Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Zero-Day RCE Vulnerability Impacts Windows, Office
Microsoft has today warned of an unpatched remote code execution vulnerability in multiple Windows and Office versions. The vulnerability, CVE-2023-36884, which has a CVSS base score of 8.3, is reportedly being actively exploited in the wild, using specially-crafted Microsoft Office documents.
While the Redmondites work up a patch, potential victims can mitigate possible infections by setting the following registry key:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATIONThe active exploitation was first uncovered by the Blackberry Threat Research and Intelligence team, who found two malicious documents submitted from an IP address in Hungary, sent as lures to an organization supporting Ukraine abroad, and a document targeting guests at the Vilnius NATO Summit who may also be providing support to Ukraine. Their analysis led them to attribute this operation to the RomCom group, also known as Tropical Scorpius, Storm-0978, UNC2596 and Void Rabisu, which has a history of attacks against Ukrainian politicians and their Western contacts.
The lures detected by Blackberry were Word documents delivered via a spear-phishing campaign, and when opened used CVE-2023-36884 to download an OLE object and connect to a C2 server in a typosquatting domain - a classic RomCom technique. In this case, they registered the domain ukrainianworldcongress[.]info, which is sufficiently close to the genuine ukrainianworldcongress[.]org that it will escape notice by most users.
The Blackberry blog post provides a detailed run-down of what their researchers observed, while Microsoft Threat Intelligence has also blogged on this, providing additional background information on RomCom campaigns. Finally, the MSRC vulnerability page provides a brief description and mitigation advice.
Blackberry Research & Intelligence Team, RomCom Threat Actor Suspected of Targeting Ukraine's NATO Membership Talks at the NATO Summit, blog post, 8 July 2023. Available online at https://blogs.blackberry.com/en/2023/07/romcom-targets-ukraine-nato-membership-talks-at-nato-summit.
Microsoft Threat Intelligence, Storm-0978 attacks reveal financial and espionage motives, blog post, 11 July 2023. Available online at https://www.microsoft.com/en-us/security/blog/2023/07/11/storm-0978-attacks-reveal-financial-and-espionage-motives/.
Microsoft Security Resource Center, Office and Windows HTML Remote Code Execution Vulnerability (CVE-2023-36884), vulnerability info, 11 July 2023. Available online at https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36884.
New Ransomware: Big Head
Back in June, Fortinet picked up on a new ransomware variant called Big Head, which was likely being distributed as a fake Windows Update; samples were subsequently submitted from the US, Spain, Frane and Turkey. Now researchers at Trend Micro have done a deep dive on the operation of this ransomware, uncovering a significant number of Big Head variants, and providing a detailed analysis of three of them.
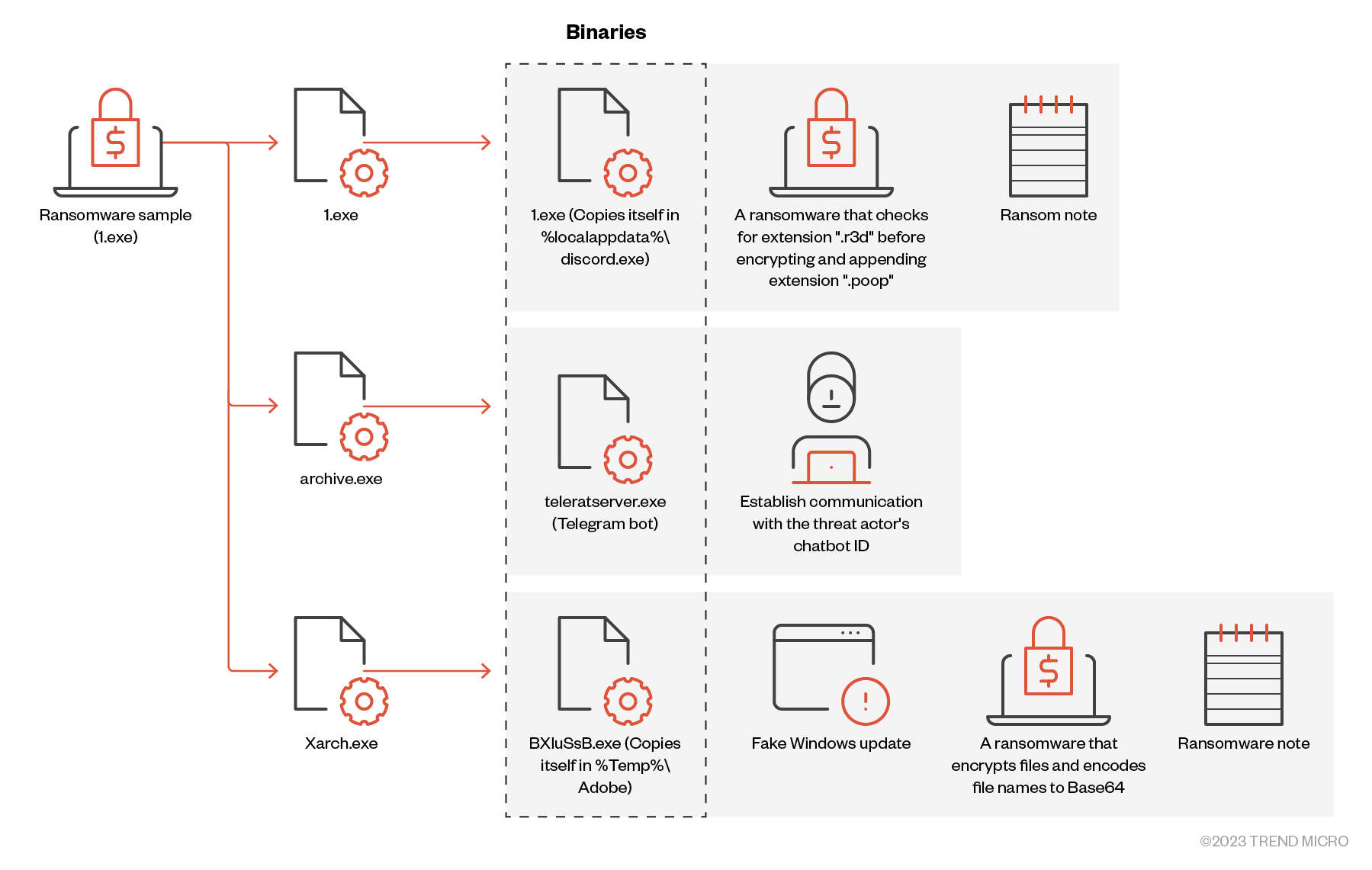
The infection chain of Big Head ransomware sample 1 (image credit: Trend Micro)
The three samples seem to have been distributed via malvertisements as fake Windows updates and fake Word installers; each sample carries three encrypted executables as resources which it decrypts, drops and then runs. In the case of the first sample, each .exe performs a different function: the first randomly generates an ID for this victim, encrypts some files, deletes volume shadow copies and drops the ransom note; the second establishes a C2 channel; the third displays a fake Windows Update window to distract the user while performing the bulk of file encryption before deleting itself.
The second sample carries different executables and while it also performs file encryption for ransom, it also carries a copy of the WorldWind infostealer. The third sample similarly acts as ransomware, but also carries a copy of the Neshta virus - perhaps to act as a distraction for analysts.
Each variant targets specific filetypes and also specific locales; it also takes care to self-terminate if running in CIS locales. Interestingly, the Trend researchers were able to track the malware developers, through their Telegram account, to their YouTube channel where they have uploaded videos demonstrating the malware. The channel name is the Bahasa phrase "aplikasi premium cuma cuma" ("premium application for free") suggesting a SE Asian origin.
