Les Bell and Associates Pty Ltd
Site blog
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Cozy Bear Targets Ukraine Supporters with Infostealer
Yesterday we reported on a Microsoft Outlook vulnerability being exploited by the Russian GRU-affiliated group APT28, a.k.a. Fancy Bear. Today it's the turn of another Russian group: APT29, a.k.a. Cozy Bear or NOBELIUM, a group affiliated with the Foreign Intelligence Service (SVR) of the Russian Federation, who are now targeting European governments and diplomatic entities which are aiding Ukraine. You may recall them from such high-profile breaches as the US Democratic National Congress hack and their trojanning of the Solar Winds Orion network management software.
This time, they specifically targeted entities with an interest in the activities of the Polish Ministry of Foreign Affairs and especially the activities of the Polish Ambassador to the US, such as a talk he gave in early February to the Columbus School of Law at the Catholic University of America in Washington DC. They prepared for this campaign by creating HTML pages containing relevant lures on the web site of a library in El Salvador, and then used spearphishing to direct likely victims to those pages.
The HTML pages in turn dropped .ISO files which contained two files: a binary called BugSplatRc64.dll and a shortcut (.lnk) file which would invoke the DLL with the command line
C:\Windows\system32\rundll32.exe BugSplatRc64.dll,InitiateDs
When this runs, it copies BugSplatRc64.dll into the user's AppData directory and creates a new registry key to invoke it on boot, as a way of persisting. BugSplatRc64.dll is an infostealer; it first gathers basic information such as the user name and IP address which it then sends to the attacker's C2 server. From there, it connects to the C2 server every minute, checking for a payload which it will download and execute as shellcode within its process.
Interestingly, the C2 server uses the public API of the popular Notion note-taking software, making it hard to differentiate from legitimate traffic. This is a common technique of APT29; previously they have used the Trello API, only switching to Notion in late 2022.
Blackberry Research & Intelligence Team, NOBELIUM Uses Poland's Ambassador’s Visit to the U.S. to Target EU Governments Assisting Ukraine, blog post, 14 March 2023. Available online at https://blogs.blackberry.com/en/2023/03/nobelium-targets-eu-governments-assisting-ukraine.
US DoJ, German Bundeskriminalamt Take Down Darknet Cryptocurrency Mixer
Despite popular belief to the contrary, cryptocurrencies such as Bitcoin do not provide complete anonymity; both police intelligence services and commercial forensics companies have developed techniques for tracking Bitcoin transactions to the destination wallets. Clearly, this poses a problem for cybercriminals such as ransomware groups, who want to use cryptocurrency as an untraceable form of international payment.
The solution has been so-called 'mixer' services, which run deposited Bitcoin (and other cryptocurrencies) through multiple rounds of transactions before depositing the total into a destination wallet, making it hard for analysts to trace in the process. Effectively, it's a highly randomized, automated form of money laundering.
Now, a coordinated operation between the US Department of Justice and the German Bundeskriminalamt has seen the seizure of two domains, a Github account, and the back-end servers of the ChipMixer service, along with over $US46 million in cryptocurrency. At the same time, Minh Quốc Nguyễn, 49, of Hanoi, Vietnam, was charged in Philadelphia with money laundering, operating an unlicensed money transmitting business and identity theft in connection with ChipMixer. If convicted, he faces a maximum of 40 years in jail.
Although ChipMixer had a domain on the public Internet, its main operation was a Tor hidden service which was used by a large criminal clientele to launder the proceeds of their crimes. Between August 2017 and March 2023, ChipMixer processed:
- $17 million in bitcoin for criminals connected to approximately 37 ransomware strains, including Sodinokibi, Mamba and Suncrypt;
- Over $700 million in bitcoin associated with wallets designated as stolen funds, including those related to heists by North Korean cyber actors from Axie Infinity’s Ronin Bridge and Harmony’s Horizon Bridge in 2022 and 2020, respectively;
- More than $200 million in bitcoin associated either directly or through intermediaries with darknet markets, including more than $60 million in bitcoin processed on behalf of customers of Hydra Market, the largest and longest running darknet market in the world until its April 2022 shutdown by U.S. and German law enforcement;
- More than $35 million in bitcoin associated either directly or through intermediaries with “fraud shops,” which are used by criminals to buy and sell stolen credit cards, hacked account credentials and data stolen through network intrusions; and
- Bitcoin used by the Russian General Staff Main Intelligence Directorate (GRU), 85th Main Special Service Center, military unit 26165 (aka APT 28) to purchase infrastructure for the Drovorub malware, which was first disclosed in a joint cybersecurity advisory released by the FBI and National Security Agency in August 2020.
"ChipMixer facilitated the laundering of cryptocurrency, specifically Bitcoin, on a vast international scale, abetting nefarious actors and criminals of all kinds in evading detection", said U.S. Attorney Jacqueline C. Romero for the Eastern District of Pennsylvania. "Platforms like ChipMixer, which are designed to conceal the sources and destinations of staggering amounts of criminal proceeds, undermine the public’s confidence in cryptocurrencies and blockchain technology. We thank all our partners at home and abroad for their hard work in this case. Together, we cannot and will not allow criminals’ exploitation of technology to threaten our national and economic security."
DoJ Office of Public Affairs, Justice Department Investigation Leads to Takedown of Darknet Cryptocurrency Mixer that Processed Over $3 Billion of Unlawful Transactions, news release, 15 March 2023. Available online at https://www.justice.gov/opa/pr/justice-department-investigation-leads-takedown-darknet-cryptocurrency-mixer-processed-over-3.
