Les Bell
User blog: Les Bell
A "cyber attack" - likely a ransomware attack - has paralysed a Western Sydney radiology clinic, leaving patients with cancelled appointments and no access to results of scans and tests.

Channel 9 News reports that Quantum Radiology, which as 10 practices across Western Sydney and the Central Coast, failed to notify patients, simply cancelling appointments without explanation and closing practices with a posted notice attributing the closure to an "unforeseen IT issue". The firm has called in police and the Australian Cyber Security Centre as it grapples with the issue, which has seen their practices closed for over a week now.
This is a textbook example of how not to deal with a ransomware attack - we know from previous cases that organizations which are open and proactive in notifying stakeholders recover well after such attacks. Affected customers will tend to take a more sympathetic view in such cases, correctly identifying the ransomware gangs as the villains. But keeping customers in the dark - especially when many are doubtless anxious about their health - is now resulting in angry patients appearing on TV; never a good look.
Meanwhile news has leaked of an earlier attack on a Brisbane chain of general practices, Top Health Doctors, which suffered a breach back in September. The breach affected approximately 5,500 patients, but the chain apparently notified them reasonably promptly, containing subsequent publicity. The breach has only come to public attention via the gazetting of a data matching program by Services Australia to identify any subsequent breaches which made use of a patient's Medicare number or Centrelink Reference Number.
I think we can now put to rest any notion that ransomware gangs will give personal health information a wide berth.
Services Australia, NOTICE OF A DATA MATCHING PROGRAM – SERVICES AUSTRALIA AND TOP HEALTH DOCTORS CUSTOMERS AFFECTED BY SEPTEMBER 2023 DATA BREACH, Australian Government Federal Register of Legislation, November 2023. Available online at https://www.legislation.gov.au/Details/C2023G01220.
Theocharous, Mikala, Patients in the dark after cyberattack forces closure of radiology clinic, 9 News, 30 November 2023. Available online at https://www.9news.com.au/national/quantum-radiology-hit-by-cyberattack-patients-in-the-dark/81428039-3254-45d2-94b3-872cb85e3164. Related video at https://www.youtube.com/watch?embed=no&v=-jmaWBKd27Y.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
In light of a spate of successful attacks exploiting vulnerabilities in web management interfaces, the US Cybersecurity & Infrastructure Security Agency has issued a "Secure by Design" alert to urge software vendors to adopt two fundamental principles in the design and development of their products:
- Take Ownership of Customer Security Outcomes
- Embrace Radical Transparency and Accountability
The first principle requires vendors to invest in key security areas such as application hardening, application features and default configuration settings. For the latter, especially, the alert recommends enforcing best practices - for example, if best practice requires shielding a system from the public internet, then the default configuration should:
- disable the product's web interface by default and provide a "loosening guide" that itemizes - in both technical and non-technical language - the risks that come with overriding the default
- configure the product so that it does not operate while in a vulnerable state, such as when directly exposed on a public IP address
- warn the administrator that overriding the default behaviour may introduce signficant risk to the organization
The alert also suggests conducting field tests to understand how customers actually deploy products in their unique environments, in order to prevent unrealistic expectations of customers' skills and abilities on the part of the developers. And, of course, developers should consistently enforce authentication throughout the product, especially on highly trusted interfaces such as administrator portals.
The second principle requires vendors to lead with transparency when disclosing product vulnerabilities, and to perform thorough investigation of vulnerabilities to correctly document CVE entries and share what they learn across industry.
CISA, Secure by Design Alert: How Software Manufacturers Can Shield Web Management Interfaces From Malicious Cyber Activity, Secure by Design Alert, 29 November 2023. Available online at https://www.cisa.gov/resources-tools/resources/secure-design-alert-how-software-manufacturers-can-shield-web-management-interfaces-malicious-cyber.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
The UK's National Cyber Security Centre, in collaboration with 23 international partners and a number of industry organizations, has released the first version of its Guidelines For Secure AI System Development. The document is aimed primarily at providers of AI systems which use models hosted by an organisation, or which make use of external API's, and provides advice for each phase of development, from design through development and deployment to operation.

Secure design starts with raising all participants' awareness of the threats and risks facing AI systems and in particular training developers in secure coding techniques and secure and responsible AI practices. It then proceeds through the modeling of threats, designing for security as well as functionality and performance and considering security benefits and tradeoffs in the selection of the AI model.
