Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Charming Kitten's Long Infection Chain Reaches Macs
The Iranian APT variously known as Charming Kitten, APT42, TA453, Mint Sandstorm and Yellow Garuda has been running a campaign targeting experts in nuclear security and Middle Eastern affairs, according to researchers at Proofpoint. The group, which is affiliated with Iran's Islamic Revolutionary Guard Corps, is using a spear-phishing campaign to deliver highly customised lure emails, the first of which is innocuous but quickly followed by an email containing a malicious link to a Google Script macro which, in turn, launches a long infection chain.
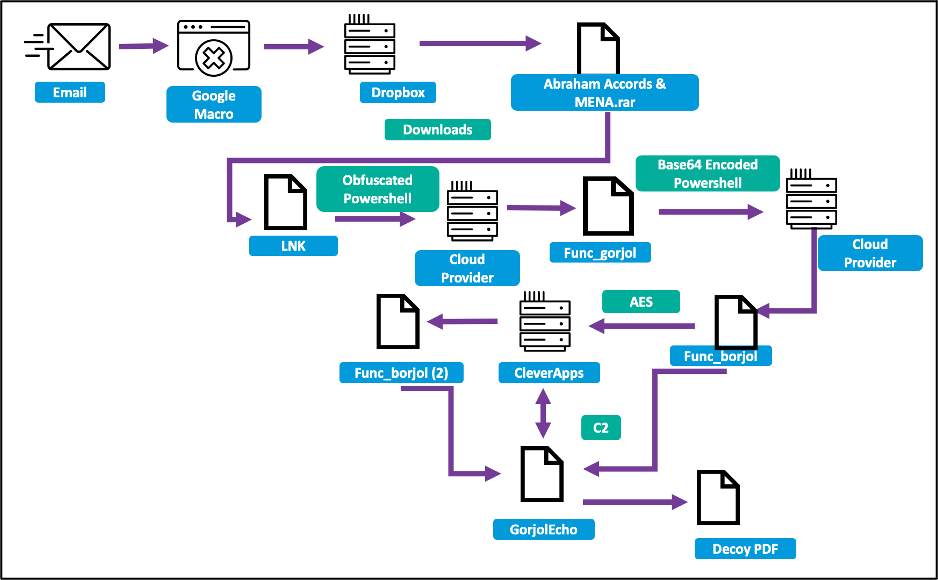
The long infection chain uses PowerShell scripts to download its various stages (image credit: Proofpoint)
A password-protected RAR file contains a dropper in the form of a .lnk file which in turn uses PowerShell to download additional stages from a cloud hosting provider - at first using base64 encoding but then switching to AES encryption, culiminating in the assembly of the final PowerShell backdoor, which the researchers dubbed GorjolEcho.
This achieves persistence by putting a copy of the initial loader stages in a StartUp entry, and then displays a decoy PDF that matches the recipient's expectations. It then commences the exfiltration of encrypted data over HTTPS to its C2 server, which is hosted in a legitimate cloud service - interestingly, HTTP error responses will cause generation of an error message in Korean, presumably as an attempted diversion. The GorjolEcho backdoor can also download and run additional modules, likely for cyber-espionage purposes.
However, the use of a .lnk file and PowerShell means this attack won't work on Mac computers, which are common in academic circles. Realizing that a targeted individual had not fallen foul of the attack, the threat actor followed up a week later with a new Mac-specific infection chain. This time, to induce the target to run an executable, their email claimed to include a VPN client; use of this would be necessary for security reasons. In fact, this was a script which used the curl command to download another shell script, dubbed NokNok, a backdoor which loops indefinitely, sending an HTTP POST to its C2 server and either executing other bash shell modules in response to the commands it receives or exiting.