At this point, there are no reports of attacks or successful infections with this malware, but it is clear that it is under active development and we can expect further variants in the months to come, making this a useful heads-up to analysts and defenders everywhere.
Gonzalez, Ieriz Nicolle, Katherine Casona and Sarah Pearl Camiling, Tailing Big Head Ransomware’s Variants, Tactics, and Impact, research report, 7 July 2023. Available online at https://www.trendmicro.com/en_us/research/23/g/tailing-big-head-ransomware-variants-tactics-and-impact.html.
More Firefox Updates
It seems like only last week that we reported on the Mozilla Foundation's release of Firefox 115 (it was). And yet here we are, preparing to restart the browser for the installation of Firefox 115.0.2, because of a newly-discovered CVE-2023-3600, a use-after-free vulnerability. You know what to do.
Uncredited, Security Vulnerabilities fixed in Firefox 115.0.2 and Firefox ESR 115.0.2, security advisory, 11 July 2023. Available online at https://www.mozilla.org/en-US/security/advisories/mfsa2023-26/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Largest NHS Trust Hit By Ransomware
The largest of the UK's National Health Service's trusts, Barts Health NHS Trust, which runs five London hospitals serving over 2.5 million patients, has been hit by a ransomware attack, according to TechCrunch. The Trust is the latest victim to appear on the dark web leak site of ALPHV, also known as BlackCat, with a claimed 70 TB of sensitive data stolen, including employee identification documents such as passports and driver licences, as well as internal emails labeled "confidential".
ALPHV has given the Trust three days to contact them in order to prevent publication of data, "most of it citizens [sic] confidential documents".
This is the second breach of NHS data in recent weeks - the first being the compromise of a dataset containing information on 1.1 million patients across 200 hospitals, which was being used at the University of Manchester for research purposes.
Page, Carly, UK battles hacking wave as ransomware gang claims ‘biggest ever’ NHS breach, TechCrunch, 10 July 2023. Available online at https://techcrunch.com/2023/07/10/uk-hacks-public-sector-nhs-ransomware/.
Exploit Code Available for VMware Aria Operations RCE Vuln
A critical vulnerability in the VMware Aria Operations for Logs analysis tool just became a lot more critical, with the company revealing that exploit code has been published, making exploitation much more likely. The vulnerability - CVE-2023-20864 - is a deserialization vulnerability which could allow an unauthenticated actor with network access to execute arbitrary code with root privileges, meriting a CVSS score of 9.8 (Critical).
VMware released a fix for this vulnerability back in April, so customers who have not yet applied the patch should do so urgently. The vulnerability is not present in Aria Operations for Logs version 8.12.
Uncredited, VMware Aria Operations for Logs (Operations for Logs) update addresses multiple vulnerabilities. (CVE-2023-20864, CVE-2023-20865), security advisory, updated 10 July 2023. Available online at https://www.vmware.com/security/advisories/VMSA-2023-0007.html.
New Infostealer Targets Macs
Yesterday we reported on how Iranian APT, Charming Kitten, quickly put together an infection chain in order to get a backdoor installed on the Macintosh of a specific cyber-espionage target. Now comes a report from Israeli security firm Guardz of a new infostealer which also targets MacOS devices.
The stealer, which they have dubbed 'ShadowVault', is being offered in the XSS dark web forum for a fee of $US500 per month. It offers extensive capabilities, including extraction of passwords, cookies, credit cards, wallets and extensions from Chromium-based and Firefox browsers, keychain database extraction, exfiltration of files, decryption of crypto wallets from all browsers, and more. For an additional fee, it can be signed with an Apple development key.
There's a moral here: while Windows systems remain the largest target for infostealers, cybercriminals and cyber-espionage groups are showing increasing interest in Macs, and Apple's customers cannot affort to be complacent about their security.
Goldman, Lauri, Guardz Uncovers A New Threat Targeting macOS – ‘ShadowVault’, blog post, 10 July 2023. Available online at https://guardz.com/blog/guardz-uncovers-a-new-threat-targeting-macos-shadowvault/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Charming Kitten's Long Infection Chain Reaches Macs
The Iranian APT variously known as Charming Kitten, APT42, TA453, Mint Sandstorm and Yellow Garuda has been running a campaign targeting experts in nuclear security and Middle Eastern affairs, according to researchers at Proofpoint. The group, which is affiliated with Iran's Islamic Revolutionary Guard Corps, is using a spear-phishing campaign to deliver highly customised lure emails, the first of which is innocuous but quickly followed by an email containing a malicious link to a Google Script macro which, in turn, launches a long infection chain.
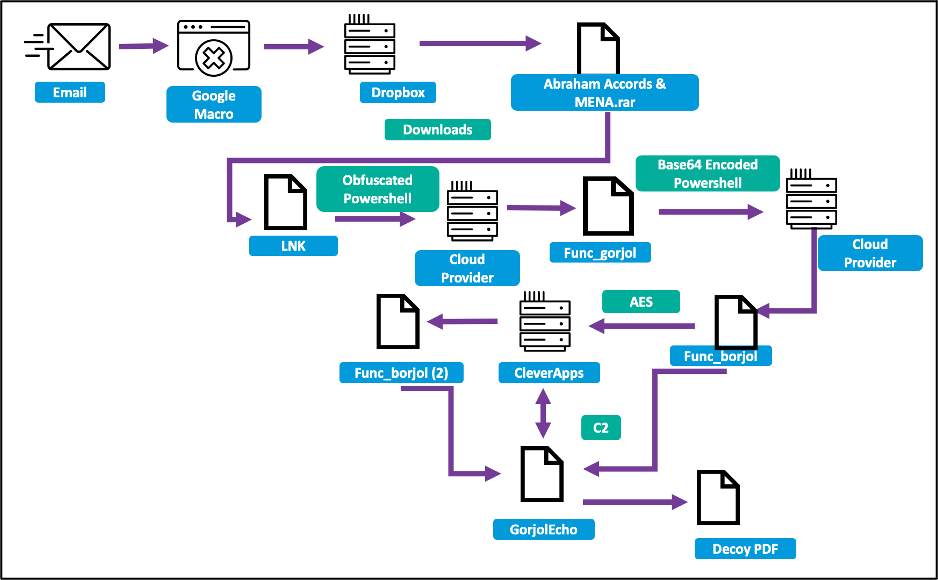
The long infection chain uses PowerShell scripts to download its various stages (image credit: Proofpoint)
A password-protected RAR file contains a dropper in the form of a .lnk file which in turn uses PowerShell to download additional stages from a cloud hosting provider - at first using base64 encoding but then switching to AES encryption, culiminating in the assembly of the final PowerShell backdoor, which the researchers dubbed GorjolEcho.
This achieves persistence by putting a copy of the initial loader stages in a StartUp entry, and then displays a decoy PDF that matches the recipient's expectations. It then commences the exfiltration of encrypted data over HTTPS to its C2 server, which is hosted in a legitimate cloud service - interestingly, HTTP error responses will cause generation of an error message in Korean, presumably as an attempted diversion. The GorjolEcho backdoor can also download and run additional modules, likely for cyber-espionage purposes.
However, the use of a .lnk file and PowerShell means this attack won't work on Mac computers, which are common in academic circles. Realizing that a targeted individual had not fallen foul of the attack, the threat actor followed up a week later with a new Mac-specific infection chain. This time, to induce the target to run an executable, their email claimed to include a VPN client; use of this would be necessary for security reasons. In fact, this was a script which used the curl command to download another shell script, dubbed NokNok, a backdoor which loops indefinitely, sending an HTTP POST to its C2 server and either executing other bash shell modules in response to the commands it receives or exiting.
