Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
It's That Day Again . . .
It's Microsoft Patchday - the second Tuesday of the month (Wednesday for those of us on the leading side of the International Date Line) - and the Redmondites have served up a major update this month, fixing 74 CVE's and two advisories and requiring a heart-stoppingly-long no-video-out reboot of my Windows 11 machine.
The first of the two advisories is termed a 'defense-in-depth' update for Office which prevents exploitation of a remote code execution vulnerability leading to the Windows Search security feature bypass vulnerability (CVE-2023-36884) which was being actively exploited in the wild. The other fixes a missing resource section for a module of the hypervisor-protected code integrity tool (hvciscan_amd64.exe and hvciscan_arm64.exe).
There are also fixes for four vulnerabilities with CVSS 3.1 base scores of 9.8:
- a privilege escalation vulnerability in Exchange Server (CVE-2023-21709)
- a remote code execution vulnerability in MSMQ (CVE-2023-35385)
- another remote code execution vuln in MSMQ (CVE-2023-36910)
- a third (!) remote code execution vulnerability in MSMQ (CVE-2023-36911)
You know what to do . . .
MSRC, August 2023 Security Updates, security update guide, 9 August 2023. Available online at https://msrc.microsoft.com/update-guide/releaseNote/2023-Aug.
Adobe Releases Security Updates, Too
While you're updating, Adobe has released a number of updates to address multiple vulnerabilities. The relevant security bulletins are:
- Adobe Acrobat and Reader: APSB23-30
- Adobe Commerce: APSB23-42
- Adobe Dimension: APSB23-44
- Adobe XMP Toolkit SDK: APSB23-45
Adobe Commerce is, of course, based on the open-source Magento e-commerce merchant server, so users of that protidct should plan to update too.
UK Voter Information Leaked
The UK's Electoral Commission has disclosed a massive breach which occurred almost two years ago - and then wasn't discovered for a year. The attack was discovered in October 2022 and was reported almost immediately to the Information Commissioner's Office and the National Crime Agency. For a year prior, the still-unidentified threat actor had access to the names and addresses of 40 million voters in the UK who were registered from 2014 onwards.
However, the breach was only publicly disclosed this week, and has done enormous damage to the reputation of the Electoral Commission, although it would not have affected vote-counting, which remains a manual, paper-based process. On the other hand, if the responsible threat actor was associated with a nation state, the information gained could conceivably have been used in influence campaigns.
Asked why it took so long to disclose the breach, an Electoral Commission spokesperson said the Commission had needed to "remove the actors and their access to our system, assess the extent of the incident, liaise with the National Cyber Security Centre and ICO, and put additional security measures in place before we could make the incident public", adding that the attack "used a sophisticated infiltration method, intended to evade our checks" - which explains why it had evaded detection for so long, and reinforces suggestions of a state-affiliated advanced persistent threat.
Mason, Rowena and Hibaq Farah, Electoral Commission apologises for security breach involving UK voters’ data, The Guardian, 9 August 2023. Available online at https://www.theguardian.com/technology/2023/aug/08/uk-electoral-commission-registers-targeted-by-hostile-hackers.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cryptominer Targets Linux Systems Via Redis
A new and 'improved' variant of the SkidMap malware has been detected by Trustwave, using a honeypot in Central Europe. SkidMap was first reported by Trend Micro almost four years ago; its primary function is cryptomining, although it could be turned to other objectives by its operator.
