Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Four Corners Cybercrime Doco Drops
As we predicted, the Australian Broadcasting Commission has made available the latest episode of its flagship current affairs program, Four Corners, on YouTube so that it is available to international viewers. The documentary deals with the nexus between cybercrime and cyberwarfare, and covers attacks in Australia - most notably on Medibank - and in Ukraine.
Four Corners, Cyber Gangs Cracked Open, documentary film, 17 April 2023. Available online at https://www.youtube.com/watch?embed=no&v=4m6Ydx0TGMY.
Alleged Criminals Challenge Evidence From 'Secure' Messaging Service
In a case that could have implications for the use of evidence obtained via implants on smartphones, around 50 alleged criminals are challenging the admissibility of evidence obtained in the Australian Federal Police's Operation Ironside.
Ironside was the Australian end of a joint operation with the FBI (who called it Trojan Shield) and Europol's Task Force Greenlight. The FBI had obtained the 'cooperation' of a developer who had been working on an encrypted messaging device called ANOM for use by criminal networks; in exchange for a reduced sentence he agreed to finish the development and make it available to his criminal customers. However, the customers did not know that the service's proxy servers were copying all messages, along with the related private keys, to FBI-controlled servers, and the FBI was sharing some of these with the AFP.
In this week's Sydney committal hearing, barristers for the defendants will challenge the validity of evidence obtained via these messages. The AFP claimed that they had been granted a "court order to legally monitor the ANOM devices of the individuals in Australia or with a clear nexus to Australia". However, magistrate Robert Williams will now have to decide whether that evidence was legally intercepted. Much hinges on the question of where duplication of of messages took place and whether the devices were connected to a telecommunications network at that time, based on technical testimony by an expert witness who has examined some of the ANOM source code.
In a similar challenge heard before the Supreme Court of South Australia, Justice Adam Kimber held that the Operation Ironside intercepts were legally conducted.
Parkes-Hupton, Heath, Why accused criminals are challenging evidence in Sydney from one of the world's biggest police stings, ABC News, 18 April 2023. Available online at https://www.abc.net.au/news/2023-04-18/accused-criminals-challenge-an0m-app-evidence-in-supreme-court/102107344.
Former FIN7 and Conti Members Join Forces
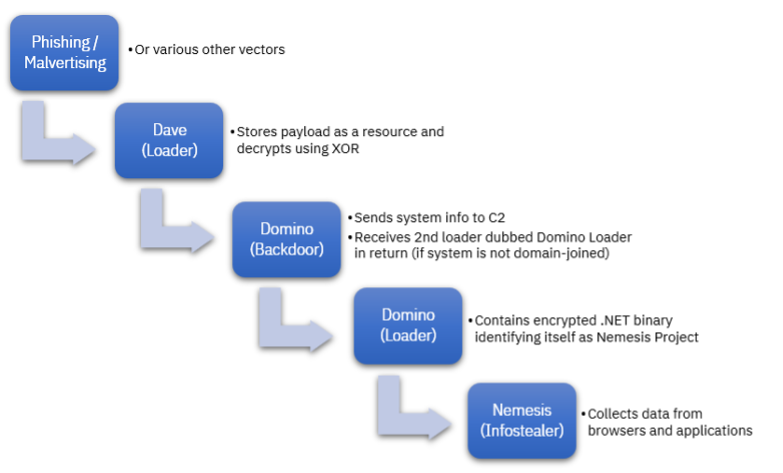
A report from IBM Security X-Force reveals that developers from the FIN7 gang have developed a new backdoor family called (by X-Force) Domino. The Domino code overlaps with the older Lizar malware which cames from the same source. But what makes recent campaigns particularly interesting is that Domino is being deployed using the Dave Loader, suggesting that the campaigns are being run by former members of the Conti ransomware syndicate. Conti fragmented into several factions, including Quantum, Royal, BlackBasta and Zeon.
These factions have used Dave Loader to deliver Cobalt Strike payloads, as well as IcedID and Emotet, which are both used as initial access vectors for subsequent ransomware operations. However, the payload of some recent Dave Loader samples was Domino Backdoor, a DLL which performs basic system enumeration (system name, user names, running processes), sending this back to the group's C2 server. The server will respond with a command which triggers download of a second loader which shares code with Domino (hence, Domino Loader) which in turn decrypts an internal payload which turns out to be a .NET infostealer called Nemesis Project.
(Image credit: IBM Security X-Force)
However, if the victim machine is a domain member, Domino Backdoor contacts a different C2 server, possibly to download a more capable backdoor such as Cobalt Strike which can then be used to pivot against other systems.
The combination of tools in this campaign indicates the fluid nature of cybercrime operations, with groups fracturing and members collaborating to form new syndicates.
Hammond, Charlotte and Ole Villadsen, Ex-Conti and FIN7 Actors Collaborate with New Domino Backdoor, blog post, 14 April 2023. Available online at https://securityintelligence.com/posts/ex-conti-fin7-actors-collaborate-new-domino-backdoor/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cozy Bear Targets NATO, EU in Cyberespionage Campaign
The Polish Military Counterintelligence Service and the CERT Polska team have reported a widespread cyber-espionage campaign targeting foreign ministries and diplomatic entities in NATO member states, the European Union and, to a lesser extent, Africa. Many of the TTP's observed are consistent with the previous activities of APT 29, a.k.a. Cozy Bear or Nobelium, which operates on behalf of the Russian SVR. However, this campaign, which is still ongoing, utilises new software tools.