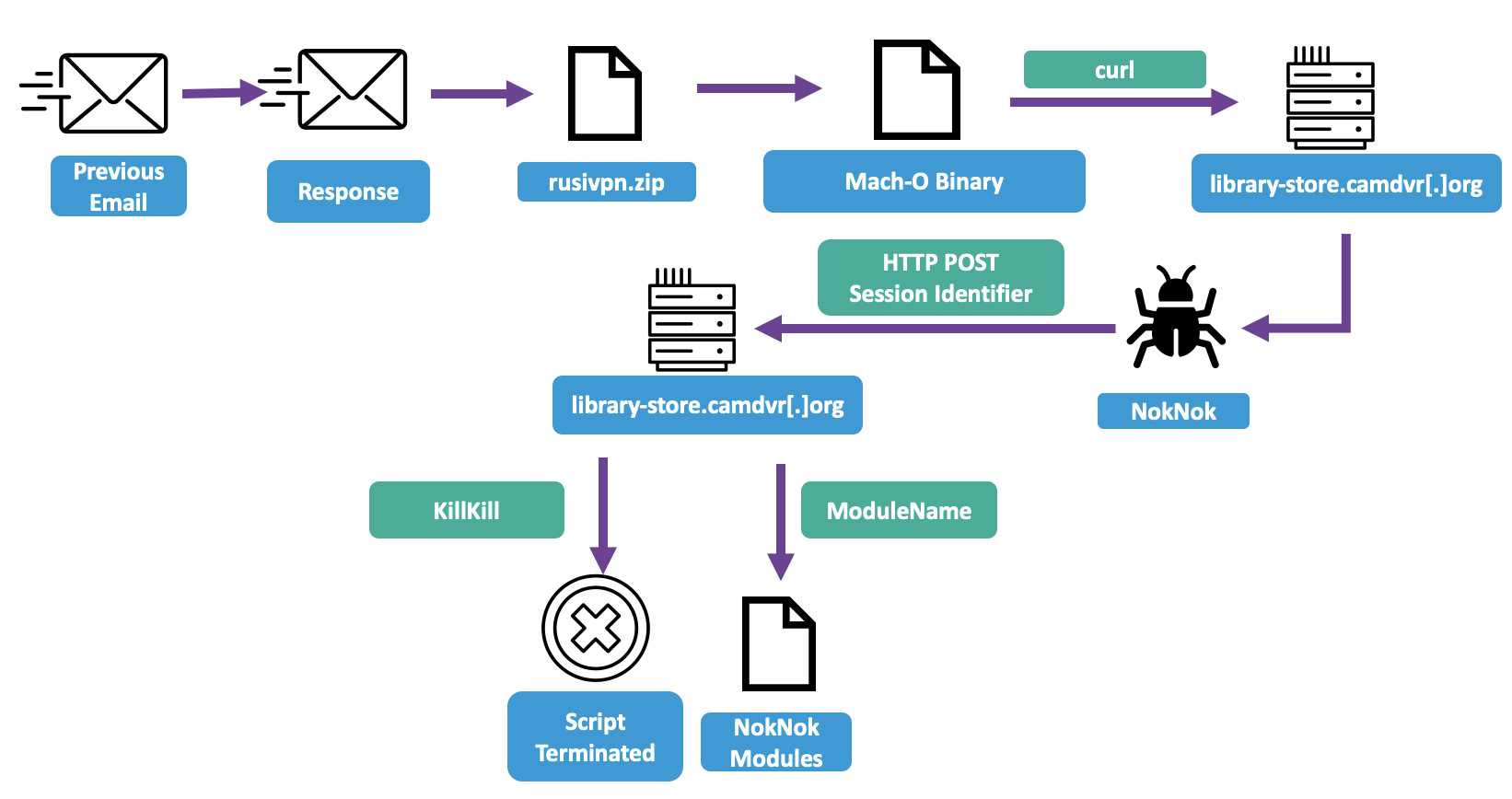
The NokNok backdoor delivery process (Image credit: Proofpoint)
The NokNok modules share common routines for encryption and base64 chunking in order to exfiltrate their results, which they generally obtain by using system commands - such as ps -ax to list running processes. There are probably additional modules for both GorjolEcho and NokNok.
While these infection chains represent a change from previous intrusions by Charming Kitten, there are sufficient similarities in both the coding techniques and overall TTP's employed for Proofpoint to attribute this campaign to the threat actor with high confidence. The efforts put in to develop new techniques, particularly using multiple legitimate cloud services as well as posting malware to new platforms, indicates a high degree of persistence.
Miller, Joshua, Pim Trouerbach, et. al., Welcome to New York: Exploring TA453's Foray into LNKs and Mac Malware, blog post, 6 July 2023. Available online at https://www.proofpoint.com/us/blog/threat-insight/welcome-new-york-exploring-ta453s-foray-lnks-and-mac-malware.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.