Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Lazarus Group Targets IIS Via DLL Sideloading Attack
Researchers at South Korean security firm AhnLab has reported on a campaign being run by North Korean state-sponsored APT the Lazarus Group. The specific attack targets servers running a vulnerable version of Microsoft's Internet Information Server, achieving initial access via a DLL sideloading technique.
In this attack, the threat actor uses the IIS web server process, w3wp.exe, to place a malicious DLL named msvcr100.dll into the same directory as a normal application executable, Wordconv.exe. When they run Wordconv.exe, this loads and executes the malicious DLL, exploiting the well known DLL search path vulnerability in Windows: rather than only loading DLL's from the system library path, Windows will search the current working directory first and load the malicious DLL instead of the legitimate one.
msvcr100.dll is very similar to an earlier Lazarus Group DLL, cylvc.dll - it decrypts a data file called msvcr100.dat in order to create an executable file in memory, which it then runs, using yet another DLL called diagn.dll to decrypt and run another executable. This process resisted forensic analysis, but since it accesses the memory of the lsass.exe process, it is most likely a credential stealer. Once credentials have been acquired, the threat actor then performs network reconnaisance and pivots to other hosts, using the RDP protocol.
The AhnLabs report includes some analysis and IOC's.
muhan, Lazarus Group Targeting Windows IIS Web Servers, technical report, 23 May 2023. Available online at https://asec.ahnlab.com/en/53132/.
Breached? At Least Think About Changing Passwords
An alarming statistic gleaned from a survey of cybersecurity breaches released by the UK Department for Science, Innovation & Technology last month reveals that only 6% of businesses and 4% of charities updated passwords after their most disruptive breach or attack of the previous 12 months. This is an astonishingly low figure, even allowing for the fact it was based on the 32% of business and 24% of charity survey respondents that had identified a breach, rather than the full sample of respondents. It also leads one to wonder: the survey question asked about only "the most disruptive breach or attack" - how many of the respondents had suffered multiple breaches? Probably more than a few, if their lax password practices are any indication.
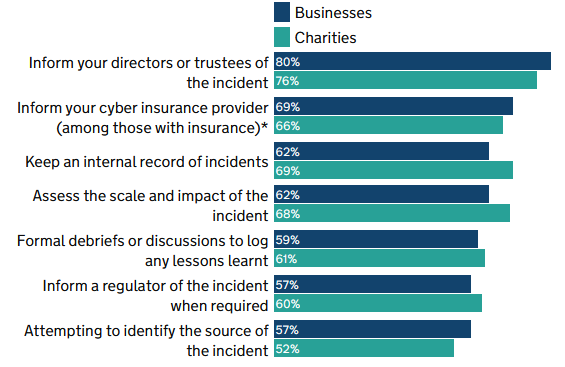
Percentage of organisations that say they take, or would take, the following actions following a cyber security incident (UK Government)
Some of the other statistics are quite alarming - for example, only 57% of businesses and 60% of charities would inform a regulator, and only slightly more would formally debrief to log any lessons learned.
Around one-third of businesses and a quarter of charities reported having experienced some kind of cybersecurity breach or attack in the previous 12 months, with larger businesses and high-income charities being more likely to identify breaches or attacks than small ones.
The report makes fascinating, albeit somewhat scary, reading.
Johns, Emma, et. al., Cyber security breaches survey 2023, UK Department for Science, Innovation & Technology, 19 April 2023. Available online https://www.gov.uk/government/statistics/cyber-security-breaches-survey-2023/cyber-security-breaches-survey-2023.
Stealthy Infostealer Targets Browsers, Crypto Wallets
From Trend Micro comes a report of a new infostealer called Bandit Stealer which is being promoted within the malware community. Bandit Stealer is written in the Go programming language, perhaps with cross-platform compatibility in mind, and makes use of sandbox detection techniques in order to evade detection and analysis by anti-malware products.
The malware attempts to achieve privilege elevation by using the runas.exe utility (a rough equivalent to *ix's sudo command). However, it fails - primarily due to the fact that to run as Administrator it will have to provide a password.
It also checks to see if it running in a container, sandbox, jail or any of several virtualization environments such as KVM, VirtualBox, VMware or Xen. However, while doing this, it also attempts to read /proc/self/status - a directory that only exists on Linux machines, indicating the intention of developing a cross-platform variant. It further downloads a text file containing hardware ID's, IP addresses, MAC addresses, usernames, hostnames and process names that might also indicate that is being run in a sandbox or test environment, and if it sees any of the blacklisted processes, it will attempt to terminate them. Again, the use of Linux-specific commands like pgrep and pkill indicate cross-platform intent.
Bandit Stealer goes on to create an autorun registry entry in order to persist through reboots, and then sets about collecting information, storing it in a vicinfo folder in the user's AppData\Local\ directory. It collects user and host information, Telegram sessions, login data, cookies, web history and credit card details from any of many different browsers, as well pilfering cryptocurrency wallets.
Initial infection seems to be through a drive-by or phishing malmails which carry a dropper.
The Trend Micro report provides a more detailed analysis and IOC's.
Camling, Sarah Pearl and Paul John Bardon, New Info Stealer Bandit Stealer Targets Browsers, Wallets, research report, 26 May 2023. Available online at https://www.trendmicro.com/en_us/research/23/e/new-info-stealer-bandit-stealer-targets-browsers-wallets.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Crisis Communications Vital When Handling Privacy Breaches
Two stories over the weekend demonstrate the importance of having a good crisis communications plan in place before a privacy breach occurs. In fact, the two cases - which involve government agencies - could almost be case studies in how not to respond to a privacy breach.
