Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
HiatusRAT Targets Defense Contractors
Since March of this year, researchers at Lumen Black Lotus Labs have been tracking a complex campaign targeting edge routers for traffic collection, which they have dubbed "HiatusRAT". In June, HiatusRAT shifted its attention from Latin America and Europe, to focus on US a military procurement system as well as Taiwanese-based organizations, suggesting that the threat actor is serving Chinese strategic interests.
Since June, multiple new versions of the HiatusRAT malware have emerged, targeting a range of platform architectures, although curiously - and somewhat audaciously - these continue to use the same C2 servers. However, the new variants have been hosted on new VPS servers, with over 90% of connections to their addresses being made from a range of Taiwanese organizations, including semiconductor and chemical manufacturers and at least one municipal government.
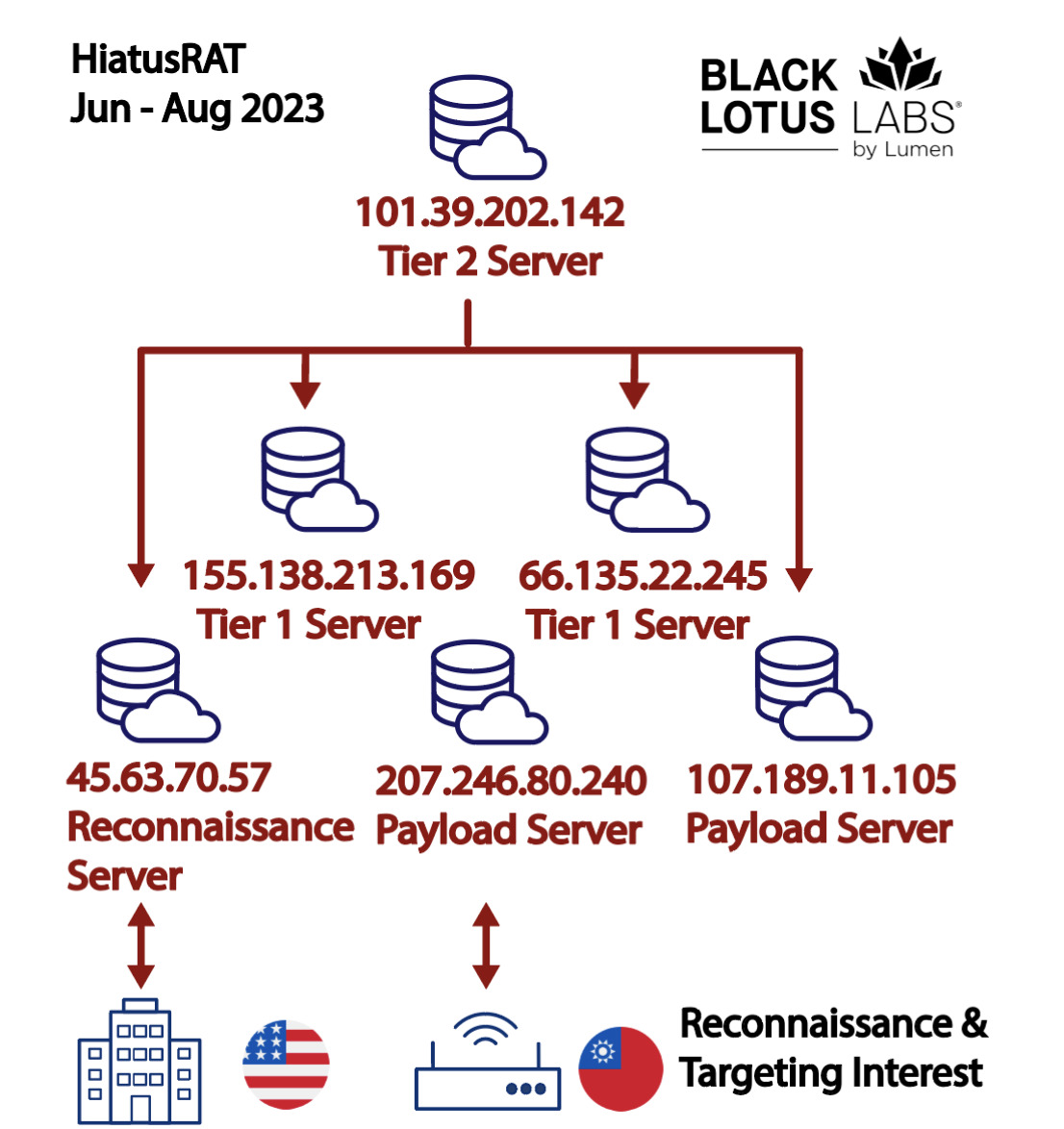
The logical connections in the new HiatusRAT network (image credit: Lumen Black Lotus Labs)
Following traffic from the distribution VPS's to upstream infrastructure, the Black Lotus Labs researchers were able to identify several new nodes in both China and the US, two of which connectd to a US Department of Defense server used for submission and retrieval of proposals for defence contracts, the traffic suggesting the threat actor was searching for publicly available information relating to defence contracts, possibly to identify defence contractors for subsequent targeting.
Black Lotus Labs, No rest for the wicked: HiatusRAT takes little time off in a return to action, blog post, 17 August 2023. Available online at https://blog.lumen.com/hiatusrat-takes-little-time-off-in-a-return-to-action/.
CISA Releases Vulnerability Summary for Week of August 14, Adds One Known Exploited Vulnerability
The US Cybersecurity & Infrastructure Security Agency has released its weekly vulnerability summary for the week of 14 August. A quick scan of just the most serious vulnerabilities - those with a CVSS 3.x score of 9.0 or above - reveals a variety of remote code execution, SQL injection, privilege escalation, missing function level access control and other vulnerabilities across a range of products including WordPress plugins, Veritas NetBackup Snapshot Manager, GitPython and various Huawei products.
CISA has also added one vulnerability to its Known Exploited Vulnerabilities Catalog - CVE-2023-26359, an Adobe ColdFusion deserialization of untrusted data vulnerability that can allow remote code execution.
CISA, Vulnerability Summary for the Week of August 14, 2023, security bulletin, 21 August 2023. Available online at https://www.cisa.gov/news-events/bulletins/sb23-233.
CISA, CISA Adds One Known Exploited Vulnerability to Catalog, cybersecurity advisory, 21 August 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/08/21/cisa-adds-one-known-exploited-vulnerability-catalog.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.