Les Bell and Associates Pty Ltd
Site blog
This blog post is intended to complement a short YouTube video on the same topic, which can be found at https://www.youtube.com/watch?v=6u8thFkTfv8. The video, and this blog, are based on just one slide, taken from the first afternoon of our flagship CISSP Fast Track course. Many of the links that follow access pages in the CISSP Course CBK Wiki - a 700-page resource - and are only available to those who are enrolled in the course.
The following description of security management tasks is somewhat idealized and will need to be tailored to the specific organisation. It primarily shows information flows rather than time - although if performing all these steps for the first time, for example as part of a greenfields project, then obviously some steps must be completed, or at least started, to provide the information required by the subsequent steps.
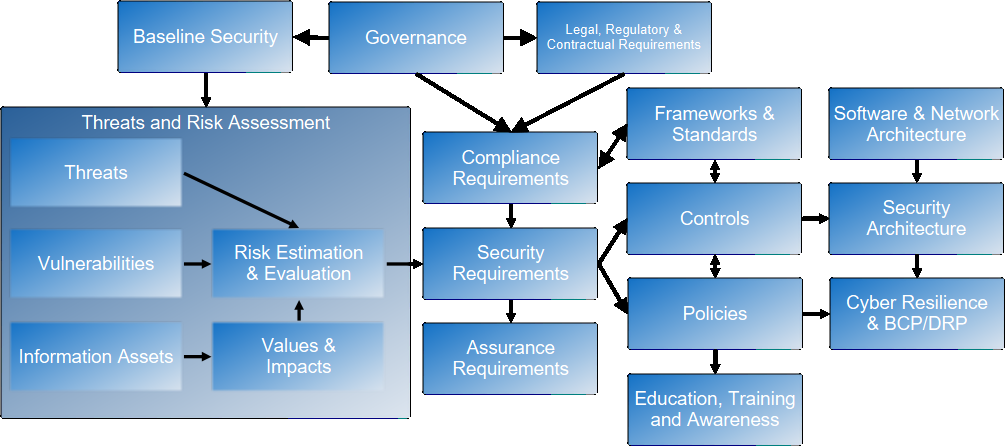
In general, the flow of information in the diagram above is top-left to lower-right, as indicated by the arrows. The top row starts with the governance process and gathering of complicance requirements; this is typically followed by deployment of baseline security controls before commencement of a formal threats and risk assessment.
Governance
Governance encompasses the activities the activities of the Board and senior management to ensure that cybersecurity risks are managed appropriately:
- The appointment of a CISO
- Education and awareness activities for the Board and senior management:
- The nature of information risk, roles and accountability
- Key cybersecurity threats and issues
- Drafting of initial security requirements
- Monitoring and reporting expectations
- Initial drafting of an Enterprise Security Policy which addresses key security governance issues
Compliance Requirements
Your board and senior management has been reading in the mainstram media about high-profile security breaches, and in the business press about the need to manage cybersecurity risk - so they will have their own requirements, which is why they have appointed a Chief Information Security Officer and authorised him to build and operate this Enterprise Security Program.
However, other entities may require you to comply with their own requirements - the law, regulations (particularly for industries like healthcare, where privacy is particularly important, finance, and critical infrastructure) and other stakeholders such as prospective customers. Government agencies, in particular, often require suppliers and subcontractors to be audited and certified compliant with with standards such as ISO 27001. Your sales team will definitely let you know if this is the case - and don't miss the opportunity to sell your cybersecurity activities as conferring a competitive advantage!
See Compliance, Legal and Regulatory Requirements.
Baseline Security
The highest priority is then to take initial, obvious steps to improve the security posture of the organization. These would, almost without exception, be discovered early in the Threats and Risk Assessment process in any case. See Baseline Security.
Threats and Risk Assessment
The topic of risk management is treated extensively in the course, where we discuss a variety of risk assessment methodologies such as ISO 27005, the NIST Risk Management Framework and Factor Analysis of Information Risk. The key steps of the process are:
- Identification of threats
- Identification of vulnerabilities
- Identification and valuation of information assets
- Risk estimation
- Risk evaluation
The output of the risk assessment process is generally a prioritized list of risks along with recommendations for their treatment. Especially when resources are constrained - e.g. additional cybersecurity staff must be hired to meet a shortfall - it is wise to allocate resources to the biggest risks first.
Security Requirements
A security requirement is essentially a high-level statement of what must be done to mitigate a risk or comply with externally-imposed requirements. The focus should be on what is to be achieved, and not how it is to be achieved - the how is achieved by controls, including policies. Abstracting the requirements in this way allows selection of new controls without having to trace back through the entire risk assessment process.