In all observed cases, the threat actor utilised spear-phishing tactics, with emails carrying invitations to meetings or collaborative documents, apparently from the embassies of European countries. In each case, the email or attached document contained a link to a compromised website containing the ENVYSCOUT script, which uses HTML smuggling to decode a downloaded file to the victim's device. While previous APT 29 campaigns have used .ZIP or .ISO files to package the malware payload and avoid its being stamped with the Mark of the Web, this time .IMG files were also used. A variety of techniques were used to entice the user into running the malware - such as adding lots of spaces to the filename so that its .EXE filetype would not be visible.
The actor's tool delivery flow (Image: CERT.PL)
Three new tools were observed:
- SNOWYAMBER – a tool first used in October 2022, abusing the Notion service to communicate and download further malicious files. Two versions of this tool have been observed.
- HALFRIG – used for the first time in February 2023. This tool is distinguished from the others by the embedded code that runs the COBALT STRIKE tool.
- QUARTERRIG – a tool first used in March 2023, sharing part of the code with HALFRIG. Two versions of this tool were observed.
SNOWYAMBER and QUARTERRIG are downloaders which perform some basic enumeration and, if the victim machine seemed to be of interest, download and run either Cobalt Strike or Brute Ratel. HALFRIG, however, is a loader which contains Cobalt Strike and runs it automatically.
The Polish Military Counterintelligence Service and CERT.PL recomend a number of configuration changes to defend against this and similar campaigns:
- Blocking the ability to mount disk images on the file system. Most users doing office work have no need to download and use ISO or IMG files.
- Monitoring of the mounting of disk image files by users with administrator roles.
- Enabling and configuring Attack Surface Reduction Rules.
- Configuring Software Restriction Policy and blocking the possibility of starting-up executable files from unusual locations (in particular: temporary directories, %localappdata% and subdirectories, external media).
gov.pl, Espionage campaign linked to Russian intelligence services, knowledge base article, 13 April 2023. Available online at https://www.gov.pl/web/baza-wiedzy/espionage-campaign-linked-to-russian-intelligence-services.
Australians Lose $A3.1 Billion to Scams
The latest Targeting Scams report from the Australian Competition and Consumer Commission has revealed that Australians lost a record $A3.1 billion to scams in 2022 - an 80% increase on the previous year. The report, which compiles data reported to the ACCC's Scamwatch, ReportCyber, the Australian Financial Crimes Exchange (AFCX), IDCARE and other government agencies, shows that the highest loss category was investment scams ($A1.5 billion) followed by remote access/tech support scams ($A229 million) and payment redirection scams ($A224 million).
The financial loss is only one dimension; since many victims lose significant amounts - their entire life savings, in some cases - they, their families and their businesses may suffer emotional distress and life disruption.
Although Scamwatch received a lower number of reports this year, the total financial losses increased significantly, with the average loss rising to almost $20,000. Scams are also increasingly difficult to detect, with more sophisticated tactics such as impersonating of official phone numbers, email addresses and websites to the insertion of scam texts in legitimate conversation threats.
ACCC, Targeting scams: Report of the ACCC on scams activity 2022, technical report, 17 April 2023. Available online at https://www.accc.gov.au/about-us/publications/serial-publications/targeting-scams-report-on-scams-activity/targeting-scams-report-of-the-accc-on-scams-activity-2022.
REvil Hacker Breaks Cover, Chats to Reporters
In an intriguing report produced by the Australian Broadcasting Corporation, journalists have chatted to a hacker who claims to be part of the REvil ransomware gang which is believed to be responsible for last year's Medibank data breach. Medibank refused to pay the demanded ransom, and in response the hackers released the medical records of around 2,000 people on their site.
The hacker, who uses the handle, "Kerasid", claims that "Australians are the most stupidest humans alive, and they have a lot of money for no reason - alot of money and no sense at all". When a reporter messaged him, "The medibank hack caused distress to millions of Australians. Does this concern you? ", he replied, "I could not care less" and later stated, "it isn’t wrong in my eyes ".
The chat was part of an investigation undertaken by ABC current affairs program, Four Corners, the report from which will air on ABC TV tonight, 17 April 2023, at 8:32 PM AEST. (Four Corners episodes are often reposted on the ABC News In-depth YouTube channel, and we will post a link in due course.)
The history of the REvil and Conti ransomware gangs is long and murky - both groups appear to have fractured, with new groups inheriting parts of their code base and recruiting new affialiates and initial access brokers. The article, and the TV program, provide an insight into the groups' structures and operations.
Longbottom, Jessica, John Lyons and Jeanavive McGregor, Chatting with a hacker, ABC News, 17 April 2023. Available online at https://www.abc.net.au/news/2023-04-17/cybercrime-hacker-chats-about-medibank-revil-russia-ukraine/102179776.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
It's World Quantum Day!
April 14th is World Quantum Day - an annual celebration promoting public understanding of quantum science and technology around the world. The World Quantum Day web site at https://worldquantumday.org lists 200 events in over 193 cities and 44 countries, so there's bound to be something for everyone.
For cybersecurity and infosec wonks, this is as good a day as any, and better than most, to once again push the need for cryptographic agility - that is, the need to design and implement our systems so that we will be able to replace those public-key crypto algorithms which may (or already have) fallen due to the ability of quantum computers to break them in polynomial time. That's essentially all of the currently-utilised algorithms based on trapdoor problems in involving factorization or the computation of logarithms in a finite field: RSA, ElGamal, Diffie-Hellman Key Agreement, DSA, and their elliptic curve derivatives.