Ransomware Group Gives Up Encryption, Focuses on Exfiltration
A new report from Redacted details the recent operations of the BianLian ransomware gang. Like many such groups, the ransom revenue they get from their activities has allowed them to thrive, polishing their tactics and techniques and hitting ever more victims. However, there is a new twist in their operations.
While ransomware gangs used to simply encrypt the victims' files, holding them hostage until a ransom was paid, when they would release a decryption key to the victims, many if not most ransomware operators added a second string to their bow: exfiltrating data and threatening to release it publicly so as to cause embarrassment to the victim (or their customers or patients). This in part explains why they have sought out the healthcare sector for special attention. In other cases, they have ransomed identity information which can be sold to other cybercriminals for identity theft attacks.
Now BianLian have taken the obvious next step. Folllowing the release (by Avast) of a decryption tool that would allow victims to recover their files, the group has decided to skip the encryption step and focus instead on extorting a payment in return for not releasing exfiltrated files. In addition, they have also invested more effort in research allowing them to tailor their threats to the victim, investigating relevant laws and regulations that might specifically apply.
The Redacted report contains a full analysis of tactics and techniques, as well as IOC's such as digest values, active and historical IP addresses and more.
Fievishohn, Lauren, Brad Pittack and Danny Quist, BianLian Ransomware Gang Continues to Evolve, blog post, 16 March 2023. Available online at https://redacted.com/blog/bianlian-ransomware-gang-continues-to-evolve/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Latitude Financial Hit With Customer Data Breach
Shares in lender and digital payment processor Latitude Group Holdings have been suspended from trading on the ASX following their notification of a cyber incident. In their announcement, the firm stated that "unusual activity" detected over the last few days is believed to have originated from a major vendor used by Latitude". Despite their taking immediate action, the attackers were able to obtain employee credentials and then use those to steal information held by two other service providers.
From the first provider, the attackers stole approximately 103,000 identification documents - more than 97% of them drivers' licences - while approximately 225,000 customer records were stolen from the second service provider.
Latitude has shut down some systems - both internal and customer-facing - while it works to contain the attack in collaboration with external specialists and the Australian Cyber Security Centre. It is also contacting the affected customers.
Here we go again; this is the second breach of identity documents, specifically drivers' licences, in recent months (the first being from Optus). Replacement of drivers' licences is a particularly painful process, and there is a lesson to be learned here about the retention of documents used for identity verification after that process has been performed. Identity documents should be viewed as a potential liability and not an information asset. If we don't fix this, expect legislation.
Gardy, Mark, Cyber Incident, ASX Announcement, 16 March 2023. Available online at https://www.asx.com.au/asx/statistics/displayAnnouncement.do?display=pdf&idsId=02644401.
Microsoft 365 CVSS 9.8 Vulnerability Being Exploited in the Wild
A couple of days ago, the US Cybersecurity & Infrastructure Security Agency added three new "known exploited vulnerabilities" to its catalog. One of these is CVE-2023-23397 (see also Microsoft's vulnerability page), which has variously been categorised as a remote code execution or privilege escalation vulnerability in Microsoft Outlook. Most significantly, this vuln merits a CVSS 3.x score of 9.8, which makes it critical.
The vulnerability allows a remote and unauthenticated attacker to obtain a victim's logon credentials by simply sending a specially-crafted malicious email. But it gets worse: the victim doesn't even need to look at the email. As Microsoft notes, the code in the malicious email "triggers automatically when it is retrieved and processed by the Outlook client. This could lead to exploitation BEFORE the email is viewed in the Preview Pane". The code then executes a pass-the-hash attack by sending the victim's NTLMv2 hash to a C2 server the attacker controls, allowing the attacker to reuse the hash with other services.
The vulnerability is present in both 32-bit and 64-bit versions of Microsoft 365 for Enterprise, as well as Microsoft Office 2013, 2016 and 2019. Interestingly, according to MDSec - who reverse-engineered one mitigation approach in order to create a proof-of-concept - the vulnerability actually exists in the Outlook code which allows the user to select an audio file to be played when a reminder for a mail item is triggered. Cute, but unnecessary - remember, the enemy of security is complexity.
According to Microsoft's Threat Analytics reports, this exploit has been used against some 15 European government, military, energy and transport organizations since April 2022, with attribution to the Russian GRU unit APT28, a.k.a. Fancy Bear. And of course, now that a PoC is available, expect others to develop their own exploits, making patching even more critical.
Meanwhile, suggested mitigations include disabling the use of NTLMv2 authentication by adding users to the "Protected Users" security group, as well as blocking outbound traffic on TCP port 445 (SMB).
Chell, Dominic, Exploiting CVE-2023-23397: Microsoft Outlook Elevation of Privilege Vulnerability, blog post, 14 March 2023. Available online at https://www.mdsec.co.uk/2023/03/exploiting-cve-2023-23397-microsoft-outlook-elevation-of-privilege-vulnerability/.
Targett, Ed, Urgent: Microsoft 365 Apps being exploited in wild through CVSS 9.8 bug, The Stack, 14 March 2023. Available online at https://thestack.technology/critical-microsoft-outlook-vulnerability-cve-2023-23397/.
