Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
World Backup Day - You Know What To Do (Don't You?)
Today is 31 March, which for more than a decade has been World Backup Day. While we, as information assurance professionals, are well aware of the need to protect our data (aren't we?), our employees, friends and associates are often not up to speed on this requirement. Now is the time to re-energize your awareness campaigns, not to mention ensuring that enterprise backup strategies and procedures are fully up-to-date and tested.
The World Backup Day web site provides some useful - albeit scary - statistics:
- 21% of people have never made a backup
- 29% of data loss cases are caused by accident (implying 71% are deliberate?)
- 113 phones are lost or stolen every minute, and
- 30% of all computers are already infected with malware
Now is a good time to promote the 3-2-1 backup strategy:
You should have three copies of your data (that's the production data and two separate backups) on two different media (e.g. disk and tape) with one copy stored off-site for disaster recovery.
Consider this just the bare minimum; there are so many options for personal system backup these days it is easy to meet this basic level and exceed it. We have SSD's and magnetic media, RAID arrays, external USB hard drives and flash drives, high-capacity LTO tape drives, optical media such as Bluray-R and cloud storage. Plus we have a wide range of software to manage all of this on both desktop (Windows, Mac, Linux) and NAS/server platforms.
In our office, all desktop and laptop machines are backed up to external hard drives using R-Drive Image to run a grandfather-father-son rotational backup scheme as a nightly batch job (we chose R-Drive image (https://www.drive-image.com/) after a semi-exhaustive comparison - and yes, it has earned its price several times over following failure of a 1 TB SSD). I also store all work on a NAS, using the Windows 'offline files' feature to keep a local copy on laptops for use while traveling and as a backup, and the NAS itself is backed up both locally and off-site.
Remember: any backup media - and this includes cloud storage - should be protected to the same level as the original data requires; this may require encryption, particularly in the cloud. And don't forget to backup external resources such as web site content - and this does not mean saving a database backup in an unprotected directory on the web server, or in unprotected AWS buckets.
Uncredited, World Backup Day, web site, undated. Available online at https://www.worldbackupday.com.
ChatGPT Leaks User Data
OpenAI has revealed that its ChatGPT AI chatbot leaked information including the titles of active users' chat history and the first message of newly-created conversations. Perhaps more significantly, it also exposed the payment data for 1.2% of ChatGPT Plus customers, including their first and last name, email address, payment address, the last four digits of their credit card number (thank you, PCI-DSS!) and the card expiry date.
The word 'active', above, is significant - the vulnerability that underlies this discovery is in the Redis client library, redis-py, which OpenAI uses to cache user information in their server instances. For a period of approximately nine hours on Monday, 20 March, a change to the OpenAI server caused a spike in Redis request cancellations, creating a small probability for each connection to return bad data. Since the problem was in this cache subsystem, it only affected currently active sessions, with the possibility that a subscriber would see another user's data rather than his own.
OpenAI's admins took the service offline and their developers immediately contacted the Redis development team to develop a bug fix which was quickly deployed and service restored. All affected users were contacted, but the risk seems to be low.
While everyone ponders the broader impact of artificial intelligence, it's important to remember these systems are still just software, with many of the vulnerabilities of simpler applications.
Uncredited, March 20 ChatGPT outage: Here’s what happened, OpenAI blog, 24 March 2023. Available online at https://openai.com/blog/march-20-chatgpt-outage.
Robertson, Adi, FTC should stop OpenAI from launching new GPT models, says AI policy group, The Verge, 30 March 2023. Available online at https://www.theverge.com/2023/3/30/23662101/ftc-openai-investigation-request-caidp-gpt-text-generation-bias.
CISA Adds Ten New Known Exploited Vulnerabilities
The US Cybersecurity & Infrastructure Security Agency has added ten new vulnerabilities to its Known Exploited Vulnerabilities Catalog. These vulnerabilities are being actively exploited in the wild, making it important to prioritize their patching or at least deployment of compensating controls:
- CVE-2013-3163 Microsoft Internet Explorer Memory Corruption Vulnerability
- CVE-2014-1776 Microsoft Internet Explorer Memory Corruption Vulnerability
- CVE-2017-7494 Samba Remote Code Execution Vulnerability
- CVE-2022-42948 Fortra Cobalt Strike User Interface Remote Code Execution Vulnerability
- CVE-2022-39197 Fortra Cobalt Strike Teamserver Cross-Site Scripting (XSS) Vulnerability
- CVE-2021-30900 Apple iOS, iPadOS, and macOS Out-of-Bounds Write Vulnerability
- CVE-2022-38181 Arm Mali GPU Kernel Driver Use-After-Free Vulnerability
- CVE-2023-0266 Linux Kernel Use-After-Free Vulnerability
- CVE-2022-3038 Google Chrome Use-After-Free Vulnerability
- CVE-2022-22706 Arm Mali GPU Kernel Driver Unspecified Vulnerability
Note that some of these vulnerabilities go back a very, very long way - 2013? Seriously? - and the fact that they are still being exploited indicates that somebody, somewhere is asleep at the wheel
CISA, CISA Adds Ten Known Exploited Vulnerabilities to Catalog, alert, 30 March 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/03/30/cisa-adds-ten-known-exploited-vulnerabilities-catalog.