Bear in mind that if somebody already has a quantum computer, they are not going to reveal that fact as it confers a tremendous advantage. And even if "they" don't yet have a quantum crypto-breaking capability, "they" can store away intercepted traffic until they do, at which point they will be able to retrospectively read encrypted traffic, some of which will still be valuable (in so-called "harvest now, decrypt later" (HNDL) schemes. So the only prudent course of action is to assume this is going to be a problem sooner rather than later, and start switching to post-quantum, or quantum-resistant, cryptographic algorithms.
The US Government is already pushing this, with the Quantum Computing Cybersecurity Preparedness Act, which mandates the migration of Federal Government systems to post-quantum crypto algorithms. And the longer we leave it, the faster the change will have to be accomplished - hence the plea for cryptographic agility, which at least lays the groundwork.
Clancy, Charles and Teresa H. Shea, Why the US Needs Quantum-Safe Cryptography Deployed Now, Dark Reading, 14 April 2023. Available online at https://www.darkreading.com/dr-tech/why-the-us-needs-quantum-safe-cryptography-deployed-now.
More Israeli Implants Revealed by Citizen Lab
The Citizen Lab researchers at the University of Toronto's Munk School of Global Affairs and Public Policy have a long track record of sterling work in revealing the activities of state-sponsored and other actors who conduct surveillance and other attacks on journalists and civil rights campaigners. In their latest report, they describe the exploits developed by Israeli spyware vendor QuaDream.
Smartphones are an excellent platform for secure (encrypted, confidential and sometimes anonymized) communications by journalists, civil rights campaigners and NGO workers. Because the traffic generated by smartphone messaging applications are encrypted, usually with reasonably well-designed key exchange protocols, it is effectively impossible for the traditional wire-tapping schemes to work - the traffic can be intercepted but not decrypted, leaving only traffic analysis as a means of attack (and sometimes, not even that).
The only way to intercept communications therefore is by means of an implant - essentially a software keystroke or other logger which is able to capture communications before it is encrypted or after it is decrypted. And so a number of firms - primarily Israeli, for some reason (most notably NSO Group) - specialize in developing such implants which can hook into the iOS and Android mobile OS's in undetectable ways. They also develop exploits which can either trick a victim into installing them - a big hurdle when the targets are sensibly paranoid and security aware - or, better still, infect a system with no user interaction at all: so-called zero-click exploits.
One such company is QuaDream, which markets its "Reign" spyware to government clients, including Singapore, Saudi Arabia, Mexico and Ghana. The company maintains an exceptionally low profile, with no web site and essentially no press coverage. It it wasn't embroiled in a legal dispute with its international marketing partner InReach, requiring the lodging of documents with a court in Cyprus, the company would be essentially invisible.
Microsoft Threat Intelligence recently captured two samples of iOS spyware which they call KingsPawn and attribute, with high confidence, to QuaDream. They passed these samples to Citizen Lab, who analysed them and determined that the first was a loader, intended to exfiltrate basic device information and then download and execute a second payload. The second sample appears to be a full featured spyware payload. The two share common code, indicating they come from the same development team.
The spyware payload has a wide range of surveillance functionality:
- Record audio from calls
- Record from the microphone ("hot mic")
- Take pictures using front & back cameras
- Exfiltrate and remove keychain items
- Generate iCloud 2FA passwords
- Search through device files and databases
- Clean up its own traces
- Track location
Detailed analysis also led to QuaDream's iOS 14 zero-day, zero-click exploit, called ENDOFDAYS. Citizen Lab identified two cases where this was used against targets in North America and Central Asia. It appears that the ENDOFDAYS exploit works by using an XML escape vulnerability in the iCloud calendar; if this is correct, it only requires the attacker to add a calendar event which injects XML data into the target's phone.
Citizen Lab were also able to devise fingerprints and identify over 600 command and control servers and 200 domain names which appear to have been linked to QuaDream's spyware between late 2021 and early 2023, and in several cases trace them back to their operators, suggesting that these systems were operated from the following countries:
- Bulgaria
- Czech Republic
- Hungary
- Ghana
- Israel
- Mexico
- Romania
- Singapore
- United Arab Emirates (UAE)
- Uzbekistan
Several of these countries have what can at best be described as a patchy track record with respect to surveillance of citizens, especially human rights advocates and journalists.
Marczak, Bill, et. al., Sweet QuaDreams: A First Look at Spyware Vendor QuaDream’s Exploits, Victims, and Customers, technical report, 11 April 2023. Available online at https://citizenlab.ca/2023/04/spyware-vendor-quadream-exploits-victims-customers/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
VPS's Replace IoT for DDoS Attackers, Says Cloudflare
In its first DDoS threat report for 2023, web acceleration and DDoS mitigation company Cloudflare reports a shift away from the use of compromised Internet of Things devices by attackers. Instead, the threat actors are making use of virtual private servers (VPS's) hosted by cloud computing service providers. The reason is simple: IoT devices are typically low-powered and connected to low-bandwidth consumer networks, while VPS's, located in large data centers, are much more powerful devices and are connected to the Internet by fat pipes.
The threat actors take over these servers by compromising unpatched servers and also hacking the management consoles using leaked API credentials. Cloudflare has been addressing this by setting up a free botnet threat feed for cloud service providers which will alert the firms to attacks originating within their own networks, so that they can be brought down promptly.
In other highlights from the DDoS threat report:
- The year began with a series of campaigns against Western targets such as banking, airports, healthcare and universities, mostly led by the pro-Russian Telegram-organized group Killnet and more recently by AnonymousSudan
- Hyper-volumetric attacks increased significantly, with the largest one peaking at over 71 million requests per second (the previous world record was 'only' 46 million rps)
- 16% of Cloudflare customers reported a Ransom DDoS attack - holding steady in comparison with the previous quester, but a 60% year-on-year increase
- The most-targeted country for HTTP DDoS traffic is Israel, which displaced the US from the top spot (followed by Canada and Turkey).