CISA Known Exploited Vulnerabilities Updates
Since we mentioned them above, here are the latest additions to the CISA Known Exploited Vulnerabilities Catalog:
- CVE-2023-23397 - Microsoft Outlook Elevation of Privilege Vulnerability (covered above)
- CVE-2023-24880 - Microsoft Windows SmartScreen Security Feature Bypass Vulnerability
- CVE-2022-41328 - Fortinet FortiOS Path Traversal Vulnerability
- CVE-2023-26360 - Adobe ColdFusion Improper Access Control Vulnerability
In fact, Adobe has released security updates for a number of their products; here are the relevant Adobe Security Bulletins:
- Commerce APSB23-17
- Experience Manager APSB23-18
- Illustrator APSB23-19
- Dimension APSB23-20
- Creative Cloud Desktop Application APSB23-21
- Substance 3D Stager APSB23-22
- Photoshop APSB23-23
- ColdFusion APSB23-25
CISA, CISA Adds Three Known Exploited Vulnerabilities to Catalog, Alert, 14 March 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/03/14/cisa-adds-three-known-exploited-vulnerabilities-catalog.
CISA, CISA Adds One Known Exploited Vulnerability to Catalog, Alert, 15 March 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/03/15/cisa-adds-one-known-exploited-vulnerability-catalog.
CISA, Adobe Releases Security Updates for Multiple Products, Alert, 14 March 2023. Available online at https://www.cisa.gov/news-events/alerts/2023/03/14/adobe-releases-security-updates-multiple-products.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Plan for TLS Certificate Renewal Automation
The Chromium Project, which underlies the Chrome browser as well as Microsoft's Edge browser, has announced that it is planning to introduce a proposed maximum "term limit" of 7 years for root CA's, as well as a maximum validity period of 3 years for subordinate CA's, and has submitted these proposed changes to the CA/Browser Forum Server Certificate Working Group for consideration. It is not clear if Google will unilaterally enforce these changes in Chrome if the Working Group rejects them.
Of more pressing concern for most readers, however, is the related proposal to reduce the maximum validity period for TLS server certificates from 398 days to just 90 days. This is just a continuation of a long-standing trend - the maximum validity period used to be three years, but was then reduced to two years and most recently, just over a year; I have routinely warned course attendees against buying long-validity certificates since most CA's do not distribute CRL's for server certificates and a compromise could allow an attacker to masquerade as the victim server for anything up to three years.
The rationale for a 90-day validity is to allow for faster adoption of emerging security capabilities and best practices, as well as promoting cryptographic agility - a 90-day validity will make it easier to quickly adopt new post-quantum algorithms.
I long ago adopted the practice of documenting the procedure of documenting the certificate renewal procedure for our certificates - a process which was frustrated by continual changes at the CA, which made certificate renewal an unnecessarily stressful and error-prone process. Readers who only manage one or two certificates for annual renewal will recognise the problem and view the prospect of manual renewal every three months with some horror. Fortunately, there is a solution.
The ACME (Automatic Certificate Management Environment) protocol enables automatic lifecycle management of TLS certificates. For example, it automates the domain verification step required by the CA - otherwise performed manually by email or creation of a text file containing a hash value on the web server - as well as the generation of a private key and submission of a Certificate Signing Request and the receipt of the issued certificate. Some ACME clients can even install the new certificate and configure the web server to use it.
The most popular ACME client is the Electronic Frontier Foundation's certbot, which is available via the standard package manager for many Linux distributions and has quite comprehensive online instructions. However, Let's Encrypt provides a useful list of alternative clients.
In a timely coincidence, Google Trust Services has announced that it will now provide free TLS certificates for Google Domains customers, and their blog post walks users through the process of installing the required API key and then using the Certbot client to register an account and obtain a certificate.
Electronic Frontier Foundation, Certbot, web page, undated. Available online at https://certbot.eff.org/.
Let's Encrypt, ACME Client Implementations, web page, 29 June 2022. Available online at https://letsencrypt.org/docs/client-options/.
Uncredited, Moving Forward, Together, Chromium Project page, 3 March 2023. Available online at https://www.chromium.org/Home/chromium-security/root-ca-policy/moving-forward-together/.
Warner, Andy and Carl Krauss, Google Trust Services now offers TLS certificates for Google Domains customers, blog post, 2 March 2023. Available online at https://security.googleblog.com/2023/03/google-trust-services-now-offers-tls.html.
Blackcat Turns Nasty
In yet another example of the consequence of not paying ransom demands, the Russia-based Blackcat ransomware group has made good on threats against a medical practice in Lackawanna Count, Pennsylvania. In February, the group compromised a radiation oncology system which stored photographs of patients undergoing cancer treatment, but the Lehigh Valley Health Network refused to pay the ransom demand.
A few weeks later, Blackcat threatened to publish data stolen from the system, claiming "We are ready to unleash our full power on you!". Now they have followed through, releasing graphic images of patients who are undergoing treatment for breast cancer, along with 7 documents containing patient information.
This is another step in an escalation by ransomware operators, as they attempt to deal with victims who refuse to pay up. As the media covers more and more cases of ransomware attacks, the public is coming to understand how aggressive the ransomware operators are and just how difficult perfect defence is, as well as the fact that paying only encourages cybercriminals.
It would be going too far to say the public - especially the directly affected victims - are sympathetic to compromised enterprises, but they are now in no doubt that the bad guys are the attackers, not the companies they breach. But it certainly makes it easier for affected companies to refuse to pay people who commit such heinous crimes.
In related news, Amazon's Ring smart doorbell division is denying that it has fallen victim to a ransomware attack by a group called ALPHV, which is known to use Blackcat. However, leaked internal chats suggest that Ring's security teams are working on something.
Newman, Lily Hay, Ransomware Attacks Have Entered a ‘Heinous’ New Phase, Wired, 13 March 2023. Available online at https://www.wired.com/story/ransomware-tactics-cancer-photos-student-records/.
