Les Bell
User blog: Les Bell
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Lapsus$ Hacker Finds Out
As we reported back in September last year, a Oxfordshire teenager was arrested on suspicion of being a key player in attacks on Rockstar Games and Uber. The teenager, now 18, has been identified as Arion Kurtaj, a key member of the Lapsus$ ransomware gang who, along with other teenagers in the UK and Brazil, conducted social engineering and more technical lateral movement exploits in extortion attacks on Rockstar, Uber, Microsoft, BT, Nvidia and Cisco, among others. Along with another 17-year-old (who is still 17, and therefore cannot be named), Kurtaj was charged with counts of blackmail, fraud and offences under the UK's Computer Misuse Act.
Back in July, psychiatrists assessed Kurtaj as autistic and deemed him not fit to stand trial; however, a trial of the other teenager was commenced, during which the jury was asked to determine whether or not he had done the acts alleged, but not whether he did them with criminal intent. They found that he had. The other teenager was found guilty.
Both defendants were unable to resist the temptation to engage in cybercrime. Despite being arrested in January 2022, upon their release they breached Nvidia's systems, using a hired accomplice to call the company's help desk to obtain credentials. They also used MFA push fatigue attacks in order to get employees to verify their logins. They were re-arrested in late March 2022, but upon his release, Kurtaj broke his bail conditions by going online again - in fact, a few weeks after the City of London Police arrested and then released him, he accessed that police force's cloud storage.
So effective were the teenagers that the US DHS ordered its Cyber Safety Review Board to examine and report upon their attacks; their report was released earlier this month, with a number of key recommendations, including a move away from voice and SMS-based MFA in favour of phishing-resistant FIDO-compliant MFA methods.
The teenagers' alleged Brazilian accomplice was arrested in October and will doubtless stand trial in that jurisdiction. Despite the fact that Kurtaj was not fit to stand trial, and did not give evidence, he is remanded in custody and both he and the unnamed teenager will be sentenced by Her Honour Judge Lees at Southwark Crown Court at a later date.
City of London Police, On the evening of Thursday 22 September ..., tweet, 23 September 2022. Available online at https://twitter.com/CityPolice/status/1573281533665972225.
Tidy, Joe, Lapsus$: Court finds teenagers carried out hacking spree, BBC News, 23 August 2023. Available online at https://www.bbc.com/news/technology-66549159.Uncredited, Cisco Talos shares insights related to recent cyber attack on Cisco, blog post, 11 September 2022. Available online at https://blog.talosintelligence.com/2022/08/recent-cyber-attack.html.
Cyber Safety Review Board, Review of the Attacks Associated with Lapsus$ and Related Threat Groups, technical report, 24 July 2023. Available online at https://www.cisa.gov/resources-tools/resources/review-attacks-associated-lapsus-and-related-threat-groups-report.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Infostealer Masquerades as MacOS App
The XLoader malware-as-a-service infostealer has existed in various forms since around 2015, targeting primarily Windows systems. Although a MacOS variant appeared in 2021, it was written as a Java program - and since most Macs no longer supported the Java Runtime Environment (JRE) as standard, its impact was highly limited.
But now a new variant has emerged, say SentinelOne researchers, this time written in the C and Objective C programming languages, compiled down to a native binary, and masquerading as an office productivity application called 'OfficeNote'. This app bundled inside a standard Apple disk image file under the name OfficeNote.dmg, signed on 17 July 2023 with the developer signature MAIT JAKHU (54YDV8NU9C).
Apple has subsequently revoked this developer key, but tests by the SentinelOne researchers indicate that the Apple malware blocker, XProtect, does not have a signature to protect against this malware, as of 21 August, and uploads to VirusTotal indicates that it spread quite widely during July. Its developers are offering this Mac version of XLoader for rent at rates of $US199/month or $US399/3 months - high in comparison with the Windows variants.
If invoked by a victim, the promised 'OfficeNote' fails to run, but in the background the malware drops and runs its payload, creating a hidden directory containing the malware as well as a LaunchAgent so that it will persist. Once running, it attempts to steal secrets from the user's clipboard as well as the Chrome and Firefox browsers, but does not target Safari. It also contacts its C2 server, hiding the server's IP address among hundreds of dummy network requests. It also uses a variety of other detection evasion techniques, such as sleeping for some time before executing malicious behaviour, and using stripped binaries to make static analysis harder.
The SentinelOne blog post contains a detailed analysis and IOC's.
Devadoss, Dinesh and Phil Stokes, XLoader’s Latest Trick | New macOS Variant Disguised as Signed OfficeNote App, blog post, 21 August 2023. Available online at https://www.sentinelone.com/blog/xloaders-latest-trick-new-macos-variant-disguised-as-signed-officenote-app/.
RCE Vulnerability Affects Ivanti Sentry
Researchers at Norwegian security firm mnemonic have discovered a zero-day vulnerability in Ivanti Sentry (formerly MobileIron Sentry), a secure gateway for mobile devices accessing corporate networks. The vulnerability, CVE-2023-38035, allows an unauthenticated threat actor to both read and write files to the Sentry server, and execute OS commands with root privileges via sudo.
The vulnerability is in some API endpoints in the Sentry server's System Manager Portal (commonly known as MICS [MobileIron Configuration Service]), which normally runs on port 8443. If this is not exposed to the Internet, a threat actor will have to have internal access. However, this can be acquired by compromising the Ivanti Endpoint Manager Mobile (EPMM), as this communicates with the Sentry server using port 8443 - and the EPMM server may be exploited via CVE-2023-35078 and CVE-2023-35081 - an authentication bypass and directory traversal vulnerabilities which have previously been exploited in the wild.
Ivanti has issued RPM packages which update currently supported versions of Ivanti Sentry.
Not entirely coincidentally, the US Cybersecurity & Infrastructure Security Agency has added this vulnerability as one of two new entries in its Known Exploited Vulnerabilities Catalog - the other is CVE-2023-27532, a missing authentication for critical function vulnerability in Veeam Backup & Replication Cloud Connect.
mnemonic, Threat Advisory: Remote Code Execution (RCE) vulnerability in Ivanti Sentry (CVE-2023-38035), blog post, 21 August 2023. Available online at https://www.mnemonic.io/resources/blog/threat-advisory-remote-code-execution-vulnerability-in-ivanti-sentry/.