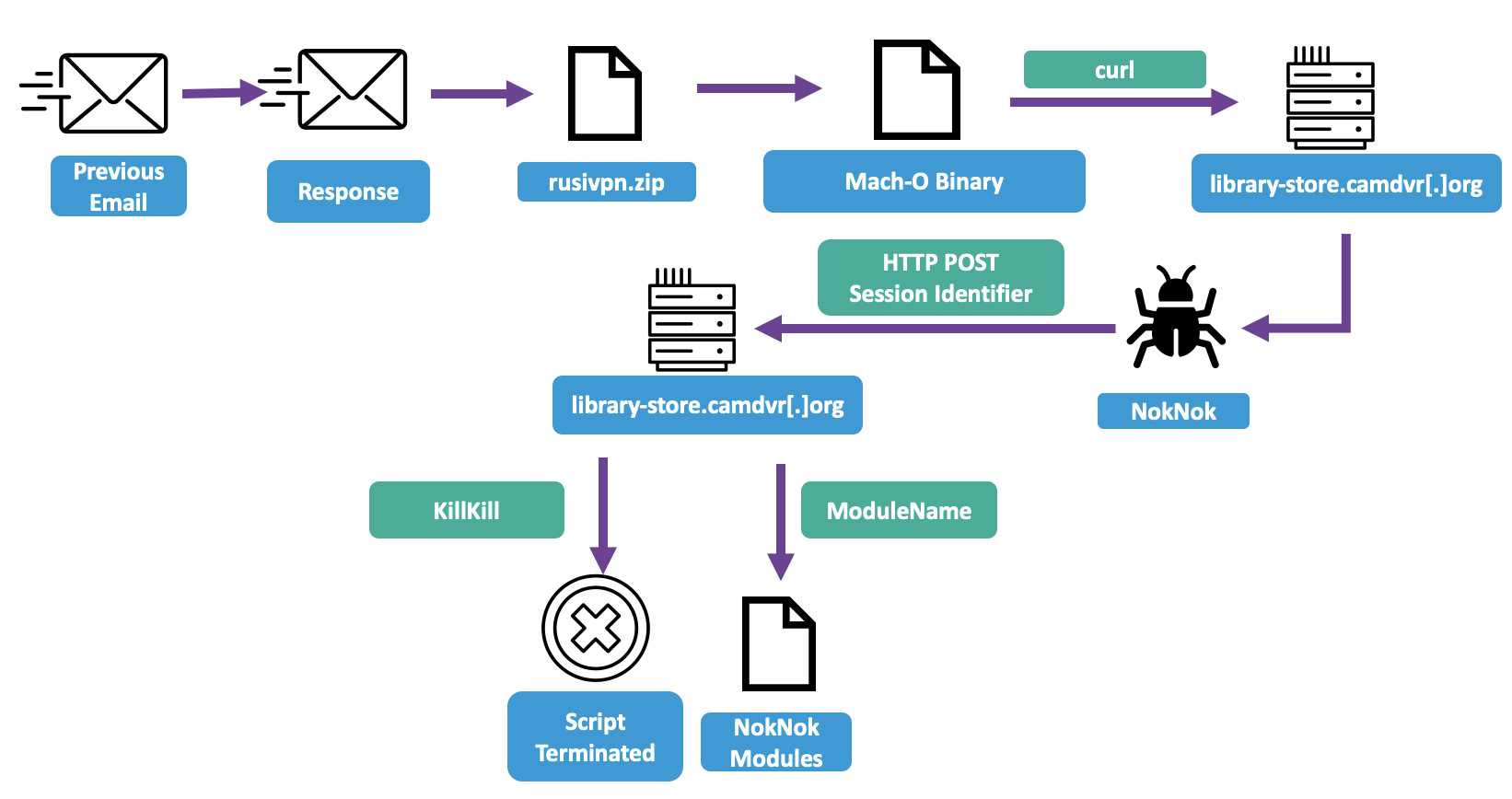
The NokNok backdoor delivery process (Image credit: Proofpoint)
The NokNok modules share common routines for encryption and base64 chunking in order to exfiltrate their results, which they generally obtain by using system commands - such as ps -ax to list running processes. There are probably additional modules for both GorjolEcho and NokNok.
While these infection chains represent a change from previous intrusions by Charming Kitten, there are sufficient similarities in both the coding techniques and overall TTP's employed for Proofpoint to attribute this campaign to the threat actor with high confidence. The efforts put in to develop new techniques, particularly using multiple legitimate cloud services as well as posting malware to new platforms, indicates a high degree of persistence.
Miller, Joshua, Pim Trouerbach, et. al., Welcome to New York: Exploring TA453's Foray into LNKs and Mac Malware, blog post, 6 July 2023. Available online at https://www.proofpoint.com/us/blog/threat-insight/welcome-new-york-exploring-ta453s-foray-lnks-and-mac-malware.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Android Spyware Plunders Phones, Sends Data to China
Security vendor Pradeo has detected two malicious Android apps which pose as file managers and could have aggregated 1.5 million installs from the Google Play Store. However, the apps are actually spyware which, despite claims to the contrary, exfiltrate a massive amount of data from the victims' phones.
The two apps are:
- File Recovery and Data Recovery - com.spot.music.filedate - over 1 million installs
- File Manager - com.file.box.master.gkd - over 500 thousand installs
On their Play Store Pages, the apps claim that no user data is collected (and that if it was, it would be encrypted in transit but cannot be deleted - a breach of many privacy laws, including the EU GDPR). However, according to Pradeo's analysis using their behavioural analysis engine, the data that is stolen and sent to servers in China includes:
- Users’ contact lists from the device itself and from all connected accounts such as email and social networks
- Media compiled in the application: Pictures, audio and video contents
- Real time user location
- Mobile country code
- Network provider name
- Network code of the SIM provider
- Operating system version number
- Device brand and model
That's quite a shopping list! Much of that information could be used to profile users and identify targets for a variety of purposes such as cyber-espionage or cybercrime, while the OS version and device information could be used in selecting an appropriate exploit.
The claimed installation numbers could have been faked in order to make the apps appear legitimate and rank higher in searches - in particular, an absence of reviews backs this interpretation. The apps are also somewhat stealthy - they hide their icons from the home screen, making them difficult to locate and uninstall - and they also force a reboot of the device, which then allows them to run automatically, and invisibly, in the background. It's entirely possible that some users may have forgotten they even installed these programs.
All this illustrates the dangers of mindlessly collecting lots of apps on a phone; users need to be careful to assess the legitimacy of apps before installing them, by reading reviews and looking for red flags, and in particular, reviewing the requested permissions before allowing installation to proceed. A 'flashlight' app that is a 40 MB download and requests access to everything on the phone is clearly not legitimate - and neither is a file manager that requests permission to access the phone book, user location information, etc.
Suau, Roxane, Two spyware tied with China found hiding on the Google Play Store, blog post, 6 July 2023. Available online at https://blog.pradeo.com/spyware-tied-china-found-google-play-store.
CISA Advisory on New Truebot Variants
The US Cybersecurity & Infrastructure Security Agency, along with its partners, has released an advisory on new variants of the Truebot loader. Traditionally, Truebot's operators - generally Russian cybercrime groups - have used phishing campaigns with malicious redirect hyperlinks to infect victims with the malware, which is then used to download the Clop ransomware.