Whistle Blown on Russian Cyberwarfare Efforts
A whistleblower, probably connected to a Moscow cybersecurity consultancy named 'Vulkan', has released a tranche of documents which reveal links between Vulkan, the Russian foreign intelligence agency (the SVR), military intelligence (the GRU and GOU), and the domestic intelligence agency (the FSB) - the latter a collaboration which could never have happened during the Soviet era, when the agencies were traditional enemies.
The software engineers at Vulkan are alleged to have worked for the agencies to support offensive security operations, train others to attack national infrastructure (particularly in Ukraine, but documents also reveal targets in the US and Switzerland), spread disinformation online and surveil and control those sections of the Internet under Russian control.
Documents link Vulkan to several projects, including Scan-V, a tool which builds a database of vulnerabilities across the Internet, and which is possibly used by Sandworm (Unit 74455 - who are also behind NotPetya and the Cyclops Blink botnet) and a system known as Amezit, which is used to surveil and control the Internet in the Commonwealth of Independent States. Another project, Crystal-2V, is used to train operatives in cyber-attacks on transport infrastructure.
The whistleblower, who leaked the documents to Munich-based investigative startup Paper Trail Media, has taken a huge risk by making them public. Eleven different media outlets, including the Guardian, Washington Post and Le Monde have been sifting through the documents and we can expect a lot more detail to emerge in coming days.
Harding, Luke, Stiliyana Simeonova, Manisha Ganguly and Dan Sabbagh, ‘Vulkan files’ leak reveals Putin’s global and domestic cyberwarfare tactics, The Guardian, 31 March 2023. Available online at https://www.theguardian.com/technology/2023/mar/30/vulkan-files-leak-reveals-putins-global-and-domestic-cyberwarfare-tactics.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Australia, New Zealand, Lag in MFA Adoption, Says Yubico
MFA vendor Yubi has published the results of their first State of Global Enterprise Authentication Survey, which garnered responses from over 16,000 employees in 8 countries: Australia, New Zealand, Singapore, the UK, the US, France, Germany and Sweden. And the results do not look good for A/NZ.
In Australia, 65% of employees still rely on username and password as the primary account authentication mechanism - higher than the global average of 59% (NZ is a little better, at 63%), leaving them exposed to basic phishing attacks. Worse still, Australians still rely heavily on SMS-based verification, at 38% of respondents, compared with the global figure of 33% (NZ: 31%). This is despite the fact that the use of SMS for verification was deprecated by NIST SP 800-63B over five years ago - a point I have been hammering in my teaching.
Australia is in line with global trends in the use of password managers, although NZ still lags a little. But we're behind again in the adoption of FIDO U2F security keys - while the global adoption rate is 20%, Australia lags at 15% and NZ at 13%. I can't help wondering if people are concerned about being denied access to systems if they don't have their keys to hand, or not being able to cope with some imagined complexity; in practice, it's not a problem - we turned on mandatory MFA, using U2F security keys, across two businesses some years ago and have had no problems other than one lost key (which was immediately revoked).
There are some other interesting statistics in the survey report, including some alarming data about user perceptions of what constitutes secure authentication.
And if you remain unconvinced about the dangers of phishing attacks, take a look at this recent video:
.Yubico AB, State of Global Enterprise Authentication Survey: including exclusive data from Australia & New Zealand, survey report, March 2023. Available online at https://www.yubico.com/resource/state-of-global-enterprise-authentication-survey-australia-and-new-zealand/.
Microsoft Brings AI to Windows Security
Microsoft this week revealed its new OpenAI GPT-4-powered security analysis tool, called Security Copilot. The new product applies OpenAI's generative artificial intelligence and Microsoft's own security-specific language and data model to the data produced by the company's security products such as Microsoft Sentinel, Defender and Intune, allowing relatively untrained analysts to identify security incidents, obtain response instructions and even produce PowerPoint presentations which summarize an incident attack chain for management.
It's also possible to drag and drop files onto the product's prompt bar and ask questions, such as whether a dropped log file contains indications of a particular threat activity. Multiple queries can be collected into 'books' which can perform sequences of steps such as reverse-engineering malware and diagramming its operation. Results can also be shared within a team and saved to provide a record of, say, an incident response investigation.
The product is not fool-proof - in Microsoft's own demo it produces a spurious reference to 'Windows 9' - but it should prove near-irresistable to overworked enterprise SOC teams.
Microsoft Security, Introducing Microsoft Security Copilot, web page, 28 March 2023. Available online at https://www.microsoft.com/en-us/security/business/ai-machine-learning/microsoft-security-copilot.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Australian Privacy Breaches Continue with Meriton Latest Victim
Today comes news of yet another Australian company which has suffered a data breach; this time it is property firm Meriton, which has contacted almost 2,000 staff and customers, warning them to take steps to protect themselves.
