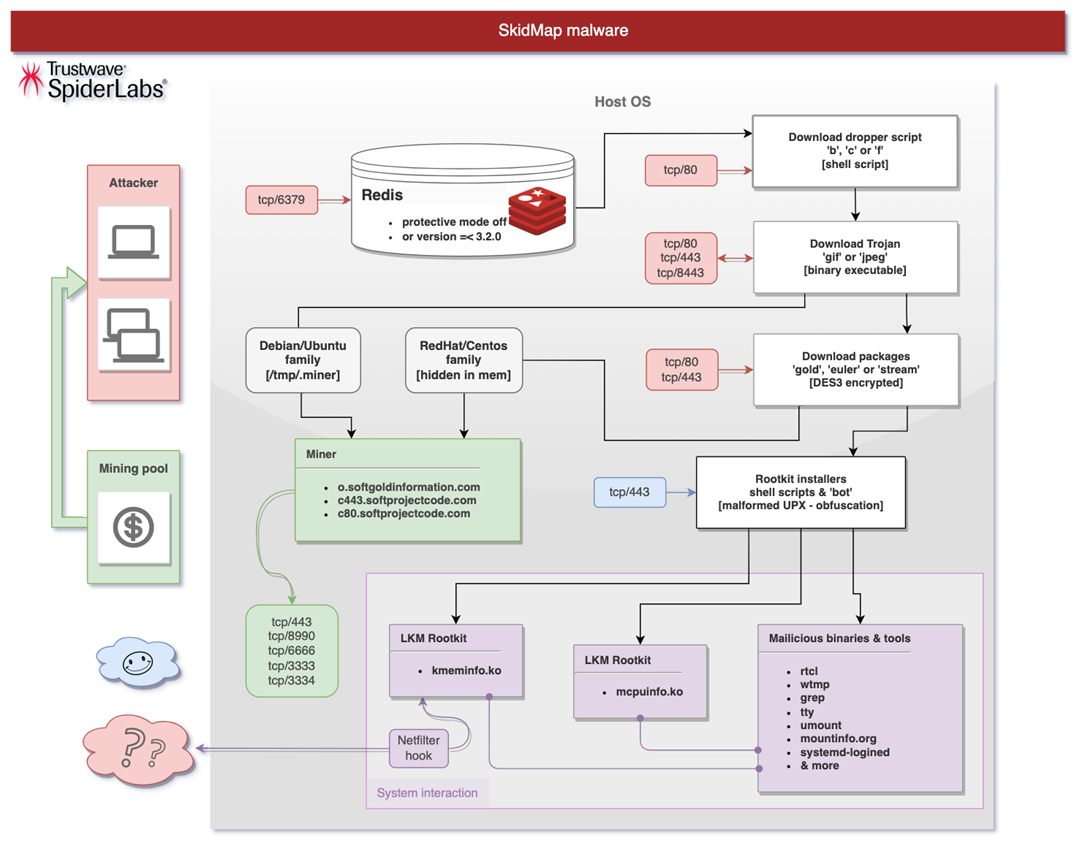
The SkidMap infection chain (image credit: Trustwave)
This latest variant initially infects its target via insecure Redis server installations - either versions prior to version 3.2.0 or instances running with protective mode disabled. The initial infection creates variables which contain base64-encoded cron jobs; when these run they will use either curl or wget to download and tun a dropper script.
The dropper, in turn, downloads an ELF executable called gif into /var/lib. When tun, this installs some SSH keys on the root account, disables SELinux, and then becomes persistent via the creation of more cron jobs; every hour the system creates a reverse shell which contacts the attackers' command and control server. The gif executable checks for various /etc/*-release text files to ascertain which Linux distribution it is running on, and depending on what it finds, it will download one of three different packages: 'gold', 'stream' or 'euler'.
Each package runs a series of shell scripts, cleaning up log entries which would indicate the infection and generally preparing the system for installation of a rootkit which consists of executables and Linux kernel modules. This will hide the operation of the ultimate payload, which is a cryptominer, but the rootkit modules have advanced functionality which go well beyond this - for example, allowing reconfiguring Netfilter to intercept network datagrams.