Ivanti, CVE-2023-38035 - Vulnerability affecting Ivanti Sentry, blog post, 21 August 2023. Available online at https://www.ivanti.com/blog/cve-2023-38035-vulnerability-affecting-ivanti-sentry.
Ivanti, CVE-2023-38035 – API Authentication Bypass on Sentry Administrator Interface, forum post, 21 August 2023. Available online at https://forums.ivanti.com/s/article/CVE-2023-38035-API-Authentication-Bypass-on-Sentry-Administrator-Interface?language=en_US.
CISA, CISA Adds Two Known Exploited Vulnerabilities to Catalog, cybersecurity advisory, 22 August 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/08/22/cisa-adds-two-known-exploited-vulnerabilities-catalog.
Telemarketer Breached; Charity Donor Details Published on Dark Web
An April attack on a Brisbane telemarketing firm, Pareto Phone, has culminated with the dark web publication of the personal information of thousands of donors to charities which used the firm. The breach has been notified to the National Cyber Security Coordinator, but it is not clear whether the Office of the Australian Information Commissioner has been notified - and if so, within the required notification period of 30 days.
The firm has been used by a number of charities, including the Cancer Council and Canteen, which supports young people with cancer, and who reported that 2,600 current and former donors hade been contacted. It said information including full names, date of birth, addresses, email addresses and phone numbers had been released, but not financial information.
The Fred Hollows Foundation said that 1,700 of its donors had been affected, and further indicated that data had been held by the telemarketer long beyond its usefulness: "We worked with Pareto Phone only during 2013 and 2014. We were not aware our data was still held by them". This suggests a significant breach of the Australian Privacy Principles, which are an annex to the Privacy Act.
Burt, Jemima, Thousands of donors to Australian charities, including Cancer Council and Canteen, have data leaked to dark web, The Guardian, 23 August 2023. Available online at https://www.abc.net.au/news/2023-08-23/qld-charity-donors-dark-web-cyber-criminals-pareto-phone/102757194.
CISA, NSA, NIST Push Post-Quantum Cryptography
Once again, we are beating the drum about cryptographic agility and the need to prepare for the possibility that well-resourced - probably (but not necessarily) affiliated with nation states - threat actors develop the capability of breaking our public-key algorithms using quantum computers.
To this end, CISA, the NSA and NIST have jointly released an factsheet to alert organizations - particularly in critical infrastructure - of the possibilities and to start planning for the migration to post-quantum cryptography (PQC) standards. NIST will release a set of PQC standards in 2024, although we already know what many of the algorithms are likely to be.
The factsheet recommends preparing a post-quantum roadmap, starting with preparing a cryptographic inventory in order to identify technology which may be vulnerable to a quantum computing attack, then engaging with suppliers to ascertain their roadmaps. We need to start now, to ensure that the cybersecurity supply chain encompasses PQC.
CISA, Quantum-Readiness: Migration to Post-Quantum Cryptography, factsheet, 21 August 2023. Available online at https://www.cisa.gov/resources-tools/resources/quantum-readiness-migration-post-quantum-cryptography.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
HiatusRAT Targets Defense Contractors
Since March of this year, researchers at Lumen Black Lotus Labs have been tracking a complex campaign targeting edge routers for traffic collection, which they have dubbed "HiatusRAT". In June, HiatusRAT shifted its attention from Latin America and Europe, to focus on US a military procurement system as well as Taiwanese-based organizations, suggesting that the threat actor is serving Chinese strategic interests.
Since June, multiple new versions of the HiatusRAT malware have emerged, targeting a range of platform architectures, although curiously - and somewhat audaciously - these continue to use the same C2 servers. However, the new variants have been hosted on new VPS servers, with over 90% of connections to their addresses being made from a range of Taiwanese organizations, including semiconductor and chemical manufacturers and at least one municipal government.
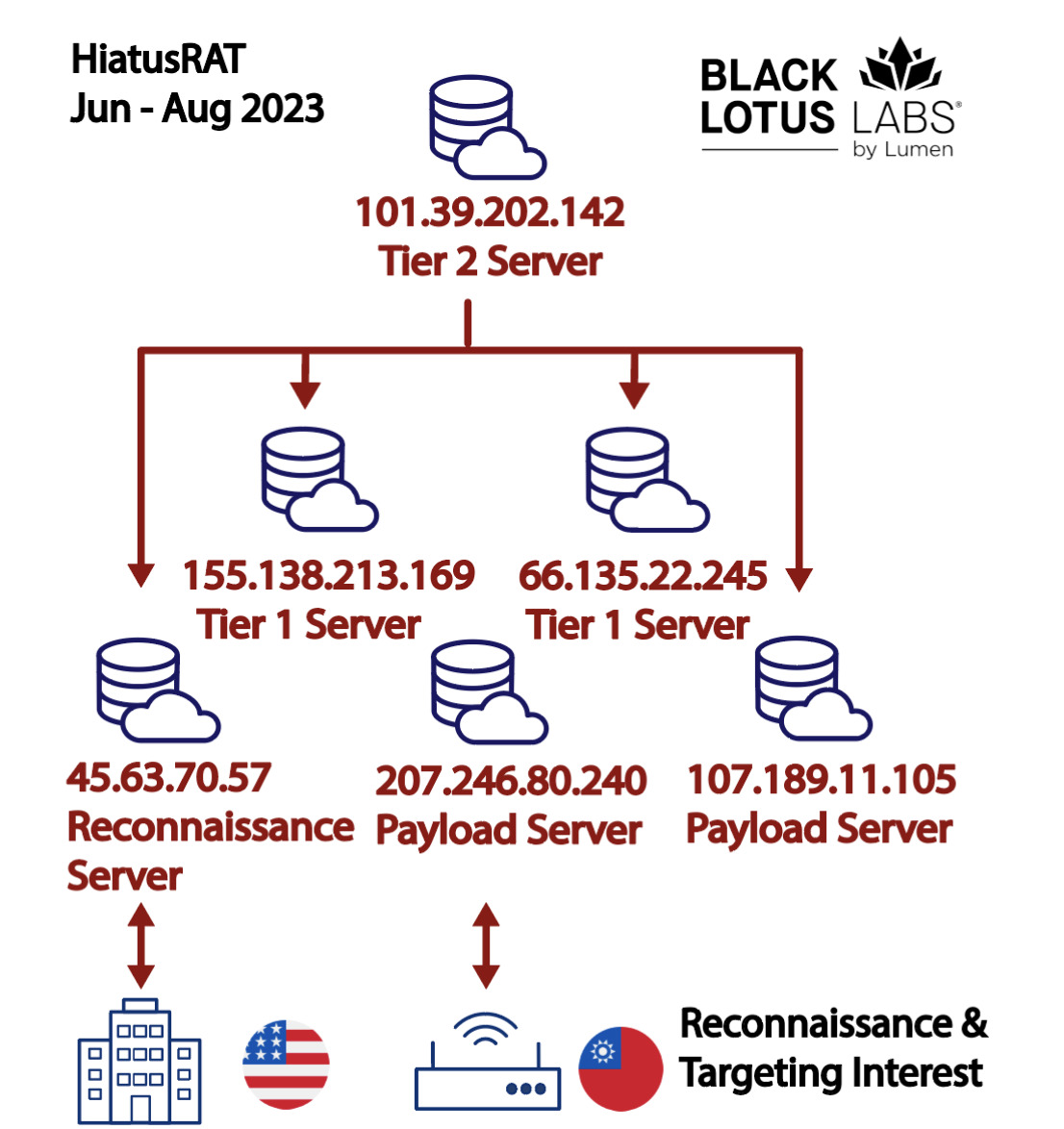
The logical connections in the new HiatusRAT network (image credit: Lumen Black Lotus Labs)