Approximately 35.6 GB of data was compromised in the January 14 breach, including contact information of guests in Meriton serviced apartments, as well as other data - potentially including health information should they, for example, have suffered an injury which required an ambulance to be requested. However, staff are more severely affected, with potential access by cybercriminals to employment information such as their salary, bank account details, tax file numbers and performance appraisals.
The company has contacted the Australian Cyber Security Centre (ACSC) as well as the Office of the Australian Information Commissioner (OAIC), and is working with data forensics and incident response professionals. It has also promised to implement enhanced cybersecurity measures in future.
Tran, Danny, Hotel and property giant Meriton hit by data hack, personal documents may be at risk, ABC News, 29 March 2023. Available online at https://www.abc.net.au/news/2023-03-29/australian-hotel-chain-meriton-hit-by-data-breach-hack/102141880.
ABC Charts Scale of Privacy Breaches
Coincidentally, the Australian Broadcasting Corporation has published an interactive news report detailing the incredible scope of Australian and international data breaches which put Australians at risk of "serious harm". Their graphic shows a total of 2,784 breaches recorded since the start of 2020, based on reports to the OAIC and obtained via administrative access requests to de-aggregated versions of the summary data released in the OAIC's bi-annual reports (available for download as a spreadsheet).
Their analysis makes sobering reading, with some stand-out conclusions. For example, "There were 164 fewer data breaches disclosed last year than back in 2020." - yet this does not gel with the growth of ransomware attacks reported internationally.
In addition, breaches involving multinationals Amazon and Spotify did not fall into the scop of 'notifiable events' in Australia and therefore do not appear in the dataset at all.
A problem that rarely attracts attention is that each successive breach allows a threat actor who collects the information to aggregate information about the affected individuals; while an individual breach may not - to the breached organization - appear to reach the threshold of putting individuals "at likely risk of serious harm" and requiring mandatory disclosure to the OAIC, when combined with other breaches it certainly may pose risk of serious harm.
We may therefore see the law further refined to require breached organizations to take steps to determine what other information may exist from previous breaches before determining the level of risk posed in a holistic manner.
Fell, Julian, Georgina Piper and Matt Liddy, This is the most detailed portrait yet of data breaches in Australia, ABC Story Lab, 28 March 2023. Available online at https://www.abc.net.au/news/2023-03-28/detailed-portrait-data-breaches-oaic-disclosures/102131586.
Pen Tests Suggest Security Postures Are Weakening, Says Cymulate
In their new "2022 State of Cybersecurity Effectiveness", Cymulate researchers analysed the results of over 1 million penetration tests conducted within production environments. Their results indicate that, using their risk rating methodology, the average enterprise's information exfiltration risk rating has increased from 30 out of 100 in 2021, to 44 out of 100 in 2022 (compare this with reporting to the OAIC described above).
In addition, there is bad news about patch management: four of the top 10 vulnerabilities in customer environments were more than two years old.
It's not as though companies aren't working hard, either. Malware detection rates are improving, and most enterprises are doing better at securing their attack surfaces; it's just that threat actors are adapting even faster.
Porter, Katrina, Cymulate Releases Findings from Over One Million Security Assessments, news release, 28 March 2023. Available online at https://cymulate.com/news/one-million-security-assessments/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Latitude Breach Goes from Bad to Worse
I doubt that readers are surprised, but: the number of customer records stolen from consumer lender Latitude Financial is far larger than initially disclosed. Latitude has revealed that the data accessed by the attacker now totals:
- 6.1 million customer records - the vast bulk provided before 2013 - including names, addresses, phone numbers and dates of birth
- 7.9 million Australian and New Zealand drivers' licence numbers
- 53,000 passport numbers
Retail customers of major chains including JB Hi-Fi, The Good Guys and Harvey Norman - all of whom use Latitude - could be affected, and some of the data goes back as far as 2005.
We've said it before, but it bears repeating: despite much infosec lore categorising data as information assets, this kind of personally identifiable information is not an asset - it is a liability. There is no business advantage to keeping identity verification data once verification has been accomplished - it does not contribute to business revenue or profit. On the contrary, it exposes the business to increased losses due to reputation damage, not to mention fines and judgements under privacy law.
There are also lessons here about the dangers of prematurely stating that either information has not been compromised or that a breach is small; later revelations simply reduce consumer confidence. There is also a lot to be said for better education of C-suites and boards about incident response, not to mention cyber risk management more generally.
Barrett, Jonathan, Latitude Financial cyber-attack worse than first thought with 14m customer records stolen, The Guardian, 24 March 2023. Available online at https://www.theguardian.com/australia-news/2023/mar/27/latitude-financial-cyber-data-breach-hack-14m-customer-records-stolen.
Patch and Update Exchange Servers, or Get Throttled
Microsoft's Exchange mail and calendar server has suffered from a lot of high-profile vulnerabilities and exploits recently - think of ProxyLogon and ProxyShell - but it seems that Exchange admins (or, more likely, their managers) are not getting the message. The Internet still has many Exchange servers which are lagging behind the latest, or even quite old, security patches - and there are still enterprises running old versions of the software that are well beyond end-of-life support, such as Exchange 2010 and even Exchange 2007.