Once infection is complete, this malware is going to prove difficult to detect - it certainly evades ClamAV and Rkhunter, although Lynis and Chkrootkit do show indications of its presence. A better approach is to put some effort into securing vulnerable Redis installations in the first place, by installing version 3.2.0 or later, setting a strong password and using network segmentation to limit external access.
Zdonczyk, Radoslaw, Honeypot Recon: New Variant of SkidMap Targeting Redis, blog post, 2 August 2023. Available online at https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/honeypot-recon-new-variant-of-skidmap-targeting-redis/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
YAPC - Yet Another PaperCut Vulnerability
The PaperCut enterprise management system has been a high priority for threat actors for the last few months, as a series of vulnerabilities have allowed its exploitation by groups like Cl0p and LockBit, who have used it for information exfiltration prior to extortion demands.
Now researchers at Horizon3.ai have disclosed a new critical vulnerability, CVE-2023-39143. This is a directory traversal vulnerability which allows unauthenticated attackers to read, delete and upload arbitrary files to a vulnerable PaperCut MF/NG server, with the possibility of remote code execution if iinstalled on Windows with the external device integration setting enabled - which it is, by default, on some PaperCut versions such as PaperCut NG Commercial or PaperCut MF.
A simple command can check whether a PaperCut server is not patched and is running on Windows:
curl -w "%{http_code}" -k --path-as-is "https://<IP>:<port>/custom-report-example/..\..\..\deployment\sharp\icons\home-app.png"
Horizon3.ai notified PaperCut, and customers are advised to upgrade to the latest PaperCut version, that is, version 22.1.3 or later. If an upgrade cannot be installed, the most appropriate mitigation is to configure an allowlist of IP addresses which can access the PaperCut server.
What's the old saw? "If you see one rat, you probably have a lot more" - and the same applies to vulnerabilities.
Sunkavally, Naveen, CVE-2023-39143: PaperCut Path Traversal/File Upload RCE Vulnerability, blog post, 4 August 2023. Available online at https://www.horizon3.ai/cve-2023-39143-papercut-path-traversal-file-upload-rce-vulnerability/.
Deep Learning Acoustic Attack Learns Keyboard Text With 95% Accuracy
That clacking sound your keyboard makes as you type? It could be leaking passwords to a nearby smartphone, or even via a Zoom or Skype session with others. In fact, it could even work with a smartwatch.
In a paper presented at the 2023 European Symposium on Security and Privacy Workshops, three UK researchers detailed an acoustic side channel attack which uses a deep learning model to classify laptop keystrokes. When trained on keystrokes recorded by a nearby smartphone, the classifier achieved an accuracy of 95%, the highest accuracy seen without the use of a language model (which would use the redundancy of human language to achieve near-100% accuracy). When trained on keystrokes recorded over Zoom, the attack still managed an accuracy of 93%.
The researchers performed initial training by pressing each alphanumeric key on a 16-inch Macbook Pro 25 times, recording the sound each made. From this, they extracted the waveform of the isolated keystrokes and produced spectrograms - which chart the intensity of each frequency - and used these to train the CoAtNet image classifier, tweaking the parameters until they had optimized the classification accuracy. Since all recent Macbooks use the same keyboard and presumably sound similar, the attack could work against other users' machines.
The researchers' results provide further evidence that passwords are an increasingly weak form of authentication. While they suggest some mitigations, including varying typing techniques, making use of the Ctrl and Shift keys, backspacing and, obviously, using randomized passphrases. I would add that the use of a password safe to paste a random password into an on-screen form would provide a particularly strong defence. Nevertheless, it is increasingly obvious that we need to move to cryptographic authentication techniques such as security keys and passkeys.