- The most-targeted country for network-layer DDoS attack traffic was China, closely followed by Singapore.
Yoachimik, Omer and Jorge Pacheco, DDoS threat report for 2023 Q1, blog post, 11 April 2023. Available online at https://blog.cloudflare.com/ddos-threat-report-2023-q1/.
Don't Charge from Public USB Outlets, Says FBI
The FBI's Denver office has tweeted a warning against the use of free USB charging stations:
Avoid using free charging stations in airports, hotels or shopping centers. Bad actors have figured out ways to use public USB ports to introduce malware and monitoring software onto devices. Carry your own charger and USB cord and use an electrical outlet instead.
We'd generally agree, but also add that a USB condom - an inline connector which connects only the power lines and blocks data transfer - is a useful alternative, especially for international travelers who want to avoid carrying lots of power adapters. However, they may disable the fast charging capabilities of some devices. In any case, leaving your high-end phone plugged in on a shelf while you queue for a coffee nearby is an invitation to theft. Better to carry a power pack and recharge inside your locked hotel room (but even then . . .).
FBI Denver, Avoid using free charging stations ..., tweet, 6 April 2023. Available online at https://twitter.com/FBIDenver/status/1643947117650538498.
New Google API Helps to Secure the Supply Chain
Google has announced a new online API - the deps.dev API - which provides free access to a dataset of security metadata including dependencies, licenses, advisories and other security-related infor for over 50 million open source software package versions. The dataset is continuously updated from a range of sources, including package registries, the Open Source Vulnerability Database, development repositories such as GitHub and GitLab, and the packages themselves. There are over 5 million packages from the Go, Maven, PyPI, npm, and Cargo ecosystems.
The API will allow the development of tools which will support analyses of software packages and the updating of configuration management databases. This will allow operations and security staff to answer questions such as
- What dependencies does this package have?
- What are the licences for the packages this application uses?
- Will moving to the latest version of this package change dependencies or the licences?
- What versions of what packages contain this file?
The impact of vulnerabilities such as Log4Shell has really brought home the lesson that we need tools that can answer these and even more basic questions, such as "A new vulnerability is being exploited - are we affected?".
Sarnesjo, Jesper and Nicky Ringland, Announcing the deps.dev API: critical dependency data for secure supply chains, blog post, 11 April 2023. Available online at https://security.googleblog.com/2023/04/announcing-depsdev-api-critical.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Russian GRU Officer Doxxed
In a classic 'man bites dog' reversal of the usual order, a Ukrainian hacktivist group called Cyber Resistance has been able to hack the email of a high-ranking officer of the Russian Main Intelligence Directorate of the General Staff of the Russian Army, otherwise known as the GRU. Even 'better', he is the head of the 85th Main Special Service Center of the GRU, military unit 26165, more commonly known as APT 28, a.k.a. Fancy Bear.
APT 28 is one of the most agressive Russian threat actors, known to have run cyberattacks against government agencies and critical infrastructure in Ukraine, the US, the Netherlands, Poland, Latvia, Germany, the Czech Republic and elsewhere. Back in 2018, the US Justice Department formally indicted 12 GRU employees for breaching the email systems of the US Democratic National Committee and attempting to interfere in the 2016 US elections. Among those indicted is the victim of this breach: Lieutenant Colonel Sergey Alexandrovich Morgachev.

(Image credit: Cyber Resistance / InformNapalm)
Among the emails retrieved by the hackers was one from Apple, warning Morgachev that the FBI had requested, and been granted, information regarding his Apple account. The Cyber Resistance hackers were also able to obtain his address details, his passport, the registration of his car (a Toyota RAV4) as well as his employment records, such as a medical certificate required for his security clearance. All of this was passed to the InformNapalm site, which has published it.
Uncredited, Hacked: Russian GRU officer wanted by the FBI, leader of the hacker group APT 28, news article, 10 April 2023. Available online at https://informnapalm.org/en/hacked-russian-gru-officer/.
It's That Day of the Month Again
It's Patchday again - that day when we install a large batch of Windows patches and reboot.
This month, the Windows 11 KB5025239 cumulative update contains fixes for 97 vulnerabilities in various Microsoft products. Key among these is a fix for CVE-2023-28252, a privilege escalation vulnerability in the Windows Common Log File System (CLFS) Driver, which the Cybersecurity & Infrastructure Security Agency has today added to its Known Exploited Vulnerabilities Catalog. The vulnerability is being exploited in ransomware attacks.
The update also adds a number of other fixes and enhancements.
Microsoft Security Response Center, April 2023 Security Updates, web page, 11 April 2023. Available online at https://msrc.microsoft.com/update-guide/releaseNote/2023-Apr.
CISA, CISA Adds One Known Exploited Vulnerability to Catalog, alert, 11 April 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/04/11/cisa-adds-one-known-exploited-vulnerability-catalog.
Guidance for Dealing with BlackLotus
Microsoft has also provided a step-by-step guide for organizations investigating whether users have been targeted by threat actors exploiting CVE-2022-21894 using the UEFI (Unified Extensible Firmware Interface) bootkit, BlackLotus. This bootkit is able to bypass the Windows Secure Boot process and deploy malware files to the EFI System Partition.
