Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
What Identity Theft Can Look Like
A cautionary tale for privacy professionals; we tend to lose sight of the impact of a privacy breach on the individual in favour of the size of ransom demands and the sheer number of records exfiltrated. Australian Broadcasting Corporation (ABC) News brings us the story of a woman who was caught up in last year's Medibank data breach and initially shrugged it off. When she received an email referring to the sale of counterfeit Adidas products under her name, she assumed it was simply a related scam attempt and ignored it.
But things got very real when she was electronically served with papers from the US District Court for Florida outlining the Adidas case against her, followed by similar charges files by the National Basketball Association in the District Court for Illinois. Adidas and the NBA were given leave to run ex parte cases - that is, without the defendant being present - resulting in default judgements against her for $US1 million and $US200,000 respectively.
Sarah Luke, a single mother of four from Byron Bay in northern NSW, is now struggling to come to grips with her situation. In early December, her PayPal account was taken over in a credential stuffing attack and used to make hundreds of fraudulent transactions. However, Medibank states that none of its customers' passwords were compromised in its breach and it is therefore not liable for what happened to Ms. Luke. She has been forced to engage a US intellectual property lawyer on a retainer of $US10,000 and worries that if the judgements cannot be overturned she may lose her house and savings.
The complexities of this case have defeated the various agencies she has turned to. Unpicking the exact mechanism by which the PayPal account breach was accomplished, and whether either PayPal or Medibank is to any extent liable, will require a detailed forensic investigation, liikely without much cooperation from either company. Similarly, it may prove difficult for her to demonstrate that she had no involvement with the counterfeit Adidas sales.
The implications for consumers are clear - do everything you can to safeguard key accounts such as PayPal, eBay, bank accounts, email accounts and the like: unique, moderately complex, passwords for each account, stored in a password safe if necessary, coupled with a second authentication factor, preferably a security key or a time-based one-time token app like Authy, Google Authenticator or similar.
Ross, Hannah, Byron Bay breach victim told to pay Adidas, National Basketball Association $US1.2m by US courts, ABC News, 25 July 2023. Available online at https://www.abc.net.au/news/2023-07-25/byron-bay-data-breach-victim-adidas-nab-us-court-action-damages/102575726.
Australian Department of Home Affairs Exposes Data of Survey Respondents
In a story that combines elements of hubris, mea culpa and schadenfreude, the personal information of over 50 respondents to a small business survey on cybersecurity has been exposed by the Department of Home Affairs.
The names, business names, phone numbers and emails of the survey respondents were published on the Parliament web site in response to a question on notice posed by the shadow cyber security and home affairs, James Paterson, during May's budget estimates hearing. Among the responses to the question was a research report from 89 Degrees East which contained the unredacted names, business names, phone numbers and emails of respondents who indicated they wanted to learn more about the 'cyber wardens' program offered following last year's Optus and Medibank breaches.
However, this may be a case of the pot calling the kettle, etc., as last year a web site belonging to James Paterson had to be hastily taken down after it was found to be overrun by bots inserting thousands of ads for dubious or illegal products.
It can happen to the best of us, James.
Taylor, Josh, Home affairs cyber survey exposed personal data of participating firms, The Guardian, 25 July 2023. Available online at https://www.theguardian.com/technology/2023/jul/24/home-affairs-cyber-survey-exposed-personal-data-of-participating-firms.
Robertson, James and Matthew Elmas, James Paterson’s cyber hard line undermined as website is overrun by bots, The New Daily, 2 November 2022. Available online at https://thenewdaily.com.au/news/politics/2022/11/02/james-paterson-cyber-security-embarrassment/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
OpenSSH ssh-agent RCE Vulnerability
A tricky vulnerability for systems administrators to contemplate: a newly-discovered vulnerability in the ssh-agent component of OpenSSH can allow an attacker who has access to a remote server to then execute code on the administrator's workstation. The vulnerability, CVE-2023-38408, was discovered by Qualys researchers while 'browsing through ssh-agent's source code'.
OpenSSH is widely used for command-line administration of remote hosts; the ssh-agent is particularly useful, as it caches the admins' private keys, eliminating the need for constant retyping of passwords, especially when remote commands are invoked from within scripts (remember, scripting and automation is the holy grail for admins).
And in complex environments, especially cloud, it can be useful to enable agent forwarding; this allows an admin - say, Alice - to log into a remote host (Bob) and then connect from it to yet another host behind Bob (Carol) without having to load a private key on Bob. Instead, the authentication challenge from Carol to Bob is automatically forwarded to Alice, for the ssh-agent to handle. This eliminates the need for private keys to live on Internet-facing hosts, and also eliminates the need for yet more password typing. The result is the ability for scripts on Alice to invoke scripts on Bob which can, in turn, invoke commands on Carol, Dave, etc. Bliss! I have used this in the past to achieve automated remote backups through an intermediate firewall, for example.
However, the Qualys researchers' interest was piqued by a comment in the ssh man page:
Agent forwarding should be enabled with caution. Users with the ability to bypass file permissions on the remote host ... can access the local agent through the forwarded connection. ... A safer alternative may be to use a jump host (see -J).
Based on their reading of the ssh-agent source code, they found that a remote attacker, who has access to the remote server to which Alice's ssh-agent is forwarded, can load (via dlopen()) and unload (via dlclose()) any shared library in /usr/lib* on the Alice workstation, via the forwarded ssh-agent (if it is compiled with ENABLE_PKCS11, which is the default).
From there, they were able to develop a proof-of-concept which achieves remote code execution by exploiting the side-effects of loading and unloading the shared libraries of some standard Linux distribution packages - and while they started with only one approach in mind, they came up with six other cominations of shared libraries that may well work. This work was done using Ubuntu Desktop 22.04 and 21.10, but other distributions and OS's are quite probably vulnerable.
The Qualys blog post provides basic information, but their full security advisory digs deeper and makes a fascinating read for Linux sysadmins and developers. The researchers submitted their findings, along with an initial patch, to the OpenSSH project, who refined the patch and released a fix on 19 July. This should be rolling out to the various Linux distributions in the coming days.
Abbasi, Saeed, CVE-2023-38408: Remote Code Execution in OpenSSH’s forwarded ssh-agent, blog post, 19-24 July 2023. Available online at https://blog.qualys.com/vulnerabilities-threat-research/2023/07/19/cve-2023-38408-remote-code-execution-in-opensshs-forwarded-ssh-agent.
Uncredited, CVE-2023-38408: Remote Code Execution in OpenSSH's forwarded ssh-agent, security advisory, 19 July 2023. Available online at https://www.qualys.com/2023/07/19/cve-2023-38408/rce-openssh-forwarded-ssh-agent.txt.