Harrison, Joshua, Ehsan Toreini and Maryam Mehnezhad, A Practical Deep Learning-Based Acoustic Side Channel Attack on Keyboards, workshop presentation paper, 3 August 2023. Available online at https://arxiv.org/abs/2308.01074.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Boodhound Renamed, New Code Base
Bloodhound, the pen testing tool for Active Directory, has been revamped with a new name and a new code base. The application has two data collection tools, called SharpHound and AzureHound, which collect data from domain controllers and domain-joined Windows systems, such as:
- Security group memberships
- Domain trusts
- Abusable rights on Active Directory objects
- Group Policy links
- OU tree structure
- Several properties from computer, group and user objects
- SQL admin links
- Members of local admin, remote desktop, DCOM and remote management groups
- Active sessions
This data can then be loaded into the Bloodhound GUI for analysis, allowing exploration of possible attack paths (by both red teams and blue teams). While originally written as an open source project, Bloodhound was also commercialized and extended by SpectorOps to produce the SaaS Bloodhound Enterprise. However, over time, the two code bases diverged - in fact, the Enterprise version has a completely different architecture - and this increased the development workload substantially, since adding features meant writing, testing and maintaining two different versions of the same code.
However, SpecterOps is now (as of 8 August) releasing Bloodhound CE (Community Edition), which is based on the BloodHound Enterprise code base. This will eliminate a lot of duplicate effort in maintaining, supporting and extending the common code base.
Hinck, Stephen, Your new best friend: Introducing BloodHound Community Edition, blog post, 2 August 2023. Available online at https://posts.specterops.io/your-new-best-friend-introducing-bloodhound-community-edition-cb908446e270.
CISA Reports on 2022's Most-Exploited Vulnerabilities
A new report from the Cybersecurity & Infrastructure Security Agency, along with international partners, details the top 12 vulnerabilities exploited by threat actors in 2022 and draws lessons from them. Among the key findings:
- Threat actors exploted older software vulns more often than recently-disclosed vulnerabilities, taking advantage of proof-of-concept code to exploit victims who had delayed patching
- However, threat actors had the most success exploiting known vulns within the first two years after public disclosure - after that time, patches and upgrades reduced their success rates
- Threat actors seem to prioritize development of exploits for severe and globally prevalent CVE's, especially if they are more prevalent in their specific targets' networks. Only the more sophisticated actors also develop tools to exploit other vulnerabilities
The report encourages a number of mitigations for both developers and end users, including adoption of secure-by-design principles - but the most obvious less is that end user organizations need to accelerate their patch management programs.
CISA, 2022 Top Routinely Exploited Vulnerabilities, cybersecurity advisory, 3 August 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-215a.
Google Adds New Privacy Tracking Tools
Last year, Google introduced a new page called Results about you (https://goo.gle/resultsaboutyou) which will report search results which contain your personal phone number, home address or email. Now the page has been updated wth a new dashboard which will allow users to request remove of those results from Google Search, and will also provide notifications when new search results containing contact info turn up.
The page is initially available in the Google app, in the US, in English only. However, it will roll out to new locations and languages in the coming months.
Google has also announced that it will make it easier for user to remote explicit or intimate personal images from search results - an increasingly common problem for many young people today as they lose control of shared images which can then end up on web sites.
Romain, Danielle, New privacy tools to help you stay safe and in control online, Google Keyword, 3 August 2023. Available online at https://blog.google/products/search/new-privacy-tools/.
Clancy, Elizabeth Mary and Boanca Klettke, 20% of young people who forwarded nudes say they had permission – but only 8% gave it. Why the gap?, The Conversation, 4 August 2023. Available online at https://theconversation.com/20-of-young-people-who-forwarded-nudes-say-they-had-permission-but-only-8-gave-it-why-the-gap-207913.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
People Can't Reliably Distinguish Deepfakes
Finance departments everywhere are awake to the possibility of whaling attacks, in which a forged email, apparently from the CEO or another senior manager directs a significant payment to a new bank account. Such attacks can be highly profitable for cybercriminals, and highly damaging to the victims - in 2019, the US subsidiary of Japanese publisher Nikkei lost $US29 million to a whaling scam, while an earlier attack on European electrical manufacturer Leoni AG netted the attackers €44 million.