One problem is the tragedy of the commons: my security depends, at least in part, on you not relaying malware email attachments and other malmail to my systems. We're all in this together.
Now Microsoft is raising the stakes for those who are running unpatched and insecure Exchange servers, with the introduction of a new enforcement system to Exchange Online - the Redmondites' cloud mail system - that will:
- Report details to admins about any unsupported or out-of-date Exchange servers in their environment that connect to Exchange Online to send email
- Throttle emails sent from these servers if they are not remediated, progressively increasing the throttling duration over time
- Block email from unremediated servers after a suitable period.
The enforcement actions will ramp up over time - see the table below:
Enforcement stages (Image: Microsoft)
Admins can request a pause on blocking for up to 90 days per year, but this will provide only temporary relief. Enforcement actions will be introduced against Exchange 2007 servers only at first, but others will follow. The fact that this will induce customers to spend up on new Exchange licences is purely coincidental.
The Exchange Team, Throttling and Blocking Email from Persistently Vulnerable Exchange Servers to Exchange Online, Exchange Team Blog, 23 March 2023. Available online at https://techcommunity.microsoft.com/t5/exchange-team-blog/throttling-and-blocking-email-from-persistently-vulnerable/ba-p/3762078.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Careful What You Ask For
Honestly, you just can't trust anyone these days. In a lovely example of this old adage, thousands of naive would-be-cybercriminals have been caught out, registering for DDoS-as-a-Service or 'booter' sites which turned out to be fakes set up by the UK's National Crime Agency.
Last week, the NCA unmasked one of the sites, replacing it with a splash page warning users that their data has been collected and law enforcement will be in touch shortly:
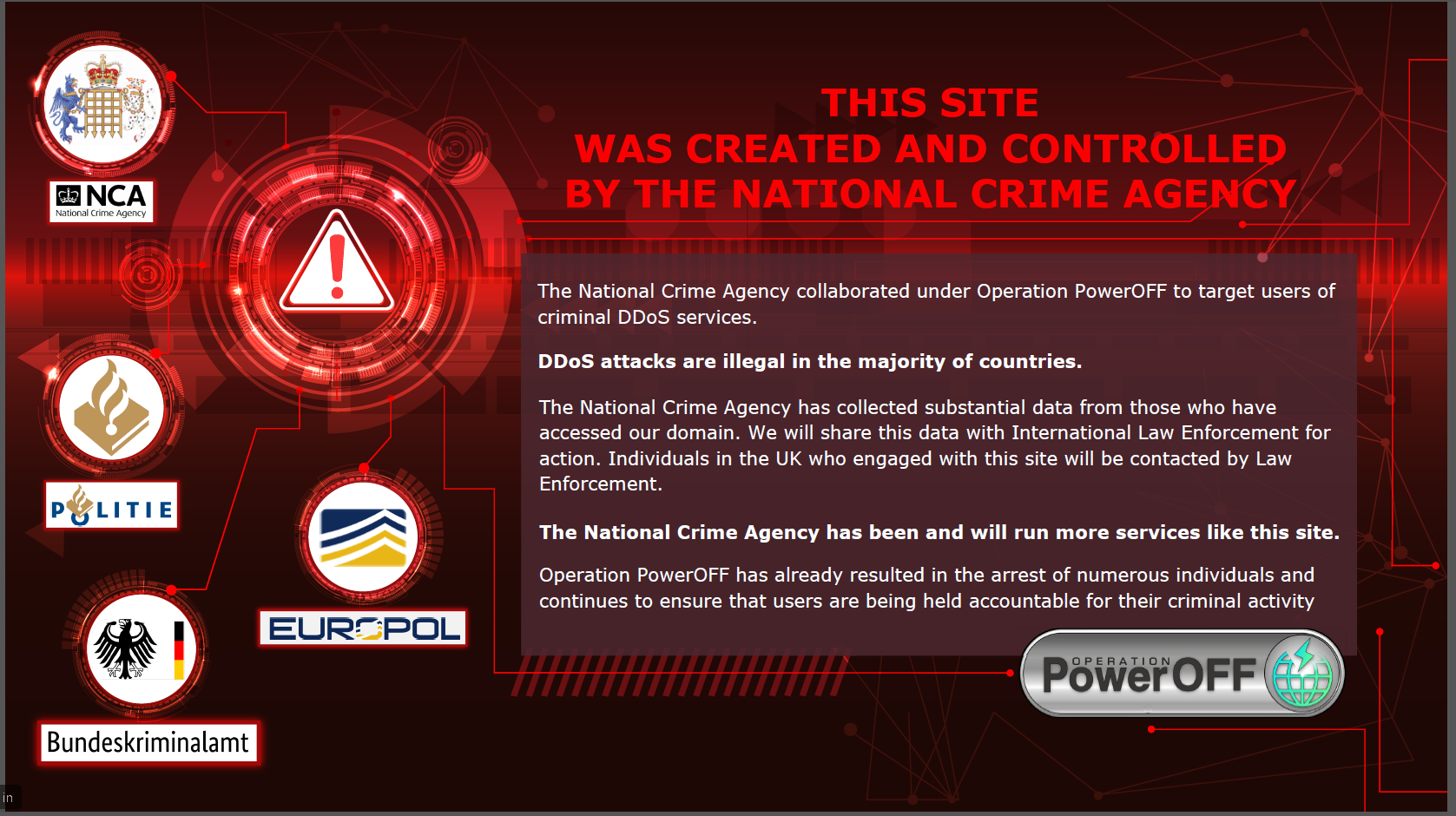
The National Crime Agency Operation PowerOff splash page (Image: National Crime Agency)
Distributed denial of service attacks are illegal in most countries - in the UK, they are covered under the Computer Misuse Act, 1990 - and while those who accessed these sites from the UK will be contacted either by the NCA or local police, details of overseas registrants will be passed to international partners including Dutch and German police.