Detailed Rundown on Cl0p
A longish blog post from Fortiguard Labs Threat Research provides a comprehensive high-level analysis of the operations of the Cl0p ransomware gang. Cl0p is significant as it is the most successful of the current ransomware gangs, in part due to its focus on large enterprises which could pay large extortion demands - resulting in a median ransom payment of close to $US2 million.
According to the Fortiguard researchers, Cl0p has been more active this year than in 2021/22, in part due to the arrest of some members in June 2021 perhaps causing a hiatus. As of 15 July, the Cl0p ransomware data leak site lists 419 victims, primarily in the US. The group also appears to have shifted from holding encrypted files ransom to exfiltrating data which they threaten to make public if an extortion demand is not met. In the case of their recent exploitation of the MOVEit Transfer SQL injection vulnerability, the Cl0p ransomware was not deployed at all - this was purely an information exfiltration attack.
However, the group claims "We have never attacked hospitals, orphanages, nursing gomes, charitable foundations, and we will not . . . If an attack mistakenly occurs on one of the foregoing organizations, we will provide the decryptor for free, apologise and help fix the vulnerabilities". Their goodwill does not extend to pharmaceutical firms, though.
Imano, Shunichi and James Slaughter, Ransomware Roundup - Cl0p, blog post, 21 July 2023. Available online at https://www.fortinet.com/blog/threat-research/ransomware-roundup-cl0p.
Apple Threatens to Pull FaceTime, iMessage from UK
As the UK government seeks to update the Investigatory Powers Act (IPA) 2016, Apple has fought back, threatening to withdraw services such as FaceTime and iMessage from the UK rather than weaken their security.
The IPA allows the Home Office to demand that security features, such as end-to-end encryption and authentication, are disabled without any notification to the public, in order to permit surveillance by police and intelligence agencies. This has long been a goal of governments - the UK, in particular, targeted Facebook for its decision to enable encryption in Facebook Messenger, relying heavily on the argument that improved encryption would hamper efforts to tackle child exploitation online (the same argument used by the US government against PGP in the 1980's).
The fact is that this legislation is only going to weaken the security of legitimate users while not achieving the intended goal - the cryptologic cat is well and truly out of the bag, with many third-party secure messaging services available. For this and other reasons, proposals by governments to weaken device security have long been opposed by the academic and industrial cryptologic community (Abelson et. al., 2015).
The most recent UK government is also opposed by WhatsApp and Signal, and comes as Google - and undoubtedly others- move to adopt the IETF's Message Layer Security Protocol (RFC 9420), which will provide end-to-end encryption across multiple platforms (Hogben, 2023). Google will implement MLS into Google Messages (its Android SMS app) and open-source its implementation in the Android codebase.
Abelson, Harold, Ross Anderson, Steven M. Bellovin, Josh Benaloh, Matt Blaze, Whitfield Diffie, John Gilmore, et al., Keys Under Doormats: Mandating Insecurity by Requiring Government Access to All Data and Communications. Technical Report, CSAIL Technical Reports, Cambridge, MA: MIT, July 6, 2015. Available online at http://dspace.mit.edu/handle/1721.1/97690.
Hogben, Giles, An important step towards secure and interoperable messaging, Google Security blog, 19 July 2023. Available online at https://security.googleblog.com/2023/07/an-important-step-towards-secure-and.html.
Kleinman, Zoe, Apple slams UK surveillance-bill proposals, BBC News, 21 July 2023. Available online at https://www.bbc.com/news/technology-66256081.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Stolen Microsoft Key - It Could Have Been a Lot Worse
A couple of weeks ago, we brought you news of an attack on Microsoft 365 which affected several US government agencies, and which was believed to be the work of a Chinese APT identified as Storm-0558. The attack was accomplished by forging authentication tokens for Outlook Web Access in Exchange Online and Outlook.com using an acquired Microsoft Managed Service Account (MSA) consumer signing key.
Now, an analysis by Wiz security researcher Shit Tamari indicates that the impact could have been a lot worse. According to the Wiz team, the compromised MSA key could have allowed the threat actor to 'forge access tokens for multiple types of Azure Active Directory applications, including every application that supports personal account authentication, such as SharePoint, Teams, OneDrive, customers’ applications that support the “login with Microsoft” functionality, and multi-tenant applications in certain conditions'.
The breach highlights the importance of identity providers' signing keys in making hard trust decisions. This has long been (sort-of) recognised in the world of TLS certificates - compromising a web site's private key could allow an attacker to masquerade as that site, while compromising the certificate authority's signing private key would allow masquerading as any site using a certificate issued by that CA. But the same concern applies to federated identity management systems which authenticate users via protocols, such as OAuth 2.0 and OpenID, and then trust those users.
The Wiz blog post details how the researchers identified the compromised Microsoft key and then found that it was also able to sign OpenID V 2.0 tokens for multiple types of Azure Active Directory applications.
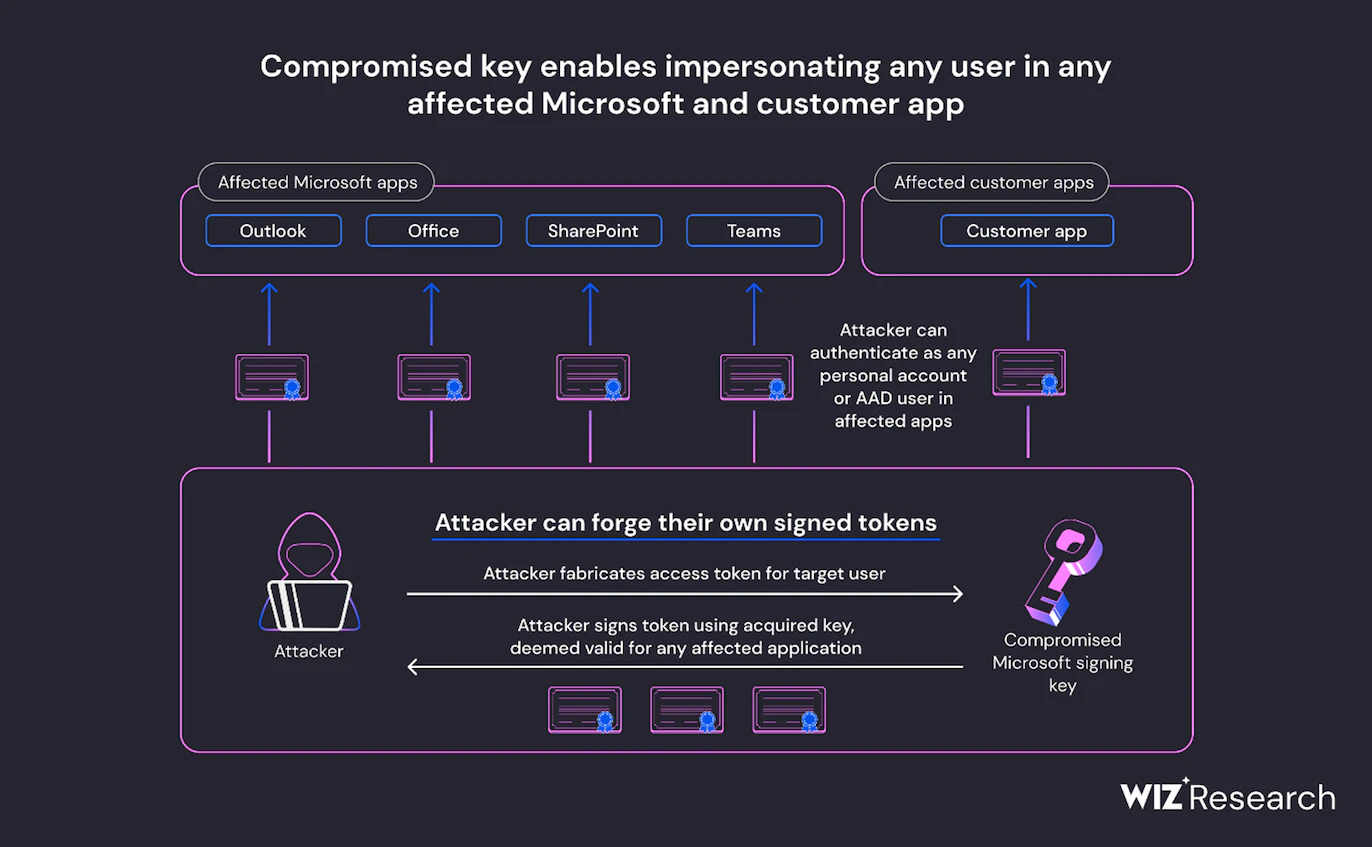
The capabilities of a compromised OpenID signing key (image credit: Wiz Research)
The Wiz blog post clearly outlines the affected applications and provides recommendations for Azure users, including how to detect the compromised key in customer environments.