Truță, Filip, Amazon’s Ring Denies Hackers’ Claims of Ransomware Infection, Bitdefender blog, 15 March 2023. Available online at https://www.bitdefender.com/blog/hotforsecurity/amazons-ring-denies-hackers-claims-of-ransomware-infection/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Emotet Bloats Files to Avoid Detection
Emotet, a botnet operation which originally started as a banking trojan back in 2014, has emerged again after a three-month hiatus, according to analysts at Trend Micro. To date, the Emotet operators have built three different botnets, known as Epochs 1, 2 and 3, but in the last few weeks Epoch 4 has emerged, delivering malmails to victims.
The primary infection technique is the use of macros in malicious Microsoft Office documents. While Microsoft disabled the execution of macros in files which bear the Mark of the Web, the document template employs social engineering techniques to trick the user into enabling macros. The Emotet crew have also taken to binary padding the documents, increasing the file size to well over 500 MBytes in order to avoid being scanned by anti-malware products - this will work because the padding comprises only 00 bytes, so that the compressed version originally downloaded is very much smaller.
The document macro will download a ZIP file from any of seven C2 servers, then extract the contents to a folder before using regsvr32.exe to load a DLL file in order to infect the victim machine. Once the machine is infected, Emotet will run infostealer and spam relay routines, which it creates by creating a copy of the certutil.exe utility, starting it in a suspended state and then replacing its code by process hollowing.
The increasing use of evasion and anti-forensic techniques highlights the importance of security education, training and awareness; alert and suspicious users really are the last line of defence against these kinds of attacks.
Kenefick, Ian, Emotet Returns, Now Adopts Binary Padding for Evasion, blog post, 13 March 2023. Available online at https://www.trendmicro.com/en_us/research/23/c/emotet-returns-now-adopts-binary-padding-for-evasion.html.
Infostealers Spread to Crackers via AI-Generated YouTube Videos
Just about the most vulnerable users on the Internet are those who want to use pirated copies of expensive software by cracking the copy protection and licence-checking features of these programs. The web is rife with malware binaries which claim to crack popular programs, but which really infect the naive victim's machine.
By now, these victims must be getting gun-shy, so often are they infected (although they may not even realize it, in some cases). As a result, simple Google ads and forum posts are decreasingly effective, and the malware operators are looking for new ways to social-engineer their victims into downloading their warez.
Their latest technique, according to CloudSEK researchers, is to use YouTube videos to appeal to the victims; after all, real people must be more trustworthy than featureless and anonymous ads, right? But actually, the videos do not feature real people at all - they are generated by artificial intelligence platforms like Synthesia and D-ID, with facial features designed to appeal to the victims, and pretend to be tutorials on how to download cracked versions of software products like Photoshop, Premiere Pro, AutoCAD and others.
In order to reach as many victims as possible, as quickly as possible, the hackers will use a variety of techniques such as phishing to take over popular YouTube accounts - ideally, with 100,000 subscribers or more. They then upload their fake video(s), adding fake comments to lend credibility to the content, and using region-specific SEO tags to improve the video's search engine rankings. For a popular YouTube channel, it will not take long for the channel owner to discover the hack and regain control, but if the video remains online for even a few hours, they can still infect hundreds of victims. On less active channels, the videos can remain online for months at a time, especially if the channel owner simply never bothers to reclaim their channel.
This entire process is highly automated, making it an efficient operation. Typically, the malware payload will be an infostealer such as Vidar, Redline or Raccoon, and it will plunder the victim's credentials, cryptocurrency wallets and other applications.
M, Pavan Karthick and Deepanjli Paulraj, Threat Actors Abuse AI-Generated Youtube Videos to Spread Stealer Malware, blog post, 13 March 2023. Available online at https://cloudsek.com/blog/threat-actors-abuse-ai-generated-youtube-videos-to-spread-stealer-malware.
Free Economics Glossary
Courtesy of security maven Robert Slade comes a highly useful resource for cybersecurity management professionals: a glossary of economics terms. Given that a common complaint of boards and C-suites is that security wonks just don't understand business, this could be a way of fighting back. Granted, it is restricted to purely economics terms - from 'absolute advantage' to 'zero-sum game' - and doesn't cover wider business jargon, but then, so much of that is mal-adapted from the tech world anyway (exhibit 1: the way business has adopted the term "agile", perverting it along the way).
Uncredited, The A to Z of economics, online glossary, undated. Available online at https://www.economist.com/economics-a-to-z.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Fake ChatGPT Extension Steals Facebook Ad Accounts
A few weeks ago we reported that hackers were capitalizing on the enormous public interest in ChatGPT to create fake websites as well as fake ChatGPT apps which would install infostealers such as Redline, Aurora and Lumina. Now, AV firm Guardio has found and analyzed yet another example being promoted via Facebook sponsored posts. This time it is a Chrome extension which claims to provide - and in fact is called - "Quick access to Chat GPT".
The extension is actually a trojan horse, in that it does exactly what it promises, by providing an interface to the official ChatGPT API - but it is also a browser-based infostealer. Once installed, it will steal cookies for any active sessions, and also will take over the victim's Facebook account. What is particularly interesting is that, once the stealer has gained access to a high-profile Facebook business account, it will use it to create more sponsored posts, promoting its own installation at the expense of the victim. And because the extension has full access to the browser, it can also make use of an authenticated session to the Meta Graph API and can perform a variety of other actions.