Identification of Related Frameworks and Standards
The security requirements identified thus far are those which address risks posed by identified threats to the enterprise. However, steps should be taken early to identify suitable frameworks and standards which may become the basis of a compliance program intended to address the risks the enterprise poses to others. See Security Frameworks, Standards and Maturity Models
Assurance Requirements
Your senior management and board will require regular reports on your progress through this process, as well as the current level of risk. Most importantly, they will want to know you're not just 'winging it', but actually working in accordance with widely-accepted standards of good practice (which is one way in which the CISSP is helpful). However, external stakeholders may also require you to complete self-assessment surveys, or pass audit by a third-party auditor, usually against one of the standards mentioned earlier. See Security Audit.
Selection of Controls
Of course, the bulk of the course is devoted to controls - technical controls, architectural controls, procedures, policies, etc. On the first afternoon, we briefly touch on some management aspects, but over the following days we dig into the technicalities in some depth. See Controls.
Development and Promulgation of Security Policies
Every organization has to have a library of security policies, starting at the top with the Enterprise Security Policy which is signed off by the board and gives the CISO authority to write and promulgate the others. Some are issue-specific, like the Acceptable Use Policy or the Social Media Policy; others provide specific information for the owners of information assets - the Information Classification Policy, for example. Some are technical, like the Policy on Use of Cryptographic Controls and meant for use by software developers, network architects and administrators.
Along with policies, there will also be standards (e.g. the Standard Desktop Environment), procedures (e.g. for provisioning new user accounts) - although these are increasingly replaced by automation and orchestration - and guidelines, which provide advice but are generally not mandatory.
Employment contracts typically require all employees to comply with the applicable policies. See Enterprise Security Policies, Standards, Procedures and Guidelines.
Security Education, Training and Awareness
But people don't read policies - so in order to change and improve the organization's security culture they have to be backed up with appropriate education (e.g. in secure coding techniques, for developers), training (on topics such as phishing, malware and scams) and reinforced with ongoing awareness programs. See Security Education, Training and Awareness.
Software and Network Architectures
In broad terms, the major components of the enterprise architecture are the application software architecture and the network architecture. These are designed by software architects, network architects and, at a higher level, enterprise architects to meet business objectives and requirements. We do a deep dive on architecture, especially security architecture, on the second day of the course.
Security Architecture
The selected controls must be implemented either in the specific application software architecture - e.g. selection and includion of an access control model - or in the network architecture - e.g. various types of firewalls, etc. Some controls - e.g. authentication services - are provided as enterprise-wide services or in infrastructure - e.g. endpoint security.
See Enterprise Security Architecture.
Planning for Cyber Resilience, Business Continuity and Disaster Recovery
You can deploy all kinds of controls in an attempt to mitigate (i.e. reduce) risk, but you can never eliminate it entirely. Sooner or later you'll encounter an adversary who is either lucky or good, and who is able to penetrate one or more layers of your defences. This is where a planned approach to resilience pays off; although traditionally BCP and DRP are IT processes managed by the CIO, some of them can be adapted to keep the business functioning even in the face of targeted attacks.
In fact, the information captured during the Business Impact Analysis phase of business continuity planning is exceptionally useful during incident response, especially when systems must be taken offline during the containment and eradication phases of the incdent response cycle.
See Cyber Resilience and Business Continuity Planning and Disaster Recovery Planning.
What Else?
Readers who are familiar with the NIST Cybersecurity Framework will realise that what has been described so far covers only two or three of the core functions of that framework: Identify, Protect, and Govern (which was introduced in V 2.0 of the CSF).
A lot of what follows over the remainder of the five-day CISSP Fast Track course delves into the technical details of these, uncovering sources of vulnerabilities, techniques for protection via different types of controls, and laying the groundwork for the final functions which are covered in the Security Operations domain: Detect, Respond and Recover.
This has been a very abbreviated overview of a large topic; even at a management overview level, it takes us an entire afternoon to cover these topics. Still, I hope readers find this useful.
Upcoming Courses
There is still just time to register for one of the two remaining CISSP courses this year:
Sydney
Online Virtual
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Only a very short post today, to point to an incredible story.
The Department of Technical and Further Education in Tasmania, decided to run a course in cybersecurity - after all, isn't there a critical "skills shortage" in the field worldwide?
(Short answer: no - but that's a topic for another day.)
They got $A3 million in funding from the federal and state governments, advertised their Certificate IV in Cyber [sic] Security, to run in Hobart and set about staffing and developing the course. They couldn't actually find people with broad experience in cybersecurity, so started with one recruit who had "managed responses to cyber incidents" but not actually been a security professional, and another who had been a "special education, arts, drama and class teacher" - but only started studying security about eight months before landing the job.