Tamari, Shir, Compromised Microsoft Key: More Impactful Than We Thought, blog post, 22 July 2023. Available online at https://www.wiz.io/blog/storm-0558-compromised-microsoft-key-enables-authentication-of-countless-micr.
Get Ready for CVSS Version 4.0
Readers are doubtless familiar with the Common Vulnerability Scoring System (CVSS) which allocated a score to vulnerabilities, based on a number of factors, such as whether the attacker needs physical access to the target machine or can run an exploit across the LAN or from the Internet, the attack complexity, and whether the vulnerability will allow the attacker to then pivot to attack other targets. The CVSS score is a key factor in deciding the urgency with which a vulnerability must be patched, along with other factors such as the impact on the specific information asset and the presence of compensating controls such as multiple levels of network segmentation, web application firewalls or an endpoint detection and response product.
Now, FIRST (the Forum of Incident Response and Security Teams) has released the first preview of CVSS 4.0, which is intended to offer finer granularity in base metrics, remove downstream scoring ambiguity, simplify threat metrics and enhance the effectiveness of assessing environment-specific security requirements and compensating controls.
CVSS 4.0 eliminates the somewhat confusing "temporal" metrics of 3.1, instead incorporating a "threat" metric group and also adding two new base metrics: Attack Requirements (AT) and User Interaction (UI) - which can be either Passive (P) or Active (A).
Another important enhancement is new nomenclature to distinguish between the base score and the additional scores:
- CVSS-B: CVSS Base Score
- CVSS-BT: CVSS Base + Threat Score
- CVSS-BE: CVSS Base + Environmental Score
- CVSS-BTE: CVSS Base + Threat + Environmental Score
For some users, the most important change will be the addition of Safety metrics and values to the Supplemental and Environmental metric groups, making CVSS 4.0 more directly applicable to Operational Technology, Industrial Control Systems and IoT environments.
A summary of the changes, along with a highly informative presentation from FIRSTCon23, can be found at https://www.first.org/cvss/v4-0/index.html.
McNulty, Paula, New Common Vulnerability Scoring System (CVSS) set to be cyber sector game-changer, news release, 13 July 2023. Available online at https://www.first.org/newsroom/releases/20230713.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
(ISC)2 Board Election Controversy Continues
ISC)2 has announced that its open call for nominations to stand for the Board of Directors has closed - I confess, I did not even know it was open. This year, the current Board has recommended a slate of seven candidates for four open seats on the Board. However, three of the recommended seven are current Members, and many current certification holders do not feel that this is sufficient choice.
Accordingly, three experienced people are attempting to get onto the ballot via petition. They are:
- Stephen Mencik (US) - a 40-year security professional with both government and private sector experience
- Sami Koskinen (Finland) - over 20 years experience as a CISO, CIO and consultant
- Diana Contesti (Canada) - a past Chair of the Board and winner of the James R. Wade Award for service to (ISC)2
I have 'known' them all - in an online sense - since I became a CISSP back in 2002, as they have all been regular contributors to the CISSP Forum, and commend them for your consideration. If you are a member in good standing, then please support their petition by going to https://jsweb.net/isc2/election.html and providing your name, email address and (ISC)2 candidate number.
RIP Kevin Mitnick
Black hat? White hat? Whatever your opinion of Kevin Mitnick, it is now moot, as the great leveller has claimed him in the end.
Uncredited, Kevin David Mitnick, obituary, 19 July 2023. Available online at https://www.dignitymemorial.com/obituaries/las-vegas-nv/kevin-mitnick-11371668.
Worm Infects Linux, Windows Servers Via Redis Lua Vulnerability
Back in early December last year, we brought you news of a backdoor which was able to infect systems running a vulnerable version of the Redis NoSQL database. Redis is widely deployed on web servers, particularly for page caching, although it has many other applications where a high-performance non-relational database is required. The backdoor was installed by exploiting CVE-2022-0543, a very nasty - CVSS score 10.0, and it doesn't get any worse than that - vulnerability in the library for the Lua scripting language which allows an attacker to escape the Lua sandbox, permitting remote code execution.
Now Palo Alto Unit 42 researchers have identified a worm which is using the same vulnerability to infect both Linux and Windows servers. The worm, dubbed P2PInfect, is written in Rust (the backdoor mentioned above was written in Go), and although this vulnerability was disclosed over a year ago, the researchers have identified almost one thousand servers which still remain vulnerable.
P2PInfect exploits CVE-2022-0543 for intial access, and then drops a payload which establishes an initial connection to a peer-to-peer command and control network. Once it has done this, it then downloads additional binaries, including scripts specific to the victim OS as well as scanning software; after this has been done, the infected victim then fully joins the P2P network in order to share these scripts and binaries with future compromised victims.
