Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Chinese APT Implants Ancient Trojan Via HTML Smuggling
Check Point Research brings us a report of a Chinese threat actor which is targeting foreign affairs ministries and embassies in a number of European countries - primarily the UK, Czech Republic, Hungary, Slovakia and Ukraine - with the likely goal of cyber-espionage, as indicated by the lure documents in the compaign emails, such as a letter originating from the Serbian embassy in Budapest, and an invitation to a diplomatic conference issued by Hungary's Ministry of Foresign Affairs.
The campaign - which Check Point have christened 'SmugX' - overlaps with previously-reported activity by the Chinese APT's RedDelta and Mustang Panda, and has been running since at least December 2022. It makes use of HTML smuggling - a technique in which the attackers hide a malicious payload inside HTML documents, enabling it to bypass network controls. Opening one of these documents starts a first stage loader consisting of the following chain of events:
- The embedded payload within some JavaScript code is decoded and saved to a blob with the appropriate filetype (e.g. application/zip)
- Instead of utilizing the HTML <a> element, the JavaScript code dynamically creates it
- A URL object is created from the blob using the createObjectURL function
- The download attribute is set with the desired filename
- Finally, the code invokes the click action, simulating a user clicking on the link, to initiate the file download
- For older browsers, the code employs msSaveOrOpenBlob to save the blob under the desired filename
This then chains to a second stage loader, of which there are two variants. The first uses a ZIP file that contains a malicious LNK file which will run PowerShell code to extract a compressed archive and save it to the %temp% directory. This archive contains three files:
- A legitimate executable - either robotaskbaricon.exe or passwordgenerator.exe - taken from a vulnerable version of the Roboform password manager
- A malicious sideloaded DLL called RoboForm.dll
- The malware payload, in a file called data.dat
The PowerShell code then runs the executable. The DLL sideloading technique allows the malicious code to be run within the context of this apparently legitimate process.
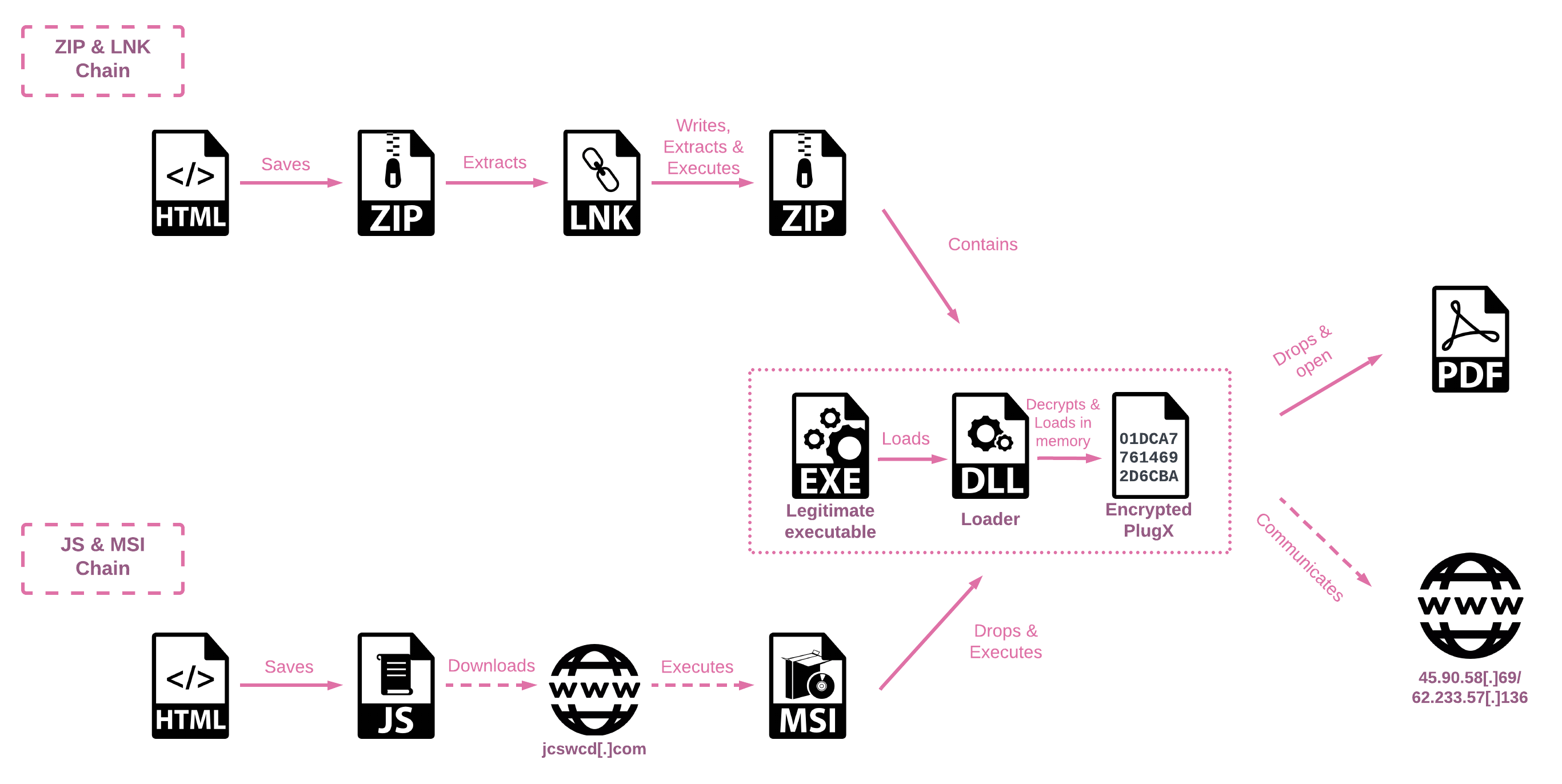
The two infection chains (image credit: Check Point Research)
The second variant of the second-stage loader uses JavaScript, rather than PowerShell, to download a MSI file, but installs the same three files.
