Les Bell and Associates Pty Ltd
Blog entries about Les Bell and Associates Pty Ltd
Cloud applications employ a variety of software architecture patterns, but high among them is the microservices architecture, which links a number of intependently-running processes. The links can be by means of RESTful API's or via message-oriented middleware such as Amazon's Simple Queue Service, Google Cloud Pub/Sub and others. Among the open source offerings like RabbitMQ and OpenMQ is the Apache Project's ActiveMQ, a Java-based multi-protocol message broker which can connect a variety of clients using protocols such as AMQP and MQTT (which is widely used on the Internet of Things). ActiveMQ is also compatible with the Java Messaging Service API, making migration of earlier application code easy.

Now Trend Micro reports on an active campaign which exploits CVE-2023-46604, a remote code execution vunerability in the Java OpenWire protocol marshaller used by ActiveMQ. The vulnerability allows an attacker to manipulate serialized class types in the protocol to instantiate any class found on the classpath. This occurs because the OpenWire code fails to validate a throwable class type (used in exception handling).
The vulnerability is being used by a threat actor to download and install malware - primarily the Kinsing cryptominer. This particular campaign uses CVE-2023-46604 to instantiate a ProcessBuilder object, calling its start() method to execute a bash shell which uses either curl or wget to download a malicious installer script from a C2 server and execute it. Once the Kinsing malware is installed and running, it fetches further binaries and payloads from the C2 server. Interestingly, Kinsing then proceeds to search for and kill any competing cryptominers before adding a cron job which will download and run its bootstrap script every minute, ensuring it is always updated. It completes its infection by installing a rootkit which loads from /etc/ld.so.preload.
It then sets to work, using the infected machine's CPU resources to mine cryptocurrencies like Bitcoin, dragging the system performance down in the process.
The Kinsing operators are not the only ones exploiting CVE-2023-46604, which makes it all the more urgent for organizations using ActiveMQ to update their systems to versions 5.15.16, 5.16.7, 5.17.6 or 5.18.3, which have been patched to call an added validateIsThrowable() method in the BaseDataStreamMarshall class.
All this shows the danger of not thoroughly sanitizing input, especially when the client is untrusted (as it usually is). We generally remember to sanitize form input from browsers and in desktop programs, but it is easy to overlook data deserialization, both when reading from databases and in message-oriented middleware.
The Trend Micro write-up includes a more detailed analysis and explanation as well as a YARA rule which can be used for scanning.
Girnus, Peter, CVE-2023-46604 (Apache ActiveMQ) Exploited to Infect Systems With Cryptominers and Rootkits, research report, 20 November 2023. Available online at https://www.trendmicro.com/en_us/research/23/k/cve-2023-46604-exploited-by-kinsing.html.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
A coalition of over a dozen major Australian corporations have teamed up to share real-time threat intelligence in an attempt to protect their customers from online scams. The new National Cyber Intel Partnership will be a key component of the government's new cybersecurity strategy, which is due to be introduced tomorrow.

A pilot program run by Westpac, Telstra and Woolworths in collaboration with the National Cyber Security Coordinator in the Department of Home Affairs allowed Westpac, for example, to pass threat intel about a phishing email and website to the ACSC for further analysis, before the details were relayed to telco Telstra to block traffic to the site.
The sharing of threat indicators is currently partially automated, using protocols like STIX and TAXII, with the aim of eventual full automation. The participants in the pilot program are expected to present their findings to other partners by the end of the year, and the scheme is expected to expand to block a much larger range of threats including malware, scam websites and lures to privileged insiders such as fake job ads.
The other members of the Partnership include Optus, TPG, National Australia Bank, Commonwealth Bank, ANZ, Qantas, National Broadband Network Co, CyberCX, Palo Alto, the Australian Competition and Consumer Commission, and the Australian Signals Directorate, with more companies expected to join in the future..
With the majority of individual consumers and businesses being customers of the major ISP's and banks, the result should be a significant increase in protection, achieved through a kind of shared immune system: once one of the members detects a threat, the entire immune system will act to block it.
In a related announcement, Minister for Home Affairs and Minister for Cyber Security, Clare O'Neill, is today expected to reveal a scheme which will provide funding for security advice and incident response for small businesses, commencing next year. I confess to taking a less sanguine view of this proposal; announcements of free government money to be distributed through individuals and small businesses tend to quickly attract a crowd of bottom feeders, as demonstrated by previous similar schemes. The result could be no improvement in the capabilities of the lowest hanging fruit, and even a drop in the maturity of those who previously were making significant efforts. Then again, anything is better than nothing. . .