Microsoft Security, Guidance for investigating attacks using CVE-2022-21894: The BlackLotus campaign, blog post, 11 April 2023. Available online at https://www.microsoft.com/en-us/security/blog/2023/04/11/guidance-for-investigating-attacks-using-cve-2022-21894-the-blacklotus-campaign/.
Fortinet Product Vulnerability Advisories
Fortiguard Labs has released its monthly Vulnerability Advisories for a range of Fortinet products. Perhaps the most significant is one which allows remote unpassworded access to the redis and mongodb subsystems in FortiPresence, and which rates a CVSS score of 9.3. However, a wide range of products also make the list, including FortiOS and FortiProxy, FortiSandbox/FortiDeceptor, FortiClient for both Windows and Mac, FortiADC, FortiAnalyzer and others.
Uncredited, April 2023 Vulnerability Advisories, PSIRT monthly advisory, April 2023. Available online at https://www.fortiguard.com/psirt-monthly-advisory/april-2023-vulnerability-advisories.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Latitude Refuses to Pay Ransom
Back in mid-March, then in late March, we reported on the data breach affecting customers of consumer lender Latitude Financial (ASX:LFS). Today Latitude confirmed that it has received a ransom demand and, in line with advice from both government and cybercrime experts, will not pay a ransom. Said Latitude Financial CEO, Bob Belan:
"Latitude will not pay a ransom to criminals. Based on the evidence and advice, there is simply no guarantee that doing so would result in any customer data being destroyed and it would only encourage further extortion attempts on Australian and New Zealand businesses in the future.
"Our priority remains on contacting every customer whose personal information was compromised and to support them through this process.
"In parallel, our teams have been focused on safely restoring our IT systems, bringing staffing levels back to full capacity, enhancing security protections and returning to normal operations.
"I apologise personally and sincerely for the distress that this cyber-attack has caused and I hope that in time we are able to earn back the confidence of our customers."
The company believes that there has been no suspicious activity in their systems since Thursday, 16 March, and is now restoring its business operations.
Gardy, Mark, Cybercrime update, ASX announcement, 11 April 2023. Available online at https://www.asx.com.au/asx/statistics/displayAnnouncement.do?display=pdf&idsId=02652931.
Tasmanian Department of Education Fileshare Hacked; 16,000 Documents Leaked
A Russian ransomware gang has allegedly obtained over 16,000 documents from the Tasmanian Department for Education, Children and Young People via the third-party file transfer service GoAnywhere, and has released them on the dark web. The documents primarily related to current and historical financial information and may include:
- names
- addresses
- school name
- DECYP reference number (used for DECYP internal account purposes)
- child name
- homeroom
- year group
- Business names
- Bank Account (if the Department paid the affected individual)
- Learner's Date of Birth (TasTAFE only)
The Tasmanian Government has established a helpline number for affected individuals on 1800 567 567.
Uncredited, Hackers release personal data from Tasmanian Government data breach, Pulse Hobart, 7 April 2023. Available online at https://pulsehobart.com.au/news/hackers-release-personal-data-from-tasmanian-government-data-breach/.
DECYP, Cyber Investigation Update, web page, 11 April 2023. Available online at https://www.decyp.tas.gov.au/cyber-investigation-update/.
CISA Adds Five Known Exploited Vulnerabilities; Veritas Backup Exec Used for Ransomware
The US Cybersecurity & Infrastructure Security Agency has added five new vulnerabilities to its Known Exploited Vulnerabilities Catalog:
- CVE-2021-27876 Veritas Backup Exec Agent File Access Vulnerability
- CVE-2021-27877 Veritas Backup Exec Agent Improper Authentication Vulnerability
- CVE-2021-27878 Veritas Backup Exec Agent Command Execution Vulnerability
- CVE-2019-1388 Microsoft Windows Certificate Dialog Privilege Escalation Vulnerability
- CVE-2023-26083 Arm Mali GPU Kernel Driver Information Disclosure Vulnerability
The most significant of these is CVE-2021-27877, which NIST's National Vulnerability Database rates has having a CVSS 3.1 score of 9.8 (critical). Mandiant reports that this vulnerability has been used by the ALPHV/BlackCat ransomware gang to gain initial access to one of their victims' networks. However, Veritas released patches for these vulnerabilities back in March 2021 - over two years ago - so there really is no excuse, etc., etc.
CISA, CISA Adds Five Known Exploited Vulnerabilities to Catalog, alert, 7 April 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/04/07/cisa-adds-five-known-exploited-vulnerabilities-catalog.
Apple Device 0days Likely Used For Spyware Implants
Last week, Apple rushed out patches for macOS Ventura, iOS version 16 and iPadOS version 16 in response to the disclosure of two zero-day exploits. The first related to a remote code execution vulnerability in the WebKit HTML engine, while the second was a code execution vulnerability in the OS kernel, which would allow privilege escalation.
The vulnerabilities were jointly reported to Apple by the Amnesty International Security Lab and the Google Threat Analysis Group, which suggests that the exploits were first discovered by privacy and human rights activitists, then analysed by Google's researchers. If so, then they were probably being used to implant spyware on behalf of government agencies somewhere.
In fact, all supported versions of iOS, iPadOS and macOS contained these vulnerabilities, and patches have been released for them. Users should check for an install these updates as soon as possible.
Ducklin, Paul, Apple zero-day spyware patches extended to cover older Macs, iPhones and iPads, blog post, 10 April 2023. Available online at https://nakedsecurity.sophos.com/2023/04/10/apple-zero-day-spyware-patches-extended-to-cover-older-macs-iphones-and-ipads/.