Following traffic from the distribution VPS's to upstream infrastructure, the Black Lotus Labs researchers were able to identify several new nodes in both China and the US, two of which connectd to a US Department of Defense server used for submission and retrieval of proposals for defence contracts, the traffic suggesting the threat actor was searching for publicly available information relating to defence contracts, possibly to identify defence contractors for subsequent targeting.
Black Lotus Labs, No rest for the wicked: HiatusRAT takes little time off in a return to action, blog post, 17 August 2023. Available online at https://blog.lumen.com/hiatusrat-takes-little-time-off-in-a-return-to-action/.
CISA Releases Vulnerability Summary for Week of August 14, Adds One Known Exploited Vulnerability
The US Cybersecurity & Infrastructure Security Agency has released its weekly vulnerability summary for the week of 14 August. A quick scan of just the most serious vulnerabilities - those with a CVSS 3.x score of 9.0 or above - reveals a variety of remote code execution, SQL injection, privilege escalation, missing function level access control and other vulnerabilities across a range of products including WordPress plugins, Veritas NetBackup Snapshot Manager, GitPython and various Huawei products.
CISA has also added one vulnerability to its Known Exploited Vulnerabilities Catalog - CVE-2023-26359, an Adobe ColdFusion deserialization of untrusted data vulnerability that can allow remote code execution.
CISA, Vulnerability Summary for the Week of August 14, 2023, security bulletin, 21 August 2023. Available online at https://www.cisa.gov/news-events/bulletins/sb23-233.
CISA, CISA Adds One Known Exploited Vulnerability to Catalog, cybersecurity advisory, 21 August 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/08/21/cisa-adds-one-known-exploited-vulnerability-catalog.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Juniper Releases Advisory for Multiple Vulnerabilities in Junos OS
Networking device manufacturer Juniper has released an advisory dealing with multiple vulnerabilities in Junos OS on SRX Series and EX Series. The vulnerabilities are:
- CVE-2023-36844: A PHP external variable modification vulnerability allows an unauthenticated network attacker to control some important environment variables (CVSS 3.x score: 5.3)
- CVE-2023-36845: A PHP external variable modification vulnerability allows an unauthenticated network attacker to control some important environment variables (CVSS 3.x score: 5.3)
- CVE-2023-36846: A function level access control vulnerability allows an unauthenticated network attacker to compromise filesystem integrity and upload arbitrary files (CVSS 3.x score: 5.3)
- CVE-2023-36847: A function level access control vulnerability allows an unauthenticated network attacker to compromise filesystem integrity and upload arbitrary files (CVSS 3.x score: 5.3)
Individually, these vulnerabilities aren't too bad, but when chained, they escalate to allow unauthenticated remote code execution.
The vulnerabilities affect all versions of Junos OS on SRX Series prior to 20.4R3-S8 and Junos OS on EX Series prior to version 20.4R3-S8. Admins of affected systems should either patch immediately or disable J-Web.
Juniper Networks Inc., 2023-08 Out-of-Cycle Security Bulletin: Junos OS: SRX Series and EX Series: Multiple vulnerabilities in J-Web can be combined to allow a preAuth Remote Code Execution, support article, 17 August 2023. Available online at https://supportportal.juniper.net/s/article/2023-08-Out-of-Cycle-Security-Bulletin-Junos-OS-SRX-Series-and-EX-Series-Multiple-vulnerabilities-in-J-Web-can-be-combined-to-allow-a-preAuth-Remote-Code-Execution?language=en_US.
ESET Spots Zimbra Phishing Campaign
Security researchers at ESET have reported a mass phishing campaign intended to capture user account credentials for the Zimbra freemium collaboration platform. The campaign seems to be targeting SME and government users in Poland, followed by Ecuador and Italy; the threat actor behind the campaign remains unidentified.
Campaign targets receive emails which purport to be from a mail server administrator, advising of an upcoming change to the client login page. Attached is an HTML 'preview' of the new login page - customized with the name and logo of the target organization and pre-filled with the intended victim's email address - which the recipient is lured to open. Should they naively enter their passphrase, it will be submitted, by the HTML form, to a server controlled by the attackers.
The campaign is far from sophisticated, but it is far from the first to target budget-constrained organizations using Zimbra Collaboration, suggesting that such campaigns are generally successful.
Šperka, Viktor, Mass-spreading campaign targeting Zimbra users, blog post, 17 August 2023. Available online at https://www.welivesecurity.com/en/eset-research/mass-spreading-campaign-targeting-zimbra-users/.