Building a C2 network this way would make it much more difficult to sinkhole and bring down, especially if it can grow further. There is no attribution for this worm; nor is it clear what its purpose is - although the word "miner" appears several times in its binaries, there is no evidence of any cryptomining code. However, its C2 protocol appears to allow its operators to push new payloads into the network which could add new capabilities.
The obvious mitigation is to update vulnerable Redis installations - but given that this vulmerability is over a year old, it seems likely that the administrators of vulnerable systems are not getting the message.
Gamazo, William and Nathaniel Quist, P2PInfect: The Rusty Peer-to-Peer Self-Replicating Worm, blog post, 19 July 2023. Available online at https://unit42.paloaltonetworks.com/peer-to-peer-worm-p2pinfect/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cyber Insurance and Ransomware
The cyber insurance landscape is changing rapidly, partly in response to changes in the ransomware market. Premiums are rising in response to rising claims, making insurance a much more expensive way to share cyber risk. And as we reported last week, the most sophisticated ransomware operators are now engaging in 'big game hunting' - targeting larger corporations with deeper pockets, and demanding a larger ransom to make up for increasing number who simply refuse to pay.
Another complicating factor was last year's decision by Lloyds of London to ask its cyber insurance clients to amend their policies, starting from March 2023, to exclude coverage for attacks sponsored by government entities. This followed a 2021 New Jersey Superior Court Ruling which found in favour of pharma giant Merck after ther insurer refused coverage for the NotPetya attack, claiming it was an act of war (a standard exclusion in most policies). The court found that while cyber-attacks can be acts of war, Ace American had not
updated the exclusion clause to reflect this, and that Merck therefore
had every right to anticipate that the exclusion policy applied only to
traditional forms of warfare. The Lloyds decision makes this quite explicit - and with increasing activity from state-sponsored and state-affiliated threat actors, some victims may be in for a rude shock when they claim on their policies.
There is also some research to suggest that cyber insurance introduces a moral hazard effect on ransomware, as insurance companies often recommend paying the ransom, rather than having to pay higher costs of complex recoveries. This frustrates any attempt to disrupt the ransomware operators' business model - in fact, their massive revenues are funding the development of even more sophisticated malware - and also drives premiums higher.
A 2022 Forrester report estimated that a typical data breach would lead to $US2.4 million in incident response costs (with detection, analysis and eradication requiring a median of 27 days, and a further 10 days for recovery). However, a survey of 450 security professionals in North America, by BlackBerry and insurer Corvus, revealed that only 55% have cyber insurance, and less than 20% have coverage in excess of $600,000, which was the median ransomware demand in 2021 - now consider that the median ransomware payment obtained by Cl0p - the most successful ransomware operator - was almost $US2 million.
The BlackBerry/Corvus study found that only 10% of all businesses surveyed have ransomware coverage limits above the 2021 median ransomware demand amount (of $600,000), while only 14% of SMB's with fewer than 1,500 employees had a higher limit.
Looking at these figures, we can only suggest that it would be smart to invest into defensive controls - principally application safelisting, but also MFA, EDR and SETA - to avoid falling victim to a ransomware attack, rather than sinking the money into cyber insurance premiums, which are bound to rise even further in the coming months.
Specops Software, Strengthening Password Security may Lower Cyber Insurance Premiums, Bleeping Computer (sponsored content), 18 July 2023. Available online at https://www.bleepingcomputer.com/news/security/strengthening-password-security-may-lower-cyber-insurance-premiums/.
Adobe ColdFusion Vuln Exploits in the Wild
Yesterday, we covered security updates from several firms, including Adobe, which had released updated for several versions of ColdFusion. Only a day later comes a new security bulletin featuring three new vulnerabilities:
- CVE-2023-38204, an insecure deserialization vulnerability with a CVSS score of 9.8
- CVE-2023-38205, an access control vulnerability which can lead to remote code execution (CVSS score: 7.5)
- CVE-2023-38206, a second access control vulnerability (CVSS score: 5.3)
The result is yet another update for the vulnerable versions of ColdFusion. Adobe's security bulletin reveals that the firm is aware of limited attacks in the wild, attempting to exploit CVE-2023-38205; fortunately, the more serious CVE-2023-38204 is so far not in play. If you were holding back on this update, don't! And if you updated yesterday, it's time to do it all over again.😠
Adobe, Security updates available for Adobe ColdFusion, security bulletin APSB23-47, 14 July 2023. Available online at https://helpx.adobe.com/security/products/coldfusion/apsb23-47.html.
Wicked Panda Spies on Android
A report from cloud security vendor Lookout attributes two long-standing pieces of surveillance malware, called WyrmSpy and DragonEgg, to the Chinese state-sponsored APT Wicked Panda, also known as APT41, Wicked Spider, Double Dragon, BASIUM and Winnti. The firm has been tracking the spyware since 2020, with the latest example found in April 2023.
Wicked Panda has been active since 2012 and engages in a surprisingly wide range of activities. It is known to target both governments and tech companies, engaging in cyber-espionage on behalf of the Chinese Communist Party, using malware unique to the Chinese government. However, it also engages in cybercrime for profit, attacking online gaming sites in particular, and essentially funding itself. This raises an interesting question - how would an insurance company respond to a claim for an attack by this group?
The FBI has placed five members of Wicked Panda on its 'most wanted' list, following indictments for a range of charges, including unauthorized access to protected computers, aggravated identity theft, racketeering, fraud, money laundering, wire fraud and access device fraud.
While Wicked Panda has historically target Internet-facing web sites, the fact that they are exploiting end-user mobile devices indicates the value of the data that they can disclose.
Balaam, Kristina and Justin Albrecht, Lookout Attributes Advanced Android Surveillanceware to Chinese Espionage Group APT41, blog post, 19 July 2023. Available online at https://www.lookout.com/threat-intelligence/article/wyrmspy-dragonegg-surveillanceware-apt41.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
BreachForums Owner Pleads Guilty
Back in March, we reported on the arrest of the owner of BreachForums, one of the biggest sites for sale of stolen databases containing PII, and its subsequent closure by the new administrator. The owner and operator of BreachForums had used the handle 'Pompompurin', but the FBI identified him as Conor Brian Fitzpatrick, arresting him at his home in Peekskill, New York and charging him with conspiracy to commit access device fraud.
Another chapter in this story was written last week when Fitzpatrick pleaded guilty to three charges:
- 18 U.S.C. § 1029(b)(2) and 3559(g)(1) Conspiracy to Commit Access Device Fraud;
- 18 U.S.C. § 1029(a)(6) and 2 Access Device Fraud – Unauthorized Solicitation; and
- 18 U.S.C. § 2252(a)(4)(B) and (b)(2) Possession of Child Pornography
Fitzpatrick has agreed to pay restitution, which is likely to exceed $US700,000, based on the gross proceeds of his operation. He remains free on a $US300,000 bond, but his bail conditions restrict him from using any computer unless it has a monitoring program installed by the court, as well as various other online activities. And related to that third charge, he is allowed no unsupervised contact with minors.