This operation follows December's takedown of 48 of the world's most popular booter sites by the FBI in collaboration with European agencies. The NCA also arrested an 18-year-old man in Devon; he was suspected to be an administrator of one of the sites.
NCA, NCA infiltrates cyber crime market with disguised DDoS sites, news release, 24 March 2023. Available online at https://www.nationalcrimeagency.gov.uk/news/nca-infiltrates-cyber-crime-market-with-disguised-ddos-sites.
Australian Federal Police Bust Cybercrime Gang
The Australian Federal Police (AFP) has busted a sophisticated cybercrime syndicate which had allegedly performed multiple identity theft and business email compromise (BEC) attacks between January 2020 and March 2023.
The AFP investigation began in October 2021, after an Indonesian businessman lost over $A100,000 in a BEC attack. The trail they uncovered led them to two Brisbane women, a Melbourne man and an Adelaide man who had allegedly operated as a cybercrime and money-laundering syndicate with links to South Africa. The AFP alleges the syndicate orchestrated more than 15 sophisticated breaches, setting up over 80 bank accounts with stolen identities to help transfer $A1.7 million in stolen cash from Australian and overseas victims.
Apart from the BEC attacks, the syndicate allegedly also ran scams targeting Facebook Marketplace users and fraudulent superannuation investments, running about 180 bank accounts through which their victims individually lost anywhere between $A2,500 and $A500,000.
On Thursday of last week, investigators executed fives search warrants across Queensland, Victoria and South Australia, arresting 35-year and 27-year old women in the Durack and Sherwood suburbs of Brisbane, a man, 26, in Wyndham Vale, Melbourne and a man, 30, in the Adelaide suburb of Croydon Park. They also seized fake passports, international driver licences and luxury handbags - plus, of course, a number of digital devices which will be subject to forensic examination.
The accused face multiple charges, including possession of false documents, dishonestly obtaining or dealing in personal financial information, dealing in proceeds of crime worth $A100,000 or more - charges which carry a maximum penalty of 20 years imprisonment.
AFP Media, Cybercrime syndicate dismantled after allegedly laundering $1.7 million, media release, 24 March 2023. Available online at https://www.afp.gov.au/news-media/media-releases/cybercrime-syndicate-dismantled-after-allegedly-laundering-17-million.
USB Keys Explode on Insertion
We are all well aware of the potential for malware to infect a system via USB keys, which is why it is so important to have a 'found devices' policy for all employees as well as a documented procedure for dealing with them inside IT/IS departments. This usually involves investigating their contents in a constrained and untrusted environment, such as an isolated throw-away machine or a revertible VM. However, from Ecuador comes news of a new challenge for junior analysts dealing with these devices.
In mid-March journalist Lenín Artieda, at Ecuadorian television station Ecuavisa, received a USB key through the mail - which, upon being inserted into a computer, exploded. Artieda was apparently unhurt and rapidly decamped for a safer location.
However, he was not alone - another journalist, Mauricio Ayora at TC Television, also received a USB key. Fortunately his employer had a strict policy about connecting devices to computers, and set it aside until after news of the first attack broke. And at Telemazonas, journalist Milton Perez also received a USB key, this time accompanied by a note clearly intended to lure the intended victim:
"This information will unmask (Ecuadorian political movement) Correísmo . If you think it's useful, we can come to an agreement and I'll send you the second part. I will communicate with you." (translation)
This time, sheer luck saved Perez - he did not insert the drive properly and it failed to detonate. However, police later confirmed that it contained explosive material, and they performed a controlled detonation of the device sent to TC Television.
So, add to your forensic toolkit: one long-handled extension for plugging suspect USB devices into computers, and a Kevlar containment sleeve to wrap around it. Stab vest and Kevlar protection for other body parts is optional.
Cluley, Graham, Danger USB! Journalists sent exploding flash drives, Bitdefender blog, 24 March 2023. Available online at https://www.bitdefender.com/blog/hotforsecurity/danger-usb-journalists-sent-exploding-flash-drives/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
CISA Releases Incident Response Tool for Microsoft Clouds
The Cybersecurity & Infrastructure Security Agency has released a new tool to help SOC analysts and threat hunters detect potentially malicious activity in Microsoft Azure, Azure Active Directory and Microsoft 365 environments. Untitled Goose adds novel authentication and data gathering methods in order to run a full investigation against these environments, enabling users to:
- Export and review AAD sign-in and audit logs, M365 unified audit log (UAL), Azure activity logs, Microsoft Defender for IoT (internet of things) alerts, and Microsoft Defender for Endpoint (MDE) data for suspicious activity.