Secure development begins with the assessment and monitoring of security of the AI supply chains across the system life cycle, then identifying, tracking and protecting the AI-related assets - the models, data (including user feedback), prompts, software, documentation, logs and assessments. The model itself, along with the data and prompts should be documented, including security-relevant information such as the sources of training data, and guardrails. It's also important to identify, track and manage technical debt, which can be more challenging in this context than for most software because of rapid development cycles and a lack of well-established protocols and interfaces.
Secure deployment depends upon the security of the underlying infrastructure, such as access controls on API's, as well as the models and data, not to mention the training and processing pipelines. The model needs to be protected continuously, against a range of both direct attacks, such as by acquiring the model weights, and indirect attacks such as querying the model via an application or API. Incident response procedures will also need to be developed, and systems will have to be subjected to security evaluation and assessment such as red-teaming. Ideally, the most secure settings will be integrated into the system as the only option, and users must be advised about where and how their data might be used, accessed or stored (e.g. reviewed by employees or contractors, or used for model retraining).
Finally, secure deployment will require monitoring of the system's behaviour to identify not just sudden, but also gradual, changes in behaviour which affect security. The system's inputs will have to be monitored and logged to allow investigation and remediation as well to meet compliance obligations. Updates will also follow a similar process to the original development, e.g. testing and evaluation, reflecting the fact that changes to data, models or prompts can lead to changes in system behaviour. Finally, developers should participate in appropriate sharing of best practices as well as vulnerability disclosure procedures.
The Guidelines themselves are quite short and pitched at a level suitable for all stakeholders, from managers and risk owners down to developers and data scientists. However, a list of additional resources including standards, guidance documents and open-source tools and test frameworks allow architects and developers to delve more deeply into the key concerns and activities.
UK National Cyber Security Centre, Guidelines for secure AI system development, web document, 27 November 2023. Available online at https://www.ncsc.gov.uk/collection/guidelines-secure-ai-system-development.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
A recent report released by trust management firm Vanta confirms a gloomy picture of the current state of cybersecurity across businesses in general, with two-thirds of businesses saying they need to improve security and compliance measures and almost one in four (24%) describing their security and compliance strategy as reactive.

Vanta's State of Trust 2023 Report, based on research conducted on their behalf by Sapio Research, surveyed the behaviors and attitudes of 2,500 business leaders across Australia, France, Germany, the UK and U.S. in order to understand the challenges and opportunities they face. In short: the expansion of attack surfaces in a post-pandemic world of hybrid work, coupled with shrinking teams and budgets, not to mention the rapid rise of generative AI, are fueling an urgent need for companies to raise their security posture - and to be able to demonstrate this to customers, investors and suppliers.
For companies of all sizes, limited visibility of risks, coupled with resource constraints, pose a challenge to security improvements. Only four in ten organizations rate their risk visibility as strong. But one in four has downsized IT staff, and 60% have already reduced IT budgets or are planning to do so as they grapple with an increasingly challenging global economic environment.
Two thirds of respondents say that customers, investors and business partners are increasingly seeking assurance of their security capabilities. While 41% provide internal audit reports, 37% supply third party audits, and 36% complete security questionnaires, one in eight (12%) admits they do not or canot provide evidence when it is requested, leading them to miss out on business opportunities. According to the report:
- Businesses spend an average of 7.5 hours per week – more than 9 working weeks a year – on achieving security compliance or staying compliant.
- Over half (54%) are concerned that secure data management is becoming more challenging with AI adoption with 51% saying that using Generative AI could erode customer trust.
- The two biggest barriers to proving and demonstrating security externally are a lack of staffing and lack of automation to replace manual work.
- Only 9% of businesses’ IT budgets are dedicated to security, with 1 in 3 leaders saying their IT budgets are continuing to shrink.
- Identity and access management and data processing that doesn’t comply with regulations are the two biggest blind spots for organizations.
Those who do make efforts on security report positive benefits; a majority 70% of leaders say that a better security and compliance strategy positively impacts their businesses thanks to stronger customer trust, while nearly three in four (72%) agree that a better security and compliance strategy would make them more efficient. Key to achieving this is automation; an overwhelming 83% of businesses have or plan to increase their use of automation, particularly for reducing manual work and streamlining vendor risk reviews and onboarding.
In order to achieve this, they are looking to artificial intelligence and machine learning, with 77% of businesses already or planning to use AI/ML to detect high risk actions. Respondents believe the biggest potential of AI will be improving the accuracy of security questionnaire responses (44%), eliminating manual work (42%), streamlining vendor risk reviews and onboarding (37%), and reducing the need for large teams (34%).