WinRAR Vulnerability Leads to RCE
Zero Day Initiative researcher 'goodbyeselene' has disclosed a rather nasty vulnerability, CVE-2023-40477, in the popular WinRAR file archiving utility. The vulnerability, which has a CVSS 3.x score of 7.8, is in the code for processing recovery volumes, where a buffer overflow can allow an attacker to execute code in the context of the WinRAR process.
The result is that, by crafting a malicious archive file, or perhaps by luring a victim to a malicious web page, an attacker can achieve a remote code execution attack. The vulnerability was fixed in WinRAR 6.23, which was released on 2 August 2023.
Zero Day Initiative, RARLAB WinRAR Recovery Volume Improper Validation of Array Index Remote Code Execution Vulnerability, security advisory, 17 August 2023. Available online at https://www.zerodayinitiative.com/advisories/ZDI-23-1152/.
BEC Attack Costs Home Buyers Their Life Savings
Finally, a salutary tale for those engaged in large personal purchases - which usually means cars and real estate. Business email compromise actors continue to attack these large transfers, and the results can be devastating.
A New South Wales couple were in the final stages of buying their first home, and had received an invoice from the conveyancer for the payment of their deposit. So they transferred the requested amount - and then heard nothing. When they investigated, they found that the account they had transferred their deposit to had been drained, and they had lost $A274,311.57. Their bank was able to recover only $A270.72.
“We were just emailing back and forth, and then we get an email saying, ‘This is the account you need to pay the money into’,” said the victim. “I had quite a reasonable relationship with the conveyancers. So I just didn’t think anything of it … It was getting close to completion.
“I just paid it. There was no warning to ring them before I pay.”
Unfortunately, the onus is on the customer to confirm the details of the destination bank account, and this should always be done out-of-band, by telephone or by using a funds transfer system that links the account to some other verification data.
Kelly, Cait, Gone in two transfers: the email scam that cost Australian homebuyers their life savings, The Guardian, 20 August 2023. Available online at https://www.theguardian.com/australia-news/2023/aug/20/australian-email-payment-redirection-scam.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
PowerShell Gallery Users Vulnerable to Typosquatting Attacks
The Windows PowerShell scripting language is incredibly powerful, able to hook into lots of low-level functionality in the underlying operating system, and hence is extremely popular with system administrators, as well as developers of admin tools. Of course, the same attributes make PowerShell attractive to threat actors, too, and they use PowerShell scripts in a range of attacks.
Now researchers at Aqua have drawn attention to a major vulnerability in the PowerShell software supply chain - specifically, in PowerShell Gallery, which is the major repository of PowerShell packages. PowerShell Gallery hosts thousands of packages and boasts billions of downloads - it is the first place administrators and PowerShell developers will turn to when looking for packages useful in their work. However, a lax approach to validating the names of submitted packages makes it possible for attackers to dupe victims into installing malicious packages.
Other repositories and package managers, such as npm, impose rules which prevent the creation of packages with a similar name to existing, legitimate, packages. For example, there is an existing npm package called reactnative, and as a consequence, no-one can create packages with names like react_native, react-native, react.native and so on. If they try, the server responds with a 403 Forbidden status.
There is no such checking in PowerShell Gallery. In addition, the use of periods in package names, such as the "Az." prefix for names of packages relating to Azure, is only a convention, and not a scoping rule that restricts the creation of packages within a domain. The Aqua researchers give the example of Aztable, a popular module which provides functions for manipulation of Azure Storage Tables - there is nothing to stop someone creating a module called Az.Table.
The problem is exacerbated by the fact that module creators can fake almost every detail in the landing page for their module, making it appear to be the legitimate package which they are spoofing. Determining the real author of a PowerShell module can be near-impossible.
These are not the only problems with PowerShell Gallery; the Aqua researchers also found a way to enumerate unlisted modules, including those which were hidden because they exposed secrets such as API keys. But they went on to create a proof-of-concept for a typosquatting attack, creating a fake module which would reveal when it was downloaded and deployed - and within just hours, they started receiving responses from hosts across multiple cloud services.
The researchers disclosed their findings to the Microsoft Security Resource Center in late September of 2022; however, as of 16 August 2023, the vulnerabilities seem to remain.
Weinberger, Mor, Yakir Kadkoda and Ilay Goldman, PowerHell: Active Flaws in PowerShell Gallery Expose Users to Attacks, blog post, 16 August 2023. Available online at https://blog.aquasec.com/powerhell-active-flaws-in-powershell-gallery-expose-users-to-attacks.
Citrix ShareFile Vulnerability Exploitation in the Wild
The Cybersecurity & Infrastructure Security Agency has added one vulnerability to its Known Exploited Vulnerabilities Catalog this week - CVE-2023-24489, a vulnerability in Citrix ShareFile, also known as Citrix Content Collaboration. This is a nasty one, with a CVSS 3.x base score of 9.8 (although Citrix rate it at only 9.1).
This vulnerability goes back to early June, when it was disclosed to Citrix by AssetNote researcher Dylan Pindur, who was able to use it "to achieve unauthenticated arbitrary file upload and full remote code execution by exploiting a seemingly innocuous cryptographic bug". The bug in question allows what is essentially a variant of a padding oracle attack, and Pindur's blog provides a nice potted explanation and demonstration of its operation.
ShareFile users should update to ShareFile storage zones controller 5.11.24 or later. This is especially important now that the vulnerability is being actively exploited.
Citrix, ShareFile StorageZones Controller Security Update for CVE-2023-24489, security bulletin, 13 June 2023. Available online at https://support.citrix.com/article/CTX559517/sharefile-storagezones-controller-security-update-for-cve202324489.
Pindur, Dylan, Encrypted Doesn't Mean Authenticated: ShareFile RCE (CVE-2023-24489), blog post, 4 July 2023. Available online at https://blog.assetnote.io/2023/07/04/citrix-sharefile-rce/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Citrix NetScaler ADC Exploitation - Almost 2,000 Machines Back-Doored
Back in mid-July, we brought you news of a Citrix security bulletin advising of patches for three significant vulnerabilities in the company's Netscaler application delivery controller. One of these, CVE-2023-3519, is a particularly nasty unauthenticated remote code execution vulnerability, with a CVSS score of 9.8 - clearly, something that should be addressed urgently.