However, the newer variants are now also obtaining initial access by exploiting CVE-2022-31199, a known vulnerability in the Netwrix Auditor - an application used for auditing both on-premises and cloud systems. In this campaign, after gaining a foothold, Truebot renames itself and then loads a remote access trojan called FlawedGrace. From there, FlawedGrace is used both for privilege escalation and to install payloads which allow the attackers to persist.
In fact, the entire campaign is quite complex, involving a variety of tools, such as Raspberry Robin malware, FlawedGrace, a custom data exfiltration tool which Cisco Talos call Teleport, and Cobalt Strike beacons. The 26-page CISA advisory provides a mapping to MITRE ATT&CK tactics and techniques, a comprehensive list of IOC's, guidance for incident response and suggested mitigations
CISA, Increased Truebot Activity Infects U.S. and Canada Based Networks, cybersecurity advisory, 6 July 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-187a.
Mozilla Releases Security Advisories
The Mozilla Foundation has released a number of advisories to address vulnerabilities in Thunderbird, Firefox and Firefox ESR. The obvious first defence for most users is to let their currently-installed versions download and install the next versions (Thunderbird 102.13, Firefox 115 and Firefox ESR 102.13).
Uncredited, Mozilla Foundation Security Advisory 2023-24 - Security Vulnerabilities fixed in Thunderbird 102.13, 4 July 2023. Available online at https://www.mozilla.org/en-US/security/advisories/mfsa2023-24/.
Uncredited, Mozilla Foundation Security Advisory 2023-23 - Security Vulnerabilities fixed in Firefox ESR 102.13, 4 July 2023. Available online at https://www.mozilla.org/en-US/security/advisories/mfsa2023-23/.
Uncredited, Mozilla Foundation Security Advisory 2023-22 - Security Vulnerabilities fixed in Firefox 115, 4 July 2023. Avilable online at https://www.mozilla.org/en-US/security/advisories/mfsa2023-22/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Node.js Supply Chain Threatened by Manifest Confusion Vulnerability
The shift away from desktop applications to cloud-hosted applications which use the web browser as the universal desktop client has seen the popularity of the JavaScript language grow massively. And having to code in both JavaScript and a back-end language like PHP or Java increases costs and generally makes life difficult - so why not code the back end in JavaScript, too? The answer to that question is Node.js, which implements a JavaScript runtime on web servers and unsurprisingly has also become massively popular.
And just like the other languages, Node.js has its own package manager and repository for distribution of useful libraries, subsystems and code packages generally, in the form of npm. But now comes news of a massive threat to the Node.js software supply chain, in the form of what a former GitHub and npm engineering manager, Darcy Clarke, has termed, "manifest confusion".
The basic problem is this: a npm package's manifest - a JSON file which lists the package id, name, version info, contents, dependencies, etc. - is published independently from its tarball (the .tgz file with the actual contents), and manifests are never fully validated against the tarball's contents. In a blog post, Clarke writes that
"From the outset, the npm project also put a lot of trust in the client vs. server-side of the registry. Looking back now, its clear that the practice of relying so heavily on a client to handle validation of data is riddle with issues"
From experience teaching some aspects of web application development, I would say this is a common problem. Web developers who work on both the client and server halves of a product often fail to recognise the trust boundary between the two and rely on the client to perform not just validation but sanitization in order to protect the server. What they don't realize is that a) the client is not under their control as it runs on an untrusted system, and b) an attacker may well run a completely different client of their own devising in order to bypass their sanitization.
Returning to the manifest confusion problem, Clarke continues:
The issue at hand is that the version metadata (aka. "manifest" data) is submitted independent from the attached tarball which houses the package's package.json. These two pieces of information are never validated against one another & calls into question which one should be the canonical source of truth for data such as dependencies, scripts, license & more. As far as I can tell, the tarball is the only artifact that gets signed & has an integrity value that can be stored & verified offline (making the case for it to potentially be the proper source; yet, very surprisngly, the name & version fields in package.json can actually differ from those in the manifest, because they were never validated).
This loophole means that threat actors could conduct a variety of different attacks - most obviously publishing a package which contains hidden dependencies or run install scripts which load malware - and Clarke's post provides proof-of-concepts for several of them. This vulnerability puts the entire npm software supply chain at risk.
Worst of all, this issue was first disclosed to GitHub in early November 2022 and further escalated by Clark in March of this year - but to date, nothing seems to have been done, publicly at least. In the meantime, Clarke recommends that users switch to using the package contents in the tarball for metadata where needed.
Clarke, Darcy, The massive bug at the heart of the npm ecosystem, blog post, 27 June 2023. Available online at https://blog.vlt.sh/blog/the-massive-hole-in-the-npm-ecosystem.
Interpol Arrests Key Figure in OPERA1ER Cybercrime Group
A cybercrime group - known variously as OPERA1ER, NX$M$, DESKTOP Group and Common Raven - has been perpetrating a variety of malware and phishing campaigns, as well as large-scale business email compromise scams, over the last four years, targeting financial institutions and mobile banking services in 15 countries across Africa, Asia and Latin America. First detected by security firm Group-IB and telco Orange, the group is believed to have stolen somewhere between $US11 million and $US30 million.
Interpol's Cybercrime Directorate established Operation Nervone to coordinate intelligence provided by the two firms above, as well as the US Secret Service's Criminal Investigative Division and Booz Allen Hamilon DarkLabs, in turn providing key information to the Direction de l'Information et des Traces Technologiques (DITT) in Côte d’Ivoire.
And so, in early June, authorities in Côte d’Ivoire were able to arrest a key suspect linked to attacks against financial institutions across Africa. The sheer number of different agencies and security firms involved in this operation - it was also backed by the African Joint Operation against Cybercrime and the INTERPOL Support Programme for the African Union in relation to AFRIPOL - clearly illustrate the complexity of international investigations, especially in comparison to the relative ease of criminal operations on the borderless Internet.
Interpol, Suspected key figure of notorious cybercrime group arrested in joint operation, news release, 5 July 2023. Available online at https://www.interpol.int/News-and-Events/News/2023/Suspected-key-figure-of-notorious-cybercrime-group-arrested-in-joint-operation.
LockBit Halts Nagoya Port Operations
Who can forget the global impact of NotPetya, the 2017 wiper which disrupted global shipping and supply chains - all because of a Russian attack on Ukraine's tax collection? Here we go again, albeit on a much smaller scale, although the impact may well flow through to purchasers of Toyota motor vehicles.
Early on Tuesday morning, an employee at the Nagoya Port Authority discovered a ransomware infection on their computer. The ransomware turns out to be the notorious LockBit 3.0, and its Russian operators have made a ransom demand in exchange for system recovery.
The impact here is not likely to be the exfiltration of sensitive data - the port system likely deals with container shipping manifests - but will primarily be the impact of business process interruption, since Nagoya is Japan's major shipping port. In particular, it is the key hub for Toyota's exports and imports, with the car maker reporting that it cannot load or unload auto parts due to the port's shutdown.
Uncredited, Pro-Russian hackers target Port of Nagoya, disrupting loading of Toyota parts, The Japan Times, 5 July 2023. Available online at https://www.japantimes.co.jp/news/2023/07/05/national/nagoya-port-cyberattack/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Swedish Companies Fined for Using Google Analytics
In a heads-up for privacy professionals everywhere, the Swedish Authoruty for Privacy Protection (Integritetsskyddsmyndigheten - IMY) has fined two companies for using Google Analytics and warned one, along with two others, to bring their security measures into line with the requirements of the EU GDPR (General Data Protection Regulation).