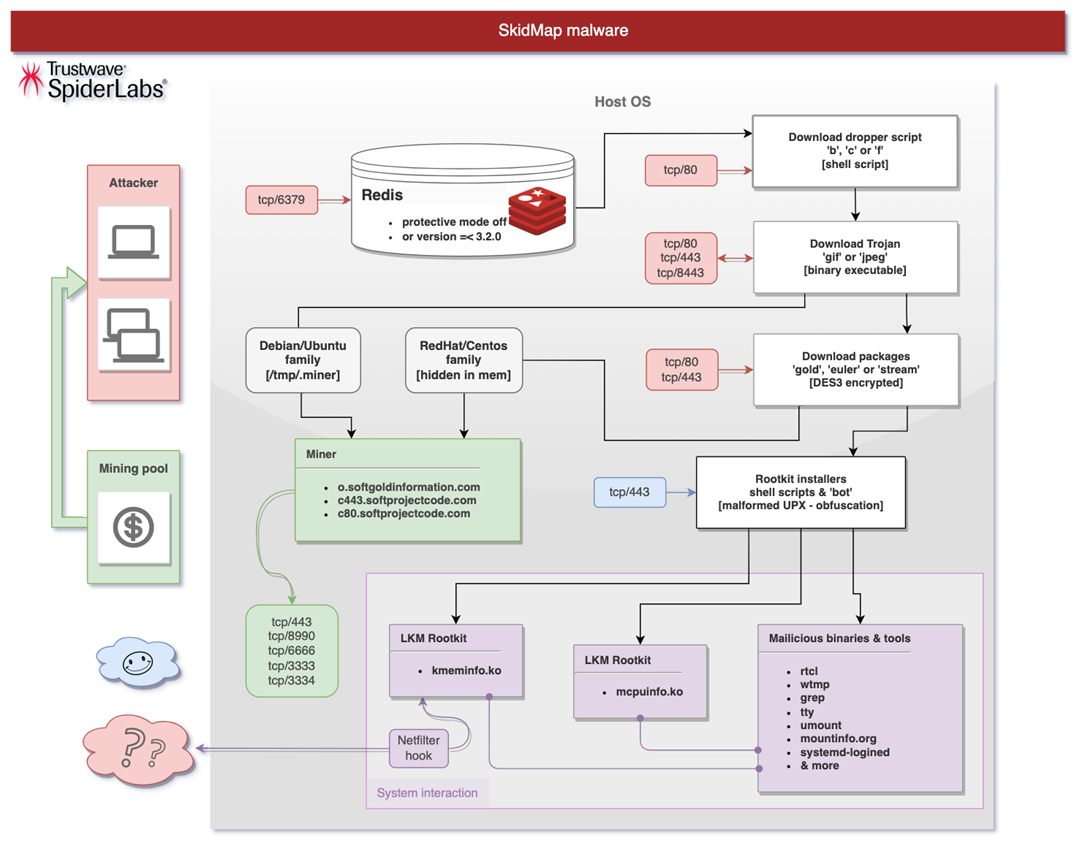
The SkidMap infection chain (image credit: Trustwave)
This latest variant initially infects its target via insecure Redis server installations - either versions prior to version 3.2.0 or instances running with protective mode disabled. The initial infection creates variables which contain base64-encoded cron jobs; when these run they will use either curl or wget to download and tun a dropper script.
The dropper, in turn, downloads an ELF executable called gif into /var/lib. When tun, this installs some SSH keys on the root account, disables SELinux, and then becomes persistent via the creation of more cron jobs; every hour the system creates a reverse shell which contacts the attackers' command and control server. The gif executable checks for various /etc/*-release text files to ascertain which Linux distribution it is running on, and depending on what it finds, it will download one of three different packages: 'gold', 'stream' or 'euler'.
Each package runs a series of shell scripts, cleaning up log entries which would indicate the infection and generally preparing the system for installation of a rootkit which consists of executables and Linux kernel modules. This will hide the operation of the ultimate payload, which is a cryptominer, but the rootkit modules have advanced functionality which go well beyond this - for example, allowing reconfiguring Netfilter to intercept network datagrams.
Once infection is complete, this malware is going to prove difficult to detect - it certainly evades ClamAV and Rkhunter, although Lynis and Chkrootkit do show indications of its presence. A better approach is to put some effort into securing vulnerable Redis installations in the first place, by installing version 3.2.0 or later, setting a strong password and using network segmentation to limit external access.
Zdonczyk, Radoslaw, Honeypot Recon: New Variant of SkidMap Targeting Redis, blog post, 2 August 2023. Available online at https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/honeypot-recon-new-variant-of-skidmap-targeting-redis/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
YAPC - Yet Another PaperCut Vulnerability
The PaperCut enterprise management system has been a high priority for threat actors for the last few months, as a series of vulnerabilities have allowed its exploitation by groups like Cl0p and LockBit, who have used it for information exfiltration prior to extortion demands.
Now researchers at Horizon3.ai have disclosed a new critical vulnerability, CVE-2023-39143. This is a directory traversal vulnerability which allows unauthenticated attackers to read, delete and upload arbitrary files to a vulnerable PaperCut MF/NG server, with the possibility of remote code execution if iinstalled on Windows with the external device integration setting enabled - which it is, by default, on some PaperCut versions such as PaperCut NG Commercial or PaperCut MF.
A simple command can check whether a PaperCut server is not patched and is running on Windows:
curl -w "%{http_code}" -k --path-as-is "https://<IP>:<port>/custom-report-example/..\..\..\deployment\sharp\icons\home-app.png"
Horizon3.ai notified PaperCut, and customers are advised to upgrade to the latest PaperCut version, that is, version 22.1.3 or later. If an upgrade cannot be installed, the most appropriate mitigation is to configure an allowlist of IP addresses which can access the PaperCut server.
What's the old saw? "If you see one rat, you probably have a lot more" - and the same applies to vulnerabilities.
Sunkavally, Naveen, CVE-2023-39143: PaperCut Path Traversal/File Upload RCE Vulnerability, blog post, 4 August 2023. Available online at https://www.horizon3.ai/cve-2023-39143-papercut-path-traversal-file-upload-rce-vulnerability/.