Apparently, a large number of administrators didn't get the message, since security researchers at consulting firm Fox-IT (part of the NCC Group), working in conjunction with the Dutch Institute of Vulnerability Disclosure (DIVD), have discovered that found over 1800 Netscaler ADC's which have been backdoored. In some cases - 1,248 cases, to be precise - the CVE-2023-3519 patch had been installed, but only after an adversary had exploited the system and installed a web shell.
A campaign to exploit CVE-2023-3519 was already underway at the time that Citrix developed and released the patch, although the exact nature of the exploitation was not made public. However, a number of security firms started digging, and Mandiant released an informative blog post just a couple of days later, detailing their discovery of a small PHP web shell located in /var/vpn/themes, and just 113 bytes in size, which appeared to be a component of the initial exploitation. They also identified a number of malicious ELF binaries and a total of six different web shells on exploited Netscaler appliances.
Mandiant has also now published a scanning tool which uses a list of IOC's to identify Netscalers which have been compromised using CVE-2023-3519.
Meanwhile, Fox-IT and the DIVD had been doing similar work, and they now have released their findings. To quote their report:
Most apparent from our scanning results is the percentage of patched NetScalers that still contain a backdoor. At the time of writing, approximately 69% of the NetScalers that contain a backdoor are not vulnerable anymore to CVE-2023-3519. This indicates that while most administrators were aware of the vulnerability and have since patched their NetScalers to a non-vulnerable version, they have not been (properly) checked for signs of successful exploitation.
This illustrates a major problem with defensive patch management: by the time a patch is released, active exploitation may already be under way, especially if a patch is developed in response to reports of a 0-day attack, and it is entirely possible that admins may, in fact, be applying the patch to systems that have already been compromised. Even a short delay in patching increases the likelihood of this occurring, since once a patch is released, threat actors immediately set to work reverse-engineering it in order to develop their own exploits.
The lesson: patching is all very well, but it is also important to use other techniques, including monitoring and scanning for indicators of compromise, to ensure that systems have not been compromised.
Citrix, Citrix ADC and Citrix Gateway Security Bulletin for CVE-2023-3519, CVE-2023-3466, CVE-2023-3467, security bulletin, 18 July 2023. Available online at https://support.citrix.com/article/CTX561482/citrix-adc-and-citrix-gateway-security-bulletin-for-cve20233519-cve20233466-cve20233467.
Nugent, James et. al., Exploitation of Citrix Zero-Day by Possible Espionage Actors (CVE-2023-3519), blog post, 21 July 2023. Available online at https://www.mandiant.com/resources/blog/citrix-zero-day-espionage.
Mandiant, Indicators of Compromise Scanner for Citrix ADC Zero-Day (CVE-2023-3519), blog post, 14 August 2023. Available online at https://www.mandiant.com/resources/blog/citrix-adc-vulnerability-ioc-scanner.
Fox-IT, Approximately 2000 Citrix NetScalers backdoored in mass-exploitation campaign, blog post, 15 August 2023. Available online at https://blog.fox-it.com/2023/08/15/approximately-2000-citrix-netscalers-backdoored-in-mass-exploitation-campaign/.
NIST Drops CSF 2.0 Exploration Tool
Only yesterday, we discussed the release of the draft 2.0 version of the NIST Cybersecurity Framework (CSF) and mentioned the impending release of a reference tool which would allow browsing, searching and export of the CSF core data in both human- and machine-readable formats. A later version of the tool will provide the informative references which link to Standards and other resources.
And, right on cue, here it is:
NIST, NIST Cybersecurity Framework (CSF) 2.0 Reference Tool, August 2023. Available online at https://csrc.nist.gov/Projects/cybersecurity-framework/Filters#/csf/filters.
Google Develops Post-Quantum Security Keys
We are strong proponents of the use of FIDO U2F security keys as the strongest variant of multi-factor authentication, and personally use them whenever possible. The only looming cloud on the horizon is the ever-more-likely possible development of an attack, using a quantum computer, on the public-key cryptographic algorithms the security keys use. Someone may already have achieved this - if they have, they certainly would not disclose it!
So we continually track developments in post-quantum cryptography (PQC) and the cryptographic agility which prepares us to switch to post-quantum algorithms when the time comes. Now Google has announced an important next step with their development and release of a quantum resilient FIDO2 security key implementation as part of OpenSK, their open source security key firmware.
This implementation is optimized for the tightly constrained hardware of a typical security key. Written in Rust, it requires only 20 KB of memory and performs acceptably, although hardware acceleration could speed it further. It uses a hybrid approach, combining the elliptic curve DSA (ECDSA) signature algorithm with the recently standardized Dilithium quantum resistant signature algorithm.
Burzstein, Elie and Fabian Kaczmarczyck, Toward Quantum Resilient Security Keys, blog post, 15 August 2023. Available online at https://security.googleblog.com/2023/08/toward-quantum-resilient-security-keys.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Biters Bit: Hackers Hack Themselves
Threat intelligence firm Hudson Rock has built a cybercrime intelligence database consisting of over 14.5 million computers infected by infostealers. Using this database, they analyzed 100 of the leading cybercrime forums, finding an amazing 120,000 infected computers, many of them belonging to hackers, which had credentials associated with cybercrime forums.
Let that sink in: these were computers, belonging to hackers, which were infected by infostealers - either unintentionally by the hackers themselves, by associates, or who knows? Bear in mind that hackers can't resist luring in would-be hackers and script kiddies with trojaned hacking tools - download something from a disreputable site like a cybercrime forum, and the phrase caveat emptor should be tattooed on your forehead. The Hudson Rock researchers were probably inspired by a previous example of this, in which an initial access broker called "La_Citrix" accidentally infected his own computer with an infostealer he was using to gather corporate credentials for Citrix and RDP servers.
Infostealers typically enumerate a lot of information, such as system information, credentials (usernames, email addresses and plaintext passwords), browser data including session and authentication cookies and even form autofill data such as names, addresses and phone numbers. It is this information that allows the real identities of the hackers to be discovered.
The biggest single group of infected users - over 57,000 of them - came from the "Nulled.to" forum; "Cracked.io" and "Hackforums.net" were in second and third place, respectively. Analyzing password strength, Hudson Rock found that cybercrime forum users generally use stronger passwords than those used on government web sites.
It also seems that the most effective infostealer for gathering information from cybercriminals is Redline, followed by Raccoon and Azorult.