- Query, export, and investigate AAD, M365, and Azure configurations.
- Extract cloud artifacts from Microsoft’s AAD, Azure, and M365 environments without performing additional analytics.
- Perform time bounding of the UAL.
- Extract data within those time bounds.
- Collect and review data using similar time bounding capabilities for MDE data.
Untitled Goose was developed by CISA with support from Sandia National Laboratories.
cisagov, untitledgoosetool, GitHub project, 23 March 2023. Available onlline at https://github.com/cisagov/untitledgoosetool.
New Security Features in Windows 11 Insider Preview Build 25324
The latest preview build of Windows 11 has a number of new features, some of them specifically related to security.
First of all, Windows is finally getting support for the SHA-3 family of hash digest functions, which won NIST's competition for a new hash function many years ago. Earlier hash functions like MD5 and the SHA-1 and SHA-2 series use the Merkel-Damgaard construction and are vulnerable to length extension attacks, which led NIST to search for an alternative. The winner was the Keccak algorithm, developed by a team including Joan Daemen (of AES/Rijndael fame), and which uses sponge construction, solving the length extension attack problem (and several others). The Windows CNG library will now support a range of SHA-3 and related functions:
- SHA3-256, SHA3-384, SHA3-512 (SHA3-224 is not supported)
- HMAC-SHA3-256, HMAC-SHA3-384, HMAC-SHA3-512
- extendable-output functions (XOF) (SHAKE128, SHAKE256), customizable XOFs (cSHAKE128, cSHAKE256), and KMAC (KMAC128, KMAC256, KMACXOF128, KMACXOF256).
The omission of SHA3-224 is of no real significance - the primary use of SHA2-224 was to prevent length extension attacks, and SHA3 is not vulnerable.
Other new features include support for camera selection for Windows Hello sign-in, and warnings against re-use of Windows passwords on sites and apps, including a UI warning on unsafe copy and paste.
Langowski, Amanda and Brandon LeBlanc, Announcing Windows 11 Insider Preview Build 25324, Windows Blog, 23 March 2023. Available online at https://blogs.windows.com/windows-insider/2023/03/23/announcing-windows-11-insider-preview-build-25324/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
NSA, CISA Issue Guidance on Identity and Access Management
Last September, we brought you news of the Supply Chain Working Panel of the Enduring Security Framework (ESF) - a cross-sector working group operating under the auspices of the Critical Infrastructure Partnership Advisory Council. Now, as part of the ESF, the Cybersecurity & Infrastructure Security Agency and the NSW have released a new paper advising best practice for Identity and Access Management (IAM). This is a major pain point for most defenders, since threat actors often exploit vulnerabilities in authentication and authorization services to compromise user credentials, achieve persistence by creating new accounts, and gain elevated privileges. Once they have achieved a toe-hold via compromised credentials, these techniques allow them to pivot and compromise additional systems in the victim network.
The paper discusses a number of mitigation techniques for these attacks:
- Identity Governance - policy-based centralized orchestration of user identity management and access control and helps support enterprise IT security and regulatory compliance;,
- Environmental Hardening - makes it harder for a bad actor to be successful in an attack;
- Identity Federation and Single Sign-On – Identity federation across organizations addresses interoperability and partnership needs centrally. SSO allows centralized management of authentication and access thereby enabling better threat detection and response options;
- Multi-Factor Authentication - uses more than one factor in the authentication process which makes it harder for a bad actor to gain access;
- IAM Monitoring and Auditing - defines acceptable and expected behavior and then generates, collects, and analyzes logs to provide the best means to detect suspicious activity.
The paper is very detailed and prescriptive; for each of the techniques above there are examples of why it matters, implementation guidance and recommended immediate actions. Well worth while reading and following - I am continually amazed that since NIST's SP 800-63 was updated in 2017, so few people have followed its advice and are still recommending very weak practices.
CISA, CISA and NSA Release Enduring Security Framework Guidance on Identity and Access Management, alert, 21 March 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/03/21/cisa-and-nsa-release-enduring-security-framework-guidance-identity-and-access-management.
Uncredited, Recommended Best Practices for Administrators: Identity and Access Management, technical report, March 2023. Available online at https://media.defense.gov/2023/Mar/21/2003183448/-1/-1/0/ESF%20IDENTITY%20AND%20ACCESS%20MANAGEMENT%20RECOMMENDED%20BEST%20PRACTICES%20FOR%20ADMINISTRATORS%20PP-23-0248_508C.PDF.
BreachForums Shuttered
Yesterday we reported on the arrest of BreachForums owner/operator Conor Brian Fitzpatrick, a.k.a. 'Pompompurin'. The hacker site continued to operate, however, being taken over by another administrator under the handle 'Baphomet'.
