Les Bell
Blog entry by Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
New Backdoor Targets Middle East Journalists, Dissidents
A new backdoor, which targets journalists, dissidents and political activists in the Middle East with the objective of cyber-espionage, has been discovered by ESET researchers. The backdoor, dubbed Deadglyph, is attributed to the Stealth Falcon APT, also known as FruityArmor, which is associated with the United Arab Emirates, and was originally discovered by Citizen Lab, who saw it conducting spyware attacks. It was also seen in 2019, when ESET analyzed an unusual backdoor it was then using.
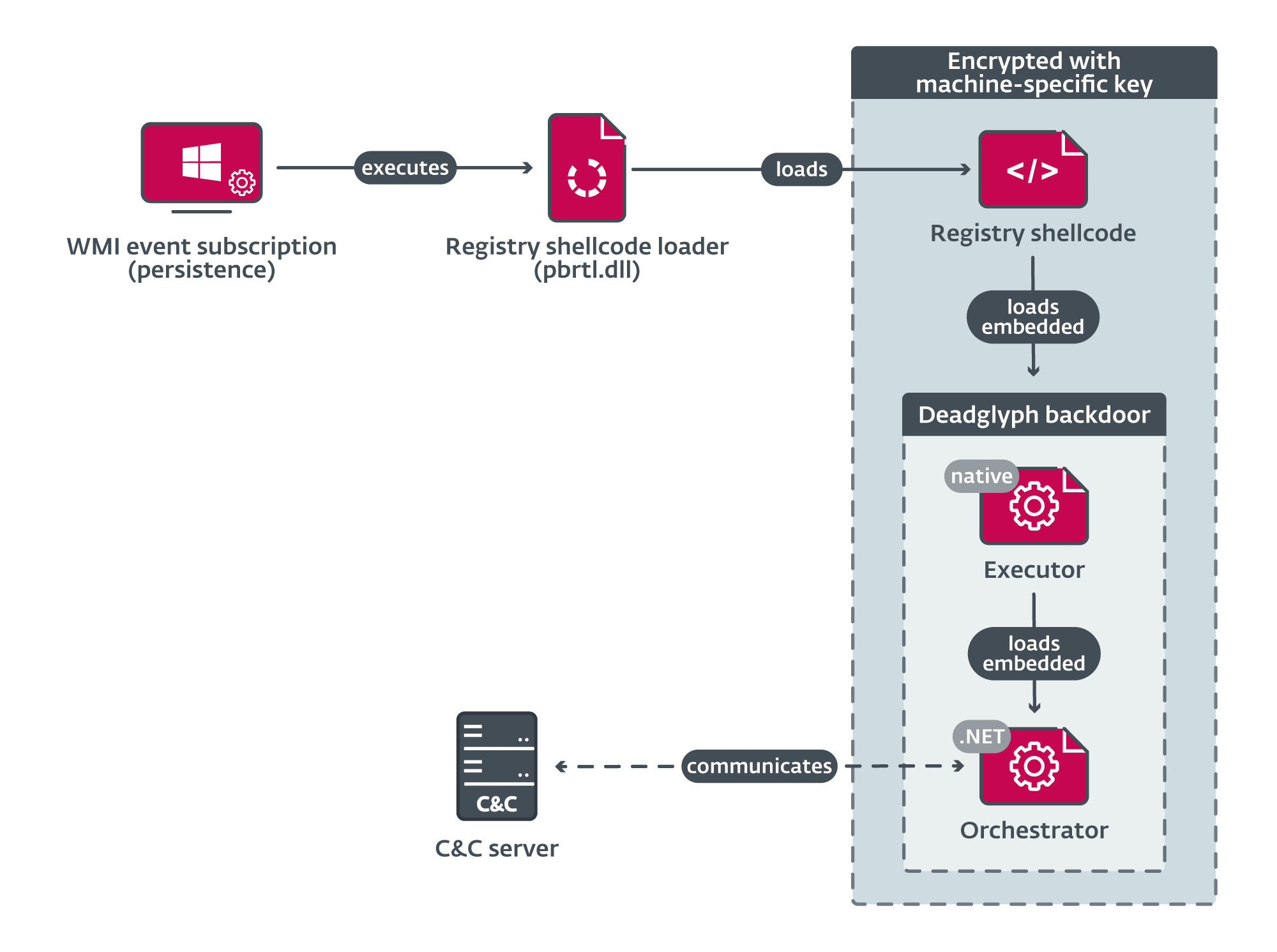
The Deadglyph loading chain components (Image: ESET)
The initial loader of the Deadglyph backdoor is the only component that resides as a disk file in the victim machine. It is a small DLL, with only one exported function which operates as a registry shellcode loader. It first RC4-decrypts the path to the encrypted shellcode in the registry, then derives a unique RC4 key from the system UUID, using it to decrypt the shellcode it retrieves from the registry and then executes it. Deriving the key from the system UUID prevents successful decryption and execution on a different computer.