The decision stems from ongoing concerns held by the EU over invasive US surveillance programs, such as PRISM and UPSTREAM, which could expose the personally identifiable information of EU residents which had been transferred to the US for processing by service providers. The US has attempted to assuage EU fears with the establishment of various compliance programs; initially a set of principles termed Safe Harbor, which was replaced in 2016 by the Privacy Shield framework. This establishes a list of companies to which EU firms could legally transfer PII; the list is maintained by the US Department of Commerce and compliance with its requirements is monitored by the US Federal Trade Commission.
However, in July 2020, the Court of Justice of the European Union declared the EU's Privacy Shield Decision invalid on account of invasive US surveillance, and stipulated stricter requirements for the transfer of data based on standard contract clauses (SCC's) which must provide data subjects a level of protection essentially equivalent to the EU GDPR and the EU Charter of Fundamental Rights. If the standard contract clauses are insufficient to do this, then EU companies which transfer PII to the US must implement additional safeguards to compensate.
Sweden's IMY has audited how four companies transfer personal data to the US via Google Analytics - specifically, a version of Google Analytics from 14 August 2020 - based on complaints from the organisation, None of Your Business (NOYB). IMY considers the data to be personal data because it can be linked with other unique data that is transferred (which is rather the point of targeted advertising analytics). The four companies based their decision to utilise Google Analytics on standard contract clauses, but after audit, IMY decided that none of the companies' additional technical security measures were sufficient.
The four companies involved are:
- Tele2 SA, which was fined 12 million Swedish Krona
- CDON AB, fined 300,000 Swedish Krona
- Coop SA
- Dagens Industri
Tele2 SA had already independently decided to stop using Google Analytics; the other three firms were ordered to stop and to implement adequate data protection mechanisms. This decision aligns with similar steps taken by authorities in Austria, France and Italy; Facebook parent Meta had previously been fined a record $U1.3 billion by the EU. All eyes are now turning to the finalization of a proposed replacement for Privacy Shield, to be called the EU-US Privacy Framework.
IMY, Four companies must stop using Google Analytics, news release, 3 July 2023. Available online at https://www.imy.se/en/news/four-companies-must-stop-using-google-analytics/.
noyb, noyb win: First major fine (€1 million) for using Google Analytics, news release, 3 July 2023. Available online at https://noyb.eu/en/noyb-win-first-major-fine-eu-1-million-using-google-analytics.
Ghostscript Feature Turns Bug, Then Turns Vulnerability
Since the release of the Apple Laserwriter back in the 1980's, the leading page description and graphics language for printers has been PostScript. It turns up everywhere: embedded into printers, but also as the underlying language for PDF, the Portable Document Format, used for document interchange near-universally. It is also an essential component of LaTeX, the technical editing and publishing system used by computer science academics and mathematicians for typesetting their work. In particular, a lot of technical graphics gets generated in the form of Postscript - particularly Encapsulated Postscript (.eps) files. And while there are plenty of PDF viewers to choose from, the majority of academics writing LaTeX will use Ghostscript to render and view .ps and .eps files.
Writing for Sophos' Naked Security blog, Paul Ducklin describes how a long-lived feature of the venerable Ghostscript program turned out to be not just a bug, but an exploitable vulnerability. On UNIX and Linux systems, print processing used to be done using shell scripts that would run a series of small text processing programs to generate whatever format the connected printer required - and to do this, they would pipe the output of one program into the next. This is a fundamental feature of the classic Software Tools concept that underlies UNIX - write small programs that each do one thing, and do it will, and then combine them to accomplish more complex tasks.
The combination is performed by using the I/O redirection features of the shell - that is, > to send the output of a program to a file, < to read the input of a program from a file, and | (the pipe symbol) to connect the output of one program into the input of the next, via an in-memory buffer. And it's not just UNIX that has this ability - Microsoft introduced it into MS-DOS 2.0 in the early 1980's (although being a single-tasking system, DOS had to run one program after the other and faked pipes via temporary files) and it lives on in Windows. Ghostscript is also often used in web applications, to generate downloadable documents from web pages.
It turns out that Ghostscript's PostScript implementation can open and write to files. And, like many UNIX programs, as well as simple file pathnames, it will accept strings that begin with the pipe symbol, |, and continue with a command into which the output will be written. In fact, this can be a complete command line, with options and arguments, etc. (Actually, the string %pipe% can also be used, in Ghostscript).
If you're a security pro, you should by now be thinking of various ways this can be used maliciously. In short, it will allow an innocuous PostScript, EPS or even PDF file to execute commands on the target system. However, this was only realized fairly recently, giving rise to CVE-2023-36664, which is finally fixed in Ghostscript 10.01.2. I say finally because, rushing to get a patch out the door, the maintainers' first attempt only checked for the %pipe% string, and it required a second attempt to also match the | symbol. This is not that unusual when programmers are under pressure to fix a vulnerability.
Ducklin, Paul, Ghostscript bug could allow rogue documents to run system commands, blog post, 4 July 2023. Available online at https://nakedsecurity.sophos.com/2023/07/04/ghostscript-bug-could-allow-rogue-documents-to-run-system-commands/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Chinese APT Implants Ancient Trojan Via HTML Smuggling
Check Point Research brings us a report of a Chinese threat actor which is targeting foreign affairs ministries and embassies in a number of European countries - primarily the UK, Czech Republic, Hungary, Slovakia and Ukraine - with the likely goal of cyber-espionage, as indicated by the lure documents in the compaign emails, such as a letter originating from the Serbian embassy in Budapest, and an invitation to a diplomatic conference issued by Hungary's Ministry of Foresign Affairs.
The campaign - which Check Point have christened 'SmugX' - overlaps with previously-reported activity by the Chinese APT's RedDelta and Mustang Panda, and has been running since at least December 2022. It makes use of HTML smuggling - a technique in which the attackers hide a malicious payload inside HTML documents, enabling it to bypass network controls. Opening one of these documents starts a first stage loader consisting of the following chain of events:
- The embedded payload within some JavaScript code is decoded and saved to a blob with the appropriate filetype (e.g. application/zip)
- Instead of utilizing the HTML <a> element, the JavaScript code dynamically creates it
- A URL object is created from the blob using the createObjectURL function
- The download attribute is set with the desired filename
- Finally, the code invokes the click action, simulating a user clicking on the link, to initiate the file download
- For older browsers, the code employs msSaveOrOpenBlob to save the blob under the desired filename
This then chains to a second stage loader, of which there are two variants. The first uses a ZIP file that contains a malicious LNK file which will run PowerShell code to extract a compressed archive and save it to the %temp% directory. This archive contains three files:
- A legitimate executable - either robotaskbaricon.exe or passwordgenerator.exe - taken from a vulnerable version of the Roboform password manager
- A malicious sideloaded DLL called RoboForm.dll
- The malware payload, in a file called data.dat
The PowerShell code then runs the executable. The DLL sideloading technique allows the malicious code to be run within the context of this apparently legitimate process.