Deep Learning Acoustic Attack Learns Keyboard Text With 95% Accuracy
That clacking sound your keyboard makes as you type? It could be leaking passwords to a nearby smartphone, or even via a Zoom or Skype session with others. In fact, it could even work with a smartwatch.
In a paper presented at the 2023 European Symposium on Security and Privacy Workshops, three UK researchers detailed an acoustic side channel attack which uses a deep learning model to classify laptop keystrokes. When trained on keystrokes recorded by a nearby smartphone, the classifier achieved an accuracy of 95%, the highest accuracy seen without the use of a language model (which would use the redundancy of human language to achieve near-100% accuracy). When trained on keystrokes recorded over Zoom, the attack still managed an accuracy of 93%.
The researchers performed initial training by pressing each alphanumeric key on a 16-inch Macbook Pro 25 times, recording the sound each made. From this, they extracted the waveform of the isolated keystrokes and produced spectrograms - which chart the intensity of each frequency - and used these to train the CoAtNet image classifier, tweaking the parameters until they had optimized the classification accuracy. Since all recent Macbooks use the same keyboard and presumably sound similar, the attack could work against other users' machines.
The researchers' results provide further evidence that passwords are an increasingly weak form of authentication. While they suggest some mitigations, including varying typing techniques, making use of the Ctrl and Shift keys, backspacing and, obviously, using randomized passphrases. I would add that the use of a password safe to paste a random password into an on-screen form would provide a particularly strong defence. Nevertheless, it is increasingly obvious that we need to move to cryptographic authentication techniques such as security keys and passkeys.
Harrison, Joshua, Ehsan Toreini and Maryam Mehnezhad, A Practical Deep Learning-Based Acoustic Side Channel Attack on Keyboards, workshop presentation paper, 3 August 2023. Available online at https://arxiv.org/abs/2308.01074.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Boodhound Renamed, New Code Base
Bloodhound, the pen testing tool for Active Directory, has been revamped with a new name and a new code base. The application has two data collection tools, called SharpHound and AzureHound, which collect data from domain controllers and domain-joined Windows systems, such as:
- Security group memberships
- Domain trusts
- Abusable rights on Active Directory objects
- Group Policy links
- OU tree structure
- Several properties from computer, group and user objects
- SQL admin links
- Members of local admin, remote desktop, DCOM and remote management groups
- Active sessions
This data can then be loaded into the Bloodhound GUI for analysis, allowing exploration of possible attack paths (by both red teams and blue teams). While originally written as an open source project, Bloodhound was also commercialized and extended by SpectorOps to produce the SaaS Bloodhound Enterprise. However, over time, the two code bases diverged - in fact, the Enterprise version has a completely different architecture - and this increased the development workload substantially, since adding features meant writing, testing and maintaining two different versions of the same code.
However, SpecterOps is now (as of 8 August) releasing Bloodhound CE (Community Edition), which is based on the BloodHound Enterprise code base. This will eliminate a lot of duplicate effort in maintaining, supporting and extending the common code base.
Hinck, Stephen, Your new best friend: Introducing BloodHound Community Edition, blog post, 2 August 2023. Available online at https://posts.specterops.io/your-new-best-friend-introducing-bloodhound-community-edition-cb908446e270.
CISA Reports on 2022's Most-Exploited Vulnerabilities
A new report from the Cybersecurity & Infrastructure Security Agency, along with international partners, details the top 12 vulnerabilities exploited by threat actors in 2022 and draws lessons from them. Among the key findings:
- Threat actors exploted older software vulns more often than recently-disclosed vulnerabilities, taking advantage of proof-of-concept code to exploit victims who had delayed patching
- However, threat actors had the most success exploiting known vulns within the first two years after public disclosure - after that time, patches and upgrades reduced their success rates
- Threat actors seem to prioritize development of exploits for severe and globally prevalent CVE's, especially if they are more prevalent in their specific targets' networks. Only the more sophisticated actors also develop tools to exploit other vulnerabilities
The report encourages a number of mitigations for both developers and end users, including adoption of secure-by-design principles - but the most obvious less is that end user organizations need to accelerate their patch management programs.
CISA, 2022 Top Routinely Exploited Vulnerabilities, cybersecurity advisory, 3 August 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-215a.
Google Adds New Privacy Tracking Tools
Last year, Google introduced a new page called Results about you (https://goo.gle/resultsaboutyou) which will report search results which contain your personal phone number, home address or email. Now the page has been updated wth a new dashboard which will allow users to request remove of those results from Google Search, and will also provide notifications when new search results containing contact info turn up.
The page is initially available in the Google app, in the US, in English only. However, it will roll out to new locations and languages in the coming months.