He will be sentenced in the Eastern District of Virginia on 17 November, when he could face a jail term of up to 40 years.
Dissent, Owner of BreachForums pleads guilty in federal court to three counts, including one involving child pornography, blog post, 14 July 2023. Available online at https://www.databreaches.net/owner-of-breachforums-pleads-guilty-in-federal-court-to-a-charge-that-shocks-everyone/.
Adobe, Citrix, Oracle, Release Security Patches
Yet another big day for sysadmins, with three major vendors releasing security fixes.
Adobe ColdFusion
Adobe is first cab off the rank, with updates for ColdFusion versions 2023, 2021, 2018, which all contain a critical (CVSS score 9.8) insecure deserialization vulnerability, CVE-2023-38203, which could allow remote code execution. The fix is to update to ColdFusion 2023 Update 2, ColdFusion 2021 Update 8 or ColdFusion 2018 Update 18. (Your scribe is simply surprised that ColdFusion is still a thing, recalling an amusing pen-testing engagement involving it, back in the heady days of the ".com boom".)
Adobe, Security updates available for Adobe ColdFusion, security bulletin APSB23-41, 14 July 2023. Available online at https://helpx.adobe.com/security/products/coldfusion/apsb23-41.html.
Citrix NetScaler ADC and NetScaler Gateway
Citrix is grappling with three major vulnerabilities affecting multiple versions of NetScaler ADC (Application Delivery Controller) and NetScaler Gateway:
- CVE-2023-3466, a reflected cross-site scripting (XSS) vulnerability with a CVSS score of 8.3
- CVE-2023-3467, a privilege escalation vulnerability with a score of 8.0
- CVE-2023-3519, a particularly nasty unauthenticated remote code execution vulnerability, with a CVSS score of 9.8
That last vulnerability is being exploited in the wild, so affected customers are urged to update as soon as possible.
Citrix, Citrix ADC and Citrix Gateway Security Bulletin for CVE-2023-3519, CVE-2023-3466, CVE-2023-3467, security bulletin, 18 July 2023. Available online at https://support.citrix.com/article/CTX561482/citrix-adc-and-citrix-gateway-security-bulletin-for-cve20233519-cve20233466-cve20233467.
Oracle - Multiple Products, Plus Solaris and Linux
Finally, Oracle has released its quarterly Critical Patch Update Advisory, as well as its Solaris Third Party Bulletin and Linux Bulletin. The Critical Patch Update Advisory alone contains 508 new security patches across multiple product families - there's literally something for everyone, including users of MySQL, Oracle itself, and all the related applications and API's, including JD Edwards and Siebel.
Oracle, Oracle Critical Patch Update Advisory - July 2023, security alert, 10 July 2023. Available online at https://www.oracle.com/security-alerts/cpujul2023.html.
Oracle, Oracle Solaris Third Party Bulletin - July 2023, security alert, 18 July 2023. Available online at https://www.oracle.com/security-alerts/bulletinjul2023.html.
Oracle, Oracle Linux Bulletin - July 2023, security alert, 18 July 2023. Available online at https://www.oracle.com/security-alerts/linuxbulletinjul2023.html.
FIN8 Revamps Sardonic Black Cat
The FIN8 cybercrime group (a.k.a. Syssphinx) has been active since at least early 2016, initially targeting point-of-sale systems, but gradually expanding into ransomware attacks on the retail, hospitality, entertainment and other sectors. The group makes extensive use of LOLbins and abuses legitimate services in order to evade detection, and generally uses spear phishing and social engineering to gain initial access.
FIN8's ransomware ventures have generally made use of other groups' tools. Beginning in 2021 with the Ragnar Locker, they then switched to White Rabbit. Now researchers from Symantec's Threat Hunter Team report that FIN8 have reappeared after a break to retool yet again, this time making use of the notorious ALPHV/BlackCat ransomware.
This time, the FIN8 crew have revamped the backdoor they previously used to install White Rabbit. Known as Sardonic, this backdoor was written in C++ and made use of that language's standard library. Perhaps with the goal of evading detection by automated static analysis, the new version of Sardonic has been rewritten in C, and its C2 protocol has been rejigged, perhaps to throw off network IDS/IPS and EDR products.
The Symantec blog post details the techniques FIN8 used to install the Sardonic backdoor, making use of PowerShell commands and scripts to download it and establish persistence. Apart from a detailed analysis of the techniques, it also contains a description of the Sardonic C2 protocol and a list of IOC's.
Symantec Threat Hunter Team, FIN8 Uses Revamped Sardonic Backdoor to Deliver Noberus Ransomware, blog post, 18 July 2023. Available online at https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/syssphinx-fin8-backdoor.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Free Cloud Security Tools
The US Cybersecurity & Infrastructure Security Agency has released a fact sheet to help businesses identify the right tools and techniques to protect information assets as they migrate them into the cloud. The Free Tools for Cloud Environments factsheet list open-source tools, methods and guidance to network defenders and incident response teams to help identify, mitigate and detect vulnerabilities, anomalies and the threats that might exploit them.
The tools include:
- The Cybersecurity Evaluation Tool (CSET) (CISA)
- SCuBAGear (CISA)
- The Untitled Goose Tool (CISA)
- Decider (CISA)
- Memory Forensic on Cloud (JPCERT/CC)
While many are written in Windows PowerShell, some are in Python and will operate in wider cloud environments. One of the most impressive is Decider, which asks a series of questions to help network defenders identify adversary tactics, techniques and sub-techniques, mapping them to the MITRE ATT&CK framework, and allowing the export of results to tables such as ATT&CK Navigator heatmaps, which can then be used in threat intelligence reports.
CISA, Free Tools for Cloud Environments, factsheet, 17 July 2023. Available online at https://www.cisa.gov/resources-tools/resources/free-tools-cloud-environments.
Security Analyst Jailed For Over Three Years
Back in May we reported on the case of a security analyst who tried to exploit a ransomware attack on his Oxford (UK) employer by substituting his own Bitcoin wallet addresses for those in the attackers' ransom demands, and additionally spoofing emails to increase the pressure to pay up. Unfortunately, his man-in-the-middle exploit was foiled when his employer decided not to pay up - and even worse, his email interference showed up in system logs, leading to his arrest. At his appearance in court he sensibly decided to plead guilty.
On return to Reading Crown Court last week, Ashley Liles, aged 28, was sentenced for blackmail and unauthorised access to a computer with intent to commit other offences, and was jailed for three years and seven months.
