Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Health, Education Sectors Targeted by New Ransomware
The ransomware world seems to be somewhat conflicted over whether or not to exploit the healthcare sector; a few groups disavow attacks on sensitive and non-profit sectors such as education and healthcare, while others, such as Cl0p, have unabashedly run highly-targeted campaigns against the healthcare industry - 77% of Cl0p's 2021 attack attempts were on the sector, according to HC3.
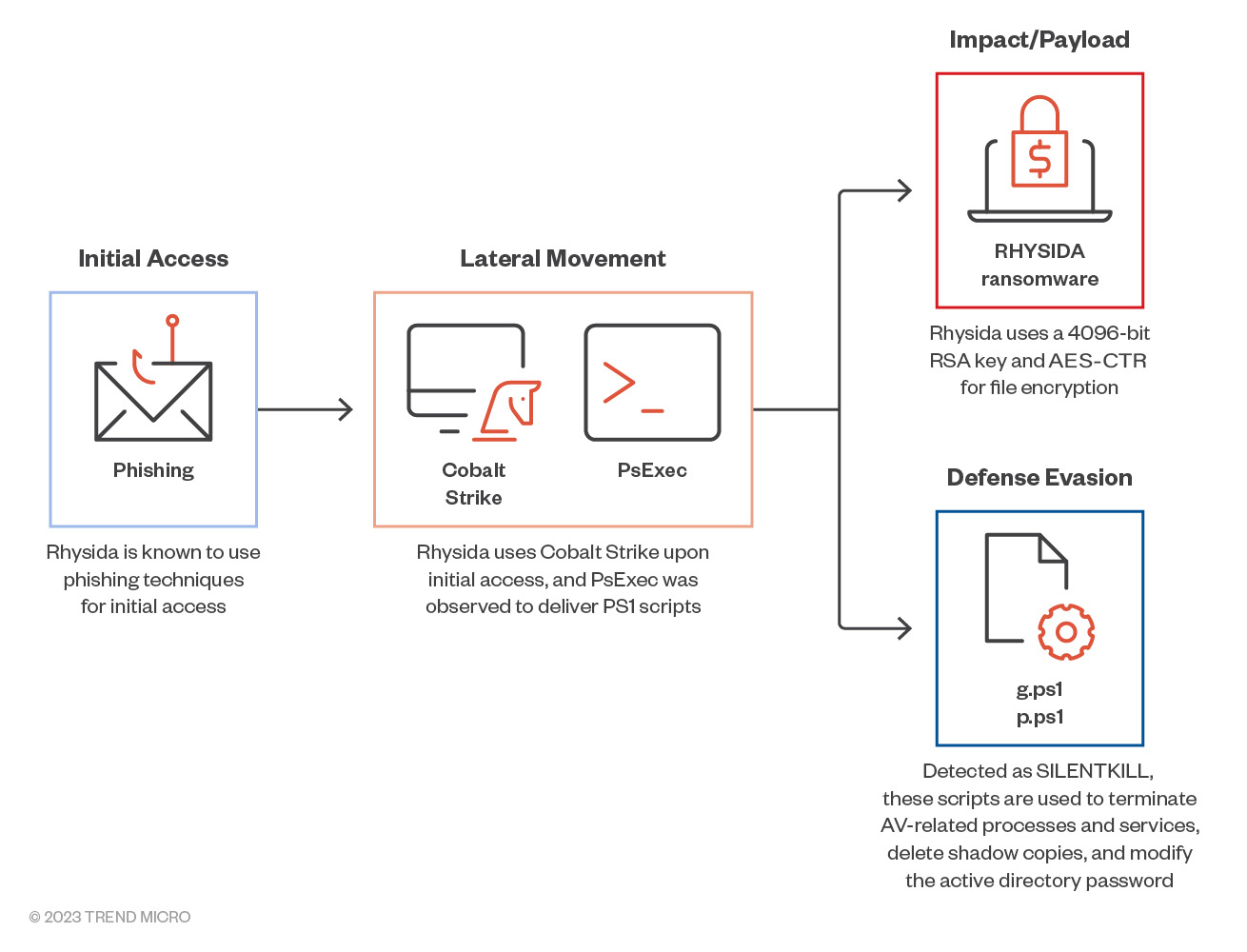
The Rhysida ransomware infection chain (image credit: Trend Micro)
Now the Health Sector Cybersecurity Coordination Center (HC3) has released a sector alert on a new ransomware-as-a-service (RaaS) group which has emerged since May of this year, utilizing phishing attacks and the Cobalt Strike post-exploitation framework to deploy their ransomware, which is known as Rhysida (for a genus of centipede which the group seems to use as their logo). The use of phishing, followed by Cobalt Strike for lateral movement and dropping payloads into victim networks, is a similar TTP to those Black Basta and FIN7 have previously used.
Rhysida encrypts victims' files using the ChaCha20 algorithm, with the key secured by 4096-bit RSA encryption, but seems to lack some basic ransomware functionality, such as disabling the volume shadow copy service and ensuring its persistence through multiple mechanisms. After performing encryption, Rhysida drops a ransom note in each directory, in the form of a PDF document - which suggests that the group is not targeting command-line-oriented servers as these would not be able to display the PDF ransom note.
Victims are threatened with public distribution of exfiltrated information, and instructed to contact the attackers via their Tor-based 'support' site, to make payment of a ransom via Bitcoin.
The group targets a number of industries - mostly in the education and manufacturing sectors, although its TTP's indicate that it is likely to turn to the healthcare sector. Most of its victims to date have been in Western Europe, North and South America and Australia; the fact that it seems to avoid the CIS countries suggest a Russian affiliation.
Trend Micro researchers have also been tracking this group, and their analysis indicates a perhaps slightly later variant of the ransomware, using AES in counter mode for encryption, and with the addition of defense evasion techniques such as deletion of volume shadow copies and termination of antivirus processes and services. In short, this malware seems to be evolving fairly rapidly.
Both the HC3 and Trend Micro reports provide suggested mitigations and a mapping to the MITRE ATT&CK framework; the Trend Micro report also contains IOC's.
Health Sector Cybersecurity Coordination Center (HC3), Clop Allegedly Targets Healthcare Industry in Data Breach, sector alert, 22 February 2023. Available online at https://www.hhs.gov/sites/default/files/clop-allegedly-targeting-healthcare-industry-sector-alert.pdf.
Health Sector Cybersecurity Coordination Center (HC3), Rhysida Ransomware, sector alert, 4 August 2023. Available online at https://www.hhs.gov/sites/default/files/rhysida-ransomware-sector-alert-tlpclear.pdf.
Trend Micro Research, An Overview of the New Rhysida Ransomware Targeting the Healthcare Sector, blog post, 9 August 2023. Available online at https://www.trendmicro.com/en_us/research/23/h/an-overview-of-the-new-rhysida-ransomware.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.