The survey results illustrate the different viewpoints around the world:
- Respondents in Australia are the most concerned about Generative AI’s potential impact on customer trust.
- Organizations in Australia are least likely to be able to provide proof of compliance to customers.
- 76% of leaders in France say they need to improve security and compliance, the highest of all markets.
- UK leaders are more concerned with keeping up to date with evolving regulations than any other market.
- Germany is one of the most likely to say that the volume of standards and regulations is a barrier to maintaining a robust security program.
- Leaders in the U.S. are most likely to delay entering new markets due to compliance requirements, admitting they’re not prioritizing compliance due to the financial investment.
- Companies in the U.S. believe they could save at least 3 hours a week by automating security and compliance tasks – the highest of any country.
While all this paints a somewhat gloomy picture, I'd say there are some important lessons to be gleaned. The first is for companies to focus on security first, and worry about compliance second. Focusing on compliance is putting the cart before the horse, and often leads to a checkbox mentality that does little to actually improve security. (I suspect this might underlie some of the attitudes reflected above from Australia and Germany.)
An insightful comment I saw recently puts it well:
Effective information security programs mitigate the risks that you face to a level that you can accept.
Compliance programs mitigate the risks that you present to others, to a level that they can accept.
You cannot achieve the second without the first. Now, having said that, compliance ultimately is important, especially in enabling new business relationships. The answer is to make use of a security framework - such as the NIST Cybersecurity Framework - which can then be used to cross-reference each control implemented against relevant standards - such as ISO 27001, HIPAA, etc. - in order to demonstrate compliance.
Having gotten this process under way, companies then will be in a much better position to take advantage of the automated reporting, for both internal management and external compliance, offered by Vanta and similar companies.
Uncredited, State of Trust Report 2023, Vanta Inc., 8 November 2023. Available online at https://www.vanta.com/downloads/the-state-of-trust-report-2023.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
As we mentioned on Monday, Australia's Minister for Home Affairs and Cyber Security * is expected today to release the Government's long awaited cybersecurity strategy. The strategy adds another $A586.9 million to an existing $A2.3 billion in cybersecurity funding which will run until the year 2030. (See Update, below, for a link to the strategy document.)

Changes for Critical Infrastructure and Telcos
The plan aims to better protect critical infrastructure; following last year's privacy breach at telco Singtel Optus, security regulation of telecommunications providers will be moved from the Telecommunications Act to the Security of Critical Infrastructure Act, "commensurate with the criticality and risk profile of the sector". It seems obvious that virtually all the other sectors of critical infrastructure are dependent on telecommunications - this should have been a no-brainer years ago.
Another likely consequence of the Optus breach is a winding back of laws which require telcos to retain enormous quantities of customer data. Several breaches have led to affected customers having to obtain new drivers licences and other identity documents because their numbers had been disclosed - but once a new customer has verified their identity, is there any real need to retain the information that was used for that purpose? When it leaks, it weakens the value of such data for verification anyway - so let state and Commonwealth agencies that need to retain that data and provide an API which can be used for verification, then log the fact that verification was provided.
Similarly, the strategy will review Commonwealth data retention requirements and, based upon the outome, will explore options to minimise and simplify data retention requirements. This will doubtless come as a relief to the telcos which have been retaining vast quantities of traffic metadata in response to requirements introduced in 2015.
As we regularly point out, once retained information is no longer of any use, it is no longer an information asset and - from a privacy and risk management perspective - can turn into an information liability.
The healthcare sector is also being prioritized, and will benefit from a new $A9.4 million platform for the sharing of threat intelligence, in a program that could be rolled out to other sectors. Table-top "wargaming" exercises will also be expanded to include the aviation, finance and telco sectors.
Protecting Individuals
In part to reduce the amount of personal information an individual has to disclose in order to verify their identity, the government is aiming to expand its Digital ID program - a smartphone app which, as far as I can tell, seems to use exactly the types of API I posit above to provide an on-device verification of personal identity, based upon government documents like drivers licence, Medicare card and passport, along with email address, data of birth and a photo ID.
There are also plans for new cyber awareness programs to better educate the public, presumably with the goal of reducing personal losses to online scams.