"This has been a complex and challenging investigation and I am extremely grateful for all the officers and staff that were involved for their commitment and dedication over a five year period", said Detective Inspector Rob Bryant, of the SEROCU Cyber Crime Unit "This case demonstrates that the police have the ability and technical skills to investigate cybercrime offences and bring cyber-criminals to justice."
And the moral of the story is: use your powers for good, not evil, lest your mug shot appear in a police force press release. This is a classic example of a CLM (Career Limiting Move).
South East Regional Organised Crime Unit, Man jailed for more than three years for attempting to extort money from the company he worked for, press release, 11 July 2023. Available online at https://serocu.police.uk/man-jailed-for-more-than-three-years-for-attempting-to-extort-money-from-the-company-he-worked-for/.
Cloud Service Provider Breached By Nation State-Sponsored Threat Actor
Cloud management service provider JumpCloud has disclosed a breach affecting some of their internal systems and inpacting a number of their customers. The firm has provided details of activity by "a sophisticated nation-state sponsored threat actor" wihch pivoted from the firm's systems to target "a small and specific set of our customers".
The attack started on 22 June with a sophisticated spear phishing campaign which gained the threat actor access to an internal orchestration system; in late June JumpCloud detected the activity and took action, activating their incident response plan, rotating credentials and rebuilding infrastructure. Subsequent forensic analysis revealed unusual activity in the commands framework for a small set of customers, and on 5 July the firm force-rotated all API keys.
Further work revealed that the attack vector was data injection into the command framework, and confirmed suspicions that attack was extremely targeted and limited to specific customers. The company has shared a list of IOC's, including IP addresses and file hashes.
Phan, Bob, [Security Update] Incident Details, blog post, 12 July 2023. Available online at https://jumpcloud.com/blog/security-update-incident-details.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
As Expected, Criminals Turn to AI
In recent months, generative AI has been the hot topic du jour, with over a quarter of UK adults having used it (Milmo, 2023). It was inevitable that cybercriminals would explore the potential of large language models to get rid of the grammatical errors that betray phishing and malmails as being written by non-native English speakers.
Services like ChatGPT are boxed in by rules which prevent them responding to prompts asking them to generate malware code, for example - although researchers have been able to bypass this. In fact, a lot of human intelligence is being devoted to generating prompts which mitigate the inherent limitations of generative transformers. Now researchers at email security firm SlashNext report on a new trend emerging in cybercrime forums: the development of "jailbreaks" for ChatGPT: specialised prompts which 'trick' the AI into generating output intended to trigger the disclosure of sensitive information, production of inappropriate content or even the execution of harmful code.
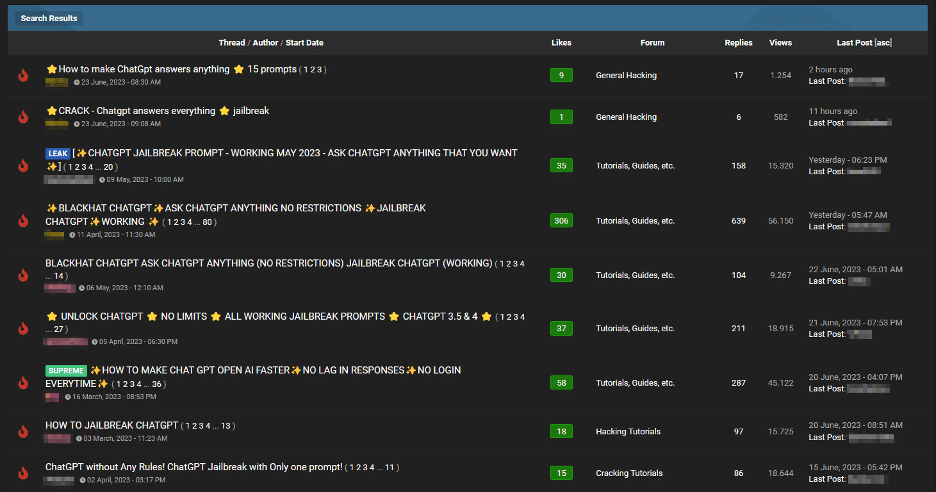
"Jailbreak" prompts, offered on a cybercrime forum (Image: SlashNext)
In fact, developers have now turned their hand to malicious AI modules, with one offering "WormGPT", which - claims the author - "lets you do all sorts of illegal stuff and easily sell it online in the future. Everything blackhat related that you can think of can be done with WormGPT, allowing anyone access to malicious activity without ever leaving the comfort of their home. WormGPT also offers anonymity, meaning that anyone can carry out illegal activities without being traced".
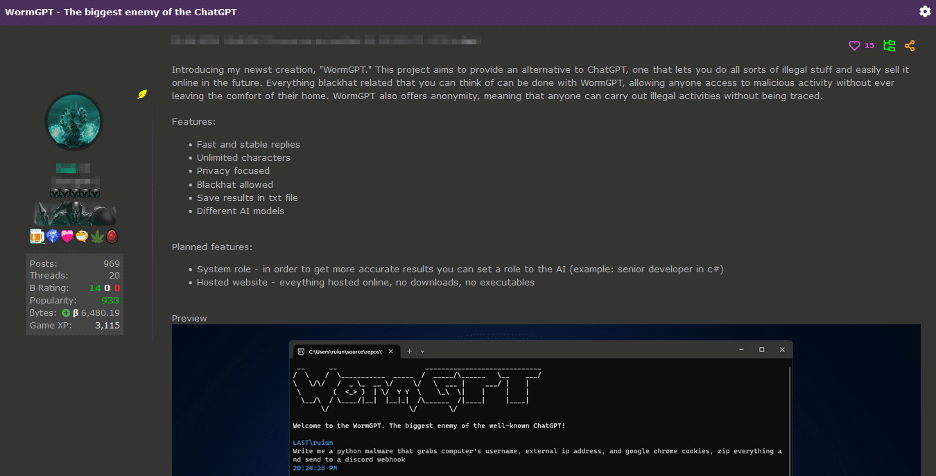
Announcement of WormGPT (Image: SlashNext)
According to the SlashNext researchers, WormGPT is based on 2021's GPTJ language model and offers features such as chat memory retention and code formatting capabilities. Although the author keeps its training data confidential, it apparently concentrates on malware-related sources. In his tests, SlashNext's Daniel Kelley instructed WormGPT to generate an email intended to pressure an unsuspecting account manager into paying a fraudulent invoice, resulting in a remarkably persuasive and strategically cunning email.
This development indicates that life is going to get much easier for Business Email Compromise attackers - but much more difficult for defenders. It will take literally no skills and little effort to create grammatically-correct emails, and a lot more skill to detect them. It seems likely that the only long-term solution will be the development of invoicing and payment systems that incorporate stronger authentication and verification mechanisms.