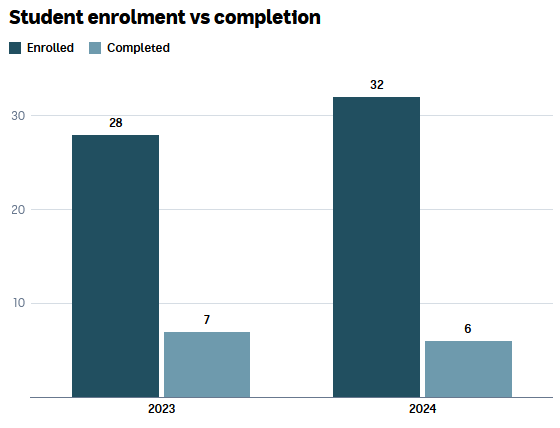
Unsurprisingly, students had started withdrawing only three months after the course had started. Even this year, about one-third of students have pulled out.
Anyway, you can read the whole sorry saga here: https://www.abc.net.au/news/2025-10-29/tastafe-cybersecurity-course-dropouts-staff-issues/105921416.
Sheesh. . . Why didn't they call me? ☹
Upcoming Courses
There is still just time to register for one of the two remaining CISSP courses this year:
Sydney
Online Virtual
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
A really interesting, and somewhat tongue-in-cheek, paper gives us a bit of welcome relief from the threat of the imminent collapse of (online) civilisation thanks to the complete breakdown of public-key cryptography.
The threat arises from the much-vaunted ability of quantum computers to break public-key crypto based on the widely-used RSA algorithm. RSA is used in many popular protocols and applications, such as Transport Layer Security, S/MIME and PGP email, and end-to-end encrypted messaging applications. It plays two important roles: a) the signing of messages in these protocols - including the signing of SSL/TLS certificates - and b) the solution of the key echange problem, by encapsulating a session key for exchange over untrusted networks (although in the latter case, especially for TLS, it has been supplanted by ECDHE, or Elliptic Curve Diffie-Hellman Key Agreement.
You see, the RSA algorithm is based upon the difficulty of factoring very large composite numbers - numbers which are the product of two large numbers which are probably prime (I say probably prime because proving the two randomly-selected large numbers actually are prime is itself a computationally challenging process, so we try a number of times to prove each number is not, and if it passes these tests, we accept it probably is). To give you an idea of the sizes involved, the RSA key for this web site uses a 4096-bit bit modulus - that's 1,234 decimal digits in length.
Hence the algorithm can be broken by an adversary who can factor very large numbers - something that is impractical using classical computers. However, in 1994 physicist Peter Shor developed an algorithm which can perform factorization of large composites in polynomial time using a combination of classical and quantum computation (Shor, 1997).
This has led to increasing concern that the cryptographic underpinnings of our 'secure enough' Internet could be completely broken, provided two problems are solved:
- Building a quantum computer with enough qubits (and not subject to noise, etc.), and
- Generalizing Shor's algorithm - the original algorithm requires the construction of a quantum circuit for each number to be factored.
Obviously, physicists, mathematicians and cryptanalysts all around the world have been beavering away on this problem over the years, some of them announcing their results in a series of 'record-breaking' factorizations of increasingly large composites. (I say 'some of them', because anyone who makes a really serious breakthrough, especially solving both those problems, is going to keep it very quiet indeed so that they can make best use of it).
I cover some of these results in our CISSP Fast Track Review course.
But now, a paper with the lovely title, Replication of Quantum Factorisation Records with an
8-bit Home Computer, an Abacus, and a Dog (Gutmann and Neuhaus, 2025) shows that a lot of the vaunted progress in quantum factorization is, in fact, smoke and mirrors. In many cases, the answers to the factorization are known in advance. In others, the two factors are carefully chosen to make factorization easy in what the authors more correctly describe as a physics experiment.
In one example, the factors of a 2048-bit RSA modulus are carefully selected to differ by only a few bits from the square root of that modulus - so that a simple integer square root calculation essentially performs the factorization. In practice, such a value would never be encountered in the real world - the RSA key generation algorithm generally requires that the two factors are much more different from each other.
Other cases rely on using prior knowledge of the factors to reduce the problem to a form that can be solved using the so-called 'compiled' form of Shor's algorithm which simply confirms that those are, in fact, the factors - something that can also be done by a simple multiplication. In other cases, preprocessing can be used to simplify the factorization or even transform it into a completely different problem which can then be solved using far fewer qubits. For example, a carefully-chosen 20,000 bit (6,021 decimal digit) number can be 'factorized' using only 2 qubits in the compiled form!
There are lots of sleight-of-hand tricks for creating these more-apparent-than-real quantum factorization records: Gutmann and Neuhaus describe the 'Smolin-Smith-Vargo algorithm' and the 'Callas Normal Form for Sleight-of-Hand Quantum Factorization', to give names to just two.
But in section 4 of their paper, they go on to perform quantum factorizations on a Commodore VIC-20 computer, one of the earliest hobby/home computers of the late 1970's, based on a 6502 processor with 1 MHz clock speed and less than only 4 KB of usable RAM. As they point out, since the 6502 is a transistor-based integrated circuit, and transistors work using quantum effects, it is just as much a "quantum computer" as the D-Wave machine (which operates by quantum annealing) used to factorize an RSA-2048 number in a widely-cited paper. In fact, the D-Wave paper feature ten different RSA-2048 moduli, and an emulated 6502 factorized them all - using an algorithm developed in 1945 for the EDVAC computer!