In the first case, NT Health, the health department of the Northern Territory (Australia), apparently mismanaged the transfer of patient health records as part of a software upgrade. Over 50,000 patients had their records transferred between two government departments in 2018 and 2019, but more than 3,000 identifiable records - some classed as very-high or high clinical risk, such as psychological reports, psychiatric facility visits, pregnancy terminations and stillbirth records and ECT records - were subsequently transferred to global software vendor Intersystems.
Then-health minister - now Territory Chief Minister - Natasha Fyles never made the privacy breach public. Instead, the breach was managed "in-house" and patients were never notified. There appears to be some disagreement between the Information Commissioner, Peter Shoyer, who claims his department provided only "brief advice ... on potential further steps" and NT Health Chief Executive Marco Briceno, who said his department "consulted extensively at the time with the information commissioner".
In the second case, Fire Rescue Victoria (FRV) was attacked in December of last year and its emergency dispatch system taken offline (and remains offline at time of writing, in late May!). However, in early March, applicants for firefighter positions received a letter disclosing that "FRV has reasonable grounds to believe that the personal information of firefighter recruit applicants may have been accessed or stolen by a malicious third party". The letter stated that the data had been shared on the dark web but offered no further details.
In fact, not only was identification and contact information compromised as part of a ransomware attack, but also medical records, passport and driver's licence details, Medicare numbers, Centrelink numbers, healthcare identifiers and potentially health information and superannuation details.
By not providing the affected people with full details of the personal information that had been compromised, FRV denied them the opportunity to take steps to protect themselves against further loss, such as obtaining new driver's licences and other identifiers. It is not clear how many individuals are affected, but they certainly number in the thousands - potentially every applicant for firefighter recruitment, and there are more than 5,000 applications each year.
Whether the agencies' handling of these incidents complies with the requirements of the Privacy Act 1988 (Cth) and, specifically, the Notifiable Breaches scheme is a matter for the Information Commissioner, but both involve personal health information and would seem to fall within the definition of a serious data breach. In any case, a reasonable person would expect to be notified when their personal information - especially health records - are compromised, so there is an argument that notification is simply a matter of applying due care.
Both cases, however, highlight the need for a well-considered data breach policy and incident response plan which covers crisis communcations and reputation repair. Failure to notify individuals seriously reduces public trust and confidence in the breached organizations - especially when a perceived cover-up makes the headlines. There is some evidence that full disclosure and transparency leads affected individuals to correctly attribute blame to cybercriminals and side - to a limited extent - with the affected organization, especially if it provides them with assistance and contacts to limit the damage.
Hislop, Jack, NT information commissioner seeks to distance himself from privacy breach of public health files, ABC News, 27 May 2023. Available online at https://www.abc.net.au/news/2023-05-27/nt-information-commissioner-privacy-breach-public-health-files/102397744.
Rizmal, Zalika, Fire Rescue Victoria's cyber-hack response a 'lesson in how not to communicate', ABC News, 27 May 2023. Available online at https://www.abc.net.au/news/2023-05-27/fire-rescue-victoria-data-hack-privacy/102400672.
Benoit, William L. “Image Repair Discourse and Crisis Communication.” Public Relations Review 23, no. 2 (June 1, 1997): 177–86.
Rikki Don't Lose That Phone
We all know that improper media sanitization before disposal leads to second-hand devices being sold with data intact and recoverable by the new owners. And, of course, if your device is stolen, there goes the opportunity to delete data and do a factory reset - so that devices bought from pawn shops and online trading sites have an even higher proportion of personal data on them.
But if you really want to cheaply acquire a lot of sensitive information, here's a source you may not have thought of: buying cellphones which are auctioned off by US police departments. It makes sense: phones which police have seized will often contain evidence of criminal activity - and in some cases, the police may have helpfully used forensic tools to provide privileged levels of access to information which would normally be protected, passing this information on to the new owner. If you're a drug dealer looking for new customers, your local police department could be a useful source of contacts!
Richard Roberts and his colleagues at the University of Maryland bought 228 police-auctioned cellphones at an average price of just $US18.00. Of these, 49 were completely unlocked and another used easily-guessable passcodes. In one case, police had used GrayKey mobile device forensics software to break into the phone, and had noted the passcode.
Several phones had stored credit card details - some legitimate and some stolen. The researchers also found scans of 5 passports and 14 driver's licences, as well as a few scans of government-issued identity credentials and some communication between sex workers and clients. As one might expect, there were also personal text messages, not to mention nude photographs.
With one phone, the researchers struck the motherlode: 24 credit reports, along with the related identity, bank account details, social security numbers and employment records - probably the work materials of an identity fraudster.
The fact that police forces do not destroy these devices or at least sanitize them is surprising, to say the least. It also highlights the importance of securing portable devices as well as the use of mobile device management software to remotely delete sensitive data when the device is lost or stolen - although subsequent use of forensic tools may defeat even that.
Roberts, Richard, Julio Poveda, Raley Roberts and Dave Levin, Blue Is the New Black (Market): Privacy Leaks and
Re-Victimization from Police-Auctioned Cellphones, preprint, IEEE Security & Privacy 2023. Available online at http://richard.technology/research/publications/ieeesp23_auctions.pdf.