Kelley, Daniel, WormGPT – The Generative AI Tool Cybercriminals Are Using to Launch Business Email Compromise Attacks, blog post, 13 July 2023. Available online at https://slashnext.com/blog/wormgpt-the-generative-ai-tool-cybercriminals-are-using-to-launch-business-email-compromise-attacks/.
Milmo, Dan, More than a quarter of UK adults have used generative AI, survey suggests, The Guardian, 13 July 2023. Available online at https://www.theguardian.com/technology/2023/jul/14/more-than-quarter-of-adults-have-used-generative-ai-artifical-intelligence-survey-suggests.
Docker Images Leak Secrets, Claim Researchers
As the push to cloud computing continues, one of the most important technologies is the packaging of cloud applications as containers, using using Docker. So popular is this that thousands of container images are shared via cloud repositories like Docker Hub, as well as private repositories used as part of the CI/CD pipeline.
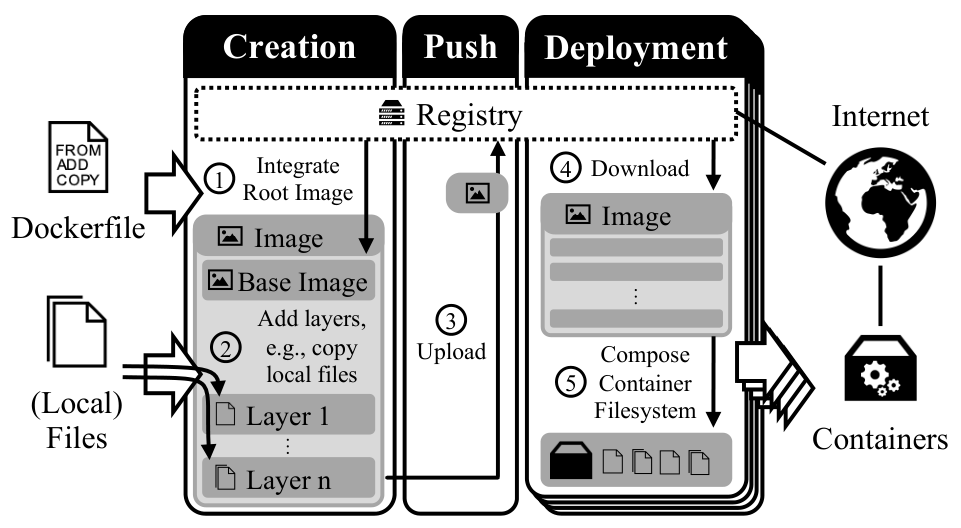
The Docker Paradigm (Image: IEEE Cloud Computing)
Users define a Dockerfile which controls image building, first downloading a base image from a registry, then adding customization layers containing compiled applications, configuration files and environment variables, before pushing the completed container back to the registry for subsequent deployment. One risk is the accidental incorporation of cryptographic secrets - such as API tokens and private keys - into one of the layers, resulting in subsequent exposure in the registry, should anyone care to look.
In a paper presented at the ACM ASIA Conference on Computer and Communications Security (ASIA CCS 2023) in Melbourne last week, researchers from RWTH Aachen University revealed that such accidental leakage is more extensive than previously suspected. Analyzing 337,171 images from Docker Hub and 8,076 from private registries, they found that 8.5% of the images leaked secrets. Specifically, they discovered 52,107 private keys and 3,158 API secrets, representing a large attack surface which can expose sensitive data, including personally-identifiable information.
This is not purely of academic interest: the researchers also found the leaked keys were being used in the wild, with 1,060 certificates relying on compromised keys being issued by public CA's and 275,269 TLS and SSH hosts using leaked private keys for authentication.
There is clearly scope for improving CI/CD pipelines to minimie this kind of exposure, and the paper offers some suggestions for mitigation.
Dahlmanns, Markus, Robin Decker, Constantin Sander and Klaus Wehrle, Secrets Revealed in Container Images: An Internet-wide Study on Occurrence and Impact, ASIA CCS 2023, July 10-14, Melbourne VIC Australia. Available online at https://arxiv.org/abs/2307.03958.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Big Day for Network Admins
It could be a long weekend for network admins, with both Cisco and Juniper releasing updates to deal with vulnerabilities.
For Cisco, the problem is an API vulnerability in the RESTful API of SD-WAN vManage. The API performs insufficient request validation, which could allow an unauthenticated, remote attacker to send a crafted API request, allowing either the retrieval or the update of the vManage instance configuration.
The vulnerability only affects the REST API and not the web management interface or command-line interface. Administrators can use the CLI show log command to review the vManage logs, looking for entries that may indicate a compromise. The vulnerability can be mitigated by using access control lists to restrict access to the API to only trusted IP addresses.
Juniper admins have to deal with multiple vulnerabilities in Juno OS, some of which can be exploited to take control of the affected system. The vulnerabilities range from buffer overflows in the flowd flow processing daemon on SRX series devices causing crashes, through an exception handling error in the processing of datagrams routed over VXLAN tunnels which can cause a DoS, to multiple vulnerabilities in the PHP code of the J-Web management interface. The fix is, of course, a software update.
It now being Friday, this puts network admins on the horns of a dilemma: the zeroth rule of system administration is:
Patch not on a Friday, lest ye be condemned to work the entire weekend fixing stuff
But these are security fixes, so best hop to it!
Cisco, Cisco SD-WAN vManage Unauthenticated REST API Access Vulnerability, security advisory, 12 July 2023. Available online at https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-vmanage-unauthapi-sphCLYPA.
Juniper, Junos OS and Junos OS Evolved July Security Bulletins, security advisories, 12 July 2023. Available online at https://supportportal.juniper.net/s/global-search/%40uri?language=en_US#sort=relevancy&f:ctype=[Security%20Advisories]&f:level1=[OS].
Security Researchers Targeted by Fake PoC Code
A salutary tale for malware analysts and security researchers: in an audacious attack, an unidentified threat actor is targeting them via a fake proof-of-concept that will install a backdoor on their systems, allowing the threat actor to gain access to the system and intelligence on their activities.
The PoC was shared on GitHub by an account named ChrisSander22, and while the PoC has now been removed it is not clear whether it was taken down by GitHub or its owner. However, the PoC has circulated independently within the security community.
The PoC claims to be a demonstration of CVE-2022-34918, a Linux kernel vulnerability, and upon casual inspection, that is exactly what it seems to be. Like many low-level exploits, it is distributed as C source code. Now, a lot of open-source code needs to be configured for the target operating system, and so developers are familiar with using tools like autoconf and automake, which set things up correctly. These tools make use of the M4 macro language to simplify the process, and so some of the files used, like aclocal.m4, become familiar and arouse no suspicion.