Google has also announced that it will make it easier for user to remote explicit or intimate personal images from search results - an increasingly common problem for many young people today as they lose control of shared images which can then end up on web sites.
Romain, Danielle, New privacy tools to help you stay safe and in control online, Google Keyword, 3 August 2023. Available online at https://blog.google/products/search/new-privacy-tools/.
Clancy, Elizabeth Mary and Boanca Klettke, 20% of young people who forwarded nudes say they had permission – but only 8% gave it. Why the gap?, The Conversation, 4 August 2023. Available online at https://theconversation.com/20-of-young-people-who-forwarded-nudes-say-they-had-permission-but-only-8-gave-it-why-the-gap-207913.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
People Can't Reliably Distinguish Deepfakes
Finance departments everywhere are awake to the possibility of whaling attacks, in which a forged email, apparently from the CEO or another senior manager directs a significant payment to a new bank account. Such attacks can be highly profitable for cybercriminals, and highly damaging to the victims - in 2019, the US subsidiary of Japanese publisher Nikkei lost $US29 million to a whaling scam, while an earlier attack on European electrical manufacturer Leoni AG netted the attackers €44 million.
I might wish that defenders implemented a really strong control in the form of cryptographically signed emails; however, while S/MIME is reasonably easy to set up in an Active Directory domain, and there is always PGP, in practice this is rarely done. The default defence is to require an out-of-band confirmation that the email is authentic - for example, by calling the manager who requested this funds transfer and getting them to confirm the request. However, scammers have become proactive in defeating this safeguard: using captured samples of the manager's voice - obtained from analyst briefings, conference presentations and elsewhere - they train a machine learning model and then use an app to convincingly emulate their voice characters, in a process known as deep faking.
Now comes research showing that deepfake audio can trick people, even when they are expecting to hear AI-processed speech. Researchers at University College London asked over 500 people to identify speech deepfakes among multiple audio clips, using generic sentences in both English and Mandarin. While the subjects were able to correctly classify the deepfakes and authentic speech approximately 70% of the time, it is likely that real-world performance of this task is much worse, since people will not be primed to the fact that they could be hearing an artificial voice, and are likely to be caught off-guard.
However, this study did not challenge the listeners to verify a particular person as opposed to a deepfake, so there remains some hope.
Hsu, Jeremy, AI voices are hard to spot even if you know audio might be a deepfake, New Scientist, 2 August 2023. Available online at https://www.newscientist.com/article/2385752-ai-voices-are-hard-to-spot-even-if-you-know-audio-might-be-a-deepfake/.
NSA Releases Hardening Guide for Cisco Next-Gen Firewalls
The National Security Agency has released a cybersecurity technical report which provides best-practices guidance to systems and network administrators on configuring and hardening Cisco Secure Firewall (previously known as Cisco Firepower Threat Defense) appliances.
These next-generation firewalls (one wonders what we are going to call the next next generation of firewalls) combine filtering at both the network and application layers. They also provide URL filtering, user authentication, malware protection and intrusion prevention as well as Cisco's Application Visibility and Control for traffic shaping and congestion management.
The 36-page guide covers hardening of the FXOS operating system as well as access control and intrusion detection policies, SSL policies, malware and file policies and secure VPN settings.
NSA, Cisco Firewower Hardening Guide, cybersecurity technical report, August 2023. Available online at https://media.defense.gov/2023/Aug/02/2003272858/-1/-1/0/CTR_CISCO_FIREPOWER_HARDENING_GUIDE.PDF.
Cozy Bear Goes Phishing in Teams
A new report from Microsoft Threat Intelligence reveals that Cozy Bear - which Microsoft tracks as Midnight Blizzard, but is also known as NOBELIUM and APT29 - has been conducting a phishing campaign in search of the credentials of both government and non-government organization employees around the world. Cozy Bear is associated with the SVR, the Foreign Intelligence Service of the Russian Federation, and is focused on cyber-espionage.
In this particular campaign, the threat actors compromise the Microsoft 365 accounts of small businesses, rename them, add a new onmicrosoft.com subdomain and then use these to send Microsoft Teams chat messages while masquerading as a technical support or security team. They will then try to social-engineer the victim into approving a multi-factor authentication prompt.
This works because the messages will come from the legitimate onmicrosoft.com domain, which Microsoft 365 automatically uses when customers do not create a custom domain.
To date, the campaign has affected fewer than 40 organizations world-wide, all of whom have been notified by Microsoft.
Microsoft Threat Intelligence, Midnight Blizzard conducts targeted social engineering over Microsoft Teams, blog post, 2 August 2023. Available online https://www.microsoft.com/en-us/security/blog/2023/08/02/midnight-blizzard-conducts-targeted-social-engineering-over-microsoft-teams/.
