Les Bell
Blog entry by Les Bell
Researchers from AhnLab Security Emergency response Center (ASEC) report on a campaign which is targeting poorly-secured MySQL database servers via insertion of a malicious User Defined Function into vulnerable Windows systems.
The Ddostf DDoS bot being installed via the MySQL service (Image credit: ASEC)
While the most popular database engine for Windows-based enterprise environments is Microsoft's SQL Server, MySQL is very popular among web developers (especially in packages such as EasyPHP) and small businesses, since it is essentially free and widely deployed on web sites. When initially installed MySQL (and its fork, MariaDB) do not password-protect the root admin account, and it is easy for a developer or inexperienced admin to overlook this step. Worse, the database server may be listening on port 3306 of a network interface, exposing it to remote attack.
The threat actor behind this campaign seems to be scanning for systems with port 3306 open, and then using brute-force or perhaps dictionary attacks to gain access (no admin password would really be an own goal). Unpatched systems may also be exposed through old vulnerabilities. Having gained initial access, the actor then uploads and installs a malicious MySQL User Defined Function (UDF) - a custom function written in C or C++ and compiled down to a dynamic link library (DLL) - perhaps by using a tool like Metasploit, which has a UDF attack payload.
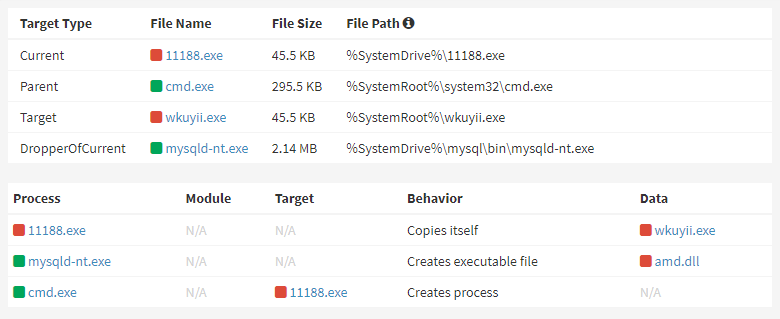
This UDF has the ability to execute commands provided by the threat actor, capturing the output as a file which the actor can review, as well as to download files for subsequent execution. This way, the actor is able to upload and install a bot, christened Ddostf, and install it into the system. Ddostf has been observed in both Linux ELF and Windows PE executable formats; it is easily identifiably by the presence of the unobscured string, ddos.tf, in its binary.
When executed Ddostf first copies itself, under a random name, into the %SystemRoot% directory before registering itself as a Windows service. It then decrypts a string to obtain the URL of its C2 server and connects to it, enumerating and reporting basic information about the infected system. The C2 server responds with a mixture of a command and related data - for example, a command to download a payload, it will provide a URL argument.
While the bot responds to only six commands, it supports a variety of built-in DDoS attacks, including SYN flood, UDP flood, layer 7 HTTP GET and POST floods and others. Apart from commands to download payloads, start and stop DDoS attacks and start/stop transmitting system status information, the bot also has a command to switch to a new DDoS C2 server for a certain period of time, suggesting the developers may be using it to infects systems and then sell DDoS as a service.
The mitigation techniques here are obvious, but unlikely to be adopted by those most affected: after installing MySQL on a Windows machine, set a strong password on the MySQL root account and any PHP or other web server service accounts, and configure development installs to only listen on localhost. The ASEC report includes IoC's, which are also likely to be of limited use.
Sanseo, Ddostf DDoS Bot Malware Attacking MySQL Servers, blog post, 14 November 2023. Available online at https://asec.ahnlab.com/en/58878/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.