Researchers Close Google CloudSQL Hole
Cloud applications often require a separate persistent data store, and so the cloud service providers typically offer both a NoSQL cloud-native database and a choice of the more popular SQL relational database engines, such as MySQL and Microsoft SQL Server. One problem service providers face is adapting and especially securing these databases for the cloud environment - they were originally developed for stand-alone operating system platforms. In the case of the open-source products like MySQL and PostgreSQL, the availability of the source code helps, but SQL Server is proprietary, and so cloud security needs to be added 'on top' rather than tightly integrated.
Understanding this led researchers at Dig Security to discover a rather nasty vulnerability in Google's CloudSQL implementation of SQL Server. The vulnerability allowed privilege escalation from basic CloudSQL user to becoming a full-fledged administrator on the SQL Server container. This was achieved in two steps: first, escalating from CustomerDbRootRole to DbRootRole, which is a Google Cloud Platform admin role, followed by exploitation of a misconfiguration which allowed a further escalation to the Sysadmin role.
This would grant full access to all data in the SQL server, as well as full access to the underlying operating system - not to mention access to service agents and some URL's which could allow pivoting to other environments.
Fortunately, the researchers collaborated with Google to resolve the underlying issues, presumably earning a nice bug bounty in the process.
Balassiano, Ofir and Ofir Shaty, GCP CloudSQL Vulnerability Leads to Internal Container Access and Data Exposure, blog post, 24 May 2023. Available online at https://www.dig.security/post/gcp-cloudsql-vulnerability-leads-to-internal-container-access-and-data-exposure.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
With an eye to the approaching weekend, some lighter reading in today's news brief:
Botnet Madness for Teens
From Scott J. Shapiro's new book, "Fancy Bear Goes Phishing", by way of IEEE Spectrum magazine, comes the fascinating tale of how an arms race between two sparring groups of teenagers, combined with an informal protection racket against Rutgers University, led to the creation of the Mirai botnet.
Shapiro, Scott J., The Strange Story of the Teens Behind the Mirai Botnet, IEEE Spectrum, 23 May 2023. Available online at https://spectrum.ieee.org/mirai-botnet.
Defending Against XPath Injection
One of the short topics I cover during our CISSP courses is the variety of injection attacks, with examples of both SQL injection and XML injection; there isn't time to go into the other types such as LDAP injection and command injection. One that I don't mention at all is XPath injection.
Trend Micro comes to the rescue here, with a nice, short but reasonably comprehensive tutorial on the topic. XPath - the XML Path Language - is used to query XML databases and it can be used by attackers in a manner similar to the more common SQL injection, retrieving information from the XML Document Object Model. In particular, with repeated queries, an attacker can 'crawl' the DOM, gradually recreating the entire XML document.
The Trend Micro tutorial walks the user through creating a simple Node.js application which queries an XML database, and then demonstrates some XPath injections. It then concludes with the defensive techniques, which are in some ways analogous to the SQL injection defenses: input sanitization, using parameterized XPath queries and using precompiled XPath queries.
Trend Micro DevOps Resource Center, Understanding XPath Injection Vulnerabilities, web page, 25 May 2023. Available online at https://www.trendmicro.com/en_us/devops/23/e/xpath-injection-vulnerabilities.html.
Exploiting SSH Public Keys for Fun and Profit
Finally, from The Hacker's Choice comes an interesting technique which exploits a little-known feature of OpenSSH in order to create a persistent backdoor on compromised systems.
OpenSSH public keys can be prefixed by various options - I bet you didn't know that, despite having read the Snail book, right? - and one of these options allows execution of a command. In the article, the author executes PowerShell to evaluate some commands, which are obscured by their conversion into a long hexdump string; the string is piped into the xxd hex dump utility to convert them back to text before evaluation.
The backdoor in this example is an installer, fetched from thc.org and then executed in memory before the user's normal shell is started.
It's a neat trick; SSH public keys are long base64-encoded strings anyway, and so at a casual glance, a long hex string will not draw attention. Generally, we can rely on a simple defence - the permission bits on ~/.ssh and the authorized_keys file within it, which will stop any other users having access to them, let alone editing a key:
drwx------. 2 username username 48 Feb 26 14:11 .
-rw-------. 1 username username 102 Jun 11 2022 authorized_keys
However, cloud instances often have keys loaded into them at boot time, and if an attacker was able to edit a root account or service key in, for example, a cloud management console . . .
Something to think about over the weekend.
root, Infecting SSH Public Keys with backdoors, blog post, 24 May 2023. Available online at https://blog.thc.org/infecting-ssh-public-keys-with-backdoors.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Chinese State-Sponsored Threat Actor Targets US Pacific Infrastructure
New reports from Microsoft and the NSA detail the activities of a stealthy cyber-espionage campaign against US critical infrastructure in the US and Pacific, particularly Guam. The threat actor involved, named Volt Typhoon, is a Chinese state-sponsored APT which has operated since mid-2021, and this campaign spans the communications, manufacturing, utility, transportation, construction, maritime, government, information technology, and education sectors with the likely long-term goal of disrupting critical communications infrastructure between the US and the Western Pacific rim in the event of any future crisis.
Volt Typhoon works hard to evade detection; once they have gained initial access - usually by compromising Fortinet FortiGuard devices - they leverage any privileges gained via the FortiGuard device, extract credentials for an Active Directory account used by the device and then pivot to other devices on the network, using these credentials. They also proxy all traffic to their targets through compromised SOHO routers, including those from ASUS, Cisco, D-Link, NetGear and Zyxel (these devices often have their admin interfaces exposed to the Internet - a very dangerous practice).