Interestingly, the VERSIONINFO resource of this and other components mimics the name 'Microsoft Corporation', using both Greek and Cyrillic Unicode characters - a form of homoglyph attack. It is this feature, along with the presence of hexadecimal ID's like 0xDEADB001 and 0xDEADB101 in its configuration. that gave the backdoor its name.
The registry shellcode contains an minimally-encrypted payload and the corresponding decryption code. Once decrypted, the body consists of a PE (Portable Executable) loader and a PE file; the latter is the native part of the backdoor, termed the Executor. This loads and decrypts its AES-encrypted configuration (keys and other settings, which are subsequently stored in the registry), then initializes the .NET runtime and loads the embedded .NET part of the backdoor, termed the Orchestrator, which is in the .rsrc section of the Executor. Once the Orchestrator is running, the Executor provides a library of native code functions which it will use.
The Orchestrator is the main component of Deadglyph; it first loads its configuration, then establishes a connection to a command and control server, using a number of threads to perform various tasks, including checking the environment for likely security-related processes - if any of these is detected, the backdoor will either pause C2 communications while the suspicious process is present, or terminate and uninstall itself. The other threads are used for periodic communication with the C2 server and to execute the received commands.
Two modules are used for C2 communications - a Network module and a Timer module. Again, the architecture is cautious to evade analysis: if it cannot establish a connection to the C2 server for a preset interval, then the backdoor terminates and uninstalls itself. The Network module communicates with the C2 server using a custom binary protocol with encrypted content is used underneath TLS/SSL, and has the ability to discover proxy configuration in the event it is on a network protected by a proxy web server.
The commands from the C2 server take the form of three types of tasks: Orchestrator tasks, which are used for configuring the backdoor; Executor tasks, which execute additional modules; and Upload tasks, which send the output of commands and errors to the C2 server. Interestingly, the backdoor does not implement the code for most of its commands - the traditional design. Rather, each command is delivered in the form of an additional module in PE format or as shellcode. This means that Deadglyph is almost infinitely extensible, and also that its capabilities cannot be fully analyzed unless and until all command/modules are captured.
However, the ESET researchers were able to capture three modules: a process creator, which provides remote command execution; an information collector, which profiles the system via Windows Management Instrumentation API queries; and a file reader, which can read a file and return it to the Orchestrator for subsequent uploading - this module was observed retrieving a victim's MS Outlook data file.
The exact exploitation mechanism by which Deadglyph infects a target system is not known; however, while investigating it, the ESET researchers discovered a .CPL (Control Panel extension) file which had been uploaded to VirusTotal from Qatar, and which appeared to be related to Deadglyph.
The ESET report provides IOC's, along with a mapping to MITRE ATT&CK techniques.
ESET Research, Stealth Falcon preying over Middle Eastern skies with Deadglyph, blog post, 22 September 2023. Available online at https://www.welivesecurity.com/en/eset-research/stealth-falcon-preying-middle-eastern-skies-deadglyph/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.