Visentin, Lisa, ‘Stop hackers in their tracks’: Corporate giants muscle up against cyber threats, Sydney Morning Herald, 19 November 2023. Available online at https://www.smh.com.au/politics/federal/stop-hackers-in-their-tracks-corporate-giants-muscle-up-against-cyber-threats-20231117-p5ekva.html.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Researchers from AhnLab Security Emergency response Center (ASEC) report on a campaign which is targeting poorly-secured MySQL database servers via insertion of a malicious User Defined Function into vulnerable Windows systems.
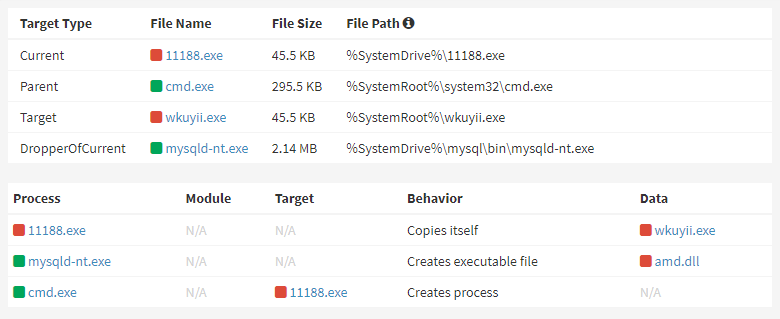
The Ddostf DDoS bot being installed via the MySQL service (Image credit: ASEC)
While the most popular database engine for Windows-based enterprise environments is Microsoft's SQL Server, MySQL is very popular among web developers (especially in packages such as EasyPHP) and small businesses, since it is essentially free and widely deployed on web sites. When initially installed MySQL (and its fork, MariaDB) do not password-protect the root admin account, and it is easy for a developer or inexperienced admin to overlook this step. Worse, the database server may be listening on port 3306 of a network interface, exposing it to remote attack.
The threat actor behind this campaign seems to be scanning for systems with port 3306 open, and then using brute-force or perhaps dictionary attacks to gain access (no admin password would really be an own goal). Unpatched systems may also be exposed through old vulnerabilities. Having gained initial access, the actor then uploads and installs a malicious MySQL User Defined Function (UDF) - a custom function written in C or C++ and compiled down to a dynamic link library (DLL) - perhaps by using a tool like Metasploit, which has a UDF attack payload.
This UDF has the ability to execute commands provided by the threat actor, capturing the output as a file which the actor can review, as well as to download files for subsequent execution. This way, the actor is able to upload and install a bot, christened Ddostf, and install it into the system. Ddostf has been observed in both Linux ELF and Windows PE executable formats; it is easily identifiably by the presence of the unobscured string, ddos.tf, in its binary.
When executed Ddostf first copies itself, under a random name, into the %SystemRoot% directory before registering itself as a Windows service. It then decrypts a string to obtain the URL of its C2 server and connects to it, enumerating and reporting basic information about the infected system. The C2 server responds with a mixture of a command and related data - for example, a command to download a payload, it will provide a URL argument.
While the bot responds to only six commands, it supports a variety of built-in DDoS attacks, including SYN flood, UDP flood, layer 7 HTTP GET and POST floods and others. Apart from commands to download payloads, start and stop DDoS attacks and start/stop transmitting system status information, the bot also has a command to switch to a new DDoS C2 server for a certain period of time, suggesting the developers may be using it to infects systems and then sell DDoS as a service.
The mitigation techniques here are obvious, but unlikely to be adopted by those most affected: after installing MySQL on a Windows machine, set a strong password on the MySQL root account and any PHP or other web server service accounts, and configure development installs to only listen on localhost. The ASEC report includes IoC's, which are also likely to be of limited use.
Sanseo, Ddostf DDoS Bot Malware Attacking MySQL Servers, blog post, 14 November 2023. Available online at https://asec.ahnlab.com/en/58878/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
 The threat posed by Rhysida ransomware has been steadily growing over recent months, leading the FBI, CISA and MS-ISAC (Multi-State Information Sharing and Analysis Center) to issue a cybersecurity advisory detailing the tactics and techniques used by its operators, as well as recommended mitigation techniques.
The threat posed by Rhysida ransomware has been steadily growing over recent months, leading the FBI, CISA and MS-ISAC (Multi-State Information Sharing and Analysis Center) to issue a cybersecurity advisory detailing the tactics and techniques used by its operators, as well as recommended mitigation techniques.