The data harvested will likely be sold off - including any ChatGPT queries the extension sends on behalf of the victim. But possibly the big payoff will be the full access to Facebook business accounts that the exension gets for the attackers.
Guardio's blog post provides a detailed analysis of the malicious extension's techniques and procedures, as well as IOC's.
Tal, Nati, “FakeGPT”: New Variant of Fake-ChatGPT Chrome Extension Stealing Facebook Ad Accounts with Thousands of Daily Installs, blog post, 9 March 2023. Available online at https://labs.guard.io/fakegpt-new-variant-of-fake-chatgpt-chrome-extension-stealing-facebook-ad-accounts-with-4c9996a8f282.
BatLoader Continues to Evolve
eSentire's Threat Response Unit has produced a report detailing their monitoring of the continued evolution of BatLoader. We first reported on BatLoader back in November of last year; at that time, VMware's Carbon Black MDR analysts had identified it as being a derivative of the earlier Zloader, which in turn traces back to the old Zeus banking trojan.
eSentire watched the BatLoader operators throughout February as they registered a number of domains which typosquat on popular application and brand names by simply adding a few characters on the end of the brand name, e.g. adobe-l[.]com as opposed to adoble.com. Using this technique, they are spoofing Adobe, Tableau, Spotify, Zoom and - inevitably (because it works!) - ChatGPT. These domains are then used to host fake download pages which deliver Windows Installer files masquerading as the related applications, with the pages being promoted via Googe Search ads.
In addition to installing the desired free application, the modified Windows Installer file contains custom actions which will execute commands - for example, installing Python (which seems to have replaced the previous versions' use of PowerShell), running pip to install other packages, and running Python programs. In this incarnation of BatLoader, the Python scripts use a technique found via Stack Overflow to achieve privilege escalation. As before, the loader is dropping payloads such as Ursnif and Cobalt Strike and, most recently, Vidar Stealer.
The eSentire TRU write-up provides recommended mitigations - primarily improved security education, training and awareness - as well as IOC's.
eSentire TRU, BatLoader Continues to Abuse Google Search Ads to Deliver Vidar Stealer and Ursnif, blog post, 9 March 2023. Available online at https://www.esentire.com/blog/batloader-continues-to-abuse-google-search-ads-to-deliver-vidar-stealer-and-ursnif.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Record DDoS Attack Reaches 900 Gbps
DDoS (Distributed Denial of Service) attacks continue to grow in intensity as botnet operators add more compromised systems to their networks. Now Akamai reports a record-breaking DDoS attack - the largest ever launched against one of their customers in the Asia-Pacific (APAC) region, with the attack traffic peaking at 900.1 gigbits per scond and 158.2 million packets per second. The attack was not just intense, but was also short-lived, sustaining the peak for less than a minute and with the overall attack lasting just a few minutes.
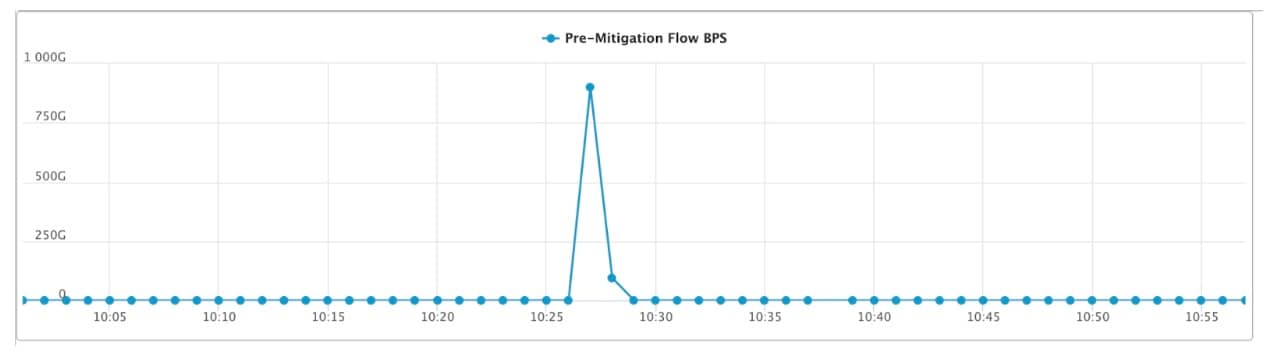
(Credit: Akamai)
The attack was distributed across all 26 of Akamai's scrubbing centers, although Hong Kong, Tokyo, São Paulo, Singapore, and Osaka saw the most traffic. 48% of the traffic was in-region. Akamai reports that, thanks to its proactive DDoS capabilities, there was no collateral damage.
Sparling, Craig, Akamai Mitigates Record DDoS Attack in Asia-Pacific (900 GBps), blog post, 8 March 2023. Available online at https://www.akamai.com/blog/security/record-breaking-ddos-in-apac.
APT Targets SonicWall Appliances
Firewalls are particularly attractive targets for threat actors; after all, compromising a firewall opens up the possibility of many new attacks on the network the firewall is defending, and there's also an opportunity to capture all kinds of useful traffic flowing through the firewall to and from a network the attacker cannot yet reach. Firewalls therefore have to be treated as bastion hosts and staunchly defended against attack - they are absolutely not a set-and-forget "solution" (I hate that word!).