But less than a day later came news that Baphomet had taken the site down. In a message posted to the BreachForums Telegram channel, he stated, "You are allowed to hate me, and disagree with my decision but I promise what is to come will be better for us all", implying that some replacement might emerge.
It is possible that the shutdown was prompted by the possibility that law enforcement may have gained access to the site's code and information about its users.
Lakshamanan, Ravie, BreachForums Administrator Baphomet Shuts Down Infamous Hacking Forum, The Hacker News, 22 March 2023. Available online at https://thehackernews.com/2023/03/breachforums-administrator-baphomet.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
BreachForums Owner Arrested on Hacking Charges
One of the biggest sites for the sale of stolen databases is BreachForum, where hackers offer personal information such as usernames and passwords for sale and subseqent use in fraud. The site is owned and, until a few days ago was operated, by a hacker using the handle 'Pompompurin'.
However, the FBI has identified Pompompurin and last week arrested Conor Brian Fitzpatrick at his home in Peekskill, New York. The agent who led the arrest stated that Fitzpatrick had admitted to using the alias, and he is now scheduled to appear in a Virgina court this week to face charges of conspiracy to commit access device fraud, following his release on a $300,00 bond paid by his parents.
Meanwhile, Breachforums remains operational, having been taken over by another administrator under the handle 'Baphomet'.
Truță. Filip, Police Arrest BreachForums Owner ‘Pompompurin’ on Hacking Charges. Parents Bail Him Out, Bitdefender blog, 21 March 2023. Available online at https://www.bitdefender.com/blog/hotforsecurity/police-arrest-breachforums-owner-pompompurin-on-hacking-charges-parents-bail-him-out/.
Ferrari Hit By Ransomware Attack
Luxury carmaker Ferrari's Italian subsidiary, Ferrari S.p.A., has disclosed a ransomware attack by an unidentified threat actor which has exfiltrated customer contact data. The company received a ransom demand, but its policy is not to pay such a ransom since it only funds further criminal activity.
Instead, Ferrari has contacted the affected customers and hired a global cybersecurity firm to manage incident response and forensic investigation. The company has also informed the relevant authorities and is assisting investigations.
Ferrari owners in Italy should probably brace for upcoming identity theft attempts.
Ferrari N.V., Cyber Incident in Ferrari, news release, 21 March 2023. Available online at https://www.ferrari.com/en-EN/corporate/articles/cyber-incident-in-ferrari.
Summary of 2022 Zero-Day Exploitations
Incident response firm Mandiant has shared some highlights of the firm's analysis of zero-day exploitations during 2022. The company tracked 55 zero-day vulnerabilities which it believes were exploited - slightly down from 2021's record-breaking 81, but still almost triple the level of 2020.
As in previous years, Chinese state-sponsored cyber-espionage groups led the field, making more use of zero-days than other groups. The leading affected vendors are the ones with the broadest product ranges - Microsoft, Google and Apple - and the most affect product types were operating systems (19 exploits), browsers (11), security, network and IT management products (10) and mobile OS's (6).
Four exploitations were financially motivated - three of these linked to ransomware operations.
There's a lesson here for most of us on the defender side of this game: patches need to be deployed faster than ever before, especially on Internet-facing systems which are not on well-defended network segements inside multiple layers of firewalls. While patient zero literally gets no warning, most of us will get a chance to deploy security patches, if we are fast enough.
Sadowski, James and Casey Charrier, Move, Patch, Get Out the Way: 2022 Zero-Day Exploitation Continues at an Elevated Pace, blog post, 20 March 2023. Available online at https://www.mandiant.com/resources/blog/zero-days-exploited-2022.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Hinata Botnet Could Deliver 3.3 Tbps DDoS, Says Akamai
Akamai researchers have analysed a newly-discovered botnet which has been spreading over the first three months of this year. The malware, which its author appears to have christened 'Hinata' after an anime character, is written in the Go programming language which is increasingly popular among malware authors because it makes reverse-engineering the resultant binaries more difficult than other languages.
However, in Hinata, Go delivers another 'benefit', in the form of a multi-threaded design which can drive network I/O harder than a single-threaded approach. In early versions, the bot was able to run DDoS attacks using a variety of protocols: HTTP, UDP, TCP and ICMP. However, the latest version focuses on HTTP and UDP only. In order to spread, Hinata exploits two main vulnerabilities - a Hadoop YARN RCE and a vuln in the miniigd SOAP service of Realtek SDK devices (CVE-2014-8361). It can also exploit Huawei HG532 routers (CVE-2017-17215).
Based on their benchmark tests with a sample of the malware and a jury-rigged C2 server, the researchers found that with a 10-second UDP flood, the bot can generate 6,733 packets totaling 421 MB. If the botnet can marshall 10,000 nodes - roughly 7% of the size of the Mirai botnet - it could therefore deliver 336 Tbps.
The Akamai blog post is a nice example of malware analysis and reverse engineering. It provides IOC's, including YARA rules and sample infector scripts, as well as Snort rules.