The threat actors behind Rhysida are known to target the education, healthcare, manufacturing, tech and government sectors, looking for low-hanging fruit. They also offer their tools and infrastructure in a Ransomeware-as-a-Service model in which they profit-share with those who lease them.
Whoever they are, they typically gain initial access via remote services such as VPN access points which they access using compromised valid credentials; they obtain these via phishing and other attacks from organisations which have not implemented multi-factor authentication. They have also been seen exploiting the Zerologin vulnerability in the Microsoft Netlogon Remote Protocol (which should have been patched back in August 2020 - as I say, low-hanging fruit).
Having established a beachhead on the internal network, the threat actors use living off the land techniques, employing the existing system software, such as PowerShell, the Windows ipconfig, whoami, nltest, and net user, net group and similar commands as well as RDP to pivot to other systems. However, they do install additional tools such as PuTTY, AnyDesk and PowerView, which they use to map the network.
The Rhysida ransomware itself encrypts each file under a 256-bit key using the ChaCha20 algorithm, with the symmetric key in turn protected by 4096-bit RSA and renaming the file to add a .rhysida extension. It simultaneously exfiltrates data, allowing the operators to engage in double extortion: pay the demanded Bitcoin ransom to obtain the decryption key and also prevent the threat actors publishing sensitive exfiltrated data.
Once encryption has been completed, a PowerShell command deletes the ransomware binary and drops a victim-specific PDF file entitled "CriticalBreachDetected", containing a unique code and instructions to contact the operator via a Tor network portal and make payment. The text of the note makes a useful IoC, since it is also embedded in the ransomware binary, allowing easy detection. (I should say, "was also embedded", since it is easily obscured, e.g. by an XOR algorithm, and the operators have almost certainly done this by now).
A long list of suggested mitigations start with the obvious: deploying phishing-resistant multi-factor authentication, removing user access to PowerShell and other command-line tools, restricting the use of RDP and other remote desktop services, application allowlisting, proactive patching, etc. It also advises validation of controls using pen-testing techniques aligned with the specific MITRE ATT&CK techniques identified. The advisory also lists IoC's, and they are downloadable in STIX XML and JSON formats.
CISA, #StopRansomware: Rhysida Ransomware, cybersecurity advisory, 15 November 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-319a.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
The Australian Signals Directorate has released its Cyber Threat Report for 2022-2023. While I haven't had a chance to read the 80-page report, there are a few standout points:
- The top3 cybercrimes reported by businesses are:
- Email compromise
- Business email compromise fraud
- Online banking fraud
- Self-reported losses due to BEC fraud totalled almost $A80 million, with an average loss of over $A39,000 per incident
- Ransomware comprised over 10 percent of all incidents, with the highest-reporting sectors, accounting for roughly one-third of reports being:
- Professional, scientific and technical services
- Retail
- Manufacturing
- The average self-reported cost of cybercrume to businesses increased by 14%:
- $46,000 for small business
- $97,200 for medium business
- $71,600 for large business
 State-sponsored actors focused on critical infrastructure, with their objectives being data theft and disruption of business. It is noticeable that cyber perations are increasingly the preferred vector for state actors to conduct espionage and foreign interference. ASD and international partners called out the Russian FSB for its use of the Snake malware for cyber-espionage, and also highlighted activity associated with a People’s Republic of
State-sponsored actors focused on critical infrastructure, with their objectives being data theft and disruption of business. It is noticeable that cyber perations are increasingly the preferred vector for state actors to conduct espionage and foreign interference. ASD and international partners called out the Russian FSB for its use of the Snake malware for cyber-espionage, and also highlighted activity associated with a People’s Republic of
China state-sponsored cyber actor that used ‘living-off-the-land’ techniques to compromise critical
infrastructure organisations.
The connection of operational technology and industrial control systems to the Internet via enterprise networks has provided increased opportunities for threat actors to attack them; ASD responded to 143 incidents related to critical infrastructure.
Proactive patching is increasingly important (today is Windows PatchDay - is your computer fully patched?) One in 5 critical vulnerabilities was exploited within 48 hours, despite patching or mitigation advice being available. Malicious cyber actors used these critical flaws to cause significant incidents and compromise networks, aided by inadequate patching.