Western Digital My Cloud Pain Continues; Company Issues Workaround
The pain of last week's breach at storage drive manufacturer Western Digital continues for its customers. With the company's My Cloud service being taken down, customers had no way to access their files, even though their devices were on the customers' own networks, as even local access required a connection to the cloud service. In fact, the problem applied not just to My Cloud, but also My Cloud Home, My Cloud Home Duo, My Cloud OS 5, SanDisk ibi, and SanDisk Ixpand Wireless Charger, as well as their related apps.
However, the company has now released a workaround which will enable access to local devices on the LAN via network mapped drives, for up to 5 concurrent local users. The procedure is slightly involved, but most SME and home users should be able to follow it, with the aid of embedded videos to walk them through.
Western Digital Support, Instructions to Enable Local Network Access on a My Cloud Home, My Cloud Home Duo and SanDisk ibi, web page, 10 April 2023. Available online at https://support-en.wd.com/app/answers/detailweb/a_id/50626.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Open Garage Doors, Everywhere, in One Easy Step!
In an outstanding demonstration of the dangers of the Internet of Things, security researcher Sam Sabetan has disclosed a collection of critical vulnerabilities in Nexx smart devices - garage door openers, alarms and plugs - which allow remote attackers to open and close garage doors, control alarms and switch devices on and off for any and all Nexx customers.
The devices boast five different vulnerabilities:
- Use of Hard-coded Credentials; CWE-798 (CVE-2023–1748, CVSS3.0: 9.3)
- Authorization Bypass Through User-Controlled Key; CWE-639 (CVE-2023–1749, CVSS3.0: 6.5)
- Authorization Bypass Through User-Controlled Key; CWE-639 (CVE-2023–1750, CVSS3.0: 7.1)
- Improper Input Validation; CWE-20 (CVE-2023–1751, CVSS3.0: 7.5)
- Improper Authentication Validation; CWE-287 (CVE-2023–1752, CVSS3.0: 8.1)
In short, the critical issue is this: the Nexx devices use a single universal password to communicate with their controlling servers in the cloud, using the MQTT (Message Queueing Telemetry Transport) IoT messaging protocol. For applications like this, a unique password should be assigned for each device in order to achieve secure, confidential, authenticated communications.
To make matters worse, the Nexx messages are broadcast universally - i.e. to all devices - and the garageDoorOpener messages expose user emails, device ID's and contractions of user names. This allows enumeration of customer and device information, as well as simple replay attacks. And it goes on from there: the Nexx app is also vulnerable to Insecure Direct Object Reference attacks, the smart alarm controller - which can turn other manufacturers' alarm systems on and off remotely - does not properly validate bearer tokens and also exposes the MAC address of those alarms.
In short, this is an epic IoT security fail. Nexx has not responded to contacts from Sabetan, the US Cybersecurity & Infrastructure Security Agency, or media outlets, and one can almost understand why: the exposure of affected customers (at least 20,000 of them) is massive, and remediation will also be a costly undertaking, if it can be done at all (if the firmware which contains the hard-coded passwords is not stored in flashable media). The only safe course for Nexx customers is to unplug these devices and contact Nexx to get them fixed or replaced.
Sabetan, Sam, The Uninvited Guest: IDORs, Garage Doors, and Stolen Secrets, blog post, 5 April 2023. Available online at https://medium.com/@samsabetan/the-uninvited-guest-idors-garage-doors-and-stolen-secrets-e4b49e02dadc.
Self-Extracting Archives Considered Harmful
Our readers are doubtless familiar with the use of WinZIP, WinRAR and similar utilities to compress files and package them for faster download and distribution. So common have these techniques become that the Windows desktop shell has code built in to transparently open ZIP files as though they are just another folder. However, most archiving utilities offer another feature that Windows doesn't: the ability to encrypt an archive under a password in order to provide some degree of security for email attachments.
In order to make it possible for a recipient to extract the contents of an password-protected archive file without having to buy additional software, many utilities can create self-extracting archive (SFX) files which package the desired files along with a stub of code for decryption and file extraction. The risk here is that it entices the recipient to run code which has just been received from a source which may be untrusted or even unknown - but naive end-users rarely stop to consider this.
Threat actors are increasingly making use of this to install malware such as backdoors into victims' machines. Crowdstrike's Falcon OverWatch team provides a nice example they recently discovered: an apparently empty SFX archive which could could implant a persistent backdoor.
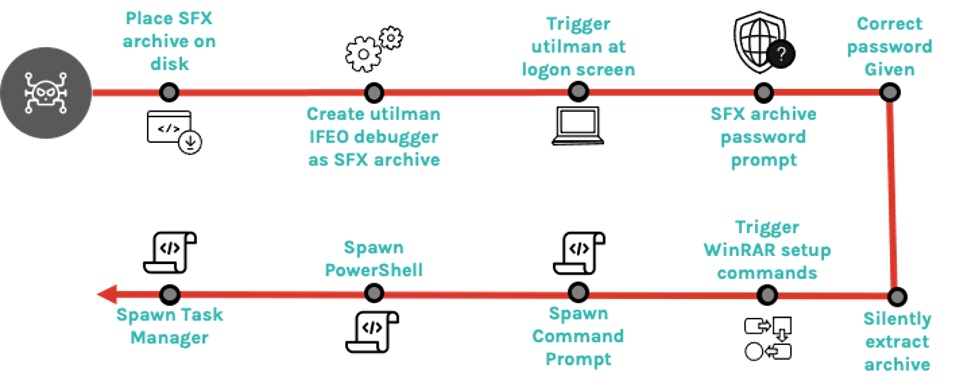
(Image credit: Crowdstrike)
In this case, the malware used a registry key to configure utilman.exe to run an ImageFileExecutionOptions debugger at logon time, with the debugger then running a password-protected SFX archive. But the really curious fact is that the archive contains only a text file of 0 bytes length, rather than any actual malware. In fact, the backdoor was established by using the ability of WinRAR SFX archives to run extended SFX commands upon successful unarchiving; in this case, the SFX would automatically spawn a command prompt, PowerShell and a copy of Task Manager with no visible dialogs - just what a threat actor needs in order to regain access to a compromised system.