Having gained access, the Volt Typhoon operators exploit the target environment via the command line, typically using LOLbins and standard operating system commands such as wmic.exe and netsh.exe as well PowerShell. For example, the command
cmd.exe /c wmic path win32_logicaldisk get caption, filesystem,freespace,size,volumename
will return information about all local and network mounted drives on the system, including drive letter, format, free space, size (network drives shared from the same server usually show the same free space and size - a useful clue) and volume label. Since WMI tracing is disabled by default, this will escape detection, and by not introducing any backdoors or other malware, and by using existing accounts, the intruders will evade detection by EDR tools.
Typically, they will attempt to dump credentials from the LSASS (Local Security Authority Subsystem Service) for subsequent exfiltration, and to use the Ntdsutil.exe command to create installation media for new domain controllers, as the files in these contain usernames and password hashes which they can crack offline by means of dictionary or rainbow tables attacks. In a few cases, the Volt Typhoon operators will create a proxy on a compromised system by using the netsh portproxy command (another LOLbin) and very rarely they will use custom versions of the open-source Impacket and FRP (Fast Reverse Proxy) tools to establish a C2 channel.
The Microsoft report provides some guidance for mitigation and protection, including IOC's, while the associated NSA Joint Cybersecurity Advisory provides more detailed analysis and guidance.
Microsoft Threat Intelligence, Volt Typhoon targets US critical infrastructure with living-off-the-land techniques, blog post, 24 May 2023. Available online at https://www.microsoft.com/en-us/security/blog/2023/05/24/volt-typhoon-targets-us-critical-infrastructure-with-living-off-the-land-techniques/.
NSA, People's Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection, Joint Cybersecurity Advisory, May 2023. Available online at https://media.defense.gov/2023/May/24/2003229517/-1/-1/0/CSA_Living_off_the_Land.PDF.
XSS Campaign Targets WordPress Sites
Researchers at Wordfence, a vendor of a specialised web application firewall for WordPress, have revealed a large-scale attack exploiting Beautiful Cookie Consent Banner, a WordPress plugin which is installed on over 40,000 sites. This plugin is vulnerable to a Stored Cross-Site Scripting (XSS) exploit via the nsc_bar_content_href parameter in versions up to and including version 2.10.1 due to insufficient input sanitization and output escaping. This allows an unauthenticated attacker to inject arbitrary scripts into pages, which will then execute whenever a user accesses those pages. The vulnerability merits a CVSS score of 7.2 (high).
A partial patch was introduced in version 2.10.1 of the plugin, and the vulnerability was finally remediated in version 2.10.2 back in January. Wordfence recommends updating to the latest version, 2.13.0, as soon as possible (systems protected by their Wordfence firewall were always protected).
Wordfence's researchers suspect this campaign, which has run since early February, is being conducted by a single threat actor, as every attack contained the same payload - which in fact, failed to work. However, now that the vulnerability is being publicized, it seems likely a competent threat actor will adopt it, making reactive patching particularly important.
Gall, Ram, Wordfence Firewall Blocks Bizarre Large-Scale XSS Campaign, blog post, 24 May 2023. Available online at https://www.wordfence.com/blog/2023/05/wordfence-firewall-blocks-bizarre-large-scale-xss-campaign/.
Security Analyst Jailed for MitM Escalation
Finally, an enjoyable read for your coffee break, with the sad tale of a Security Analyst at a company which had fallen victim to a ransomware attack. Rather than working diligently on behalf of his employer to fend off the attack, the insider decided to turn the situation even further to his advantage, by substituting his own Bitcoin wallet addresses for those in the attackers' ransom demands, and additionally spoofing emails to increase the pressure to pay up.
Unfortunately, his man-in-the-middle exploit was foiled when his employer decided not to pay up - and even worse, his email interference showed up in system logs, leading to his arrest. Although it took 5 years for his case to finally come to court, he decided last week to plead guilty - presumably in hopes of a reduced sentence - and will return to Reading Crown Court for sentencing on 11 July.
South East Regional Organised Crime Unit, Man convicted of blackmail and other offences, press release, 22 May 2023. Available online at https://serocu.police.uk/man-convicted-of-blackmail-and-other-offences/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Kimsuky is Back With New Phishing Campaign
North Korean cyber-espionage APT Kimsuky is running a campaign targeting organizations that show an interest in the DPRK, including human rights activists, defector support organizations and information services, according to researchers at SentinelOne. Kimsuky has been active since at least 2012, engaging in spearphishing and social engineering campaigns to collect intelligence and access sensitive information in order to further the interests of the North Korean government,
In the new campaign, Kimsuky has shifted to using a variant of the RandomQuery malware; although RandomQuery has a range of capabilities including keylogging and dropping additional malware, this variant is used only to perform file enumeration and information exfiltration.
The malware is distributed using Microsoft Compiled HTML Help (CHM) files, which has long been Kimsuky's favourite technique. The group is also using a wider range of TLD's for their C2 infrastructure, including .space, .asia, .click and .online, although they also continue to use legitimate-looking names in the .com domain.
The Sentinel Labs report provides a full analysis of this RandomQuery variant, along with IOC's and a list of malicious domains.
