Les Bell
Blog entry by Les Bell
This blog post is intended to complement a short YouTube video on the same topic, which can be found at https://www.youtube.com/watch?v=6u8thFkTfv8. The video, and this blog, are based on just one slide, taken from the first afternoon of our flagship CISSP Fast Track course. Many of the links that follow access pages in the CISSP Course CBK Wiki - a 700-page resource - and are only available to those who are enrolled in the course.
The following description of security management tasks is somewhat idealized and will need to be tailored to the specific organisation. It primarily shows information flows rather than time - although if performing all these steps for the first time, for example as part of a greenfields project, then obviously some steps must be completed, or at least started, to provide the information required by the subsequent steps.
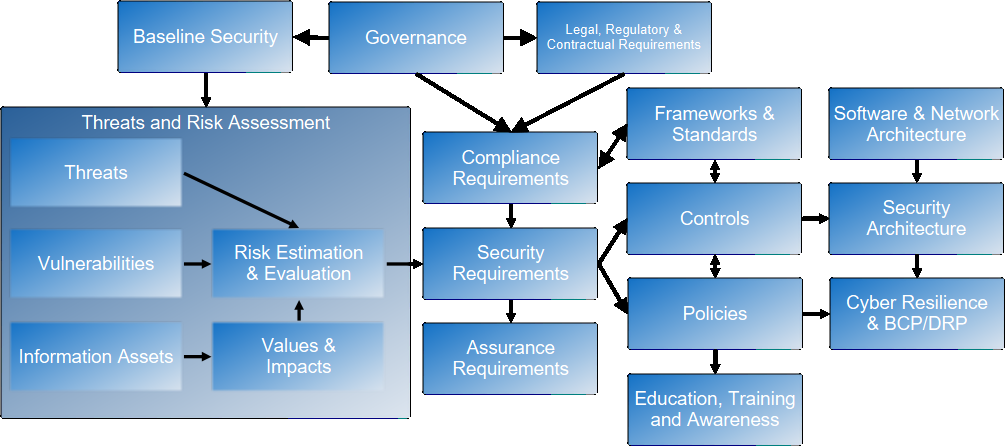
In general, the flow of information in the diagram above is top-left to lower-right, as indicated by the arrows. The top row starts with the governance process and gathering of complicance requirements; this is typically followed by deployment of baseline security controls before commencement of a formal threats and risk assessment.
Governance
Governance encompasses the activities the activities of the Board and senior management to ensure that cybersecurity risks are managed appropriately:
- The appointment of a CISO
- Education and awareness activities for the Board and senior management:
- The nature of information risk, roles and accountability
- Key cybersecurity threats and issues
- Drafting of initial security requirements
- Monitoring and reporting expectations
- Initial drafting of an Enterprise Security Policy which addresses key security governance issues
Compliance Requirements
Your board and senior management has been reading in the mainstram media about high-profile security breaches, and in the business press about the need to manage cybersecurity risk - so they will have their own requirements, which is why they have appointed a Chief Information Security Officer and authorised him to build and operate this Enterprise Security Program.
However, other entities may require you to comply with their own requirements - the law, regulations (particularly for industries like healthcare, where privacy is particularly important, finance, and critical infrastructure) and other stakeholders such as prospective customers. Government agencies, in particular, often require suppliers and subcontractors to be audited and certified compliant with with standards such as ISO 27001. Your sales team will definitely let you know if this is the case - and don't miss the opportunity to sell your cybersecurity activities as conferring a competitive advantage!
See Compliance, Legal and Regulatory Requirements.
Baseline Security
The highest priority is then to take initial, obvious steps to improve the security posture of the organization. These would, almost without exception, be discovered early in the Threats and Risk Assessment process in any case. See Baseline Security.
Threats and Risk Assessment
The topic of risk management is treated extensively in the course, where we discuss a variety of risk assessment methodologies such as ISO 27005, the NIST Risk Management Framework and Factor Analysis of Information Risk. The key steps of the process are:
- Identification of threats
- Identification of vulnerabilities
- Identification and valuation of information assets
- Risk estimation
- Risk evaluation
The output of the risk assessment process is generally a prioritized list of risks along with recommendations for their treatment. Especially when resources are constrained - e.g. additional cybersecurity staff must be hired to meet a shortfall - it is wise to allocate resources to the biggest risks first.