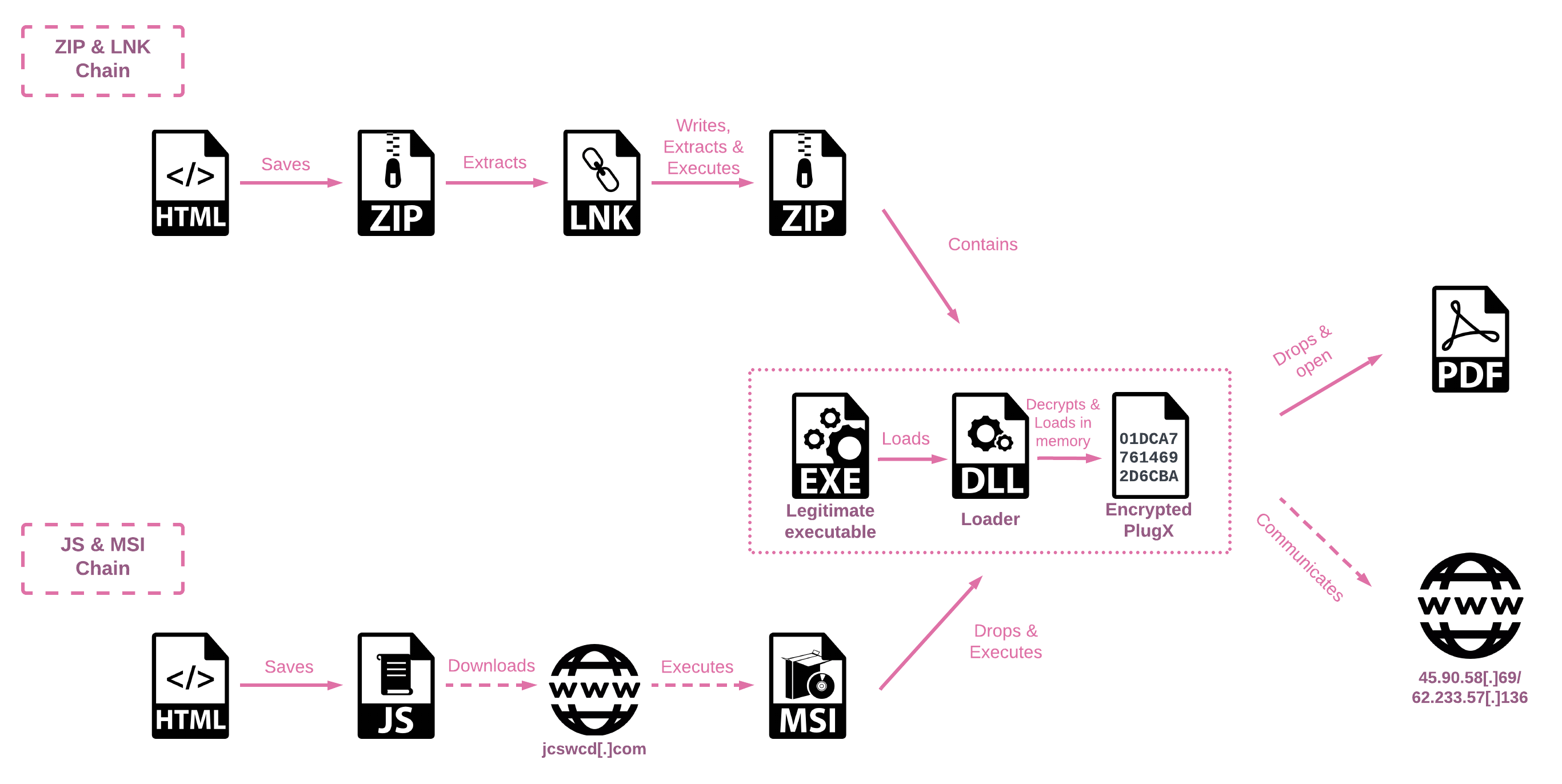
The two infection chains (image credit: Check Point Research)
The second variant of the second-stage loader uses JavaScript, rather than PowerShell, to download a MSI file, but installs the same three files.
The final payload is the PlugX remote access trojan, which has been used by multiple Chinese threat actors since 2008; its long life may be attributed to its modular structure which accommodates a variety of plugins which extend its functionality to include file theft, screen captures, keystoke logging and remote command execution. One notable change in this version is the switch to using RC4 encryption rather than the simple XOR technique used in previous samples.
The use of a variety of HTML smuggling infection chains, coupled with DLL sideloading, seems to have allowed this and perhaps similar campaigns to evade detection.
Check Point Research, Chinese Threat Actors Targeting Europe in SmugX Campaign, report, 3 July 2023. Available online at https://research.checkpoint.com/2023/chinese-threat-actors-targeting-europe-in-smugx-campaign/.
ISC2 Bylaws Voting Resumes
As we reported last week, the International Information Systems Security Certification Consortium - (ISC)2 - ran into difficulties with some of its online systems, specifically the page for making Annual Maintenance Fee payments, but more importantly the page for voting on proposed bylaw amendments.
While I continue to do battle with (ISC)2 over the AMF payment snafu, at least the bylaw voting process has resumed. Members can find a link to the voting page at the top of their dashboard after logging in - https://my.isc2.org/s/dashboard. Before voting, I recommend reading Stephen Mencik's blog posts, at https://smencik1.wordpress.com/2023/06/06/upcoming-by-laws-vote-info-and-recommendation/ and https://smencik1.wordpress.com/2023/06/26/by-laws-voting/.
CISA Vulnerability Summary
The US Cybersecurity and Infrastructure Security Agency has released its vulnerability summary for the week of 26 June. The list is long, but helpfully broken into sections by CVSS severity levels:
- High: vulnerabilities with a CVSS base score of 7.0 - 10.0
- Medium: vulnerabilities with a CVSS base score of 4.0 - 6.9
- Low: vulnerabilities with a CVSS base score of 0.0 - 3.9
So far, I have only skimmed quickly - I will search for anything directly relevant to my needs later - but I'm seeing a lot of WordPress plugins as well as Apple and Android OS's getting mentions. It seems all the usual categories of vulnerabilities keep turning up: use-after-free, directory traversals, Time-of-Check/Time-of-Use, out-of-bounds reads. Sigh - maybe it's time for we humans, creatures of bounded rationality as we are, to give up writing software, we are so bad at it.
CISA, Vulnerability Summary for the Week of June 26, 2023, bulletin, 3 July 2023. Available online at https://www.cisa.gov/news-events/bulletins/sb23-184.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Active Exploitation of WordPress Plugin
Specialist WordPress security firm Wordfence has reported on active exploitation of an unpatched privilege escalation vulnerability in Ultimate Member, a plugin installed on over 200,000 WordPress sites. The vulnerability has not been properly patched in version 2.6.6, the latest version of the plugin, and Wordfence recommend uninstalling the plugin until a complete patch becomes available.
The Ultimate Member plugin is intended to add easy registration and account management on WordPress sites. Unfortunately, the registration form component performs inadequate sanitization of form keys, making it possible for users to register and set arbitrary metadata on their account - including the wp_capabilities meta value which, if set to 'administrator', blesses an attacker with full capabilities on the site. Although a series of updates have attempted to block this by including a predefined list of banned metadata keys, attackers have found a number of simple ways to bypass this, such as varying the case, including slashes, and URL-encoding the keys.
The result is CVE-2023-3460, which garners a CVSS score of 9.8 (Critical). Wordfence's advisory provides indicators of compromise, and the company has released a firewall rule for their products which will protect customers against exploitation.
Chamberland, Chloe, PSA: Unpatched Critical Privilege Escalation Vulnerability in Ultimate Member Plugin Being Actively Exploited, blog post, 29 June 2023. Available online at https://www.wordfence.com/blog/2023/06/psa-unpatched-critical-privilege-escalation-vulnerability-in-ultimate-member-plugin-being-actively-exploited/.
Avast Releases Akira Decryptor
Anti-malware firm Avast has released a decryptor for the Akira ransomware which appeared in March 2023 and has gone on to attack a variety of industries including education, finance and real estate. Akira's approach to file encryption is interesting - its authors favouring a lightweight, fast approach (using Dan Bernstein's Chacha 2008 stream cipher) that only partially encrypts files in order to render them unusable, rather than performing full encryption. In most respects, it is similar to the earlier Conti ransomware, suggesting a link of some kind between the authors.