Milenkoski, Aleksandar and Tom Hegel, Kimsuky | Ongoing Campaign Using Tailored Reconnaissance Toolkit, technical report, 23 May 2023. Available online at https://www.sentinelone.com/labs/kimsuky-ongoing-campaign-using-tailored-reconnaissance-toolkit/.
CISA Updates Ransomware Guidance
The US Cybersecurity & Infrastructure Security Agency, FBI, NSA and Multi-State Information Sharing and Analysis Center (MS-ISAC) have updated their #StopRansomware Guide in light of the accelerated tactics and techniques employed by ransomware groups since the initial release of the Guide in 2020. The update incorporates lessons learned from the past two years and includes additional recommended actions, resources, and tools to maximize its relevancy and effectiveness and to further help reduce the prevalence and impacts of ransomware.
The new Guide was developed through the Joint Ransomware Task Force, which was established by the US Congress in 2022 and is co-chaired by CISA and the FBI.
The Guide is available at https://www.cisa.gov/resources-tools/resources/stopransomware-guide.
Cybersecurity & Infrastructure Security Agency, CISA and Partners Update the #StopRansomware Guide, Developed through the Joint Ransomware Task Force (JRTF), alert, 23 May 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/05/23/cisa-and-partners-update-stopransomware-guide-developed-through-joint-ransomware-task-force-jrtf.
Windows Adds Support for .rar, .tar, .gz. (Groan)
Buried among a list of innovations being added to Windows - such as Window Copilot (an AI assistant) and a raft of other AI-powered extensions - is the announcement that the Redmondites are adding native support for additional archive formats, including tar, 7-zip, rar, gz and many others using the libarchive open-source project.
Oh, great. Windows' graphical shell already supports automatic opening and extraction of .zip and .iso formats, and while this is convenient, it has also been seized upon as a way for malware operators to get their product installed onto the systems of unsuspecting victims. Windows normally tags email attachments with the Mark of the Web, to mark them as unsafe and discourage victims from unsafe practices like enabling macros in these files.
However, Windows does not similarly tag the files inside these archive formats, allowing them to sneak past this defensive line. Now the bad guys will have a whole new set of archive filetypes, many of which will be unfamiliar to the unsuspecting victims.
Sigh. As for the privacy and security dangers of AI in the OS - well, that ship has sailed and pointing out the problems is like peeing into the wind.
Panay, Panos, Bringing the power of AI to Windows 11 – unlocking a new era of productivity for customers and developers with Windows Copilot and Dev Home, blog post, 23 May 2023. Available online at https://blogs.windows.com/windowsdeveloper/2023/05/23/bringing-the-power-of-ai-to-windows-11-unlocking-a-new-era-of-productivity-for-customers-and-developers-with-windows-copilot-and-dev-home/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
BlackCat Deploying New Signed Kernel Driver
One of the primary defences against the introduction of malware into systems, especially into the operating system itself, is the checking of digital signatures on installable software such as drivers. However, this defence is steadily weakening as malicious actors abuse Microsoft signing portals, use leaked and stolen certificates or make use of underground services to obtain valid code-signing certificates or Extended Validation certificates that are tied to real identities.
Now Trend Micro reveals details of a February 2023 attack by the BlackCat ransomware group in which they first attempted to deploy a Microsoft-signed driver which had previously been detected by Mandiant and was easily detected. Having failed with this approach, they switched to signing a new driver called ktgn.sys using cross-signing certificates which had been issued by Thawte to BopSoft and by VeriSign to YI ZENG. This allows the driver to be loaded on Windows systems, even when code signing policies are enforced.