An example of this is a campaign recently identified by Mandiant, working in partnership with SonicWall's Product Security and Incident Response Team (PSIRT). Analysis of a compromised machine revealed a number of malware files which give the attacker highly privileged access to the appliance, as well as allowing long-term persistence. The files mostly consist of bash scripts, along with one ELF executable which is a variant of the TinyShell backdoor.
| Path | Hash | Function |
|---|---|---|
| /bin/firewalld | e4117b17e3d14fe64f45750be71dbaa6 | Main malware process |
| /bin/httpsd | 2d57bcb8351cf2b57c4fd2d1bb8f862e | TinyShell backdoor |
| /etc/rc.d/rc.local | 559b9ae2a578e1258e80c45a5794c071 | Boot persistence for firewalld |
| /bin/iptabled | 8dbf1effa7bc94fc0b9b4ce83dfce2e6 | Redundant main malware process |
| /bin/geoBotnetd | 619769d3d40a3c28ec83832ca521f521 | Firmware backdoor script |
| /bin/ifconfig6 | fa1bf2e427b2defffd573854c35d4919 | Graceful shutdown script |
The main malware script, /bin/firewalld, starts by executing the TinyShell backdoor with command-line arguments that get it to create a reverse or 'shovel-back' shell which connects outwards to the attacker's C2 server at a specific date/time. From there, it scans every file on the system, likely to perform credential theft, executing SQL commands on the sqlite3 database /tmp/temp.db (which contains session information including hashed credentials) and also executing other components. The /bin/firewalld script is started by /etc/rc.d/rc.local in the event of a reboot.
/bin/iptabled is essentially the same script, presumably in order to provide a degree of resilience. The two scripts each check to see if the other is running, and starts it if it is not. You will notice the innocuous filenames here - these are exactly the kind of filenames you would expect to see on a firewall machine - although not in these locations.
However, a firmware update could overwrite these files. In order to avoid that, the /bin/geoBotnetd script checks every ten seconds for a new firmware upgrade to appear at /cf/FIRMWARE/NEW/INITRD.GZ, and if it does, effectively re-packages it to contain the malware scripts, ready for installation. Finally, the main malware script also modifies the main SonicWall binary firebased to call the /bin/ifconfig6 script on shutdown - this simply brings the eth0 network interface down, sleeps for 90 seconds and then shuts the system down as it normally would. Presumably this is a quick fix for some problem the attackers encountered.
The techniques used in this campaign are similar to those used in previous attacks by Chinese threat actors on Pulse Secure VPN devices as well as attacks on Fortinet devices. For this reason, Mandiant suspects a Chinese threat actor, which it currently tracks as UNC4540, is behind this campaign.
Lee, Daniel, Stephen Eckels and Ben Read, Suspected Chinese Campaign to Persist on SonicWall Devices, Highlights Importance of Monitoring Edge Devices, blog post, 8 March 2023. Available online at https://www.mandiant.com/resources/blog/suspected-chinese-persist-sonicwall.
Tips on Avoiding LDAP Injection Attacks
LDAP - the Lightweight Directory Access Protocol - is often used as part of authentication by web applications, especially for single sign-on across disparate applications. This makes LDAP injection - a close relative of the better known SQL injection - an attractive technique for attackers; they can use it to enumerate user accounts or credentials, log in without a valid password or even perform privilege escalation attacks.
A nicely-written short blog post from Trend Micro gives a brief rundown with examples of LDAP injection techniques, as well as advice on mitigation.
Trend Micro DevOps Resource Center, How to Avoid LDAP Injection Attacks, blog post, 9 March 2023. Available online at https://www.trendmicro.com/en_us/devops/23/c/avoid-ldap-injection-attacks.html.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Acer Confirms Breach
It seems like only yesterday we reported on the alleged exfiltration of 160 GB of assorted product information and strategic presentations from Taiwanese tech manufacturer Acer. (Oh, wait - it was.)
Now Acer has confirmed the breach, adding that they had "detected an incident of unauthorized access to one of our document servers for repair technicians. ... While our investigation is ongoing, there is currently no indication that any consumer data was stored on that server". It seems that the breach is confined to Acer's intellectual property.
Hardcastle, Jessica Lyons, Acer confirms server intrusion after miscreant offers 160GB cache of stolen files, The Register, 8 March 2023. Available online at https://www.theregister.com/2023/03/08/acer_confirms_server_breach/.
Microsoft Introduces Local Security Authority Protection
The Local Security Authority (LSA) Subsystem process - lsass.exe - is responsible for enforcing the security policy on a Windows system. It authenticates users logging on, handles password changes and creates access tokens. In short, if an attacker can compromise this process, they own you and the machine, and possibly a chunk of your network.
The latest pre-release, Windows 11 Insider Preview Build 25314, released yesterday to the Canary Channel, adds a new feature called Local Security Authority protection. This prevents an entire class of attacks by preventing unsigned drivers and plugins from loading into the LSA. This could potentially cause some incompatibilities, but Microsoft says the company will audit for a period of time to check for these and if no incompatibilities are detected, LSA protection will automatically be turned on.
The setting for this can be seen in the Windows Security application under "Device Security" -> "Core Isolation".
Another security improvement in this build is the disabling of the Remote Mailslot Protocol. Mailslots were the NetBIOS equivalent of the UDP protocol - a simple, connectionless protocol - and hardly anything uses it these days.
Langowski, Amanda and Brandon LeBlanc, Announcing Windows 11 Insider Preview Build 25314, blog post, 8 March 2023. Available online at https://blogs.windows.com/windows-insider/2023/03/08/announcing-windows-11-insider-preview-build-25314/.