Yet Another Mozilla Update
The Mozilla Foundation has released yet another round of security updates for its browsers. Many of the fixed vulnerabilities are high-severity. The affected products, with links to their related advisories are:
- Firefox 116: https://www.mozilla.org/en-US/security/advisories/mfsa2023-29/
- Firefox ESR 115.1: https://www.mozilla.org/en-US/security/advisories/mfsa2023-31/
- Firefox ESR 102.14: https://www.mozilla.org/en-US/security/advisories/mfsa2023-30/
You know what to do: Help -> About Firefox, and install the update.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
ACSC, CISA, NSA Joint Advisory on Web Application Access Control Abuse
The Australian Cyber Security Centre, US Cybersecurity & Infrastructure Security Agency and the US National Security Agency have released a joint cybersecurity advisory to address the risks posed by insecure direct object reference (IDOR) vulnerabilities. The advisory is aimed primarily at designers, architects and developers of web applications.
IDOR vulnerabilities are often easy to spot, which makes them attractive to threat actors. When you see something like this in the URL bar of your browser:
https://www.bigcorp.com/account/statement?acctid=320345465423
then you are looking at a likely IDOR. The object in question is your account with BigCorp, and the direct reference is the account ID or number appearing as a URL argument. The question that should immediately pop into the mind of a security-aware observer is: if the acctid was set to a different number, would the page display someone else's account statement? If it would, then that is an insecure direct object reference.
Of course, insecure direct references need not appear in the URL - they could equally well be hidden or visible form fields
The fact is, there is no need for this direct reference at all. In most cases, you have but one account with BigCorp, and 'you' are identified by a session token generated when you logged in and passed between server and browser in the form of a secure cookie (if you didn't need to log in, then the IDOR is not your biggest problem!). Since the server knows who you are, it also knows your account number, and there is no need for the client to pass it back, whether in the HTTP header of a POST request or in the URL of a GET request.
If you do have multiple accounts - for example, with a bank where the customer has a mix of cheque, savings, credit card and other accounts - then they can be referenced indirectly, for example by an index into an array of account references maintained within the server-side code, or even better, via a mapping which uses a cryptographically strong random value.
In practice, the presence of IDOR vulnerabilities signals deeper problems within a web application such as missing function level access control or even broken authentication and session management. The latter is near-inexcusable; every web developer should be familiar with good authentication and session management techniques, but in practice even that is not strictly necessary since many projects are based on platforms (such as WordPress, Joomla, etc.) and frameworks that provide the required code.
In my courses, I teach that web development projects should start with the selection of a suitable access control model; for many web applications this will be role-based access control (RBAC). And again, many platforms provide the required functionality in the form of flexibly-defined permissions which can be associated with roles and then allocated to users. Attendees at our CISSP Fast Track Review course have access to a basic relational database schema for RBAC and PHP code which will perform an access check on every user request, only allowing the code to run if that user occupies a role with the required permissions.
The joint advisory delves into more detail for developers, with a useful list of suggested mitigations:
- Implement secure-by-design and -by-default principles and practice in development methodologies
- Follow secure coding practices
- Test code to identify vulnerabilities
- Coduct role-based training for developers
- Exercise due diligence when selecting third-party platforms, frameworks or libraries
- Establish a vulnerability disclosure program
End-user organizations are offered a similar list:
- Exercise due diligence when selecting web applications
- Apply software patches for these applications as soon as possible
- Configure web applications to log and generate alerts from tampering attempts
- Create, maintain and exercise a basic cyber incident response plan and related crisis communications plan
- Conduct regular, proactive penetration testing
- Use dynamic application security testing tools and vulnerability scanners
- Use a web application firewall to filter, monitor and block malicious traffic
- Use a data loss prevention tool
- Immediately report detected vulnerabilities to the vendor or developer
- Consider establishing a vulnerability disclosure program
For each of these points, the advisory provides additional explanatory detail.
CISA, Preventing Web Application Access Control Abuse, cybersecurity advisory, 27 July 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-208a.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Linux Variant of P2PInfect Uses Different Initial Access Vector
A couple of weeks ago we covered a new worm which was spreading between systems running the Redis NoSQL database. A Windows version of P2PInfect was discovered by Palo Alto's Unit 42, who established that it was exploiting CVE-22-0543, a Lua sandbox escape vulnerability with a CVSS 3 score of 10.0. P2PInfect got its name because it builds a peer-to-peer command and control network, and we pointed out that this "would make it much more difficult to sinkhole and bring down, especially if it can grow further". And, as expected, it is growing further.
Researchers at Cado Security Labs have discovered a Linux variant of P2PInfect, which uses a different vector for initial access.