Online scams and cybercrime continue to increase: individuals made almost 94,000 reports of cybercrime - an increase of 23% over the previous year. The top four cybercrimes reported by individuals are:
- Identity fraud
- Online banking fraud
- Online shopping fraud
- Investment fraud
The Australian Competition and Consumer Commission’s Targeting Scams report revealed Australians lost over $3 billion to scams in 2022. This is an 80 per cent increase on total losses recorded in 2021.
In short, we cybersecurity professionals are far from being out of a job.
Uncredited, ASD Cyber Threat Report 2022-2023, report, 14 November 2023. Available online at https://www.cyber.gov.au/about-us/reports-and-statistics/asd-cyber-threat-report-july-2022-june-2023.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
The Australian Cyber Security Centre, aided by the US's Cybersecurity and Infrastructure Security Agency, has released a guidance package aimed at ensuring continuity of operations for both email communications and critical business applications following a significant incident - the most obvious example being a ransomware attack, but physical disasters do happen, too.

The package, entitled Business Continuity in a Box, is aimed at small and medium businesses and provides step-by-step instructions on how to deploy the necessary services in the cloud. It consists of three guidance documents plus a supporting PowerShell Script:
- ACSC Business Continuity In a Box - Overview
- ACSC Business Continuity In a Box - Communications
- ACSC Business Continuity In a Box - Applications
- ACSC Business Continuity In a Box - Automation Tool
The Communications document provides a detailed, step-by-step, plan for provisioning a replacement email service using a Microsoft 365 Business Standard Tenant (one can't help wondering if the focus on Microsoft's cloud is the first fruit of Microsoft's recent much-touted $A5 billion investment in cybersecurity and AI in Australia).
In stage 1, the user reviews the pack and verifies that they have the prerequisites (a Windows 10 or 11 computer, a phone, an email account, relevant information about the organisation - particularly access to its DNS configuration - and a credit card).
In stage 2, the guide walks the user through provisioning the MS 365 tenant, while in stage 3, they update the organisation's DNS entries, following provider-specific guidance supplied at the time by Microsoft. Stage 4 uses a PowerShell script to apply configuration settings to the MS 365 tenant and the associated Exchange Online instance. while the final stage validates the environment.
The guide seems to be well thought-out, with good explanations at an appropriate level for an only moderately technical user who is working quickly, under pressure, possibly somewhat panicked.
Despite my idle musings above, the guide does make the point that this MS 365 account can operate on a 30-day free trial, so it's not very profitable for Microsoft (but neither will it cost them much, either). But I wouldn't be surprised if Google and other SaaS providers produced similar guides for their own services.
The Continuity of Applications guide is, of necessity, much less detailed - there being so many different types of applications. It covers three stages - 1: determining the critical applications (essentially a crude Business Impact Analysis, described in a few paragraphs), 2: Determining a continuity path (selecting SaaS, PaaS or IaaS), and 3: deploying an IaaS application environment, IaaS being the fastest way to deploy an existing application, although some basic applications could be deployed on SaaS using low-code/no-code tools such as Microsoft PowerApps or Google AppSheet (unfortunately, not covered here).
The discussion for stage 3 covers the various architectural principles and patterns as well as relevant issues, and is more agnostic than the Continuity of Communications document, providing examples for MS Azure, AWS and Google Cloud. However, in all cases, a lot more preparation work will be required of the user, if they are to respond quickly to a business continuity incident.
Overall, this is a useful set of preparatory documents for SME's. What's more, we know from experience that at least some of the techniques described really work. Take, for example, the experience of Norsk Hydro, which suffered a targeted ransomware attack (Beaumont, 2019 and Clueley, 2019,) but quickly got on the front foot by deploying an interim web site in Azure and providing status updates to customers via email (which was unaffected since they were already using MS 365).
ASD and ACSC (with CISA), Business Continuity in a Box, documentation web page, 10 November 2023. Available online at https://www.cyber.gov.au/smallbusiness/business-continuity-in-a-box.
Beaumont, Kevin, How Lockergoga took down Hydro — ransomware used in targeted attacks aimed at big business, DoublePulsar blog, 21 March 2019. Available online at https://doublepulsar.com/how-lockergoga-took-down-hydro-ransomware-used-in-targeted-attacks-aimed-at-big-business-c666551f5880.
Clueley, Graham, In its ransomware response, Norsk Hydro is an example for us all, blog article, 3 April 2019. Available online at https://www.grahamcluley.com/in-its-ransomware-response-norsk-hydro-is-an-example-for-us-all/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
It's only been a week since Australia's Department of Home Affairs released its first Critical Infrastructure Annual Risk Review - November being Critical Infrastructure Security Month. And only a couple of days later, top-tier telco Singtel Optus suffered a major day-long outage - this one apparently not cybersecurity-related, but with some important lessons for us, nonetheless.
