Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
BlackCat Deploying New Signed Kernel Driver
One of the primary defences against the introduction of malware into systems, especially into the operating system itself, is the checking of digital signatures on installable software such as drivers. However, this defence is steadily weakening as malicious actors abuse Microsoft signing portals, use leaked and stolen certificates or make use of underground services to obtain valid code-signing certificates or Extended Validation certificates that are tied to real identities.
Now Trend Micro reveals details of a February 2023 attack by the BlackCat ransomware group in which they first attempted to deploy a Microsoft-signed driver which had previously been detected by Mandiant and was easily detected. Having failed with this approach, they switched to signing a new driver called ktgn.sys using cross-signing certificates which had been issued by Thawte to BopSoft and by VeriSign to YI ZENG. This allows the driver to be loaded on Windows systems, even when code signing policies are enforced.
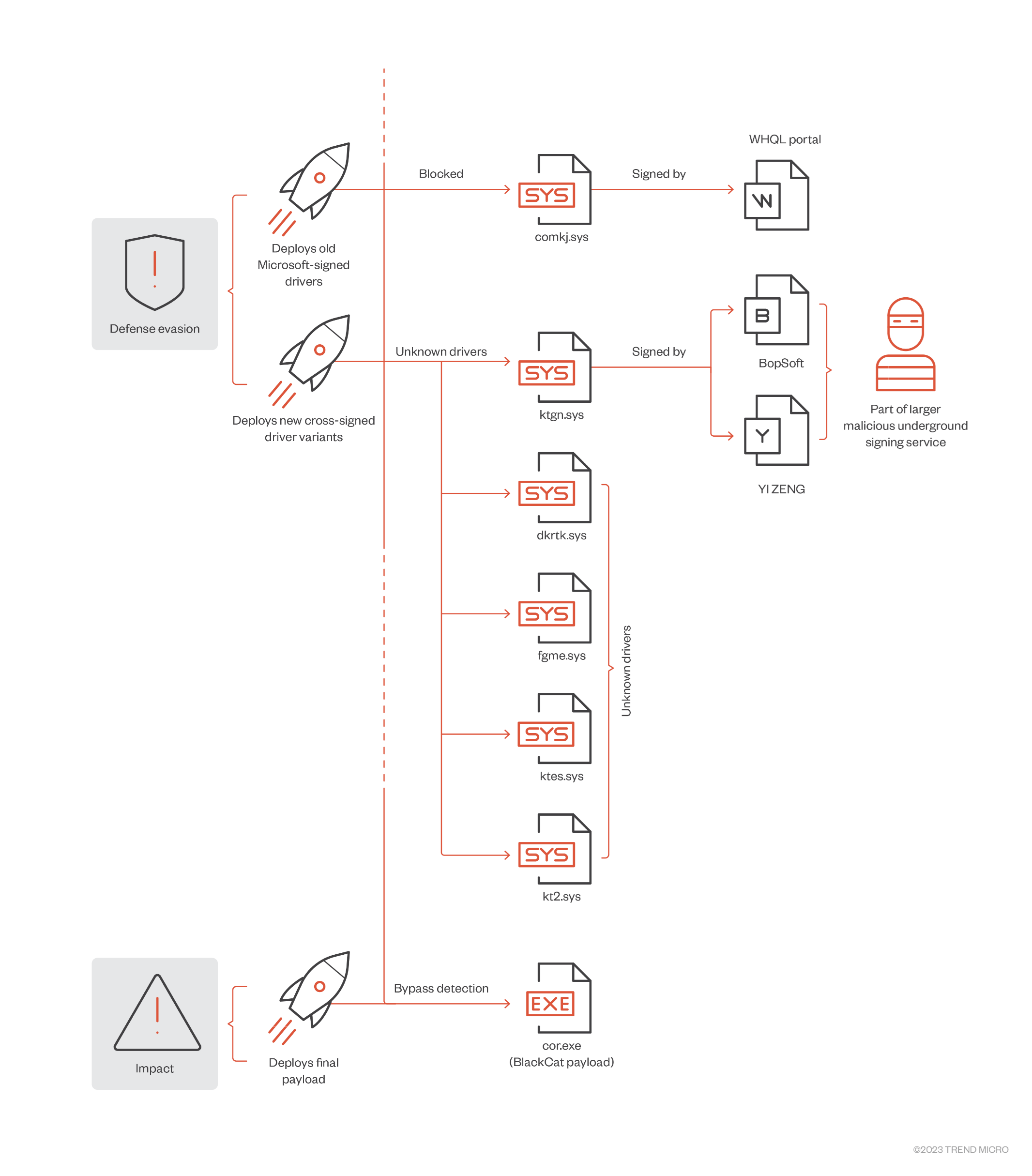
The files dropped by a BlackCat affiliate in the defence evasion phase. (Trend Micro)
The driver was dropped into the user temp directory by a VM-protected user agent, tjr.exe, which then installs the driver with start value = System, so that it will load when the system reboots. The code of the driver is obfuscated but its purpose is to use the IOCTL KillProcess call to kill security-related agent processes and evade detection. Furthermore, it does not register an unload callback process, so it can only be removed by deleting its registry key and rebooting.
The two issuers involved have both now revoked the certificates, but we can expect this technique to be used increasingly by threat actors. The Trend Micro report provides additional detail and recommended mitigation techniques.
Zohdy, Mahmoud, et. al., BlackCat Ransomware Deploys New Signed Kernel Driver, research report, 22 May 2023. Available online at https://www.trendmicro.com/en_us/research/23/e/blackcat-ransomware-deploys-new-signed-kernel-driver.html.
Possible Iranian Threat Actor Targets Saudi Arabia, Middle Eastern States