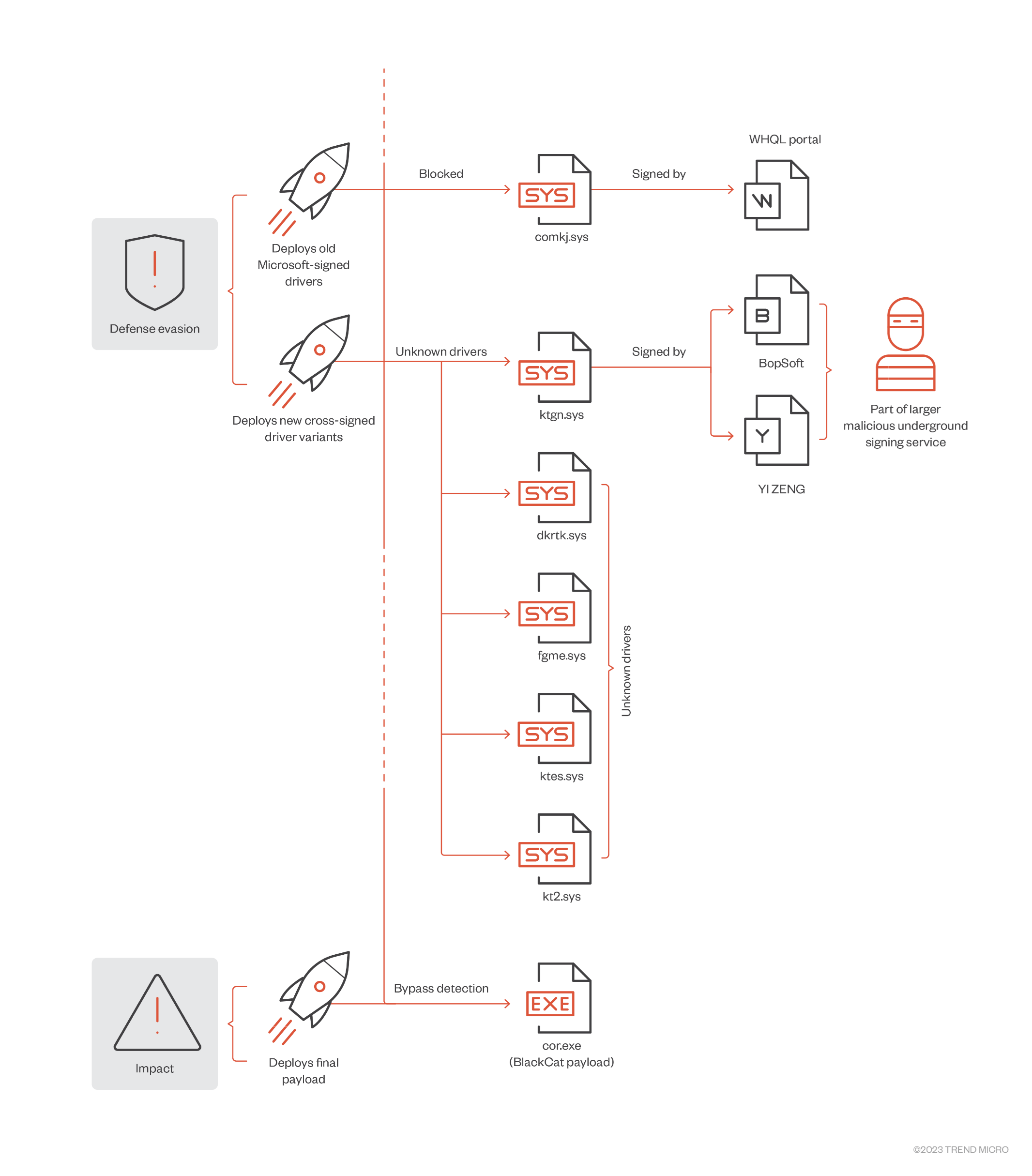
The files dropped by a BlackCat affiliate in the defence evasion phase. (Trend Micro)
The driver was dropped into the user temp directory by a VM-protected user agent, tjr.exe, which then installs the driver with start value = System, so that it will load when the system reboots. The code of the driver is obfuscated but its purpose is to use the IOCTL KillProcess call to kill security-related agent processes and evade detection. Furthermore, it does not register an unload callback process, so it can only be removed by deleting its registry key and rebooting.
The two issuers involved have both now revoked the certificates, but we can expect this technique to be used increasingly by threat actors. The Trend Micro report provides additional detail and recommended mitigation techniques.
Zohdy, Mahmoud, et. al., BlackCat Ransomware Deploys New Signed Kernel Driver, research report, 22 May 2023. Available online at https://www.trendmicro.com/en_us/research/23/e/blackcat-ransomware-deploys-new-signed-kernel-driver.html.
Possible Iranian Threat Actor Targets Saudi Arabia, Middle Eastern States
Still on the topic of kernel driver exploits, Fortinet reports on a campaign which utilises an interesting injection technique via a Windows kernel driver called WinTapix.sys. This driver essentially functions as a loader, making use of a position independent shellcode project called Donut, which can inject .NET assemblies, PE files and other Windows payloads into suitable processes and execute them, passing in any required parameters.
As in the case above, the WinTapix.sys driver is partially protected by virtualization to prevent reverse engineering, but Fortinet's analysts were able to work out the injection process as well as the resultant backdoor, encryption and proxy functionalities the tool provides. Their report provides a comprehensive analysis, IOC's, a mapping to the MITRE ATT&CK matrix and a rather nice graph of the attack flow.
Revay, Geri and Hossein Jazi, WINTAPIX: A New Kernel Driver Targeting Countries in The Middle East, blog post, 22 May 2023. Available online at https://www.fortinet.com/blog/threat-research/wintapix-kernal-driver-middle-east-countries.
Google Wants Higher-Quality Bug Bounty Submissions; Will Pay More
Google has announced a new quality rating system for security vulnerability reports, in an attempt to encourage more research in the higher-impact areas of its Android and Google Device products. The new system will rate vulnerability reports as High, Medium or Low quality based on the level of detail in the submission. The key elements desired are:
- Accurate and detailed description, identifying the product and with enough detail to allow maintainers to understand the issue and get to work on a fix
- Root cause analysis, describing why the issue occurs and what source code needs to be fixed
- Proof-of-concept, demonstrating the vulnerability
- Reproducibility, in the form of a step-by-step procedure which reproduces the vulnerability on an up-to-date device
- Evidence of reachability, demonstrating the type of issue and the level of access or execution obtained
Security researchers may well feel as though they have had their homework submission returned with a lower mark than they were expecting - but Google is now offering bug bounties of up to $15,000 through this program, which should ease the sting a little.
Jacobus, Sarah, New Android & Google Device Vulnerability Reward Program Initiatives, blog post, 17 May 2023. Available online at https://security.googleblog.com/2023/05/new-android-google-device-VRP.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
ASX Gives Up On Blockchain
In a final blow to that perennial solution in search of a problem, blockchain technology, the Australian Stock Exchange has announced that it has completely abandoned all attempts to replace its aging CHESS (Clearing House Electronic Subregister System) settlement system with the once-charismatic 'solution'. In November last year, we reported that the ASX had halted the project following an independent review, taking a $A250 million loss in the process.