The final payload is the PlugX remote access trojan, which has been used by multiple Chinese threat actors since 2008; its long life may be attributed to its modular structure which accommodates a variety of plugins which extend its functionality to include file theft, screen captures, keystoke logging and remote command execution. One notable change in this version is the switch to using RC4 encryption rather than the simple XOR technique used in previous samples.
The use of a variety of HTML smuggling infection chains, coupled with DLL sideloading, seems to have allowed this and perhaps similar campaigns to evade detection.
Check Point Research, Chinese Threat Actors Targeting Europe in SmugX Campaign, report, 3 July 2023. Available online at https://research.checkpoint.com/2023/chinese-threat-actors-targeting-europe-in-smugx-campaign/.
ISC2 Bylaws Voting Resumes
As we reported last week, the International Information Systems Security Certification Consortium - (ISC)2 - ran into difficulties with some of its online systems, specifically the page for making Annual Maintenance Fee payments, but more importantly the page for voting on proposed bylaw amendments.
While I continue to do battle with (ISC)2 over the AMF payment snafu, at least the bylaw voting process has resumed. Members can find a link to the voting page at the top of their dashboard after logging in - https://my.isc2.org/s/dashboard. Before voting, I recommend reading Stephen Mencik's blog posts, at https://smencik1.wordpress.com/2023/06/06/upcoming-by-laws-vote-info-and-recommendation/ and https://smencik1.wordpress.com/2023/06/26/by-laws-voting/.
CISA Vulnerability Summary
The US Cybersecurity and Infrastructure Security Agency has released its vulnerability summary for the week of 26 June. The list is long, but helpfully broken into sections by CVSS severity levels:
- High: vulnerabilities with a CVSS base score of 7.0 - 10.0
- Medium: vulnerabilities with a CVSS base score of 4.0 - 6.9
- Low: vulnerabilities with a CVSS base score of 0.0 - 3.9
So far, I have only skimmed quickly - I will search for anything directly relevant to my needs later - but I'm seeing a lot of WordPress plugins as well as Apple and Android OS's getting mentions. It seems all the usual categories of vulnerabilities keep turning up: use-after-free, directory traversals, Time-of-Check/Time-of-Use, out-of-bounds reads. Sigh - maybe it's time for we humans, creatures of bounded rationality as we are, to give up writing software, we are so bad at it.
CISA, Vulnerability Summary for the Week of June 26, 2023, bulletin, 3 July 2023. Available online at https://www.cisa.gov/news-events/bulletins/sb23-184.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.