Security Requirements
A security requirement is essentially a high-level statement of what must be done to mitigate a risk or comply with externally-imposed requirements. The focus should be on what is to be achieved, and not how it is to be achieved - the how is achieved by controls, including policies. Abstracting the requirements in this way allows selection of new controls without having to trace back through the entire risk assessment process.
Identification of Related Frameworks and Standards
The security requirements identified thus far are those which address risks posed by identified threats to the enterprise. However, steps should be taken early to identify suitable frameworks and standards which may become the basis of a compliance program intended to address the risks the enterprise poses to others. See Security Frameworks, Standards and Maturity Models
Assurance Requirements
Your senior management and board will require regular reports on your progress through this process, as well as the current level of risk. Most importantly, they will want to know you're not just 'winging it', but actually working in accordance with widely-accepted standards of good practice (which is one way in which the CISSP is helpful). However, external stakeholders may also require you to complete self-assessment surveys, or pass audit by a third-party auditor, usually against one of the standards mentioned earlier. See Security Audit.
Selection of Controls
Of course, the bulk of the course is devoted to controls - technical controls, architectural controls, procedures, policies, etc. On the first afternoon, we briefly touch on some management aspects, but over the following days we dig into the technicalities in some depth. See Controls.
Development and Promulgation of Security Policies
Every organization has to have a library of security policies, starting at the top with the Enterprise Security Policy which is signed off by the board and gives the CISO authority to write and promulgate the others. Some are issue-specific, like the Acceptable Use Policy or the Social Media Policy; others provide specific information for the owners of information assets - the Information Classification Policy, for example. Some are technical, like the Policy on Use of Cryptographic Controls and meant for use by software developers, network architects and administrators.
Along with policies, there will also be standards (e.g. the Standard Desktop Environment), procedures (e.g. for provisioning new user accounts) - although these are increasingly replaced by automation and orchestration - and guidelines, which provide advice but are generally not mandatory.
Employment contracts typically require all employees to comply with the applicable policies. See Enterprise Security Policies, Standards, Procedures and Guidelines.
Security Education, Training and Awareness
But people don't read policies - so in order to change and improve the organization's security culture they have to be backed up with appropriate education (e.g. in secure coding techniques, for developers), training (on topics such as phishing, malware and scams) and reinforced with ongoing awareness programs. See Security Education, Training and Awareness.
Software and Network Architectures
In broad terms, the major components of the enterprise architecture are the application software architecture and the network architecture. These are designed by software architects, network architects and, at a higher level, enterprise architects to meet business objectives and requirements. We do a deep dive on architecture, especially security architecture, on the second day of the course.
Security Architecture
The selected controls must be implemented either in the specific application software architecture - e.g. selection and includion of an access control model - or in the network architecture - e.g. various types of firewalls, etc. Some controls - e.g. authentication services - are provided as enterprise-wide services or in infrastructure - e.g. endpoint security.
See Enterprise Security Architecture.
Planning for Cyber Resilience, Business Continuity and Disaster Recovery
You can deploy all kinds of controls in an attempt to mitigate (i.e. reduce) risk, but you can never eliminate it entirely. Sooner or later you'll encounter an adversary who is either lucky or good, and who is able to penetrate one or more layers of your defences. This is where a planned approach to resilience pays off; although traditionally BCP and DRP are IT processes managed by the CIO, some of them can be adapted to keep the business functioning even in the face of targeted attacks.
In fact, the information captured during the Business Impact Analysis phase of business continuity planning is exceptionally useful during incident response, especially when systems must be taken offline during the containment and eradication phases of the incdent response cycle.
See Cyber Resilience and Business Continuity Planning and Disaster Recovery Planning.
What Else?
Readers who are familiar with the NIST Cybersecurity Framework will realise that what has been described so far covers only two or three of the core functions of that framework: Identify, Protect, and Govern (which was introduced in V 2.0 of the CSF).
A lot of what follows over the remainder of the five-day CISSP Fast Track course delves into the technical details of these, uncovering sources of vulnerabilities, techniques for protection via different types of controls, and laying the groundwork for the final functions which are covered in the Security Operations domain: Detect, Respond and Recover.
This has been a very abbreviated overview of a large topic; even at a management overview level, it takes us an entire afternoon to cover these topics. Still, I hope readers find this useful.
Upcoming Courses
There is still just time to register for one of the two remaining CISSP courses this year:
Sydney
Online Virtual
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.