Now the exchange has stated that it is considering its options to replace CHSS, but that any attempt will not involve blockchain or distributed ledger technology. At a meeting with participants, project director said that, "while we continue to explore all the options, certainly we will need to use a more conventional technology than in the original solution in order to achieve the business outcomes".
New York blockchain tech form Digital Asset had hoped that the project would be resurrected, but those hopes are now dashed.
Kaye, Byron, Australian stock exchange says software overhaul won't involve blockchain, Reuters, 19 May 2023. Available online at https://www.reuters.com/markets/australian-stock-exchange-says-software-overhaul-wont-involve-blockchain-2023-05-19/.
Low Earth Orbit Satellites Vulnerable to Jamming
Few realise the extent to which our lives have been changed by low earth orbit satellites. One obvious example is the disappearance of maps, atlases and street directories for driving; almost everyone has switched to GPS-based navigation systems, which utilise signals from a constellation of satellites continually orbiting the earth.
A more recent innovation is the provision of Internet access via SpaceX's Starlink network of low earth orbit satellites, which have proven popular with RV'ers and users in remote areas, as well as institutions - such as our local council - which are signing up in order to have a backup service in case of outages in terrestrial services.
However, in a world of international tensions, these satellite services are highly vulnerable to attack. Unlike the higher-orbit geostationary satellites, which remain over a fixed position on the earth's surface, low earth orbit communications satellites appear over the horizon, zoom (roughly) overhead and disappear again, meaning that they must frequently hand over their ground station connections to the next satellite of the constellation. This handover introduces delays and opens up more more surface for interference, according to Mark Manulis, professor of privacy and applied cryptography at the Universite of the Federal Armed Forces Cyber Defense Research Institued in Munich.
We have previously seen jamming and spoofing of GPS satellites, affecting shipping in the Black Sea and airliners around the Kaliningrad region, Eastern Finland, the Black Sea and the Eastern Mediterranean area, prior to, but especially since the beginning of, the Russian invasion of Ukraine. While the Starlink satellites transmit at higher power levels, mking them harder to jam than GPS, Elon Musk has already claimed that SpaceX has seen attempts to jam the system. In addition, Russia's defence agencies commissioned a system called Tobol which is intended to counter attempted jamming of their own satellites - indicating that they have already done considerable work in this area.
A report in IEEE Spectrum claims that commercial satellites are nowhere near the level of security found in military satellites, and considerable work is now in progress to remediate this situation.
Laursen, Lucas, Satellite Signal Jamming Reaches New Lows: Starlink and other LEO constellations face a new set of security risks, IEEE Spectrum, 18 May 2023. Available online at https://spectrum.ieee.org/satellite-jamming.
Understanding Hackers Vital, Says Lawyer
A new book from the founding director of Yale University's Cybersecurity Lab, lawyer Scott Shapiro, makes the case that we can only effectively tackle cybercrime if we understand not only how people hack, but why. In "Fancy Bear Goes Phishing", Shapiro examines several case studies such as the hacking of Paris Hilton's T-Mobile Sidekick and the infamous Morris Worm, to extract some important lessons.
In an interview in New Scientist, he explains why he has made available a free online hacking course, and talks about the futility of purely technical defences.
Adam, David, Knowing how to hack will be vital in a cybercrime-filled future, New Scientist, 16 May 2023. Available online at https://www.newscientist.com/article/mg25834390-100-knowing-how-to-hack-will-be-vital-in-a-cybercrime-filled-future/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Vuln Exposes KeePass Master Password; PoC Available
A vulnerability in the dialog used by password safe program KeePass to accept the user's master password and decrypt its database allows an attacker to extract that master password. The vulnerability (CVE-2023-32784) allows an attacker to reconstruct the master password from a process memory dump from KeePass version 2 on Windows (version 1.x is unaffected).
Given the difficulty of obtaining that dump remotely, the vulnerability is probably not that severe; if the system is already infected, however, there is a possibility that the intruder could obtain passwords for other systems, sites and applications.
The flaw is in SecureTextBoxEx, a Windows.Forms.TextBox control used to enter passwords. Said its discoverer, vdohney,
"The flaw exploited here is that for every character typed, a leftover string is created in memory. Because of how .NET works, it is nearly impossible to get rid of it once it gets created. For example, when "Password" is typed, it will result in these leftover strings: •a, ••s, •••s, ••••w, •••••o, ••••••r, •••••••d."
vdohney has also created a proof-of-concept which searches the dump for these patterns and offers a likely password character for each position in the password.
The good news is that the KeePass developers have already worked out a fix, which will be in KeePass version 2.54 and should be available in early June. Meanwhile, a workaround is that the PoC does not work if the password is copied and pasted into the form via the clipboard.
Dammit - only yesterday I was recommending KeePass to an audience, and now this happens! 😞
vdohney, Security - Dumping Master Password from Memory, Even When Locked, discussion thread, 1 May 2023. Available at https://sourceforge.net/p/keepass/discussion/329220/thread/f3438e6283/#0829.
vdohney, KeePass 2.X Master Password Dumper (CVE-2023-32784), GitHub project, 5 May 2023. Available online at https://github.com/vdohney/keepass-password-dumper.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
TP-Link Routers Targeted by Chinese APT
Checkpoint researchers have revealed a campaign, aimed at European foreign affairs entities, which they have linked to a Chinese state-sponsored APT they refer to as Camaro Dragon, and which has similar TTP's to a previously-identified APT named Mustang Panda.