Hudson Rock, 100,000 Hackers Exposed from Top Cybercrime Forums, blog post, 14 August 2023. Available online at https://www.hudsonrock.com/blog/100-000-hackers-exposed-from-top-cybercrime-forums.
NIST Drafts Major Update to Cybersecurity Framework, Adds Governance Function
The US National Institute of Standards and Technology (NIST) has had a major success on its hands for almost a decade, in the form of its Framework for Improving Critical Infrastructure Cybersecurity. As the name suggests, this framework was originally developed for critical infrastructure like the energy grid as well as financial and telco networks - but its logical structure, coupled with the fact that it was freely downloadable let to it rapidly becoming popular across a range of organizations, right down to small and medium enterprises, both inside the US and internationally. Perhaps as a consequence, it has become better known just as the Cybersecurity Framework (CSF).
While most users were able to adapt 2018's version 1.1 of the CSF to their needs - after all, it is a framework, meaning that it provides a conceptual organizing structure and principles while actually referencing a range of other informative standards - it became obvious that the next revision would have to have a broader scope. Accordingly, the recently-released draft of version 2.0 is now officially titled "The Cybersecurity Framework", and its scope has explicitly been expanded to apply to all organizations regardless of type or size.
In order to direct this update, NIST issued a request for information in February 2022. "Many commenters said that we should maintain and build on the key attributes of the CSF, including its flexible and voluntary nature", said Cherilyn Pascoe, lead developer of the framework. "At the same time, a lot of them requested more guidance on implementing the CSF and making sure it could address emerging cybersecurity issues, such as supply chain risks and the widespread threat of ransomware. Because these issues affect lots of organizations, including small businesses, we realized we had to up our game".
As a consequence, the five principal functions of the Framework - Identify, Protect, Detect, Respond and Recover - have been augmented by a new sixth: Govern. This covers have an organization can establish its own approach to developing and supporting a cybersecurity strategy, setting cybersecurity risk alongside other senior leadership concerns such as legal, financial, operational and other types of risk.
The draft also introdiices the concept of profiles, which tailor and refine the Framework for specific industry sectors and use cases, such as manufacturing industry, elections, the smart grid and extreme fast charging infrastructure for EV's. Following the release of this draft in a few weeks will be a CSF 2.0 reference tool which will allow browsing, searching and export of the CSF core data in both human- and machine-readable formats. A later version of the tool will provide the informative references which link to Standards and other resources.
NIST, NIST Drafts Major Update to Its Widely Used Cybersecurity Framework, news release, 8 August 2023. Available online at https://www.nist.gov/news-events/news/2023/08/nist-drafts-major-update-its-widely-used-cybersecurity-framework.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Bulletproof Hosting Service Shut Down, Five Admins Arrested
In a joint operation, US and European agencies have seized all the servers of, and closed down, a bulletproof hosting service which was being used by cybercriminals to launch attacks across the world.
Image credit: Europol
According to court documents unsealed in Tampa, Florida, last week, Artur Karol Grabowski, 36, operated a web hosting company named LolekHosted, which offered secure web hosting intended to facilitate a variety of cybercrime activities, including ransomware, brute-forcing and phishing. The site allowed its clients to register using false information, making payments via cryptocurrencies. Its systems did not maintain logs of its clients' server IP addresses and in fact, frequently changed them; it also ignored abuse complaints made by third parties, and notified clients of any enquiries received from law enforcement agencies. Grabowski advertised that the site was "bulletproof", provided "100% privacy hosting" and allowed clients to host "everything except child porn."
Among the ransomware variants hosted by LolekHosted was NetWalker, which was deployed on approximately 400 networks of roughly 50 victims including municipalities, hospitals, law enforcement and emergency services, school districts, colleges, and universities, resulting in payment of over BTC 5,000 (with a current value of approximately $US146 million). One of these victims was located in the Middle District of Florida, which is why the US District Court there issued a seizure warrant for the domain registration of Lolekhosted.net - see the new banner above.
Meanwhile, the Polish Central Cybercrime Bureau (Centralne Biuro Zwalczania Cyberprzestępczości) under the supervision of the Regional Prosecutor's Office in Katowice (Prokuratura Regionalna w Katowicach) took action, seizing all the servers and arresting five administrators. It is not clear whether Grabowski was one of those arrested, but if so, and extradited to the US, he will face charges of computer fraud conspiracy, wire fraud conspiracy, and international money laundering which will attract a sentence of up to 45 years in prison.
Europol, 5 arrested in Poland for running bulletproof hosting service for cybercrime gangs, news release, 11 August 2023. Available online at https://www.europol.europa.eu/media-press/newsroom/news/5-arrested-in-poland-for-running-bulletproof-hosting-service-for-cybercrime-gangs.
US DoJ Office of Public Affairs, Administrator of 'Bulletproof' Webhosting Domain Charged in Connection with Facilitation of NetWalker Ransomware, press release, 11 August 2023. Available online at https://www.justice.gov/opa/pr/administrator-bulletproof-webhosting-domain-charged-connection-facilitation-netwalker.
DHS Plans Review of Cloud Security Practices
Last month, we brought you news of a number of attacks on Microsoft 365 (Outlook Online) which affected a number of US and European government agencies, which which were attributed by Microsoft to a Chinese state-affiliated threat actor which they track as Storm-0558. The attacks were accomplished by forging authentication tokens for Outlook Web Access in Exchange Online and Outlook.com using an acquired Microsoft Managed Service Account (MSA) consumer signing key.
In response to this intrusion, the Department of Homeland Security's Cyber Safety Review Board (CSRB) has announced plans for an in-depth review on the malicious targeting of cloud computing environments, focusing on the approaches which government, industry and cloud service providers should employ to strengthen identity management and authentication in the cloud. The intention is to develop actionable recommendations that will advance security practices for both cloud service providers and their customers.
"Organizations of all kinds are increasingly reliant on cloud computing to deliver services to the American people, which makes it imperative that we understand the vulnerabilities of that technology", said Secretary of Homeland Security Alejandro N. Mayorkas. "Cloud security is the backbone of some of our most critical systems, from our e-commerce platforms to our communication tools to our critical infrastructure. In its reviews of the Log4j vulnerabilities and activities associated with Lapsus$, the CSRB has proven itself to be ready to tackle and examine critical and timely issues like this one. Actionable recommendations from the CSRB will help all organizations better secure their data and further cyber resilience".