In section 5 of the paper, the authors performed several of the record-breaking factorizations using an abacus. In section 6, they replicated an earlier demonstration in which Gutmann trained a dog to 'perform factorizations' - the dog, Scribble, was trained to bark three times, and then re-trained to bark 5 times. One can only imagine what they might have achieved - perhaps even factorization of the RSA-2048 numbers - had Mr. Ed been available!
It's not all fun and games, however - section 7 turns serious by suggesting a numer of evaluation criteria for future claims of record-breaking quantum factorizations.
So, can we relax and abandon all efforts to move to post-quantum crypto or quantum-resistant cryptographic techniques? The prudent approach would suggest not. After alll, we know what we know - but we don't know what possible adversaries might know. As Bletchley Park demonstrated with the Ultra intelligence produced by their breaking of the Enigma cipher, you never want to leak your capabilities to an adversary, causing them to change their techniques (the Enigma cracking was not publicly disclosed until the 1970's). And a well-resourced adversary could also store and save intercepted communications traffic in preparation for an attack becoming feasible, then use it to retrospectively break that traffic.
So, don't panic - the sky is not falling. But plan for the eventual switch to quantum-resistant crypto, such as the standards (e.g. CRYSTALS-Dilithium) adopted by NIST. You never know . . .
References and Further Reading
Gutmann, Peter, and Stephan Neuhaus, Replication of Quantum Factorisation Records with an8-bit Home Computer, an Abacus, and a Dog, IACR pre-print, March - September 2025. Available online at https://eprint.iacr.org/2025/1237.
Shor, Peter W., Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer, SIAM Journal on Computing, 26 (5), 1 October 1997. Available online at http://epubs.siam.org/doi/abs/10.1137/S0097539795293172.
Upcoming Courses
There is still just time to register for one of the two remaining CISSP courses this year:
Sydney
Online Virtual
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
During the last day of our CISSP course, when we cover Security Operations, I make reference to a 2013 tweet by Mudge, one of the founders of L0pht Consulting, authors of the popular l0phtcrack dictionary attack program. In it, Mudge states that:
DoD data (cleared for release) shows on average 1/3 of vulns in government systems is in the security software.
And he provides a supporting graph:
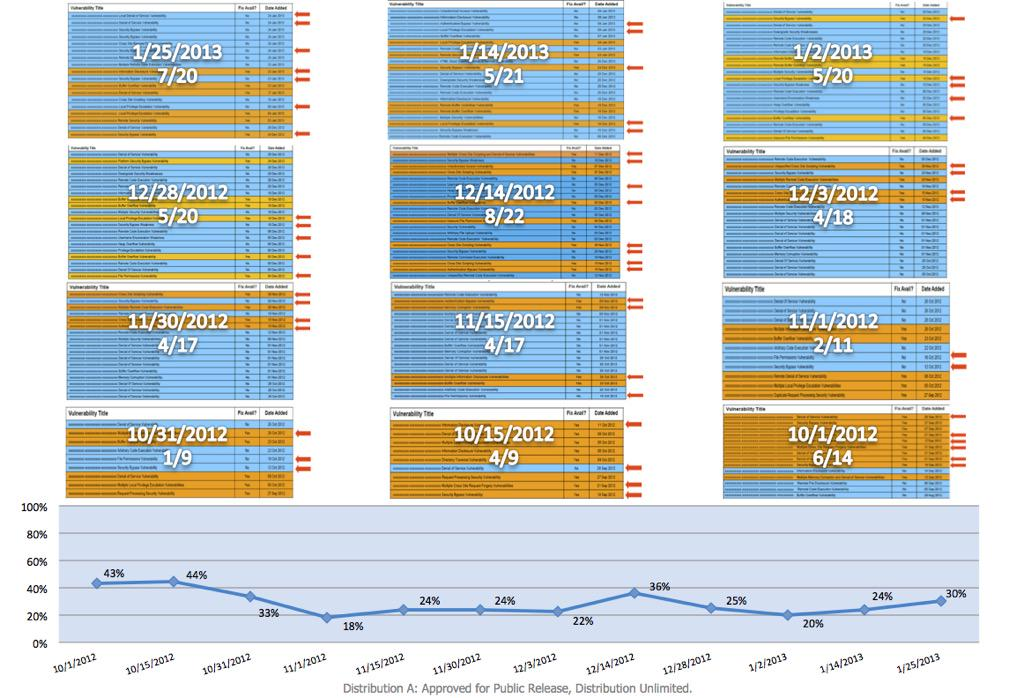
This reinforces a point introduced earlier in the Security Engineering domain of the course, when we discuss the design of evaluated products, particularly trusted systems: the way to achieve a secure design is to remove unnecessary functionality and eliminate unneeded code, simplifying the design and reducing the attack surface. Conversely, attempting to improve security by adding more and more software actually makes things worse.