 And just when everyone thought it couldn't get any worse, ports operator DP World Australia has been hit with a 'cybersecurity incident' (I would say breach, rather than incident, as their defences failed) - this one quite likely the early phases of a ransomware attack.
And just when everyone thought it couldn't get any worse, ports operator DP World Australia has been hit with a 'cybersecurity incident' (I would say breach, rather than incident, as their defences failed) - this one quite likely the early phases of a ransomware attack.
Turning first to Optus, the firm started to experience a major network failure starting around 4 am on Tuesday 7 November. There's been no official word so far, but the signs point to a failed BGP-4 configuration change which propagated throughout the firm's systems, since other network operators reported a spike in BGP-4 routing advertisements from the company, beginning around then. This brought down the company's cellular network, since voice calls in this 4G/5G/6G world are no longer switched analog signals, but Voice over IP.
You might be thinking, "Hang on - the whole point of the packet-switched IP protocol which runs the Internet, and the dynamic routing protocols which control its routing, is precisely to deal with this by detecting outages and routing around them!". And you'd be right, except for a couple of things:
First, the days when telephone exchanges were huge sandstone or concrete buildings which were manned 24 x 7 by technicians are long gone. These days, the 'central office' switching centre gear is much, much smaller, and is remotely managed - which is great as long as your network lets you connect to those switches and fix any configuration problems. But if your network routing is b0rked, then you've just sawn through the branch you were sitting on, and are rapidly hurtling towards terra firma.
The switches that failed first were located in two Melbourne suburbs, and so a technician apparently had to be despatched with a laptop and cable to connect to the AUX port of the switches. Meanwhile, a domino effect had set in, with routes being dropped all over the place. There are other potential complicating factors, too - think about physical access control: a great big chunky key will always work, but a badge reader will need network connectivity.
Over 12 hours later, the network was gradually coming up again, mollifying customers who had suffered significant losses. Coffee shops, hairdressers and retailers of all sizes were unable to take payments, since their credit card terminals rely on the cellular and in this post-COVID era hardly anyone carries cash. The result was a clamor for compensation - to which Optus was slow in responding, offering many customers an extra 200GB of free data (on top of an unlimited data plan, in many cases!).
There are clearly lessons here about resilience by means of redundancy, cost-cutting, the importance of planned responses to material incidents, breaches and outages, including crisis communications, and the value of dual-SIM smartphones with a spare pre-paid SIM.
Turning to DP World: the UAE-based logistics firm is the largest port operator in Australia, handling one third of the country's maritime freight through its ports in Sydney, Melbourne, Brisbane and Fremantle. On Friday 10 November, the company detected a breach and responded by disconnecting from the Internet and calling in cybersecurity specialists, including the Australian Cyber Security Centre, this being critical infrastructure.
As a result of this containment effort the firm had to close down its port operations, including its connections with landside transport and logistics companies. This could lead to supply-chain disruption and product shortages in the pre-Christmas retail peak - so we can expect more unhappy retailers.
DP World remains offline as of 7 am on Monday 13 November 2023, but hopes to back online within days.
'They' say that bad things always come in threes, so I'm waiting with bated breath. . .
McKenzie, Parker, What caused the Optus outage and how it exposed Australia’s communications framework, The New Daily, 8 November 2023. Available online at https://www.thenewdaily.com.au/finance/consumer/2023/11/08/optus-outage-cause-resiliency.
AAP, Cyber attack shuts down major port operator, The New Daily, 11 November 2023. Available online at https://www.thenewdaily.com.au/news/2023/11/12/dp-world-cyberattack.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
 Online magazine Tom's Hardware is reporting a claimed breakthrough in quantum computing which can break RSA-2048 - that is, given an RSA public key with a 2048-bit modulus, it can derive the private key in polynomial time. Even better, it can do this without requiring a huge, expensive super-cooled quantum circuit - instead, it works on a smartphone or Linux desktop.
Online magazine Tom's Hardware is reporting a claimed breakthrough in quantum computing which can break RSA-2048 - that is, given an RSA public key with a 2048-bit modulus, it can derive the private key in polynomial time. Even better, it can do this without requiring a huge, expensive super-cooled quantum circuit - instead, it works on a smartphone or Linux desktop.