Once completed, Secretary Mayorkas will provide a report to the Cybersecurity and Infrastructure Security Agency and thence ultimately to President Biden. The CSRB has previously reported on the log4j vulnerability and its most recent report, publicly released only last week, examined the recent attacks by the extortion-focused Lapsus$ ransomware group, finding that Lapsus$ leveraged simple techniques to evade the industry-standard security tools used by most enterprises.
Department of Homeland Security, Department of Homeland Security’s Cyber Safety Review Board to Conduct Review on Cloud Security, press release, 11 August 2023. Available online at https://www.dhs.gov/news/2023/08/11/department-homeland-securitys-cyber-safety-review-board-conduct-review-cloud.
Cyber Safety Review Board, Review of the Attacks Associated with Lapsus$ and Related Threat Groups, technical report, 24 July 2023. Available online at https://www.cisa.gov/resources-tools/resources/review-attacks-associated-lapsus-and-related-threat-groups-report.
CISA Releases Vulnerability Summary for Week of 7 August
The Cybersecurity & Infrastructure Security Agency has released its weekly summary of new vulnerabilities culled from NIST's National Vulnerability Database. It includes the usual array of issues, some with CVSS scores of 9.8 and 9.9. As always, worth a look.
CISA, Vulnerability Summary for the Week of August 7, 2023, bulletin, 14 August 2023. Available online at https://www.cisa.gov/news-events/bulletins/sb23-226.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
US Aims to Further Secure Open Source Software
There was a time, twenty years or so ago, when large software firms, particularly in the US Pacific North-West, were highly dismissive of open source software. However, in today's world, its importance cannot be over-stated - the vast majority of software stacks are either completely or partially based on open source. In fact, by some estimates, open source underpins 96% of the world's software and is a major public good, not to mention a major foundry for innovation.
However, open source is not without its risks - who can forget the Heartbleed vulnerability in OpenSSL, or the log4j vulnerability of late 2021? Both of these highlight the exent to which commercial vendors are highly reliant on open source projects, yet contribute little or nothing to the costs of development and maintenance. OpenSSL was deployed by virtually every commercial UNIX vendor, yet they contributed nothing to its maintenance - a situation which, fortunately, changed dramatically following the adverse publicity generated, while the log4j vulnerability was first reported by a software engineer at Alibaba - a corporation with market capitalization of $US348 billion at the time - which had contributed nothing to the Apache Foundation's maintenance costs.
As a result, there are increasing concerns that the current open source development model may not be sustainable, with a number of codebases relying on open source projects that had no development activity and no user updates in the preceding two years - suggesting that these projects are no longer being maintained at all.
Earlier this year, the National Security Advisor to the White House, Jake Sullivan, hosted a one-day meeting of major software industry companies to discuss initiatives to improve open source security, and now the Cybersecurity and Infrastructure Security Agency, the Office of the National Cyber Director, the National Science Foundation, the DoD's Advanced Research Projects Agency and the Office of Management and Budget have announced a Request for Information, seeking industry input on where the US government should prioritize efforts to secure open source software. This initiative will integrate the National Cybersecurity Strategy's focus on open source with CISA's Secure by Design efforts.
Over the last year, the interagency Open Source Software Security Initiative (OS3I) working group has identified several focus areas, such as reducing the proliferation of memory unsafe programming languages (which we have seen bear fruit with the incorporation of support for Rust in the Linux kernel and elsewhere); designing implementation requirements for secure and privacy-preserving security attestations; and identifying new focus areas for prioritization. The RFI is intended to further that last area by identifying areas most appropriate to focus government priorities, and addressing critical questions such as:
- How should the Federal Government contribute to driving down the most important systemic risks in open-source software?
- How can the Federal Government help foster the long-term sustainability of open-source software communities?
- How should open-source software security solutions be implemented from a technical and resourcing perspective?
The RFI process will engage with interested parties in three phases:
- Phase I - Addressing Respondent Questions About this RFI (which can be sent to OS3IRFI@ncd.eop.gov by 18 August 2023)
- Phase II - Submission of Responses to the RFI by Interested Parties, which will conclude on 10 October 2023
- Phase III - Government Review
The RFI provides additional guidance for potential respondents, including questions which they should address and a list of potential areas and sub-areas of focus.
In the CISA news release, the authors make the point that "The federal government is one of the largest users of open source software in the world, and we must do our part to help secure it. This requires widescale efforts to help uplift the level of security in the open source ecosystem." They then go on to compare this effor to President Eisenhower's Federal Aid Highway Act of 1956, which authorized $US25 billion of funding to build 41,000 miles of highways over the next decade; the result, according to one report, was that "every $1 spent returned more than $6 in economic productivity".
The scale of this effort may be smaller, but considering the contribution of open source software projects to the global economy and the current level of losses due to cyber-attacks, the return on investment may be even higher. And the authors do not expect the government to carry the economic can, pointedly remarking that, "We envision an ecosystem in which creating secure open source code and regularly assessing the security of existing open source code is the norm rather than an added burden. As part of this, software manufacturers that consume open source software should contribute back to the security of the open source software they depend upon".
Goldstein, Eric and Camille Stewart Gloster, We Want Your Input to Help Secure Open Source Software, news release, 10 August 2023. Available online at https://www.cisa.gov/news-events/news/we-want-your-input-help-secure-open-source-software.
Office of the National Cyber Director, Open-Source Software Security: Areas of Long-Term Focus and Prioritization, Request for Information (RFI), 10 August 2023. Available online at https://www.regulations.gov/document/ONCD-2023-0002-0001.
Synopsis Inc., 2023 Open Source Security and Risk Analysis Report, technical report, 16 February 2023. Available online at https://www.synopsys.com/software-integrity/resources/analyst-reports/open-source-security-risk-analysis.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Phishing Email Infection Chain Uses Rusty Injector
A phishing campaign analysed by FortiGuard Labs researchers has revealed the use of a new injector as part of its infection chain. The injector, which is written in the Rust programming language, allows the attackers to base64-encode its shellcode payload and then encrypt it with their choice of AES, RC4 or LZMA in order to evade detection.