Small and Medium Businesses
However, perhaps the public can be best served by improving the posture of business. The strategy allocates $A290.8 million for this area, via awareness programs, along with the development of an incident response playbook for ransomware, along with a mandatory no-fault reporting scheme for ransomware attacks and payments. Concerns that some businesses were failing to disclose breaches for fear of a backlash from regulators, not to mention customers (think class action) has also led the government to consider the establishment of "safe harbour" legislation to ensure that such disclosures to a reporting scheme could not be used for other purposes.
This approach has worked well in aviation safety for decades, encouraging pilots, other crew and maintenance engineers to come forward with useful information about incidents which fortunately did not result in accidents. As long as such a program provided actionable information - rather than simply telling us what we already know - it could prove useful; perhaps the best use would be providing psychologists and behavioural specialists with insights as to why boards and senior management do not take cybersecurity seriously enough.
Small businesses will also get a new "resilience service" to assist with recovery in the aftermath of an attack, and - as mentioned on Monday - there will be a "cyber health-check" program to offer free, tailored security assessments to business owners. I seriously doubt that this will have much real impact, other than on the bank balances of those providing the "free" assessments.
There are already excellent new technologies available to businesses of all sizes in order to better protect both themselves and their customers - particularly phishing resistant authentication schemes like U2F security keys and FIDO2 authentication via passkeys. What we should be doing is assisting business to adopt them (perhaps via open-source development), rather than relying on long-deprecated techniques like SMS'ed verification codes. Hopefully, this will form part of the new strategy.
Growing the Workforce
As is usual for such strategies, a lot is made of the "skills gap" and a supposed workforce shortage. The government proposes to address this via more education in addition to prioritizing immigration for highly skilled cybersecurity professionals. Based on my conversations with security professionals around the world, this seems likely to miss the mark; bootcamp-style programs and certifications to rapidly train people with no experience are not producing workers of any actual use, while experienced security professionals are reporting that they are being passed over for relatively unskilled candidates seeking much lower salaries. If anything, cybersecurity is suffering something of a 'brain drain' as the necessary skills and experience are undervalued.
Finally - and we've heard this refrain before - the strategy aims to make Australia a "world leader" in cybersecurity by 2030: "We will advance the global frontier of cyber security. We will lead the development of emerging cyber technologies". Doubtless some of the submissions are by companies which dream of a future in which government funding will help them take their products to the next level and export them to an admiring world. Consumers who have had their personal information disclosed in a never-ending stream of breaches might, perhaps, have a more realistic view of Australia's security capabilities.
Grattan, Michelle, New cyber policy to harden defences against our ‘fastest growing threat’, The Conversation, 21 November 2023. Available online at https://theconversation.com/new-cyber-policy-to-harden-defences-against-our-fastest-growing-threat-218255.
Knott, Matthew, Hackers’ honeypot: customer data storage laws set to be wound back, Sydney Morning Herald, 21 November 2023. Available online at https://www.smh.com.au/politics/federal/hackers-honeypot-customer-data-storage-laws-set-to-be-wound-back-20231114-p5ejwt.html.
Manfield, Evelyn, Australian Cyber Security Strategy outlines how government plans to tackle cyber crime, ABC News, 21 November 2023. Available online at https://www.abc.net.au/news/2023-11-21/federal-government-cyber-safety-framework/103132226.
* That really should be "Cybersecurity" - there is no such thing as a "cyber", nor is "cyber" an adjective. The word derives from the ancient Greek κυβερνήτης (kubernetes or kybernetes), which referred to the steersman or pilot of a galley. The same word is the root of "governor" and "governance", but comes to us through the 1947 coinage of "cybernetics" by MIT mathematician Norbert Wiener to refer to the field of control and communication, both in the animal and the machine. So now you know better. Please don't "cyber all the things".
Update
The Strategy document has now been released, and is available at https://www.homeaffairs.gov.au/about-us/our-portfolios/cyber-security/strategy/2023-2030-australian-cyber-security-strategy.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Cloud applications employ a variety of software architecture patterns, but high among them is the microservices architecture, which links a number of intependently-running processes. The links can be by means of RESTful API's or via message-oriented middleware such as Amazon's Simple Queue Service, Google Cloud Pub/Sub and others. Among the open source offerings like RabbitMQ and OpenMQ is the Apache Project's ActiveMQ, a Java-based multi-protocol message broker which can connect a variety of clients using protocols such as AMQP and MQTT (which is widely used on the Internet of Things). ActiveMQ is also compatible with the Java Messaging Service API, making migration of earlier application code easy.