This led me to coin one of many mantras which I drop into discussions about security.
The enemy of security is complexity.
This is, sadly, as true as ever. In fact, the situation has only got worse.
Back in February 2024, I blogged about the problem of developers relying more and more heavily on external dependencies. Many libraries and subsystems are sourced from repositories such as GitHub, making them vulnerable to a range of supply-chain attacks, such as the insertion of back-doored versions using near-identical names. And this is, of course, in addition to the possibility of vulnerabilities in the original code.
In the IEEE Spectrum article (Hubert, 2024) which had set me pondering this, the author cited the example of a relatively simple photo-sharing application which had 1,600 dependencies on external libraries. Now, consider how likely it is that none of those 1,600 dependencies has any vulnerabilities. I'd say your chances are close to zero.
The solution is to improve programmer education and reduce reliance on external dependencies. Hubert demonstrates this by developing a lean image-sharing program that consists of just 1,600 lines of source code plus five important dependencies - a much more secure approach.
Now, this is all well and good, but some software has to provide a wide range of functionality - and this applies particularly to security-related software. Hubert points to a vulnerability in the Barracuda Email Security Gateway - specifically in the way a third-party Perl module would unpack Excel spreadsheets to scan them for malware - allowing arbitrary code execution as it did so.
Since then, the problem has only been exacerbated by our success in improving security education, training and awareness among enterprise employees. This has paid off by reducing the effectiveness of phishing attacks, leading threat actors to rely more heavily on exploitation of software vulnerabilities in network management and security software, as these are reachable over the Internet and often assumed to be secure. If an attacker can compromise the perimeter defences, they can then pivot to move further into the victim's networks.
We saw the first indications of this five years ago - remember the huge impact of the attack on SolarWinds Orion network management software? Russian threat actors managed to compromise SolarWinds' software build system, and insert a backdoor into the software, leading to breaches at roughly 100 companies and government agencies, including the US Treasury Department and the National Telecommunications and Information Administration.
After the initial incident response, the company called a halt to new feature development and refocused 400 developers on improving software quality, including security. (The SolarWinds CISO, Tim Brown, who claims he lost 25 pounds (just over 11 kg) in 20 days during the incident response, doubtless wished they had done this before the breach.)
In their 2025 analysis of 0-day exploits (Charrier, 2025), Google Threat Intelligence Group reported that:
Zero-day vulnerabilities in security software and appliances were a high-value target in 2024. We identified 20 security and networking vulnerabilities, which was over 60% of all zero-day exploitation of enterprise technologies.
And so it continued, with subsequent attacks on Ivanti, Citrix NetScaler, Cisco, Juniper, Fortinet, Palo Alto Networks and SonicWall.
We need the companies who sell us network management and security products to get serious about security by design, educating their developers on secure coding techniques and reducing reliance on external dependencies. We also need to focus even more heavily on defense-in-depth approaches to network defence, making use of network segmentation and explicitly defined trust boundaries.
What's more, we need to apply the same principles in our own systems and software development. At the risk of using an old cliché: keep it simple, stupid. Write the code yourself when you can, rather than googling for an external library (or, worse, relying on AI suggestions or even vibe coding). Never forget: the enemy of security is complexity. Keep it out, wherever possible.
References and Further Reading
Charrier, Caset, et. al., Hello 0-Days, My Old Friend: A 2024 Zero-Day Exploitation Analysis, Google Threat Intelligence Group blog, 29 April 2025. Available online at https://cloud.google.com/blog/topics/threat-intelligence/2024-zero-day-trends.
Hubert, Bert, Why Bloat Is Still Software’s Biggest Vulnerability: A 2024 plea for lean software, IEEE Spectrum, 8 February 2024. Available online at https://spectrum.ieee.org/lean-software-development.
Mudge, DoD data (cleared for release) . . ., tweet, 2013. Available online at https://twitter.com/dotMudge/status/642758829697056768/photo/1.
Taylor, Josh, ‘I lost 25 pounds in 20 days’: what it’s like to be on the frontline of a global cyber-attack, The Guardian, 19 October 2025. Available online at https://www.theguardian.com/technology/2025/oct/19/global-cyber-attack-russian-hack-solarwinds-stress-health.
Upcoming Courses
There is still just time to register for one of the remaining CISSP courses this year:
Sydney
Online Virtual
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.