An important feature of Redis is its support for replication, which allows nodes configured as followers to acts as replicas of a leader, with the goal of high availability and failover. P2P exploits this capability by connecting to an Internet-exposed Redis instance and issuing the SLAVEOF command to make it a replica of their malicious leader. The attacker can then use the MODULE LOAD command to load a malicious .so (shared object - the Linux equivalent to a DLL) file which creates a reverse shell, allowing remote command execution on the compromised host. From there, it connects its C2 server to retrieve and install the primary payload.
P2PInfect also attempts initial access via a cron unauthenticated RCE mechanism - but this is less successful than the SLAVEOF technique.
The main payload is a backdoor, written in a combination of C and Rust. It then sets about reconfiguring the system, installing an additional SSH public key to allow persistent access, renaming binaries so that their use will escape detection, and adding firewall rules to allow it to join the threat actor's botnet. The botnet itself is well designed, serving payloads via HTTP, and using TLS for command and control via signed messages, with certificates for both server and client ends of a connection. And although some of the payload filenames suggest cryptomining, there was no evidence of cryptomining activity, although this may be started at a later date.
The Cado Security Labs blog provides a full analysis of the worm code, as well as IOC's and a YARA rule for detection.
Bill, Nate and Matt Muir, Cado Security Labs Encounter Novel Malware, Redis P2Pinfect, blog post, 31 July 2023. Available online at https://www.cadosecurity.com/redis-p2pinfect/.
Yet Another WordPress Plugin Is Vulnerable
One massive benefit of using WordPress as a content management system is its rich ecosystem of plugins which make it an easy platform for customization. But along with these plugins comes the need to secure code from developers who, or may not, be fully up to speed on secure web coding techniques.
Specialist WordPress security firm Patchstack has disclosed multiple vulnerabilities in the Ninja Forms plugin:
CVE-2023-37979 - a POST-based reflected cross-site scripting (XSS) vuln that allows privilege escalation (CVSS 3 score: 7.1)
CVE-2023-38386 - a broken access control vuln in the form submissions export feature affecting Subscriber role
CVE-2023-38393 - a broken access control vuln in the form submissions export feature affecting Contributor role
For those who are interested, the Patchstack blog post provides an analysis of the vulnerable code, but users - and there are over 900,000 active installations - should update the Ninja Forms plugin to at least version 3.6.26.
Muhammad, Rafie, Multiple High Severity Vulnerabilities in Ninja Forms Plugin, blog post, 27 July 2023. Available online at https://patchstack.com/articles/multiple-high-severity-vulnerabilities-in-ninja-forms-plugin/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Novel Backdoor Exploits Barracuda Email Gateways
Security appliance vendor Barracuda has had a torrid few months, starting with their May disclosure than a particularly aggressive and skilled threat actor had targeted their Email Security Gateway appliance by exploiting CVE-2023-2868, a remote command execution 0-day vulnerability. The threat actor, tracked as UNC4841 and likely of Chinese origin, used this to install a reverse shell and then, in turn, deploy a persistent backdoor called SEASPY.
So potent and persistent was SEASPY that Barracuda took the unprecendented step of offering customers a replacement device (or a virtual appliance) as they could not be confident that a firmware update could completely eradicate the malware.
Now comes news of yet another backdoor for the Barracuda ESG appliance. SUBMARINE is a novel persistent backdoor which runs with root privileges and lives in an SQL database on the device. It consists of multiple artifacts - an SQL trigger, shell scripts and a loaded library for a Linux daemon - that together enable persistence, command and control and cleanup.
According to a malware analysis report, the US Cybersecurity & Infrastructure Security Agency obtained seven malware samples containing the backdoor, as well as "associated Multipurpose Internet Mail Extensions (MIME) attachment files from the victim. These files contained the contents of the compromised SQL database, which included sensitive information". CISA also warns that this malware "poses a severe threat for lateral movement".
CISA has released three malware analysis reports detailing the original reverse shell and SEASPY backdoor, as well as the SUBMARINE backdoor. The reports provide a detailed analysis of each exploit, based on multiple malware samples, with hash values for all files, behavioural IOC's, YARA rules and other detections. Affected customers are urged to use these to check for indications of exploitation and lateral movement to other systems. They should also discontinue use of any compromised appliance and contact Barracuda support to obtain a new appliance.
Barracuda, Barracuda Email Security Gateway Appliance (ESG) Vulnerability, legal notice, 28 July 2023. Available online at https://www.barracuda.com/company/legal/esg-vulnerability.
CISA, CISA Releases Malware Analysis Reports on Barracuda Backdoors, cybersecurity advisory, 28 July 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/07/28/cisa-releases-malware-analysis-reports-barracuda-backdoors.
Larsen, Austin, et. al., Barracuda ESG Zero-Day Vulnerability (CVE-2023-2868) Exploited Globally by Aggressive and Skilled Actor, Suspected Links to China, blog post, 15 June 2023 (updated 28 July 2023). Available online at https://www.mandiant.com/resources/blog/barracuda-esg-exploited-globally.