Now Trend Micro reports on an active campaign which exploits CVE-2023-46604, a remote code execution vunerability in the Java OpenWire protocol marshaller used by ActiveMQ. The vulnerability allows an attacker to manipulate serialized class types in the protocol to instantiate any class found on the classpath. This occurs because the OpenWire code fails to validate a throwable class type (used in exception handling).
The vulnerability is being used by a threat actor to download and install malware - primarily the Kinsing cryptominer. This particular campaign uses CVE-2023-46604 to instantiate a ProcessBuilder object, calling its start() method to execute a bash shell which uses either curl or wget to download a malicious installer script from a C2 server and execute it. Once the Kinsing malware is installed and running, it fetches further binaries and payloads from the C2 server. Interestingly, Kinsing then proceeds to search for and kill any competing cryptominers before adding a cron job which will download and run its bootstrap script every minute, ensuring it is always updated. It completes its infection by installing a rootkit which loads from /etc/ld.so.preload.
It then sets to work, using the infected machine's CPU resources to mine cryptocurrencies like Bitcoin, dragging the system performance down in the process.
The Kinsing operators are not the only ones exploiting CVE-2023-46604, which makes it all the more urgent for organizations using ActiveMQ to update their systems to versions 5.15.16, 5.16.7, 5.17.6 or 5.18.3, which have been patched to call an added validateIsThrowable() method in the BaseDataStreamMarshall class.
All this shows the danger of not thoroughly sanitizing input, especially when the client is untrusted (as it usually is). We generally remember to sanitize form input from browsers and in desktop programs, but it is easy to overlook data deserialization, both when reading from databases and in message-oriented middleware.
The Trend Micro write-up includes a more detailed analysis and explanation as well as a YARA rule which can be used for scanning.
Girnus, Peter, CVE-2023-46604 (Apache ActiveMQ) Exploited to Infect Systems With Cryptominers and Rootkits, research report, 20 November 2023. Available online at https://www.trendmicro.com/en_us/research/23/k/cve-2023-46604-exploited-by-kinsing.html.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
A coalition of over a dozen major Australian corporations have teamed up to share real-time threat intelligence in an attempt to protect their customers from online scams. The new National Cyber Intel Partnership will be a key component of the government's new cybersecurity strategy, which is due to be introduced tomorrow.

A pilot program run by Westpac, Telstra and Woolworths in collaboration with the National Cyber Security Coordinator in the Department of Home Affairs allowed Westpac, for example, to pass threat intel about a phishing email and website to the ACSC for further analysis, before the details were relayed to telco Telstra to block traffic to the site.
The sharing of threat indicators is currently partially automated, using protocols like STIX and TAXII, with the aim of eventual full automation. The participants in the pilot program are expected to present their findings to other partners by the end of the year, and the scheme is expected to expand to block a much larger range of threats including malware, scam websites and lures to privileged insiders such as fake job ads.
The other members of the Partnership include Optus, TPG, National Australia Bank, Commonwealth Bank, ANZ, Qantas, National Broadband Network Co, CyberCX, Palo Alto, the Australian Competition and Consumer Commission, and the Australian Signals Directorate, with more companies expected to join in the future..
With the majority of individual consumers and businesses being customers of the major ISP's and banks, the result should be a significant increase in protection, achieved through a kind of shared immune system: once one of the members detects a threat, the entire immune system will act to block it.
In a related announcement, Minister for Home Affairs and Minister for Cyber Security, Clare O'Neill, is today expected to reveal a scheme which will provide funding for security advice and incident response for small businesses, commencing next year. I confess to taking a less sanguine view of this proposal; announcements of free government money to be distributed through individuals and small businesses tend to quickly attract a crowd of bottom feeders, as demonstrated by previous similar schemes. The result could be no improvement in the capabilities of the lowest hanging fruit, and even a drop in the maturity of those who previously were making significant efforts. Then again, anything is better than nothing. . .
Visentin, Lisa, ‘Stop hackers in their tracks’: Corporate giants muscle up against cyber threats, Sydney Morning Herald, 19 November 2023. Available online at https://www.smh.com.au/politics/federal/stop-hackers-in-their-tracks-corporate-giants-muscle-up-against-cyber-threats-20231117-p5ekva.html.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Researchers from AhnLab Security Emergency response Center (ASEC) report on a campaign which is targeting poorly-secured MySQL database servers via insertion of a malicious User Defined Function into vulnerable Windows systems.