For files of 2,000,000 bytes and smaller, the ransomware encrypts the first half of the file, while for larger files, it encrypts four blocks interspersed within the file. In both cases, the encryption uses a random key, and Akira appends a structure which contains the original file size, the malware version number, the type of encryption performed and the random key, encrypted using RSA public-key crypto with a 4096-bit modulus. The extension .akira is then appended to the filename, and an akira_readme.txt ransom note is dropped into each folder.
In order to use Avast's decryptor, a victim must find a matched pair of files - one encrypted, one the pre-ransom unencrypted version - that are as large as possible. The decryption tool will examine these and attempt to extract the decryption key. Once this is found, the decryptor tool can proceed to decrypt all the files on drive, optionally saving backups as it goes (highly recommended).
The Avast researchers do not describe how their key-cracking process works, but I have my suspicions (and my former cryptography students should be able to guess, too 😉).
Of course, the decryptor tool cannot provide any protection against any consequences of information exfiltration threatened in the Akira ransom note - it can only recover lost files.
Avast Threat Research Team, Decrypted: Akira Ransomware, blog post, 29 June 2023. Available online at https://decoded.avast.io/threatresearch/decrypted-akira-ransomware/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
MITRE Updates Top 25 Most Dangerous Software Vulnerabilities
The Homeland Security Systems Engineering and Development Institute, which is operated for the DHS by MITRE, has released its 2023 Common Weakness Enumeration (CWE) Top 25 Most Dangerous Software Weaknesses. This is calculated by analyzing the last two years' public vulnerability data in the National Vulnerability Data (NVD) - that's 43,996 CVE records - for root cause mappings to CWE weaknesses. The 2023 CWE Top 25 also incorporates updated data for recent CVE records in the database that underlies CISA Known Exploited Vulnerabilities Catalog (KEV).
The top 25 are:
- Out-of-bounds Write CWE-787
- Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') CWE-79
- Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') CWE-89
- Use After Free CWE-416
- Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') CWE-78
- Improper Input Validation CWE-20
- Out-of-bounds Read CWE-125
- Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') CWE-22
- Cross-Site Request Forgery (CSRF) CWE-352
- Unrestricted Upload of File with Dangerous Type CWE-434
- Missing Authorization CWE-862
- NULL Pointer Dereference CWE-476
- Improper Authentication CWE-287
- Integer Overflow or Wraparound CWE-190
- Deserialization of Untrusted Data CWE-502
- Improper Neutralization of Special Elements used in a Command ('Command Injection') CWE-77
- Improper Restriction of Operations within the Bounds of a Memory Buffer CWE-119
- Use of Hard-coded Credentials CWE-798
- Server-Side Request Forgery (SSRF) CWE-918
- Missing Authentication for Critical Function CWE-306
- Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition') CWE-362
- Improper Privilege Management CWE-269
- Improper Control of Generation of Code ('Code Injection') CWE-94
- Incorrect Authorization CWE-863
- Incorrect Default Permissions
CWE-276
There are a couple of new entrants in the list: 22. Improper Privilege Management shot up from 29th position last year, while 24. Incorrect Authorization moved from #28. Also rocketing up the charts were 4. Use After Free (last year's #7, but known to account for around half the bugs in the Chrome browser) and 11. Missing Authorization, which rose from the #16 position.
Looking at the list, it's not exactly comforting to see old favourites are still with us after many, many years - including, in top position, Out-of-bounds Write, a.k.a. the Buffer Overflow and its various close relatives, which has been with us since at least the 1960's, if not before. Perhaps the adoption of memory-safe languages like Rust into development, including in the kernels of both Linux and Windows, will see this wizened old character handed a gold watch and pensioned off into retirement.
Likewise, the appearance of XSS and SQL Injection just below this (and Command Injection just a little lower) is more than a bit disturbing. Clearly, we need to do a better job of educating programmers, rather than checking them for a pulse and then turning them loose to copy-and-paste code fragments from StackOverflow. We should also be using static analysis a lot more - many of the entries in the Top 25 can easily be caught this way.
The CWE Top 25 Most Dangerous Software Weaknesses can be found at https://cwe.mitre.org/top25/. Essential reading for most developers (along with the various OWASP Top 10's), I'd say - and could be the basis of some profitable management discussions as well as some 'lunch-and-learn' sessions.
CISA, 2023 CWE Top 25 Most Dangerous Software Weaknesses, news alert, 29 June 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/06/29/2023-cwe-top-25-most-dangerous-software-weaknesses.
All Is Not Well in CISSP-Land
Disturbing developments continue at the International Information Systems Security Certification Consortium (ISC)2 - the gatekeeper of the 'gold standard' certification for security pro's, the CISSP. Last year's board election saw over 80 candidates nominated to take part in the election - but a behind-closed-doors, undocumented 'selection process' run by the then-current board resulted in only six candates being put on the election slate to fill the six open positions. The result was an election in name only - it really didn't matter how the membership voted. And the bar for write-in candidates - of whom there were several - made it impossible for any of them to get the necessary votes for election.
A little later, the board proposed a number of changes to the Bylaws that would have further consolidated its powers and stifled the voices of the members. Unsurprisingly, these were voted down by the members, with veteran member Stephen Mencik working tirelessly to point out the problems and, eventually, proposing an alternative set of of amendments that seemed, to those members discussing them, to be a much better way forward.
Unsurprisingly, the board reacted very negatively to this, accusing Stephen of violating an NDA (he hadn't, as best we can determine) and making various other threats. Early this month, the board conducted a webinar - at an ungodly hour, as far as most of a global membership are concerned - to explain their response and their proposed way forward with a new vote on the Bylaws amendments.
I strongly urge all current CISSP's to read Stephen's blog commentary on this webinar, at https://smencik1.wordpress.com/2023/06/06/upcoming-by-laws-vote-info-and-recommendation/. There are several problems with their proposed voting process - not least of them that the member petition called for a vote on each of the proposed amendments individually, while the Bylaws Committee has set up a procedure whereby members must vote for either the petition's alternative bylaw amendments as a block, the board's proposals as a block, or neither of these.
In any case, voting opened on June 20th.
And closed a few hours later.
Members received an email which read, in part:
A vulnerability has been identified in our bylaws voting platform. We hold the integrity of our member voting paramount and have suspended voting until a secure environment is restored. No data were compromised.
We will provide updates when available. All members will have an opportunity to vote prior to the August 1, 2023, Special Meeting. To ensure the integrity of the results, all members will be asked to resubmit their vote.
Since then: silence. One has to wonder about a vulnerability in the voting platform of the organization that operates the self-proclaimed 'gold standard' in infosec.
Stephen has blogged about this also, at https://smencik1.wordpress.com/2023/06/26/by-laws-voting/, and I would urge reading it, as well as other entries at https://smencik1.wordpress.com/.
I cannot say I am entirely surprised at this snafu - your humble scribe has been encountering his own difficulties with the (ISC)2 web site. The end of June marks the time to pay my Annual Maintenance Fees (AMF) in order to continue to be a member in good standing (and thereby, of course, vote in Great Bylaws Controversy of 2022/23). So, earlier this week, I dutifully logged in to the site, entered my credit card details and submitted payment. In response, I was greeted with a payment confirmation page that had blank fields for payment date, receipt number, order summary, payment amount and balance. The promised emailed receipt did not turn up, either.