Google Analyzes 0-day Exploits
Google has published its fourth annual year-in-review analysis of 0-day vulnerabilities exploited in the wild, extracting the major trends and lessons. Key findings include:
- Long patching delays on Android mean 0-days continue to work long after initial disclosure
- Mitigations in browsers have driven threat actors to shift from 1-click to 0-click exploits
- Over 40% of 0-days were variants of previously-reported vulnerabilities
- Attackers are independently discovering and exploiting the same vulnerabilities
The last point provides some reason for optimism; when an exploit is discovered and a fix released, there's an increasing chance that it will mitigate not only the original exploit but also others.
However, the news for Android users is not so good. The problem is the length of the Android supply chain, between the original device manufacturers, through Google, to the mobile device manufacturers. A good example is CVE-2022-38181, a vulnerability in the ARM Mali GPU kernel driver, which was reported to the Android security team in July 2022. While the Android team labeled the issue "Won't Fix" because it was device-specific, they referred it to ARM, who released a new driver version in October. However, in November Google's Threat Analysis Group discovered an exploit in the wold - yet it was not until April 2023 that a fix was incorporated in Android itself - that is, 9 months after the initial report.
There are similar delays affecting Android implementations from mobile device vendors - for example, in December 2022, the Threat Analysis Group discovered an exploit targeting the latest version of the Samsung Internet browser, which at that time was running on Chromium 102, released 7 months earlier in May 2022. This delay meant that the attackers could use CVE-2022-3038, which had been fixed in Chrome 105 of June 2022. The attack chain also used CVE-2022-22706, another ARM Mali GPU kernel driver vulnerability which had been fixed by ARM in January 2022 but did not appear in the Android Security Bulletin until June 2023 - 17 months after the patch was released and it was publicly known to be actively exploited in the wild.
This paints a rather depressing picture; threat actors don't need to research vulnerabilities themselves in order to produce 0-day exploits - instead, they can simply watch for them to be disclosed publicly, then use the information to work up n-day exploits which will produce results for months to come.
Stone, Maddie, The Ups and Downs of 0-days: A Year in Review of 0-days Exploited In-the-Wild in 2022 , blog post, 27 July 2023. Available online at https://security.googleblog.com/2023/07/the-ups-and-downs-of-0-days-year-in.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
CISA Releases Analysis of Critical Infrastructure Sectors
The US Cybersecurity & Infrastructure Security Agency has released an analysis and infographic summarising 121 risk and vulnerability assessments (RVA's) conducted across multiple critical infrastructure sectors in fiscal year 2022 (FY22).
The analysis provides a sample attack path, based loosely on 11 of the MITRE ATT&CK framework's 14 tactics, which threat actors could leverage to compromise an organization using weaknesses identified in the RVA's. It discusses the possible techniques used to achieve each tactic, from Initial Access through Execution, Persistence, Privilege Escalation, Defense Evasion and others to Lateral Movement, Collection, Command and Control and, finally, Exfiltration.
The infographic highlights the most successful techniques for each tactic that the RVA's documented, displayed as a pie chart with the size of each slice proportional to that technique's success rate.
While the RVA's, and consequently the analysis and infographic, are specific to critical infrastructure, they nonetheless provide useful awareness information for enterprises more generally.
CISA, CISA Releases Analysis of FY22 Risk and Vulnerability Assessments, cybersecurity advisory, 26 July 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/07/26/cisa-releases-analysis-fy22-risk-and-vulnerability-assessments.
CISA Vulnerability Summary
Speaking of CISA, the agency has released its summary of new vulnerabilities recorded in the NIST National Vulnerability Database (NVD) for the week of 17 July.
CISA, Vulnerability Summary for the Week of July 17, 2023, bulletin, 24 July 2023. Available online at https://www.cisa.gov/news-events/bulletins/sb23-205.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Australian Government Cheaps Out on Identity Management, Loses Half a Billion
For many years now, the Australian Government has been prone to placing faith in technology without really understanding it. We have seen this with debacles like the near-useless COVIDSafe contact-tracing app, which cost over $A20 million in total, and identified two (2) COVID-positive cases. We saw it with the Robodebt disaster, which was not only illegal but caused misery and even deaths. We saw it in the cancellation of the Australian Apprenticeship Management System.
To this viewer outside the Canberra bubble, it has seemed as though politicians, especially Ministers, had been captured by consultants with a surfeit of political connections over technical ability. In particular, previous governments have been resistant to sound principles of identity management, such as the development of a cryptographically-based or biometric personal identity for use by citizens transacting government business. Instead, they have relied on awkward schemes based on passwords, out-of-band verification using the PSTN (mTAN's) - in other words, six-digit numbers sent as a text message - and knowledge of identifiers such as the tax file number. These schemes are weak, deprecated (see NIST SP 80063B S5.1.3.3) or just plain silly.