Jenkins Vulnerabilities Allow RCE
Jenkins is an extremely versatile open-source cloud automation and orchestration server which is a near-essential part of the DevOps pipeline. Perhaps the key to its flexibility is its support for plugins. Now researchers at Aqua Nautilus have discovered a chain of vulnerabilities which they have dubbed CorePlague, in Jenkins Server and Update Center. Exploitation of these vulnerabilities - CVE-2023-27898 and CVE-2023-27905 - can allow an unauthenticated attacker to execute arbitrary code on the Jenkins server, leading to complete compromise of the system.
The key to the vulnerabilities is a stored XSS exploitable by a Jenkins plugin with a malicious core version, which the attackers upload to the Jenkins Update Center. The vulnerability will be triggered when the victim opens the Available Plugin Manager on their Jenkins Server, when the XSS allows the attacker to run arbitrary code using the Script Console API. The exploitation does not require the manipulated plugin to be installed - the malicious plugin could simply be on the public Jenkins Update Center.
The Jenkins team were notified back in January, and have issued patches for both the Jenkins Server and for the Jenkins Update Center. Users should check their server versions and update.
Goldman, Ilay and Yair Kadkoda, CorePlague: Severe Vulnerabilities in Jenkins Server Lead to RCE, blog post, 8 March 2023. Available online at https://blog.aquasec.com/jenkins-server-vulnerabilities.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
German and Ukrainian Police Bust DoppelPaymer Ransomware Gang
In late February, the German Regional Police (Landeskriminalamt Nordrhein-Westfalen) and the Ukrainian National Police (Націона́льна полі́ція Украї́ни), arrested suspected core members of the DoppelPaymer ransomware threat actor. The gang, which has ties to Russia, has been extorting large companies since 2019 - its most prominent victims include the UK's National Health Service and Duesseldorf University Hospital, the latter case resulting in the death of a woman who had to be urgently taken to another city for treatment.

Dirk Kunze, head of the cybercrime department of the North Rhine-Westphalia state police, said at least 601 victims had been identified worldwide, with US victims having paid at least $US42.5 million between May 2019 and March 2021. The group specialized in "big game hunting" and operated a professional recruitment operation, asking candidates for references for past cybercrimes and offering 'employees' paid vacations.
German offcers raided the house of a German national who is believed to have been a key player in the group, and seized equipment which is being analyzed in order to determine his exact role. Ukrainian police officers interrogated a Ukrainian national following a simultaneous raid, and also searched two locations in Kiev and Kharkiv, seizing electronic equipment for forensic examination.
Three further suspects are beyond the reach of European law enforcement: Russian citizens Igor Turashev, 41, and Irina Zemlyanikina, 36, as well as Igor Garsin, 31, who was born in Russia but whose nationality is unknown. Turashev is also wanted by US authorities for his part in attacks carried out with BitPaymer, a predecessor to DoppelPaymer.
Europol Media Office, Germany and Ukraine hit two high-value ransomware targets, media release, 6 March 2023. Available online at https://www.europol.europa.eu/media-press/newsroom/news/germany-and-ukraine-hit-two-high-value-ransomware-targets.
Jordans, Frank, European police, FBI bust international cybercrime gang, news report, 6 March 2023. Available online at https://apnews.com/article/germany-russia-europol-fbi-cybercrime-ukraine-ransomware-f0652c5ef0a281738a50ee02e4191413.
Intensive Spam Campaign Gets Woman Arrested
A Sydney woman was arrested by the Australian Federal Police at her home on 1 March, appearing before Penrith Local Court the following day where she was bailed to reappear on 11 April 2023. What got her arrested was a spamming campaign in which she is alleged to have used multiple domains to send - wait for it - 32,397 emails over a 24-hour period until she was arrested. That's more than an email every three seconds; isn't automation wonderful?
An ordinary spam campaign would not have triggered such rapid action, but all these emails were sent to the office of a Commonwealth Member of Parliament (hence the AFP taking an interest). The volume of emails impaired workers from operating office systems and prevented members of the public making contact with the office.
The woman was charged with one count of committing unauthorised impairment of electronic communication, contrary to section 477.3 of the Criminal Code Act 1995 (Cth). The maximum penalty for this offence is 10 years’ imprisonment. Further charges have not been ruled out.
AFP Media, Woman charged for alleged cyber-attack against Federal MP, media release, 2 March 2023. Available online at https://www.afp.gov.au/news-media/media-releases/woman-charged-alleged-cyber-attack-against-federal-mp.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Privileged Insider Defrauds Australian Museum
Australian Federal Police have executed a search warrant at the Macquarie Park (Sydney) home of a man, 23, arresting him in connection with an alleged cybercrime-enabled fraud against the Australian National Maritime Museum (ANMM). Police seized a number of electronic items including a laptop, hard drives and a mobile phone for forensic analysis.

Photo Credit:AFP
The man appeared at Burwood Local Court on Friday 3 March on several charges:
- Two counts of unauthorised access and modification with intent to commit a serious computer offence, contrary to section 477.1 of the Criminal Code Act 1995 (Cth),
Four counts of dishonestly obtaining or dealing in personal financial information, contrary to section 480.4 of the Criminal Code Act 1995 (Cth), and
Five counts of dishonestly obtaining property by deception, contrary to section 192E of the Crimes Act 1900 (NSW).
The AFP will allege that the man was a contracted IT support worker for a third-party service provider, and that he accessed ANMM's accounts payable system and changed bank account details stored in the system to his own. It is further alleged that he obtained the financial details of several individuals and businesses, using the credit card information to make a series of unauthorised purchases.
In November 2023, the ANMM detected anomalies in provided financial information for some contractors, and called in independent forensic investigators who identified the extent of the issue. The AFP was then notified, and linked the alleged offender to the unauthorised access to several systems and servers.