Upcoming Courses
Sydney
- SE221 CISSP Fast Track Review, 17 - 21 March 2025
- SE221 CISSP Fast Track Review, 21 - 25 July 2025
- SE221 CISSP Fast Track Review, 3 - 7 November 2025
Melbourne
- SE221 CISSP Fast Track Review, 28 April - 2 May 2025
- SE221 CISSP Fast Track Review, 25 - 29 August 2025
Online Virtual
- SE221 CISSP Fast Track Review, 20 - 24 January 2025
- SE221 CISSP Fast Track Review, 3 - 7 March 2025
- SE221 CISSP Fast Track Review, 12 - 16 May 2025
- SE221 CISSP Fast Track Review, 23 - 27 June 2025
- SE221 CISSP Fast Track Review, 18 - 22 August 2025
- SE221 CISSP Fast Track Review, 23 - 17 October 2025
- SE221 CISSP Fast Track Review, 24 - 28 November 2025
Online Virtual, One Day per Week for 5 Weeks
Online with Evening Classes Delivery
- SE221E CISSP Fast Track Review Evening Classes, 19 February - 7 May 2025
- SE221E CISSP Fast Track Review Evening Classes, 3 September - 19 November 2025
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Our flagship CISSP Fast Track Review course is now fully updated to meet the 15 April 2024 exam outline. The course includes new material on a number of topics - principally artificial intelligence, high performance computing and networking.
"The course did not need much updating at all", said course developer and presenter Les Bell. "The course is continually updated and has always been slightly ahead of the CISSP detailed content outline, on the assumption that the material will turn up in the Common Body of Knowledge sooner or later."
In particular the presentation slides used during the 5-day course are backed by a wiki which contains over 670 pages of detailed information as well as references and links to external sources. For example, the wiki already contained pages on machine learning and artificial intelligence, as well as separate pages on attack techniques such as prompt injection and training data extraction, making it easy to expand. Using a wiki has made it easy to cross-reference and reorganise topics which may appear in multiple domains of the CISSP CBK.
The course is taught in both 5-day face-to-face sessions and a virtual/online format, using a blended learning approach which includes an online component. This includes quizzes with feedback which links directly back into the wiki, so that students get immediate detailed feedback, speeding pre-exam revision. The course site also provides other resources such as discussion forums and post-class support.
Further information, including the course schedule, is at https://www.lesbell.com.au/mod/page/view.php?id=481 (the schedule of upcoming courses is, of course, below).
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
We've all received them - those not-very-clever text messages, 'apparently' from a toll road tag operator or similar, warning that the tag account has run out of funds and needs to be topped up. I say, 'apparently', because to most of us they're very apparently not genuine - but it seems enough people fall for them to make it profitable for the operators, as they damn things just kept coming.

A SIM box containing multiple SIM's and cellphone modems, used for smishing (Wikimedia Commons)
But we should see a sharp decline, following an operation by the NSW Police Cybercrime Squad, who set up a strike force to investigate a syndicate allegedly responsible for sending over 80 million fraudulent messages (given Australia's population of 25 million, that represents over-saturation) over 5 months.
Around 6 am on Thursday 15th Feb, the NSW Police's Public Order & Riot Squad assisted Strike Force Kanbi detectives in executing search warrants at two Sydney apartments. In one, police arrested two men, aged 37 and 43, and located three large SIM boxes along with "a number" of SIM cards. In another nearby apartment, they arrested a 35-year-old man and located a large amount of identity information, SIM cards, eight mobile phones and some cannabis.
The strike force detectives were assisted by local telcos, using their information to locate these SIM boxes and then plan their dawn raids.
At Burwood police station, the men were all charged with 'use equipment connected to network to commit serious offence' under section 474.14(1) of the Criminal Code Act 1995 (Cth) and 'deal with identity info to commit an indictable offence' under Section 192J of the Crimes Act 1900 (NSW), which carries a maximum penalty of 10 years imprisonment. The younger man faces an additional charge of possessing a prohibited drug.
The men were refused bail and appeared in the Burwood Local Court the following morning. They were formally refused bail and remanded to reappear in the same court on Friday 1 March. I dare say the police forensics unit will be taking a close look at any and all seized devices to gather further information about this group and their activities - which could lead to a prolonged trial.
NSW Police, Three men charged over alleged SMS phishing scam responsible for sending over 80 million fraudulent texts, news release, 26 February 2024. Available online at https://www.police.nsw.gov.au/news/news_article?sq_content_src=%2BdXJsPWh0dHBzJTNBJTJGJTJGZWJpenByZC5wb2xpY2UubnN3Lmdvdi5hdSUyRm1lZGlhJTJGMTEwNjMzLmh0bWwmYWxsPTE%3D.
Sydney Criminal Lawyers, Use Telecommunications Network with Intent to Commit Serious Offence, web page, 21 August 2023. Available online at https://www.sydneycriminallawyers.com.au/criminal/legislation/criminal-code-act/use-telecommunications-network-with-intent-to-commit-serious-offence/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Ten years after its introduction, the US National Institute of Standards and Technology (NIST) has updated its ubiquitous Cybersecurity Framework (CSF).