By contrast, many European countries have implemented electronic identity cards which carry not only biometric data but also store a private key and certificate which can be used for authentication as well as to sign and verify documents and transactions. Why did the nation which wanted to become "one of the top three digital governments in the world ... that other nations can look to for guidance and inspiration" fall so far behind? (That was a rhetorical question.)
The IAM pigeon has come home to roost rather spectacularly with reports that more than half a billion dollars has been fraudulently claimed from the Australian Taxation Office (ATO), by criminals exploiting glaring loopholes in the linkage between the hokey MyGov system and taxpayer ATO accounts.
The fraud begins with a criminal creating a fake MyGov account, and then linking the new account to a genuine taxpayer's ATO account using easily-acquired identity information such as their tax file number (TFN) or date of birth. Some of this information is available cheaply on the dark web, obtained from previous data breaches or can be obtained by social engineering. The phone number in the ATO account is then changed so that mTAN's are sent to the fraudster, not the taxpayer, and the bank and email addresses are similarly changed. The fraudster then submits fake Business Activity Statements (BAS) and tax refund claims - which are paid to the changed bank account.
In the 2021/22 financial year, more than 7,500 accounts were compromised with over $A237 million paid, while in the 2022/23 financial year, the scam netted $A320 million from 8,100 compromised taxpayer accounts. That's a total of $A557 million.
It's past time for the ATO to pension off its hokey approaches to identity and access management and start doing things properly. And it's well past time for our politicians to look outside the Canberra bubble and find some competent consultants to advise them.
Charette, Robert N., Australia’s Digital Transformation Stumbles Badly: A new report finds a “litany of failures” in Australia’s attempt to digitize government services, IEEE Spectrum, 6 July 2018. Available online at https://spectrum.ieee.org/australias-digital-transformation-stumbles-badly.
Curnow, Sarah and Dan Oakes, ATO reveals more than $557 million claimed by fraudsters exploiting security loophole, ABC News, 26 February 2023. Available online at https://www.abc.net.au/news/2023-07-26/ato-reveals-cost-of-mygov-tax-identity-crime-fraud/102632572.
US SEC Tightens Cyber Governance, Risk Management and Incident Disclosure Requirements
The US Securities and Exchange Commission has adopted new rules requiring public companies to disclose material cybersecurity incidents and to annually provide information on their cybersecurity risk management, strategy and governance. In particular, reports of material incidents must now be made within four days, and will require a description of the material aspects of the incident's nature, scope and timing as well as its likely or actual impact on the company. The rules will require comparable disclosures by foreign share issuers.
An incident disclosure will be made in a new Item of Form 8-K and will require the following information:
- When the incident was discovered and whether it is ongoing;
- A brief description of the nature and scope of the incident;
- Whether any data were stolen, altered, accessed, or used for any other unauthorized purpose;
- The effect of the incident on the registrant’s operations; and
- Whether the registrant has remediated or is currently remediating the incident.
Annual reports will now require more consistent and informative disclosure of firms' approach to risk management, including a description of policies and procedures for the identification and management of cyber threats. Firms will also have to describe how the board and management oversee cyber risk:
- Whether the entire board, specific board members, or a board committee is responsible for the oversight of cybersecurity risks;
- The processes by which the board is informed about cybersecurity risks, and the frequency of its discussions on this topic; and
- Whether and how the board or board committee considers cybersecurity risks as part of its business strategy, risk management, and financial oversight.
Companies will also have to disclose whther they have a CISO and where the CISO reports, whether other management positions or committees are responsible for measuring and managing cyber risk and the processes by which they do so.
Annual reports will also require additional details of the cybersecurity expertise, if any, of board members, including prior work experience and certifications, as an aid to investors in making both investment and voting decisions. However, the Commission has also proposed a safe harbor providing that any directors identified as cybersecurity experts would not be deemed experts for liability purposes but also clarifying that the duties, obligations and liabilities of non-expert directors are not decreased, either.
Although these new rules only apply to companies traded on US exchanges, we can expect this approach to spread more widely, with other countries likely adopting similar requirements and liabilities of board members of private companies being similarly tightened. For CISO's, it means more formalisation of both risk management and incident response programs and a lot more communication with boards.
Securities and Exchange Commission, SEC Adopts Rules on Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure by Public Companies, press release, 26 July 2023. Available online at https://www.sec.gov/news/press-release/2023-139.
Securities and Exchange Commission, 17 CFR Parts 229, 232, 239, 240, and 249: Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure, final rule, 26 July 2023. Available online at https://www.sec.gov/rules/final/2023/33-11216.pdf.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.