Seaman, Chad, Larry Cashdollar and Allen West, Uncovering HinataBot: A Deep Dive into a Go-Based Threat, blog post, 16 March 2023. Available online at https://www.akamai.com/blog/security-research/hinatabot-uncovering-new-golang-ddos-botnet.
Privacy Breach Hits Australian Skin Cancer Study
Medical research institute QIMR Berghofer has been hit by a data privacy breach affecting the personal details of more than one thousand people participating in a skin cancer study, according to the institute. The breach occurred at a contractor, Datatime, which provides scanning and data entry services.
The 2021 QSKIN study involved the mailing of survey forms to 9749 participants, whose names and addresses were held by Datatime. 1128 participants completed the survey and returned the forms to Datatime, presumably for scanning, and their information, including name, address and Medicare numbers may have been compromised in the breach.
This particular breach occurred back in November 2022, and we reported on it at the time, so it is curious that QIMR Berghofer is only disclosing it publicly now. It also highlights the importance of supplier relationship management; the medical researchers relied on the fact that "Datatime is ISO Accredited" - but they are certified against ISO 9001, and not an information security related standard like ISO 27001.
Uncredited, Media statement, media statement, 20 March 2023. Available online at https://www.qimrberghofer.edu.au/news/media-statement/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Android Vulnerable to Spyware Apps, Say Researchers
In a forthcoming paper, to be presented at the Privacy Enhancing Technologies Symposium in Zurich this (northern hemisphere) summer, researchers from UCSD, Cornell and New York Universities will recommend that the Android mobile OS enforce stricter requirements on which apps can hide icons.
At present, it is possible for spyware apps to not appear in the launch bar when they initially open, and to masquerade under innocuous names like "Wi-Fi" or "Internet Service", making it difficult for victims to identify spyware planted on their devices by a disgruntled spouse, partner or other stalker. The apps also resist attempts to install them, and some will also automatically restart themselves after being stopped by the Android system or after reboots. “We recommend adding a dashboard for monitoring apps that will automatically start themselves", say the researchers.
A secondary concern is that spyware apps often do little to protect sensitive information they collect; for example, many do not encrypt data as they upload it to their command and control servers - and this includes the login credentials of the spyware purchaser themselves. On other cases, the uploaded data is stored using public URL's - some of them easily predictable - that makes the data easily accessible. One leading spyware service had an authentication vulnerability that would allow all the data, for every account, to be accessed by third parties.
There are several lessons here. Obviously, some spyware products rely on simple tricks to evade detection on the victim's phone, and Android could easily be enhanced to eliminate these. But also, people who buy and use spyware are placing themselves at risk.
Patringenaru, Ioana, This is What Happens When Your Phone is Spying on You, UC San Diego Today, 13 March 2023. Available online at https://today.ucsd.edu/story/spywarestudy2023.
Samsung Exynos Modem Chips Vulnerable, Says Google
Sticking with Android for a few moments longer: TechCrunch reports that Google's Project Zero security team has found 18 different zero-day vulnerabilities in the Samsung Exynos modem chips used in many different Android phones, wearables and even vehicles. These include four severe vulnerabilities which could be used to compromise a victim's phone "at the baseband level with no user interaction, and require only that the attacker know the victim's phone number", according to Project Zero head Tim Willis.
Among the affected devices - although there are more - are:
- Samsung mobile devices, including the S22, M33, M13, M12, A71, A53, A33, A21s, A13, A12 and A04 series;
- Vivo mobile devices, including those in the S16, S15, S6, X70, X60 and X30 series;
- Google Pixel 6 and Pixel 7 series (patched in the March security update);
- Connected vehicles that use the Exynos Auto T5123 chipset.
While they wait for patches, suggested user mitigations include turning off wi-fi calling and Voice-over-LTE in the device settings. The remaining 14 vulnerabilities are less severe since they require either access to the device or internal access to the cellular network systems.
Whittaker, Zack, Google warns users to take action to protect against remotely exploitable flaws in popular Android phones, TechCrunch, 17 March 2023. Available online at https://techcrunch.com/2023/03/16/google-warning-samsung-chips-flaws-android/.
Australian Taxation Office, Centrelink, Accounts Vulnerable to Voice Deepfake Attack
Both the Australian Taxation Office and the Commowealth social services agency Centrelink give their clients the option of verifying their identity over the phone using a "voiceprint" along with some other information. Now a Guardian journalist has discovered that using just four minutes of training audio they were able to use a machine learning-based voice cloning app to generate a synthetic voiceprint and then use this, along with their customer reference number, to gain access to their own account.
This would allow an attacker to access sensitive information held by either government agency, and illustrates the danger of relying such an easily-fakable characteristic as a form of biometric authentication. The same technique has been adopted by a number of banks and other agencies world-wide, who should perhaps be putting their efforts behind cryptographic techniques instead.
Evershed, Nick and Josh Taylor, AI can fool voice recognition used to verify identity by Centrelink and Australian tax office, The Guardian, 17 March 2023. Available online at https://www.theguardian.com/technology/2023/mar/16/voice-system-used-to-verify-identity-by-centrelink-can-be-fooled-by-ai.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