I might wish that defenders implemented a really strong control in the form of cryptographically signed emails; however, while S/MIME is reasonably easy to set up in an Active Directory domain, and there is always PGP, in practice this is rarely done. The default defence is to require an out-of-band confirmation that the email is authentic - for example, by calling the manager who requested this funds transfer and getting them to confirm the request. However, scammers have become proactive in defeating this safeguard: using captured samples of the manager's voice - obtained from analyst briefings, conference presentations and elsewhere - they train a machine learning model and then use an app to convincingly emulate their voice characters, in a process known as deep faking.
Now comes research showing that deepfake audio can trick people, even when they are expecting to hear AI-processed speech. Researchers at University College London asked over 500 people to identify speech deepfakes among multiple audio clips, using generic sentences in both English and Mandarin. While the subjects were able to correctly classify the deepfakes and authentic speech approximately 70% of the time, it is likely that real-world performance of this task is much worse, since people will not be primed to the fact that they could be hearing an artificial voice, and are likely to be caught off-guard.
However, this study did not challenge the listeners to verify a particular person as opposed to a deepfake, so there remains some hope.
Hsu, Jeremy, AI voices are hard to spot even if you know audio might be a deepfake, New Scientist, 2 August 2023. Available online at https://www.newscientist.com/article/2385752-ai-voices-are-hard-to-spot-even-if-you-know-audio-might-be-a-deepfake/.
NSA Releases Hardening Guide for Cisco Next-Gen Firewalls
The National Security Agency has released a cybersecurity technical report which provides best-practices guidance to systems and network administrators on configuring and hardening Cisco Secure Firewall (previously known as Cisco Firepower Threat Defense) appliances.
These next-generation firewalls (one wonders what we are going to call the next next generation of firewalls) combine filtering at both the network and application layers. They also provide URL filtering, user authentication, malware protection and intrusion prevention as well as Cisco's Application Visibility and Control for traffic shaping and congestion management.
The 36-page guide covers hardening of the FXOS operating system as well as access control and intrusion detection policies, SSL policies, malware and file policies and secure VPN settings.
NSA, Cisco Firewower Hardening Guide, cybersecurity technical report, August 2023. Available online at https://media.defense.gov/2023/Aug/02/2003272858/-1/-1/0/CTR_CISCO_FIREPOWER_HARDENING_GUIDE.PDF.
Cozy Bear Goes Phishing in Teams
A new report from Microsoft Threat Intelligence reveals that Cozy Bear - which Microsoft tracks as Midnight Blizzard, but is also known as NOBELIUM and APT29 - has been conducting a phishing campaign in search of the credentials of both government and non-government organization employees around the world. Cozy Bear is associated with the SVR, the Foreign Intelligence Service of the Russian Federation, and is focused on cyber-espionage.
In this particular campaign, the threat actors compromise the Microsoft 365 accounts of small businesses, rename them, add a new onmicrosoft.com subdomain and then use these to send Microsoft Teams chat messages while masquerading as a technical support or security team. They will then try to social-engineer the victim into approving a multi-factor authentication prompt.
This works because the messages will come from the legitimate onmicrosoft.com domain, which Microsoft 365 automatically uses when customers do not create a custom domain.
To date, the campaign has affected fewer than 40 organizations world-wide, all of whom have been notified by Microsoft.
Microsoft Threat Intelligence, Midnight Blizzard conducts targeted social engineering over Microsoft Teams, blog post, 2 August 2023. Available online https://www.microsoft.com/en-us/security/blog/2023/08/02/midnight-blizzard-conducts-targeted-social-engineering-over-microsoft-teams/.
Yet Another Mozilla Update
The Mozilla Foundation has released yet another round of security updates for its browsers. Many of the fixed vulnerabilities are high-severity. The affected products, with links to their related advisories are:
- Firefox 116: https://www.mozilla.org/en-US/security/advisories/mfsa2023-29/
- Firefox ESR 115.1: https://www.mozilla.org/en-US/security/advisories/mfsa2023-31/
- Firefox ESR 102.14: https://www.mozilla.org/en-US/security/advisories/mfsa2023-30/
You know what to do: Help -> About Firefox, and install the update.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.