Les Bell
Blog entry by Les Bell
Ten years after its introduction, the US National Institute of Standards and Technology (NIST) has updated its ubiquitous Cybersecurity Framework (CSF).

The old version 1.1 was widely adopted, primarily because unlike many national and international standards, it is free. However, it was initially developed for use within US government agencies, for whom NIST is legally the official standards regulatory body, and then extended to cover critical infrastructure. It required some adaptation when used by private-sector and non-US organizations, but that did not stop it becoming one of the most popular frameworks. In fact, the older versions were translated into 13 languages.
Framework - Not a Standard
It's important to understand that the CSF is a framework, not a standard. Frameworks sit above standards, and provide a higher-level view of the requirements mandated by a range of standards. In essence, a framework is a conceptual model, and can be useful in clarifying one's thinking about the entire range of cybersecurity activities.
Of course, most of those requirements are security controls - and in that sense, the CSF is a controls catalogue. However, it actually cross-references the controls and control objectives from a range of different standards.
Another key convenience of the CSF is that it makes compliance efforts and gap analysis significantly easier. An organisation which has already implemented, or perhaps achieved certification against, a particular standard can use the CSF to check off requirements which it already meets from other standards. This makes it much easier to identify the work required to comply with additional standards.
Organization
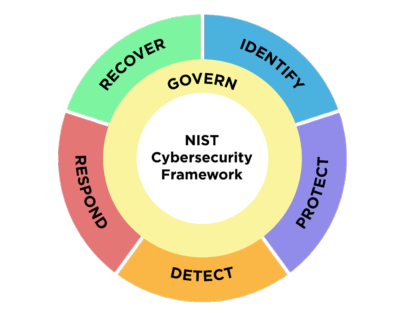
The original standard was organized around five key functions:
- Identify (assets, threats, vulnerabilities, etc.)
- Protect (assets, via authentication, authorization and other controls
- Detect (compromises and attacks)
- Respond (incident response)
- Recover (restore assets and operations)
To these has been added a new function, Govern, which encompasses the establishment, communication and monitoring of the organization's overall risk management strategy, policies and expectations. This is a large function, as it integrates with all the other functions.
Under the functions, as before we find categories and subcategories, along with the informative references which point to the relevant standards. However, the mapping spreadsheet now adds a column containing implementation examples, which help to clarify what the subcategory really means and how to comply.
Version 2.0 has been extensively reworked, with extensive community feedback on the draft, to meet the needs of a much wider set of communities, including the private sector and community organizations such as schools.
It has also been expanded - while the older versions really consisted of a single volume plus a huge spreadsheet mapping the framework to standards, it now adds an array of supporting resources. These include quick-start guides for small business and for the creation of organizational profiles, as well as guidance for the creation of community profiles. A second worksheet provides even more detail.
Also new is a searchable catalogue of informative references, as well as a Cybersecurity and Privacy Reference Tool (CPRT) which contains a browsable set of the NIST guidance documents. Finally, a CSF 2.0 Reference TOol allows exploration and searching of the entire CSF in both human-readable and machine readable (JSON) formats.
I would expect that many organizations will rapidly migrate to version 2.0 of the CSF. The framework can be found at https://www.nist.gov/cyberframework.
Uncredited, NIST Releases Version 2.0 of Landmark Cybersecurity Framework, news release, 26 February 2024. Available online at https://www.nist.gov/news-events/news/2024/02/nist-releases-version-20-landmark-cybersecurity-framework.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Melbourne, 18 - 22 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.