The claim is made in the abstract of a preprint posted to open-source publishing site, ResearchGate, by Ed and Ann Gerck, of Planalto Research.
Now, until last year, I was a university lecturer in Applied Cryptography, and I taught some aspects of quantum crptology - both the use of quantum key distribution (QKD) and quantum cryptanalysis. In particular, I taught the basics of quantum computing and the operation of Shor's Algorithm for factoring large composites (which is the way to break RSA crypto), including how the quantum computer is used to derive the periodicity of a function.
I've read the abstract in question, and it doesn't make much sense to me. A few points to bear in mind:
- I cannot conceive of any way to run a quantum algorithm on a smartphone. Quantum computing just doesn't work that way.
- A breakthrough of this magnitude would not be published on an open-source site - if I had come up with it, I'd submit it for one of the major cryptology conferences like IACR, CRYPTO or EuroCRYPT. What's more, if it passed muster, I'd get star billing.
- Peer review, while important for academic publishing, could easily be dispensed with in a case like this: the claim can be verified by returning the private keys in response to a few public keys given as a challenge. For bonus points, show it actually running on a smartphone.
- The abstract also reveals that "that we are working on a post-quantum, HIPAA compliant, end-to-end, patent-free, export-free, secure online solution, to replace RSA as soon as possible". This work is apparently based on an earlier proprietary crypto algorithm called ZSentry. Frankly, nobody cares whether crypto is HIPAA-compliant; the question is whether it is FIPS accredited. This is just hand-waving, with added buzzwords for the technically unsophisticated, and one can only wonder whether the claim to have broken RSA is an attempt to stimulate demand for post-quantum crypto - which can in any case be met by several other solidly-based algorithms already on the standards track.
I've been banging the drum pretty consistently for many years on the need for cryptographic agility - preparedness to replace existing public-key algorithms before it is too late. But I'd be very surprised if this was the expected quantum apocalypse.
As I've long told my students, in the world of cryptology, there's not a great distance between secret sauce and snake oil. And, as UTS researcher Chris Ferrie points out, the world of quantum physics has spawned a lot of BS.
Tyson, Mark, Scientist Claims Quantum RSA-2048 Encryption Cracking Breakthrough, Tom's Hardware, 4 November 2023. Available online at https://www.tomshardware.com/software/security-software/quantum-rsa-2048-encryption-cracking-breakthrough-claim-met-with-scepticism.
Gerck, Ed and Ann Gerck, QC Algorithms: Faster Calculation of Prime Numbers, preprint, August 2023. Available online at https://www.researchgate.net/publication/373516233_QC_Algorithms_Faster_Calculation_of_Prime_Numbers.
Ferrie, Chris, Quantum Bullshit: How to Ruin Your Life with Advice from Quantum Physics, Sourcebooks, 2023. Available in Kindle format via Amazon at https://www.amazon.com/Quantum-Bullsh-Ruin-Advice-Physics-ebook/dp/B0BQCGRT4V/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
The Australian Department of Home Affairs and the Cyber and Infrastructure Security Centre has released the first Critical Infrastructure Annual Risk Review, to mark Critical Infrastructure Security Month.
 The review found that foreign interference and espionage are principal threats to Australia's infrastructure, with foreign actors seeking everything from critical research and intelligence to details on production and service levels.
The review found that foreign interference and espionage are principal threats to Australia's infrastructure, with foreign actors seeking everything from critical research and intelligence to details on production and service levels.
However, the review also pointed out that trusted insiders pose a significant threat to the critical infrastructure sector, since they can deliberately - or accidentally - disclose sensitive information to third parties, manipulate systems and networks to cause damage, or be recruited by foreign intelligence services. Dark web job ads targeting disgruntled employees are used as a recruitment tool, and are also used as a vector for delivery of malware via trojaned application forms.
The report also pointed to the effectiveness of cyber attacks such as the 2021 Colonial Pipeline incident, which started as a ransomware attack on corporate systems but led to a decision to shut down operational technology systems in order to mitigate cross-system compromise.
The 31-page report has short chapters on critical infrastructure risk and regulation, sector interdependencies, cyber/infosecurity, supply chain threats, physical threats, natural hazards and personnel risks. It concludes with a short section which looks to the future.
Industry Partnerships Branch, Department of Home Affairs, Critical Infrastructure Annual Risk Review, November 2023. Available online at https://www.cisc.gov.au/resources-contact-information-subsite/Documents/critical-infrastructure-annual-risk-review-first-edition-2023.pdf.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.