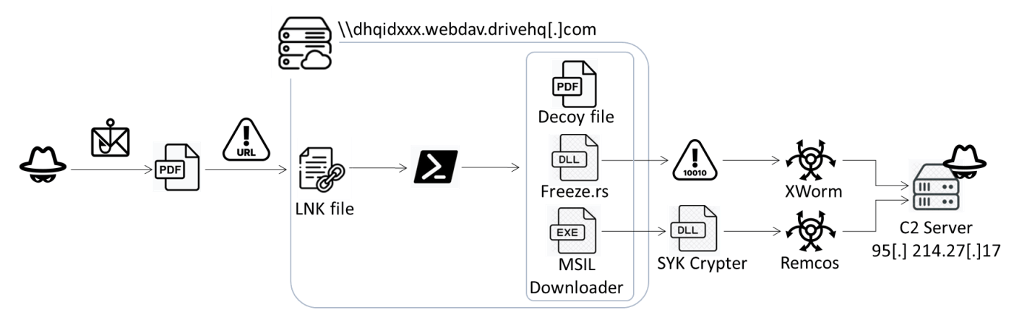
The infection chain - the injector is derived from the "Freeze.rs" Red Team tool. (image credit: FortiGuard Labs)
The attack is delivered via a malicious PDF attachment to a phishing email; the PDF uses a blurred image to lure the victim into clicking a button, which reads "View Document on Desktop", in front of it. Clicking the button causes the victim's system to download a malicious HTML file; rather than simply using JavaScript to download a malware payload - an action that could easily be spotted by EDR tools - the file uses the search-ms protocol to trigger a search for a specific file on a remote cloud storage server provided by DriveHQ.
While this file displays a PDF file icon, it is actually a .LNK file which executes a PowerShell script. This, in turn, uses regsvr32 to launch the injector from a file called doc.dll. The injector starts by displaying a decoy file, T.pdf, which contains the unblurred text the user expects, executes AA.exe and then force-closes all File Explorer windows.
The doc.dll injector creates a notepad.exe process, then decompresses or decrypts and base64-decodes the shellcode, injecting it into that process; this mirrors the behaviour of a red team tool called "Freeze.rs", which was only launched in May, not long before this campaign started. The shellcode uses code to bypass the Windows Antimalware Scan Interface (AMSI) and Windows Lockdown Policy (WLDP) before executing XWorm, a .NET remote access trojan which is capable of enumerating device information, keystroke logging, screenshot capture and remotely controlling the victim system.
The other file, AA.exe, is a downloader programmed in Microsoft Intermediate Language (MSIL) which downloads an obfuscated SYK Crypter carrying a payload which is ultimately decrypted and injected into a process to run the Remcos RAT (actually, a legitimate remote access utility). The AA.exe downloader also remains persistent, by being copied into the "Startup" folder.
Given the extensive detection evasion techniques employed in this campaign, it will prove difficult for anti-malware and EDR tools to respond to it. As always, we have to rely on the user as the last line of defence, alerting them to the use of a button in front of a blurred image to lure them into download the malware. Genuine business documents, such as purchase orders and invoices, simply do not work this way - so don't fall for the lure!
Lin, Cara, Attackers Distribute Malware via Freeze.rs And SYK Crypter, blog post, 9 August 2023. Available online at https://www.fortinet.com/blog/threat-research/malware-distributed-via-freezers-and-syk-crypter.
Citizen Lab Uncovers Classic Crypto Vulnerability in Tencent Sogou Input Method
While this particular vulnerability only exists in a virtual keybard for inputting Chinese ideographic characters on Windows, Android and iOS, it carries a lesson for all of us. An analysis of the Tencent Sogou Input Method conducted by University of Toronto's Citizen Lab turned up a classic vulnerability in its "EncryptWall" home-spun encryption system. Given that Sogou Input Method - a predictive keyboard which uses the Wubi 5-stroke character model - has over 455 million monthly active users and accounts for 70% of Chinese input method users, the security of its encryption system is important for users who wish to avoid surveillance.
The Citizen Lab researchers discovered that the EncryptWall system uses its own home-spun method to encrypt requests which are sent to the EncryptWall API endpoints over conventional HTTP protocol. In other words, rather than using HTTPS, which operates using the TLS protocol to encrypt its entire payload - both headers and bodies - Encryptwall tunnels its encrypted traffic over unencrypted HTTP POST requests. The encryption is performed using 256-bit AES (probably 128-bit AES would be fine) with the AES key protected using 1024-bit RSA (probably not strong enough) with PKCS#1.5 padding.
The major vulnerability is in the implementation of AES, which is done using cipher block chaining (CBC) mode. The way this is done renders it vulnerable to a padding oracle attack - an attack which was discovered back in 2002 by Vaudenay. In this attack - a type of chosen ciphertext attack - the attacker is able to send datagrams to a system and examine the returned error codes or messages to see whether they indicate a decryption error or a padding error - and thereby discover the correct key and then the message contents.
It turns out that the iOS implementation of EncryptWall is not vulnerable, for the simple reason that its POST requests are all sent over TLS, which fixed the padding oracle vulnerability several versions ago. However, both the Windows and Android versions are vulnerable.
The lesson for users is obvious: since the researchers disclosed the vulnerability to Tencent, a fix is available and users should update to version 13.7 for Windows, 11.26 for Android and 11.25 for iOS. For software developers, the lesson is an old one: don't try to roll your own cryptographic schemes! It would have been much simpler for the Tencent developers to simply encapsulate their API traffic in TLS, since they would not have had to develop their own crypto implementation - but it would have been more secure, too, since TLS fixed the problem only a year or so after it was discovered, i.e. in 2003.
Knockel, Jeffrey, Zoë Reichert and Mona Wang, “Please do not make it public”: Vulnerabilities in Sogou Keyboard encryption expose keypresses to network eavesdropping, technical report, 9 August 2023. Available online at https://citizenlab.ca/2023/08/vulnerabilities-in-sogou-keyboard-encryption/.
Vaudenay, Serge, Security Flaws Induced by CBC Padding: Applications to SSL, IPSEC, WTLS..., Advances in Cryptology - EUROCRYPT 2002, pp. 534–545. Available online at http://link.springer.com/chapter/10.1007/3-540-46035-7_35.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.