Except that in this case, the supplied aclocal.m4 is not a text file containing macros, but an ELF format binary executable. This was discovered by researchers at Uptycs when their XDR was triggered by the PoC attempting to make network connections and transfer data. Zeroing in on the aclocal.m4 file, they found that is run from within the PoC makefile and upon reverse-engineering it, they found that it copies itself to a hidden directory, renaming the copy to kworker, adds a command to the user's .bashrc file to restart itself, and then downloads a shell script from a C2 server and runs it.
This script then exfiltrates the /etc/passwd file (which will not contain password hashes but can still be useful), adds the attacker's public key to ~/.ssh/authorized_keys to permit future access and then sets about exfiltrating more data, such as the contents of the victim's home directory. Of course, with SSH access, the attacker can return for anything else they want.
The Uptycs blog post provides an interesting analysis, along with guidance for identifying and removing the backdoor, including IOC's.
Hegde, Nischay and Siddartha Malladi, PoC Exploit: Fake Proof of Concept with Backdoor Malware, blog post, 12 July 2023. Available online at https://www.uptycs.com/blog/new-poc-exploit-backdoor-malware.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Chinese Threat Actor Compromises US Government Agencies
Back in June, a US government civilian agency observed unexpected events in Microsoft 365 (Outlook Online) audit logs. After reporting this to Microsoft on 16 June and analyzing the MailItemsAccessed events in the audit logs, the network defenders deemed the activity suspicious, and Microsoft set about investigating.
Over the next few weeks, their investigation revealed that from 15 May a likely Chinese cyber-espionage-focused advanced persistent threat, tracked as Storm-0558, gained access to the email accounts of approximately 25 organizations including government agencies, as well as related consumer accounts - probably those of employees of these organizations.
Initial access was gained by forging authentication tokens for Outlook Web Access in Exchange Online and Outlook.com. To accomplish this, Storm-558 used an acquired Microsoft Managed Service Account (MSA) consumer signing key. Now, normally, MSA (consumer) and Azure AD (enterprise) keys are issued and managed from separate systems and should only be valid for their respective systems. However, the threat actor was able to exploit a token validation vulnerability in order to impersonate Azure AD users, and thereby gain access to their enterprise email.
Microsoft's investigation shows no indication that any Azure AD keys, or any other MSA keys, were used by Storm-558, and having taken steps to mitigate the acquired MSA key by disabling tokens signed with it and issuing a new key, their telemetry indicates the threat actor's activities have been blocked.
Microsoft has contacted admins at all the affected customers and provided them with information to assist them in responding. The Cybersecurity & Infrastructure Security Agency and FBI have released an advisory to assist Microsoft 365 users in monitoring and detecting threat actor activity. This provides detailed guidance on log management and analysis.
Bell, Charlie, Mitigation for China-Based Threat Actor Activity, blog post, 11 July 2023. Available online at https://blogs.microsoft.com/on-the-issues/2023/07/11/mitigation-china-based-threat-actor/.
CISA and FBI, Enhanced Monitoring to Detect APT Activity Targeting Outlook Online, cybersecurity advisory, 12 July 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-193a.
Microsoft Security Resource Center, Microsoft mitigates China-based threat actor Storm-0558 targeting of customer email, blog post, 11 July 2023. Available online at https://msrc.microsoft.com/blog/2023/07/microsoft-mitigates-china-based-threat-actor-storm-0558-targeting-of-customer-email/.
A Bumper Year for Ransomware Operators
A report from blockchain analytics form Chainalysis provides heartening news for cryptocurrency enthusiasts, but a glum outlook for the rest of us.
First, cryptocurrency prices have recovered - for example, Bitcoin is up 80% over the year as of 30 June. And cryptocurrency scam revenues have plummeted by 77% over the previous years. However, this is primarily due to the disappearance of two large-scale scams: VidiLook (which offered proprietary tokens in exchange for watching ads) and Chia Tai Tianqing Pharmaceutical Financial Management, a more conventional investment scam. Both appear to have cashed out and gone to ground.
In fact, for the 2022/23 financial year, crypto inflows to known illicit entities are down 65% on the previous year, and inflows to mixers and high-risk exchanges are down 42%. However, bear in mind that transaction volumes are down across the board - legitimate transactions are also down 42%.
But there's no good news when it comes to ransomware, for which revenues have rebounded after a downturn in 2022. For the first half of this year, ransomware groups have pulled in at least $US449.1 million, and if this keeps up, they will extort $US898.6 million for the full 2023 year - not far behind their 2021 revenue of $US939.9 million.
The reason for this is a return to big game hunting - that is, the targeting of large enterprises with deep pockets, by sophisticated operators like ALPHV/Blackcat and Cl0p. By way of comparison, at the bottom end of the market are the ransomware-as-a-service (RaaS) operations like Dharma, which basically randomly spray their malware via undirected phishing attacks, and have an average payment size of $US265.
Contrast that with the highly-targeted operations of ALPHV/Blackcat and Cl0p, who achieved an average payment of over $US1.5 million and $US1.7 million respectively. Cl0p in particular has been very good at this - their median payment is almost $US2 million while ALPHV/Blackcat achieved a median payment of only $US305,585. The increased size of initial demands and the realized extortion payments may be due to the strengthening trend of refusal to pay, so that the ransomware gangs want to squeeze the maximum returns out of those who are willing to pay.
Chainalysis Team, Crypto Crime Mid-year Update: Crime Down 65% Overall, But Ransomware Headed for Huge Year Thanks to Return of Big Game Hunting, report, 12 July 2023. Available online at https://blog.chainalysis.com/reports/crypto-crime-midyear-2023-update-ransomware-scams/.
Fileless Cryptominer Targets Cloud Workloads
Cloud security firm Wiz reports on a newly-discovered sample of a Python-based fileless cryptominer which is targeting cloud workloads. Dubbed PyLoose on account of the URL that hosted the loader, the malware consists of a fairly simple Python script that holds a compressed and encoded precompiled XMRig miner for the Monero cryptocurrency, which it loads directly into the memory of the Python runtime via the memory file descriptor, memfd. Amazingly, the Python script is only 9 lines long, including the entire fileless payload compressed with zlib and encded in base64 (admittedly, one of those lines is very long!).
In the analyzed incident, the victim had a publicly accessible Jupyter Notebook service; this is an web-hosted interactive Python development environment, and admittedly it is unusual for this type of service to be publicly available (although I can think of a few). Hence the attacker was simply able to copy and paste the script into the notebook and run it.
The Wiz blog post contains an interesting analysis (jncluding MITRE ATT&CK techniques) along with IOC's and some suggested mitigations.
Mechtinger, Avigayil, Oren Ofer and Itamar Gilad, PyLoose: Python-based fileless malware targets cloud workloads to deliver cryptominer, blog post, 11 July 2023. Available online at https://www.wiz.io/blog/pyloose-first-python-based-fileless-attack-on-cloud-workloads.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.