AFP Detective Leading Senior Constable Clare Yammine said trusted insiders remained a very real threat to the Australian community, and initial estimates of the total value of money allegedly diverted in this matter at $90,000.
“The AFP is committed to preventing and prosecuting cybercrime and fraud committed against Australians and businesses,” Leading Sen-Constable Yammine said.
AFP Media, Third-party IT contractor arrested for $90,000 fraud, media release, 4 March 2023. Available online at https://www.afp.gov.au/news-media/media-releases/third-party-it-contractor-arrested-90000-fraud.
Yet Another IoT Thing to Worry About: EV Charge Points
Researchers at specialist energy network security firm Saiflow have found that cyber attackers can disable electric vehicle (EV) charge points and cause a denial of service by exploiting versions of the Open Charge Point Protocol (OCPP) that use WebSocket communications. OCPP is used for communication between the charge points (CP) and a central system management service (CSMS) which together form a charging station network.
The attack exploits two new vulnerabilities that were found in the OCPP standard. First, the standard does not specify how to handle more than one connection to a single charge point simultaneously. As a consequence, an attacker can disrupt the current connection between the CP and the CSMS by simply opening an additional "new" connection to the CSMS. To do this, the attacker also has to exploit a second vulnerability: weak authentication in OCPP.
SaiFlow's researchers tested this approach on multiple CSMS providers; some would close the original CP connection, effectively disconnecting the CP, while others will keep the connection but not use it. Both cases expose the charging station network to a DDoS attack, but the second case will also fail to notify the charge point operator that something is wrong. The attack can also expose some sensitive and personal information.
These vulnerabilities exist in OCPP 1.6J, which is the most commonly deployed; OCPP 2.0.1, which is only now rolling out, could also be vulnerable if authentication is not properly implemented.
Saposnik, Lionel Richard and Doron Porat, Hijacking EV Charge Points to Cause DoS, blog post, 1 February 2023. Available online at https://www.saiflow.com/hijacking-chargers-identifier-to-cause-dos/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Welcome to today's daily briefing on security news relevant to our CISSP (and other) courses. Links within stories may lead to further details in the course notes of some of our courses, and will only be accessible if you are enrolled in the corresponding course - this is a shallow ploy to encourage ongoing study. However, each item ends with a link to the original source.
News Stories
Mustang Panda Deploys New Backdoor
Mustang Panda (also identified as TA416, RedDelta and BRONZE PRESIDENT) is a China-based cyber-espionage threat actor that may have been operating since 2014, target a wide range of organizations in S.E. Asia, the US and Europe. Now ESET researchers report that the group has been running a campaign since January 2023 which is utilizing a new backdoor which seems to be completely original and not descended from existing malware or other publicly-available projects. The new malware, dubbed MQsTTang, is much simpler than the group's previous tools, consisting of only a single stage and using only the most basic evasion techniques.
The backdoor gets its name from its somewhat novel use of the standardized IoT messaging protocol MQTT for its C2 communication; as a side benefit, this allows the group to hide its C2 servers behind legitimate brokers. It provides only fairly limited functionality - at this stage, just remote command execution, with output sent back to the attackers.
The malware is distributed via spearphishing malmails, typically as RAR archives containing only a single executable, which usually has a name related to diplomacy and passports, suggesting the targets are political and government organizations. ESET has seen unknown entities in Bulgaria and Australia in their telemetry, but believe the campaign is targeting a Taiwanese government institution as well as others in Asia and Europe - Mustang Panda has dramatically increased its activities there since the Russian invasion of Ukraine.
The ESET report provides a detailed analysis along with a mapping to MITRE ATT&CK techniques as well as IOC's.
Côté Cyr, Alexandre, MQsTTang: Mustang Panda’s latest backdoor treads new ground with Qt and MQTT, blog post, 2 March 2023. Available online at https://www.welivesecurity.com/2023/03/02/mqsttang-mustang-panda-latest-backdoor-treads-new-ground-qt-mqtt/.
Cryptomining Campaign Targets Redis Deployments
Redis is a popular in-memory NoSQL key-value database that is popular for real-time analytics and sharing session data in web server farms and cloud environments. Now Cado Labs researchers report on a cryptoacking campaign which targets insecure Redis deployments in order to install the XMRig cryptominer.
The basic initial access exploit is very simple: the insecure Redis instance is given a command which creates a simple cron job that runs every two minutes. This job will run the curl command to fetch a shell script, save it as .cmd and then invoke bash to execute it. What is novel about this is that it fetches the file from the free and open source transfer.sh command line file transfer service, rather than historically popular services like pastebin.com.
Once the script is running, it starts by un-hardening the system, disabling SELinux and setting the resolver to use public DNS servers. It also removes other cron jobs and frees up as much memory as possible, probably for use by XMRig - however, to do this it forces the kernel to drop some in-memory data structures which could severely impact performance for the legitimate applications on the system.
From there, ths script clears log files, reconfigures iptables firewall rules, kills any competing cryptominers and downloads binaries for pnscan - which it will use to propagate itself - and XMRig, which then sets about mining Monero cryptocurrency.
The Cado Labs report provides more detail, along with IOC's.
Muir, Matt, Redis Miner Leverages Command Line File Hosting Service, blog post, 2 March 2023. Available online at https://www.cadosecurity.com/redis-miner-leverages-command-line-file-hosting-service/.
These news brief blog articles are collected at https://www.lesbell.com.au/blog/index.php?courseid=1. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.