The old version 1.1 was widely adopted, primarily because unlike many national and international standards, it is free. However, it was initially developed for use within US government agencies, for whom NIST is legally the official standards regulatory body, and then extended to cover critical infrastructure. It required some adaptation when used by private-sector and non-US organizations, but that did not stop it becoming one of the most popular frameworks. In fact, the older versions were translated into 13 languages.
Framework - Not a Standard
It's important to understand that the CSF is a framework, not a standard. Frameworks sit above standards, and provide a higher-level view of the requirements mandated by a range of standards. In essence, a framework is a conceptual model, and can be useful in clarifying one's thinking about the entire range of cybersecurity activities.
Of course, most of those requirements are security controls - and in that sense, the CSF is a controls catalogue. However, it actually cross-references the controls and control objectives from a range of different standards.
Another key convenience of the CSF is that it makes compliance efforts and gap analysis significantly easier. An organisation which has already implemented, or perhaps achieved certification against, a particular standard can use the CSF to check off requirements which it already meets from other standards. This makes it much easier to identify the work required to comply with additional standards.
Organization
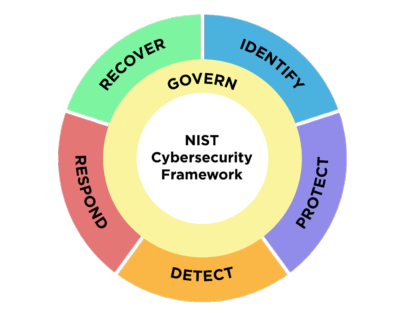
The original standard was organized around five key functions:
- Identify (assets, threats, vulnerabilities, etc.)
- Protect (assets, via authentication, authorization and other controls
- Detect (compromises and attacks)
- Respond (incident response)
- Recover (restore assets and operations)
To these has been added a new function, Govern, which encompasses the establishment, communication and monitoring of the organization's overall risk management strategy, policies and expectations. This is a large function, as it integrates with all the other functions.
Under the functions, as before we find categories and subcategories, along with the informative references which point to the relevant standards. However, the mapping spreadsheet now adds a column containing implementation examples, which help to clarify what the subcategory really means and how to comply.
Version 2.0 has been extensively reworked, with extensive community feedback on the draft, to meet the needs of a much wider set of communities, including the private sector and community organizations such as schools.
It has also been expanded - while the older versions really consisted of a single volume plus a huge spreadsheet mapping the framework to standards, it now adds an array of supporting resources. These include quick-start guides for small business and for the creation of organizational profiles, as well as guidance for the creation of community profiles. A second worksheet provides even more detail.
Also new is a searchable catalogue of informative references, as well as a Cybersecurity and Privacy Reference Tool (CPRT) which contains a browsable set of the NIST guidance documents. Finally, a CSF 2.0 Reference TOol allows exploration and searching of the entire CSF in both human-readable and machine readable (JSON) formats.
I would expect that many organizations will rapidly migrate to version 2.0 of the CSF. The framework can be found at https://www.nist.gov/cyberframework.
Uncredited, NIST Releases Version 2.0 of Landmark Cybersecurity Framework, news release, 26 February 2024. Available online at https://www.nist.gov/news-events/news/2024/02/nist-releases-version-20-landmark-cybersecurity-framework.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
 A recent news story reveals that artificial intelligence can pose yet another risk which many will not have anticipated.
A recent news story reveals that artificial intelligence can pose yet another risk which many will not have anticipated.
Many companies have switched to using chatbots to provide online customer support via their web sites - a chatbot will work 24/7 without breaks and, even better, without payment or complaining about working conditions. And of course, these chatbots have inevitably progressed from simple keyword-recognising rules engines to much more sophisticated conversationalists based on large language models. Ideally, these models would hardly need training - turn them loose on the company's web site, feed them a product catalog, pricing information and the related terms and conditions, and turn them loose to solve all your customer support problems.
However, a recent decision by the Civil Resolution Tribunal of British Columbia (Moffatt v. Air Canada) suggests that it's not quite that simple. Back in 2022, Jake Moffat suffered a family bereavement and needed to travel to Toronto to attend his grandmother's funeral. Some airlines offer concessions, such as reduced fares, for passengers traveling due to the death of an immediate family member (you learn something new every day). And so, Mr. Moffat went to the Air Canada web site to book his travel.
While on the site, he used the customer support chatbot, and asked it about bereavement fares. The reply (which Mr Moffat wisely captured as a screenshot) says, in part
Air Canada offers reduced bereavement fares if you need to travel because of an imminent death or a death in your immediate family.
…
If you need to travel immediately or have already travelled and would like to submit your ticket for a reduced bereavement rate, kindly do so within 90 days of the date your ticket was issued by completing our Ticket Refund Application form. (emphasis in original)
Now, the words "bereavement fares" were a highlighted and underlined link to Air Canada's specific web page dealing with bereavement travel - which says, in part, that the bereavement policy does not apply to requests for bereavement consideration oafter travel has been completed. Hence, the web page says one thing, but the chatbot says quite another.