The campaign utilises malicious firmware implants for TP-Link routers. The implants have several malicious components including a custom backdoor named Horse Shell which provides the attackers with persistent access and enables lateral movement into compromised networks. This technique, of compromising Internet-facing network devices and modifying their software or firmware, is a long-standing favourite of Chinese APT's.
The Checkpoint article provides an analysis of the Horse Shell backdoor, which is a MIPS32 ELF implant, written in C++. Its main capabilities are:
- A remote shell which allows execution of arbitrary shell commands on the infected device
- File transfer to and from the infected device
- A SOCKS proxy, allowing relay of communication between infected devices
The shell is firmware-agnostic, and can be integrated into the firmware of devices from different vendors, although the exploit which is used for initial access is not yet clear.
Cohen, Itay, Radoslaw Madej, et. al., The Dragon Who Sold His Camaro: Analyzing Custom Router Implant, technical report, 16 May 2023. Available online at https://research.checkpoint.com/2023/the-dragon-who-sold-his-camaro-analyzing-custom-router-implant/.
Four RCE Vulns in Cisco Small Business Series Switches
Cisco has released an advisory warning of four critical RCE vulnerabilities in the web-based user interface of products in their Small Business Series switches. The vulnerabilities are:
- CVE-2023-20159 (CVSS score 9.8): A stack buffer overflow
- CVE-2023-20160 (CVSS score: 9.8): An unauthenticated BSS buffer overflow
- CVE-2023-20161 (CVSS score: 9.8): An unauthenticated stack buffer overflow
- CVE-2023-20024 (CVSS score: 8.6): An unauthenticated heap buffer overflow
The following products are affected:
- 250 Series Smart Switches
- 350 Series Managed Switches
- 350X Series Stackable Managed Switches
- 550X Series Stackable Managed Switches
- Business 250 Series Smart Switches
- Business 350 Series Managed Switches
- Small Business 200 Series Smart Switches
- Small Business 300 Series Managed Switches
- Small Business 500 Series Stackable Managed Switches
The 220 Series and Business 220 Series smart switches are not affected.
Cisco has released free software updates which fix these vulnerabilities, and Cisco customers are advised to update as soon as possible.
Cisco, Cisco Small Business Series Switches Buffer Overflow Vulnerabilities, security advisory, 17 May 2023. Available online at https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sg-web-multi-S9g4Nkgv.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Who Should Attempt the CISSP Exam?
I'm often asked who the CISSP certification is aimed at; my university students typically ask whether they should attempt the certification before or while in their first job, for example (almost certainly not, for the undergraduates - they usually could not meet the experience requirements, while some of the Masters students could).
Primarily, the CISSP is for those who are moving upwards from a technical background in one or a few of the CBK Domains (e.g. network security, security architecture, etc.) into a management or supervisory position where they will need to:
- utilise a broad understanding of the other domains, to which they may already have had some exposure
- supervise technical professionals across all or most domains
- understand how *all* aspects of security need to be covered in balance, and
- communicate - in *both* directions - with senior management, that is, not just advise management.
The last point is probably the key one. Communication to management will mainly involve translating technical assessments of threats, vulnerabilities, etc. into business risk which management can relate to their existing understanding of risk, and this is a key reason why cybersecurity risk assessment processes and risk matrices, etc. should be aligned with the existing risk management processes across the rest of the enterprise.
But it also works the other way: translating senior management business concerns and requirements into technical security requirements. Once managers understand the risks posed to the assets they own, in part due to the business processes they rely upon, it is up to them to decide the level of risk they will accept. This is a business decision, and not one that security professionals are equipped to make.
Although some of this operates at the level of C-suite and board concerns with governance and policy, some of it involves other managers' specific concerns with opportunities presented by new technologies (cloud, apps, machine learning, related privacy issues), etc. as well as managing risks associated with specific business processes or information assets as they change.
In any case, I have found a security governance and management course is of benefit to students and practitioners who are still in the early stages of their career. Many tend to focus tightly on their particular interests or immediate job concerns - typically penetration testing, which is always an attractive aspect of cybersecurity for novices (something I don't understand - long hours, lots of reverse engineering and disassembling code, keeping on top of the latest vulnerabilities and exploits; I'd burn out).
However, a governance and management course helps them put it all in perspective and realise a) that their particular role is far from the only one needed in any large enterprise, let alone the most important one, and b) how their role fits in and the factors which influence the demand for their services. It certainly rounds them out as a professional.
For undergraduate students in cybersecurity, governance, risk and management is sometimes offered as a third-year subject; it's usually found in Masters programs. But for those already in the workforce, or who have not completed a specialist cybersecurity degree, tackling the CISSP - whether by self-study or a course - is probably the best way to get a comprehensive overview of the other areas of the field, how they all fit together, and how they are managed.
All this leads me to conclude that, right now, the CISSP is not of value just to the CISO level, especially in larger enterprises.
A Look Inside the Bulgarian 'Virus Factory'
A fascinating read in The Guardian last week provides an insight into the minds of competitive young virus authors in Bulgaria in the 1980's. These were the heady days of virus development, where curiosity was the driving force, in a search for new techniques to infect the MS-DOS systems of the era. It was a kinder, gentler time, when the massive profits provided by ransomware had not yet become a factor.
Shapiro, Scott J, On the trail of the Dark Avenger: the most dangerous virus writer in the world, The Guardian, 9 May 2023. Available online at https://www.theguardian.com/news/2023/may/09/on-the-trail-of-the-dark-avenger-the-most-dangerous-virus-writer-in-the-world.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.