Because many anti-malware tools will scan only the files within a self-extracting archive, and this archive contained only an innocent-looking empty text file, it could easily escape detection.
Minton, Jill, How Falcon OverWatch Investigates Malicious Self-Extracting Archives, Decoy Files and Their Hidden Payloads, blog post, 31 March 2023. Available online at https://www.crowdstrike.com/blog/self-extracting-archives-decoy-files-and-their-hidden-payloads/.
ChatGPT Happily Works on the Dark Side
Many IT and security professionals have experimented with ChatGPT, getting it to write code. Inevitably, our thoughts drift to how threat actors might make use of such tools. While ChatGPT's creators, OpenAI, have put in place some protections and obvious requests to write malware will be blocked, we are learning that chaining multiple requests and using oblique phrasing can often circumvent OpenAI's defensive efforts.
Now Forcepoint solutions architect Aaron Mulgrew has shown how, with just a few hours experimenting and very limited tech skills, ChatGPT can be enticed into writing some functional malware - in this case, an undetectable information exfiltration tool that uses steganographic techniques.
The basic technique that Mulgrew used was to generate small snippets of code and then manually assemble the completed code. By asking ChatGPT for code to a) find large PNG files, b) steganographically encode the found files and c) exfiltrate them to Google Drive, he was able to create a working proof-of-concept. Unfortunately, when processed by VirusTotal, this first version was flagged as malicious by five different vendors out of 69 possible detections - not a bad start, though.
Armed with some clues about why some vendors might be detecting this code, Mulgrew then set about getting ChatGPT to refactor the code, first by incorporating some steganography code directly, rather than calling an external library. Next, to evade sandbox detection, he had ChatGPT delay execution of the code by two minutes. Finally, after a simple request to obfuscate the code was rebuffed, he simply had ChatGPT change all the variable names to random English first names and surnames. This time, VirusTotal did not detect the code as malicious.
The final step was to achieve initial access or delivery, e.g. by getting a naive user to execute it. Mulgrew was able to coax ChatGPT into providing instructions to package the executable as a Windows screensaver (.SCR) file. However, this led to three detections by VirusTotal - but at least the point was made: ChatGPT can be 'social engineered' into writing malware, and we should expect threat actors to take advantage of this in coming months.
Interestingly, Mulgrew ended his experiment by getting ChatGPT's advice on how to mitigate this kind of attack, and it was pretty much what you might expect: generally obvious but certainly not foolproof.
Mulgrew, Aaron, I built a Zero Day with undetectable exfiltration using only ChatGPT prompts, blog post, 4 April 2023. Available online at https://www.forcepoint.com/blog/x-labs/zero-day-exfiltration-using-chatgpt-prompts.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Data Breach Affects Over 2,000 South Australian Students
TAFE SA (South Australia's Technical and Further Education provider) has disclosed a somewhat disturbing breach affecting 2,224 students who were enrolled in classes prior to the end of 2021, and possibly going as far back as 2016.
TAFE SA only discovered the breach after SA Police informed them that they had seized devices containing scanned copies of student identification forms. These contain copies of proof-of-identity documents, including driver's licences and passports. The forms also contain student ID numbers, course details, a fill name, address and date of birth - just what is needed for identity theft.
TAFE has, of course, conducted an investigation into how the breach occurred, but a forensic investigation has, to date, found no evidence that network systems were illegally accessed or that the breach occurred from an external source - all of which suggests that this was an insider attack. Access to the system that holds the student ID forms has been further restricted, with access on a need-to-know basis.
Affected students have been contacted and are being offered advice as well as support through IDCARE. TAFE will also reimburse expenses for replacement of compromised identity documents.
You already know what we are going to say: once identity documents have been used to verify identity, they are a liability, and not an asset.
TAFE SA, Data Breach, information page, 28 March 2023. Available online at https://www.tafesa.edu.au/about-tafesa/data-breach.
FBI Seizes 'Bot Shop' Credential Store
In a coordinated multinational action, the FBI has seized several domain names associated with a site which traded in passwords, cookies and other credentials stolen from malware-infected computers, according to blogger Brian Krebs. Genesis Market has been online since 2018, under the slogan "Our store sells bots with logs, cookies, and their real fingerprints" and allowed its criminal customers to select victims by IP address or by domain names.
Early yesterday, agencies from multiple countries, including Australia, Canada, Denmark, Germany, the Netherlands, Spain, Sweden and the UK, led by the FBI, replaced the home pages on domains associated with Genesis Market and served arrest warrants on dozens of people affiliated with its operations.
The 'bots' sold by the sites provide all the original victim's authentication cookies, which can be loaded into a browser plugin, allowing access to online system accounts with no need for a password or other authentication credentials - including, in some cases, no need for second authentication factors. In general, systems will view any connection from the bot as being part of the same session the victim had established previously. The bot also provides the fingerprint - i.e. the agent type and other identifying characteristics sent in HTTP requests - of the victim's browser, so that will also look the same to targeted sites.