In a previous telephone conversation with an Air Canada agent, Mr. Moffat was told that the bereavement fare would be approximately $C380. However, presumably relying on the information provided by the chatbot (though this is not explicitly stated), he went ahead and booked the Vancouver-Toronto flight, and a few days later booked the Toronto-Vancouver flight, for fares of $C794.98 and $C845.38, respectively.
He then set about applying for a partial refund of the fares to match the bereavement fare. Despite email exchanges through December 2022 and February 2023. Air Canada's position was that although the chatbot had provided "misleading words", it had provided the link to the bereavement travel web page and said that it would update the chatbot.
Before the Tribunal, Air Canada argued that it cannot be held liable for information provided by one of its agents, servants or representatives, and that the chatbot is a separate legal entity that is responsible for its own actions - a position the Tribunal found to be "remarkable". Holding that the chatbot is still just a part of the Air Canada web site, and that the company is responsible for all the information on that site, the Tribunal found that Mr. Moffat's claim of negligent misrepresentation was successful and awarded damages.
A few key takeways:
- It is reasonable for a customer (or other user) to rely upon the information provided by a chatbot.
- Although the chatbot may provide a link to an information page that contains additional information, there is no reason why a customer should know that one part of the site is accurate, and another is not.
- A chatbot effectively acts as an agent of the company which operates it. It really is not sensible to argue that it has independent agency in its own right.
Cecco, Leyland, Air Canada ordered to pay customer who was misled by airline’s chatbot, The Guardian, 17 February 2024. Available online at https://www.theguardian.com/world/2024/feb/16/air-canada-chatbot-lawsuit.
Moffatt v. Air Canada, 2024 BCCRT 149, CanLII, 14 February 2024. Available online at https://canlii.ca/t/k2spq.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for our various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
One of my personal security mantras is: The enemy of security is complexity. A fascinating post in IEEE Spectrum makes the same point, specifically about contemporary approaches to software development.

In "Why Bloat Is Still Software's Biggest Vulnerability", Bert Hubert calls out software architects and developers generally over the dire state of software security, pointing to the last year's highly-publicized exploitations of Ivanti, MOVEit, Outlook, Confluence, Barracuda Email Security Gateway and the Citrix NetScaler products - to name just a few.
The current software market actually penalizes developers who take the time to deal with security properly. The market continuously demands new software, with more and more sophisticated features (if your product doesn't incorporate AI in some form, you're dead in the water). At the same time, customers prize convenience, and there's a huge advantage to the first movers in the market - hence a focus on shipping a minimum viable product before the seed capital runs out. Security? Well, we can figure that out later.
A particular problem is the increasing reliance on third-party - usually open-source - libraries sourced from repositories which may themselves have vulnerabilities. Hubert points to one, relatively simple, photo-sharing application which has 1,600 dependencies on external libraries (!). This provides an attacker with an enormous attack surface which is largely beyond the control of both the central application developer and the user.
External libraries are well-nigh essential when a product has to provide a wide range of functionality. As Hubert explains, the Barracuda Email Security Gateway vulnerability lay in the way a third-party Perl module would unpack Excel spreadsheets to scan them for malware - allowing arbitrary code execution as it did so. But if you're a security pro working on a mail gateway product, do you want to invest the time and effort required to write your own code to securely parse a spreadsheet file? I thought not.
To Hubert's credit, he puts his money where his mouth is by developing a lean image-sharing program that consists of just 1,600 lines of source code plus five important dependencies.
Is there an answer to the increasing complexity of software, along with the exponentially-growing attack surface it presents? It would be a brave man that pushes back against the demand for do-everything functionality, especially in a security product. But I can't help wondering how many times the Barracuda product actually saved a completely naive user from opening a spreadsheet and allowing it run a malware macro, versus how many organizations' networks were exploited via the vulnerability in the email gateway.
The US Cybersecurity & Infrastructure Security Agency has partnered with the Open Source Security Foundation (OpenSSF) Securing Software Repositories Working Group to publish the Principles for Package Repository Security framework. This defines four levels of security maturity for package repositories to be measured in areas sich as authentication, authorization, CLI tooling and general capabilities. This at least allows the establishment of a roadmap to secure that end of the software supply chain.
In the meantime, I know I'll be pursuing a lean approach wherever possible.
Cable, Jack and Zach Steindler, Principles for Package Repository Security, Open Source Security Foundation, February 2024. Available online at https://repos.openssf.org/principles-for-package-repository-security.
Hubert, Bert, Why Bloat Is Still Software’s Biggest Vulnerability: A 2024 plea for lean software, IEEE Spectrum, 8 February 2024. Available online at https://spectrum.ieee.org/lean-software-development.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.