Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Qakbot Annual Evolution Continues
The operators of the Qakbot banking trojan - also known as Qbot and Pinkslipbot - have a pattern of taking the northern summer months off to, presumably, take some time off and also to refresh their tactics and the malware code. Researchers from Lumen's Black Lotus Labs have reported on the latest incarnation of Qakbot, which has evolved new initial infection and C2 techniques.
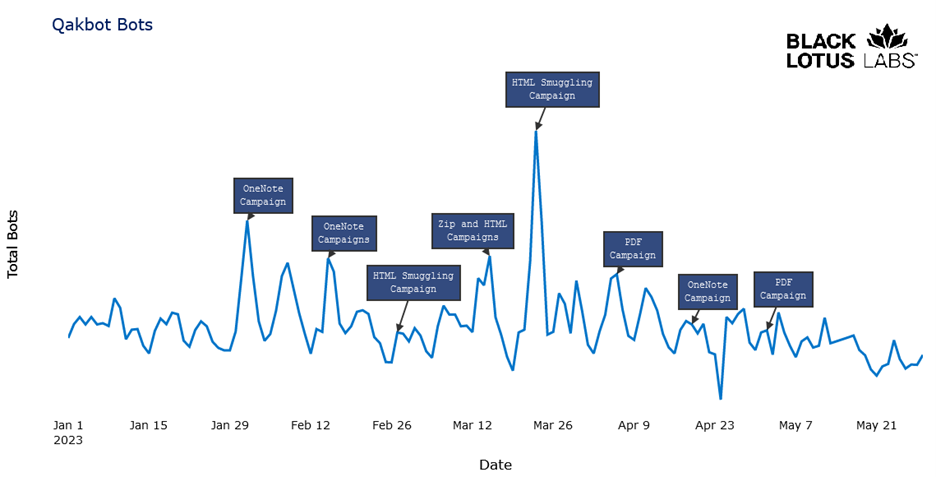
Daily active Qakbot bots, January - May 2023, with infection techniques (image credit: Lumen Black Lotus Labs)
During 2022, Qakbot had been relying on MS Office-based macro exploitation for initial infection, but after Microsoft disabled macros by default for Office users, they quickly switched between a variety of techniques: malicious OneNote files, HTML smuggling techniques, Mark of the Web evasion and malicious PDF's.
The Qakbot C2 infrastructure also evolved into a two-tier structure, with the first tier largely existing in residential dynamically-allocated consumer IP address space. These machines are frequently rebooted and their anti-malware tools frequently automatically updated, making it hard for the threat actor to persist in them, but Qakbot keeps its numbers up by retooling the machines it infects as C2's. Telemetry shows that a Qakbot victim machine is rapidly pillaged for data - after one week, it has sent 90% of all the data it will ever send to a C2, after which the operators will then use the victim for other purposes, including becoming a C2 or a proxy in their own infrastructure. The rapid turnover and changing IP addresses also enables Qakbot to elude tools which work on IP addresses as IOC's.
The second tier of C2 infrastructure is hosted on VPS machines, typically in data centers beyond the reach of all but Russian law enforcement.
Formosa, Chris, Steve Rudd and Ryan English, Qakbot: retool, reinfect, recycle, blog post, 1 June 2023. Available online at https://blog.lumen.com/qakbot-retool-reinfect-recycle/.
Google Triples Chrome Exploit Bug Bounty
Google has announced a higher maximum bug bounty in their Chrome Vulnerability Rewards Program. Until 1 December 2023, the first vulnerability report providing a functional full chain exploit resulting in a Chrome sandbox escape will be eligible for triple the full reward amount - that is, a reward of up to $US180,000 (and possibly more, with other bonuses).
Subsequent full chain reports submitted during this period will be eligible for double the full reward amount.
Bug reports may be submitted in advance while development of the functional exploit continues, but the functional exploit must be submitted by 1 December; only the first functional full chain exploit received is eligible for the triple reward amount. The exploit must result in Chrome browser sandbox escape, with a demonstration of attacker remote control or remote code execution outside the sandbox, with no or very little reliance on user interaction.
Ressler, Amy, Announcing the Chrome Browser Full Chain Exploit Bonus, blog post, 1 June 2023. Available online at https://security.googleblog.com/2023/06/announcing-chrome-browser-full-chain.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.