The FBI has made no official statement to date; but a statement is likely forthcoming.
Krebs, Brian, FBI Seizes Bot Shop ‘Genesis Market’ Amid Arrests Targeting Operators, Suppliers, blog post, 4 April 2023. Available online at https://krebsonsecurity.com/2023/04/fbi-seizes-bot-shop-genesis-market-amid-arrests-targeting-operators-suppliers/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Western Digital Hit By Security Breach - MyCloud Taken Offline
Storage drive manufacturer Western Digital has disclosed a network security incident involving some of its systems. On 26 March the company identified an incident in which an unauthorized third party gained access to its systems. The firm activated its incident response procedures and commenced an investigation with the assistance of external incident response and digital forensics experts.
The investigation to date suggests that the intruder was able to exfiltrate certain information from the affected systems and the company is working to understand that nature and scope of that data. Among the response actions, several systems and services have been taken offline; at time of writing the My Cloud status page at https://status.mycloud.com/os4 indicates that My Cloud Home and My Cloud OS 5 services are down.
(Author pauses, stares at all the WD external backup drives around his office and counts himself fortunate to be very cautious in his use of external cloud services.)
FGS Global, Western Digital Provides Information on Network Security Incident, news release, 3 April 2023. Available online at https://www.businesswire.com/news/home/20230402005076/en/Western-Digital-Provides-Information-on-Network-Security-Incident.
US DoJ Seizes Over $US112 Million From Crypto Investment Scammers
The US Department of Justice has managed another win in the constant battle against cryptocurrency scammers, this time seizing virtual currency worth an estimated $US112 million linked to cryptocurrency investment scammers. Judges in the District of Arizon, the Central District of California and the District of Idaho had authorized seizure warrants.
The virtual currency accounts were allegedly used to launder proceeds of various cryptocurrency confidence scams. In these schemes - often referred to as 'pig fattening' or 'pig butchering' - fraudsters cultivate long-term relationships with victims met online, eventually enticing them to make investments in fraudulent cryptocurrency trading platforms. In reality, however, the funds sent by victims for these purported investments were instead funneled to cryptocurrency addresses and accounts controlled by scammers and their co-conspirators.
In 2022, investment fraud caused the highest losses of any scam reported by the public to the FBI’s Internet Crimes Complaint Center (IC3), totaling $3.31 billion. Frauds involving cryptocurrency, including pig butchering, represented the majority of these scams, increasing a staggering 183% from 2021 to $2.57 billion in reported losses last year.
Office of Public Affairs, Justice Department Seizes Over $112M in Funds Linked to Cryptocurrency Investment Schemes, news release, 3 April 2023. Available online at https://www.justice.gov/opa/pr/justice-department-seizes-over-112m-funds-linked-cryptocurrency-investment-schemes.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Class Action Invites Latitude Financial Customers to Join
While many security professionals agonise over the possibility of fines for privacy breaches, it is worth remembering that much older penalties continue to apply and can have much more severe consequences than a fine. We reported last week that the breach of consumer lender Latitude Financial had worsened as more details emerged, with investigations revealing that as many as 14 million customer records were compromised.
Now comes news that law firms Gordon Legal and Hayden Stephens and Associates are investigating a potential legal action against Latitude Financial and are looking into whether the lender's security measures and protocols were effective and whether the company had taken appropriate steps to protect its customers' personal information. Of course, should this reach court - or even prior mediation - a lot will depend on a) how the breach actually occurred and b) how a court defines 'appropriate steps' (a more common phrase in legislation is 'reasonable steps').
Current and former customers who believe they may have been affected by the data breach are invited to register their interest. Their site also contains links to useful online resources for those affected, as well as a list of news reports on the breach.
Hayden Stephens and Associates, Latitude Financial Data Breach Investigation, web site, 28 March 2023. Available online at https://www.latitudedatabreach.com.au/.
WordPress Plugin Exposes Millions of Sites
By far the most popular web site content management system is WordPress; millions of businesses use it as the basis of their sites, especially because of its huge range of extensions and plugins. Unfortunately, many of these sites are poorly maintained - a practice that could hit a huge number this week, as hackers exploit a critical vulnerability in a premium WordPress plugin.
The vulnerability, which has a CVSS 3.1 score of 8.8 (high) is present in the Elementor Pro plugin. In particular, it is in the elementor-pro/modules/woocommerce/module.php component, which is loaded when Elementor Pro is installed on WordPress sites that also have the WooCommerce merchant server plugin activated. The component registers two AJAX actions, one of which - pro_woocommerce_update_page_option - is intended to allow the Administrator or the Shop Manager to update some WooCommerce options.
Unfortunately, the function does not check that the user invoking it has appropriate privileges, and it also does not sanitize user input. As a result, an authenticated attacker is able to create an administrator account by enabling the users_can_register setting and setting the default_role to administrator while also changing the administrator email address (admin_email). The vulnerability was discovered and documented by Jerome Bruandet of Ninja Technologies Network.
However, now researchers at another firm, Patchstack, report that the vulnerability is being actively exploited. Users are advised to urgently update their Elementor Pro installations to version 3.11.7 or later (the free version of Elementor is unaffected).
Bruandet, Jerome, High severity vulnerability fixed in WordPress Elementor Pro plugin. blog post, 28 March 2023. Available online at https://blog.nintechnet.com/high-severity-vulnerability-fixed-in-wordpress-elementor-pro-plugin/.
Dave, Critical Elementor Pro Vulnerability Exploited, blog post, 30 March 2023. Available online at https://patchstack.com/articles/critical-elementor-pro-vulnerability-exploited/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.