Still on the topic of kernel driver exploits, Fortinet reports on a campaign which utilises an interesting injection technique via a Windows kernel driver called WinTapix.sys. This driver essentially functions as a loader, making use of a position independent shellcode project called Donut, which can inject .NET assemblies, PE files and other Windows payloads into suitable processes and execute them, passing in any required parameters.
As in the case above, the WinTapix.sys driver is partially protected by virtualization to prevent reverse engineering, but Fortinet's analysts were able to work out the injection process as well as the resultant backdoor, encryption and proxy functionalities the tool provides. Their report provides a comprehensive analysis, IOC's, a mapping to the MITRE ATT&CK matrix and a rather nice graph of the attack flow.
Revay, Geri and Hossein Jazi, WINTAPIX: A New Kernel Driver Targeting Countries in The Middle East, blog post, 22 May 2023. Available online at https://www.fortinet.com/blog/threat-research/wintapix-kernal-driver-middle-east-countries.
Google Wants Higher-Quality Bug Bounty Submissions; Will Pay More
Google has announced a new quality rating system for security vulnerability reports, in an attempt to encourage more research in the higher-impact areas of its Android and Google Device products. The new system will rate vulnerability reports as High, Medium or Low quality based on the level of detail in the submission. The key elements desired are:
- Accurate and detailed description, identifying the product and with enough detail to allow maintainers to understand the issue and get to work on a fix
- Root cause analysis, describing why the issue occurs and what source code needs to be fixed
- Proof-of-concept, demonstrating the vulnerability
- Reproducibility, in the form of a step-by-step procedure which reproduces the vulnerability on an up-to-date device
- Evidence of reachability, demonstrating the type of issue and the level of access or execution obtained
Security researchers may well feel as though they have had their homework submission returned with a lower mark than they were expecting - but Google is now offering bug bounties of up to $15,000 through this program, which should ease the sting a little.
Jacobus, Sarah, New Android & Google Device Vulnerability Reward Program Initiatives, blog post, 17 May 2023. Available online at https://security.googleblog.com/2023/05/new-android-google-device-VRP.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.