Les Bell
Blog entry by Les Bell
During the last day of our CISSP course, when we cover Security Operations, I make reference to a 2013 tweet by Mudge, one of the founders of L0pht Consulting, authors of the popular l0phtcrack dictionary attack program. In it, Mudge states that:
DoD data (cleared for release) shows on average 1/3 of vulns in government systems is in the security software.
And he provides a supporting graph:
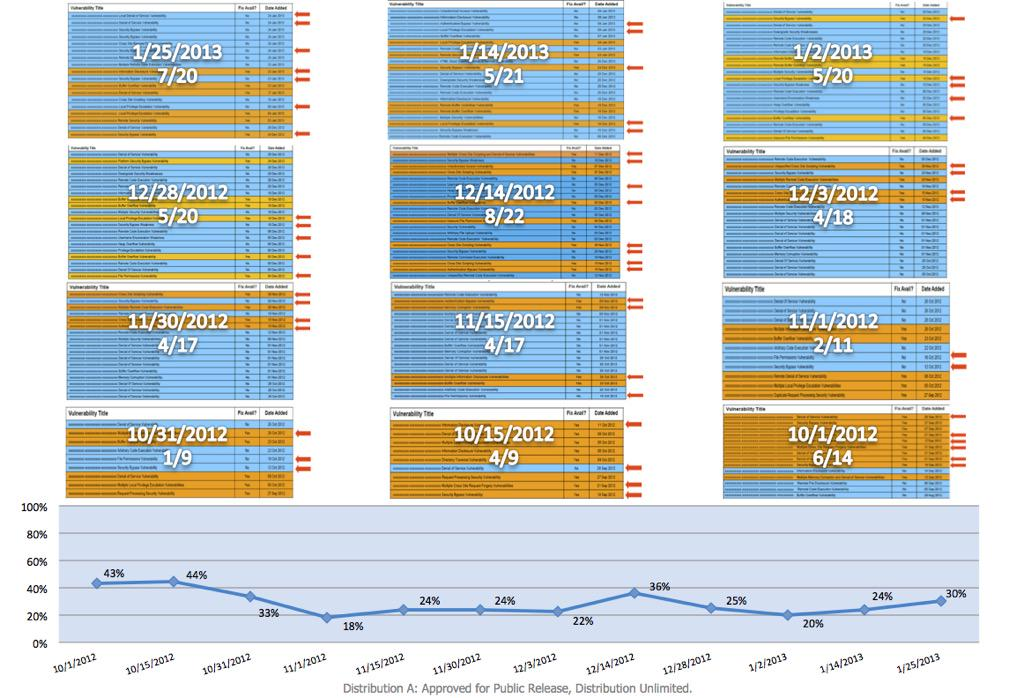
This reinforces a point introduced earlier in the Security Engineering domain of the course, when we discuss the design of evaluated products, particularly trusted systems: the way to achieve a secure design is to remove unnecessary functionality and eliminate unneeded code, simplifying the design and reducing the attack surface. Conversely, attempting to improve security by adding more and more software actually makes things worse.
This led me to coin one of many mantras which I drop into discussions about security.
The enemy of security is complexity.
This is, sadly, as true as ever. In fact, the situation has only got worse.
Back in February 2024, I blogged about the problem of developers relying more and more heavily on external dependencies. Many libraries and subsystems are sourced from repositories such as GitHub, making them vulnerable to a range of supply-chain attacks, such as the insertion of back-doored versions using near-identical names. And this is, of course, in addition to the possibility of vulnerabilities in the original code.
In the IEEE Spectrum article (Hubert, 2024) which had set me pondering this, the author cited the example of a relatively simple photo-sharing application which had 1,600 dependencies on external libraries. Now, consider how likely it is that none of those 1,600 dependencies has any vulnerabilities. I'd say your chances are close to zero.
The solution is to improve programmer education and reduce reliance on external dependencies. Hubert demonstrates this by developing a lean image-sharing program that consists of just 1,600 lines of source code plus five important dependencies - a much more secure approach.
Now, this is all well and good, but some software has to provide a wide range of functionality - and this applies particularly to security-related software. Hubert points to a vulnerability in the Barracuda Email Security Gateway - specifically in the way a third-party Perl module would unpack Excel spreadsheets to scan them for malware - allowing arbitrary code execution as it did so.
Since then, the problem has only been exacerbated by our success in improving security education, training and awareness among enterprise employees. This has paid off by reducing the effectiveness of phishing attacks, leading threat actors to rely more heavily on exploitation of software vulnerabilities in network management and security software, as these are reachable over the Internet and often assumed to be secure. If an attacker can compromise the perimeter defences, they can then pivot to move further into the victim's networks.
We saw the first indications of this five years ago - remember the huge impact of the attack on SolarWinds Orion network management software? Russian threat actors managed to compromise SolarWinds' software build system, and insert a backdoor into the software, leading to breaches at roughly 100 companies and government agencies, including the US Treasury Department and the National Telecommunications and Information Administration.
After the initial incident response, the company called a halt to new feature development and refocused 400 developers on improving software quality, including security. (The SolarWinds CISO, Tim Brown, who claims he lost 25 pounds (just over 11 kg) in 20 days during the incident response, doubtless wished they had done this before the breach.)
In their 2025 analysis of 0-day exploits (Charrier, 2025), Google Threat Intelligence Group reported that:
Zero-day vulnerabilities in security software and appliances were a high-value target in 2024. We identified 20 security and networking vulnerabilities, which was over 60% of all zero-day exploitation of enterprise technologies.
And so it continued, with subsequent attacks on Ivanti, Citrix NetScaler, Cisco, Juniper, Fortinet, Palo Alto Networks and SonicWall.
We need the companies who sell us network management and security products to get serious about security by design, educating their developers on secure coding techniques and reducing reliance on external dependencies. We also need to focus even more heavily on defense-in-depth approaches to network defence, making use of network segmentation and explicitly defined trust boundaries.
What's more, we need to apply the same principles in our own systems and software development. At the risk of using an old cliché: keep it simple, stupid. Write the code yourself when you can, rather than googling for an external library (or, worse, relying on AI suggestions or even vibe coding). Never forget: the enemy of security is complexity. Keep it out, wherever possible.
References and Further Reading
Charrier, Caset, et. al., Hello 0-Days, My Old Friend: A 2024 Zero-Day Exploitation Analysis, Google Threat Intelligence Group blog, 29 April 2025. Available online at https://cloud.google.com/blog/topics/threat-intelligence/2024-zero-day-trends.
Hubert, Bert, Why Bloat Is Still Software’s Biggest Vulnerability: A 2024 plea for lean software, IEEE Spectrum, 8 February 2024. Available online at https://spectrum.ieee.org/lean-software-development.
Mudge, DoD data (cleared for release) . . ., tweet, 2013. Available online at https://twitter.com/dotMudge/status/642758829697056768/photo/1.
Taylor, Josh, ‘I lost 25 pounds in 20 days’: what it’s like to be on the frontline of a global cyber-attack, The Guardian, 19 October 2025. Available online at https://www.theguardian.com/technology/2025/oct/19/global-cyber-attack-russian-hack-solarwinds-stress-health.
Upcoming Courses
There is still just time to register for one of the remaining CISSP courses this year:
Sydney
Online Virtual
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.