So I contacted their customer service, a.k.a. member support, to be told that no, payment had not gone through. So, late the following day, after checking my credit card history and seeing no transaction, I tried again - with the same result, a blank confirmation and no receipt.
The next morning - and I wish I could say I was surprised - the credit card account showed a transaction for the first (apparently unsuccessful) payment attempt. I advised member support only to be told that, no, the transaction had not gone through.
"Yet", I replied. "The operative word here is 'yet'" - with no response from member support. And sure enough, the second payment attempt was also successful, with the transaction turning up in my credit card account this morning. I wouldn't be surprised if a third turns up tomorrow.
But still, the "member dashboard" at (ISC)2 shows my AMF as still outstanding, on this last day of my membership year, despite my now having paid it twice.
I cannot but laugh at the declaration at the bottom of the broken (ISC)2 payment confirmation page:
"(ISC)² has been issued an attestation of compliance from a qualified security assessor (QSA) from the Payment Card Industry (PCI). Our payment operations are validated to follow best practices to increase controls around cardholder data to reduce credit card fraud."
I've been told by another CISSP that his AMF payment was initially blocked by his own bank as they saw (ISC)2's payment processing as too risky. I've now raised a dispute with my own bank for the duplicate payment; I imagine that won't do much for their reputation either.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
CISA & NSA Release Guidance on Defending CI/CD Pipelines
The US Cybersecurity & Infrastructure Security Agency, together with the NSA, has released an information sheet - of 23 pages - on defending the Continuous Integration / Continuous Delivery (CI/CD) environments that form an essential part of DevOps and DevSecOps.
CI/CD sits at the confluence of a number of factors: the switch to cloud environments, deployment of applications using containers and Platform-as-a-Service architectures, and the application of automation and orchestration throughout the software development lifecycle. It provides a largely straight path from the source code repository where developers check in their code, through the build, test and deployment phases right into production.
As threat actors find it harder and harder to compromise production systems, so they have shifted their attention to the earlier steps in the software supply chain, prefering to compromise source code repositories and the other steps in the CI/CD pipeline. After helpfully defining terms - not every security pro has a development background, unfortunately, and those who do often left the field before the advent of DevOps - the 'sheet' moves on to enumerating the threats (based on the OWASP Top 10 CI/CD Security Risks) and the relevant attack surfaces, including:
- Insecure code
- Poisoned pipeline execution
- Insufficient pipeline access controls
- Insecure system configuration
- Usage of third-party services
- Exposure of secrets
This is followed by three interesting scenarios, and then suggested mitigations to harden CI/CD environments, such as:
- Using recommened cryptography
- Minimize the use of long-term credentials
- Signing the CI/CD configuration and verifying it throughout the process
- Requiring a second programmer to review and approve code as part of the check-in process
- Implementing the principle of least privilege for CI/CD access
- Carefully securing secrets, tokens and keys, including ensuring none are left embedded in code
- Proactively patching and updating CI/CD tools and the underlying systems
- Implementing security scanning tools such as static and dynamic testing early in the C/CD process
- Restricting untrusted libraries and tools
- Quickly removing temporary resources such as VM's and Kubernetes clusters after use
- Implementing software bill of materials (SBOM) and software composition analysis (SCA)
- Architecting, building and testing for resiliency
An appendix maps the various CI/CD threats to the MITRE ATT&CK framework tactics as well as a the D3FEND countermeasures. The information sheet also provides many links to additional guidance documents. I'd say this information sheet is required reading for the many information assurance pros whose developers have been tardy in inviting them to the DevOps party. Time to replace that with DevSecOps!
NSA and CISA, Defending Continuous Integration/Continuous Delivery (CI/CD) Environments, cybersecurity information sheet, June 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/06/28/cisa-and-nsa-release-joint-guidance-defending-continuous-integrationcontinuous-delivery-cicd and https://media.defense.gov/2023/Jun/28/2003249466/-1/-1/0/CSI_DEFENDING_CI_CD_ENVIRONMENTS.PDF.
Second Thoughts About AI?
The AI hype cycle is finally dying down, as more and more stories surface of embarrassing AI disasters such as the one that befell a lawyer who filed a ChatGPT-written document citing non-existent cases. Now, a new survey from Malwarebytes has revealed the initial enthusiasm for ChatGPT has faded, with 81% of respondents concerned about possible security and safety risks, 63% not trusting the information it produces and 51% wanting to see work on it paused while regulations catch up.
If you are familiar with Gartner's hype cycle, you probably agree: we've fallen from the Peak of Inflated Expectations to the Trough of Disillusionment.
As an AI enthusiast from the early 1970's (in the Department of Cybernetics at the University of Reading) I'd say that's unfortunate: the sins of commercial large language models (LLM's) should not be transferred to the many less ambitious and less spectacular applications of machine learning and AI that are making continuous incremental progress. In large part, the inflated expectations were inevitable as the public, who do not understand the internal operation of transformers and generative LLM's, poked and prodded at the beast and were amazed when it produced lucid and articulate responses. Surely something that speaks so fluidly - and at length, too! - must actually be intelligent!
Sorry - no.
When put to work on a bounded and high-quality corpus of traning material - for example, a database of legislation and regulations - such programs can do an excellent job of tasks such as summarization and abstraction as well as answering questions which demand only limited inference. I can see them being incredibly useful in GRC applications, for example, where they could spare analysts many hours of boring reading and searching to determine the consequences of various proposed actions.
Where ChatGPT and its ilk fall down is in two areas. Firstly, they train on the public world wide web (as it existed in 2021, in the case of GPT-3). And the web is notoriously full of misinformation, disinformation and outright malinformation. And secondly, being limited purely to statistical processing of words - knowing synonyms, how frequently words appear, how often they appear in various combinations, etc. - and not their meanings, LLM's can't tell fact from fiction, so happily treat the two the same way.
And when processing case law or academic papers, for example, the LLM's record things like the types of names that appear in case titles (some companies, some inviduals, etc.) and the styles of paper titles, author names and their related institutions, reference styles, etc.. When spinning words around to create output, they will quite happily pick relevant words and spin them into plausible-sounding cases and papers - a process referred to as AI hallucination.
This process is likely to get worse, as the use of generative LLM's by news aggregation sites, and especially disinformation sites, rapidly increases on the web. As other LLM's train on this data, so a feedback loop will develop in which AI trains on AI-generated text. Can you spell, garbage in, garbage out?
A recent paper by Shumailov et. al. (with Ross Anderson, of "Security Engineering fame, as one of the co-authors) addresses this very topic, finding that "model-generated content in training causes irreversible defects in the resulting models, where tails of the original content distribution disappear. We refer to this effect as Model Collapse and show that it can occur in Variational Autoencoders, Gaussian Mixture Models and LLMs. We build theoretical intuition behind the phenomenon and portray its ubiquity amongst all learned generative models".
In short, LLM's have their place, and as long as they stay in it and aren't unleashed to roam the world wide web, they are going to perform valuable work, including in security-related areas such as compliance assurance, software development (essentially a transformation problem from problem specification to executable code), automated malware analysis (explicating what machine code does and is likely intended to achieve), etc. But let's keep our expectations in check, mmmkay?
Shunailov, Ilia, The Curse of Recursion: Training on Generated Data Makes Models Forget, arXiv preprint, 31 May 2023. Available online at https://arxiv.org/abs/2305.17493v2.
Stockley, Mark, 81% concerned about ChatGPT security and safety risks, Malwarebytes survey shows, blog post, 27 June 2023. Available online at https://www.malwarebytes.com/blog/news/2023/06/chatgpt.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.