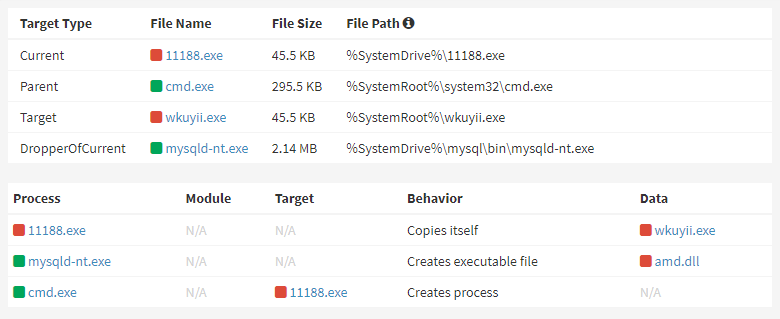
The Ddostf DDoS bot being installed via the MySQL service (Image credit: ASEC)
While the most popular database engine for Windows-based enterprise environments is Microsoft's SQL Server, MySQL is very popular among web developers (especially in packages such as EasyPHP) and small businesses, since it is essentially free and widely deployed on web sites. When initially installed MySQL (and its fork, MariaDB) do not password-protect the root admin account, and it is easy for a developer or inexperienced admin to overlook this step. Worse, the database server may be listening on port 3306 of a network interface, exposing it to remote attack.
The threat actor behind this campaign seems to be scanning for systems with port 3306 open, and then using brute-force or perhaps dictionary attacks to gain access (no admin password would really be an own goal). Unpatched systems may also be exposed through old vulnerabilities. Having gained initial access, the actor then uploads and installs a malicious MySQL User Defined Function (UDF) - a custom function written in C or C++ and compiled down to a dynamic link library (DLL) - perhaps by using a tool like Metasploit, which has a UDF attack payload.
This UDF has the ability to execute commands provided by the threat actor, capturing the output as a file which the actor can review, as well as to download files for subsequent execution. This way, the actor is able to upload and install a bot, christened Ddostf, and install it into the system. Ddostf has been observed in both Linux ELF and Windows PE executable formats; it is easily identifiably by the presence of the unobscured string, ddos.tf, in its binary.
When executed Ddostf first copies itself, under a random name, into the %SystemRoot% directory before registering itself as a Windows service. It then decrypts a string to obtain the URL of its C2 server and connects to it, enumerating and reporting basic information about the infected system. The C2 server responds with a mixture of a command and related data - for example, a command to download a payload, it will provide a URL argument.
While the bot responds to only six commands, it supports a variety of built-in DDoS attacks, including SYN flood, UDP flood, layer 7 HTTP GET and POST floods and others. Apart from commands to download payloads, start and stop DDoS attacks and start/stop transmitting system status information, the bot also has a command to switch to a new DDoS C2 server for a certain period of time, suggesting the developers may be using it to infects systems and then sell DDoS as a service.
The mitigation techniques here are obvious, but unlikely to be adopted by those most affected: after installing MySQL on a Windows machine, set a strong password on the MySQL root account and any PHP or other web server service accounts, and configure development installs to only listen on localhost. The ASEC report includes IoC's, which are also likely to be of limited use.
Sanseo, Ddostf DDoS Bot Malware Attacking MySQL Servers, blog post, 14 November 2023. Available online at https://asec.ahnlab.com/en/58878/.
Upcoming Courses
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
 The threat posed by Rhysida ransomware has been steadily growing over recent months, leading the FBI, CISA and MS-ISAC (Multi-State Information Sharing and Analysis Center) to issue a cybersecurity advisory detailing the tactics and techniques used by its operators, as well as recommended mitigation techniques.
The threat posed by Rhysida ransomware has been steadily growing over recent months, leading the FBI, CISA and MS-ISAC (Multi-State Information Sharing and Analysis Center) to issue a cybersecurity advisory detailing the tactics and techniques used by its operators, as well as recommended mitigation techniques.
The threat actors behind Rhysida are known to target the education, healthcare, manufacturing, tech and government sectors, looking for low-hanging fruit. They also offer their tools and infrastructure in a Ransomeware-as-a-Service model in which they profit-share with those who lease them.
Whoever they are, they typically gain initial access via remote services such as VPN access points which they access using compromised valid credentials; they obtain these via phishing and other attacks from organisations which have not implemented multi-factor authentication. They have also been seen exploiting the Zerologin vulnerability in the Microsoft Netlogon Remote Protocol (which should have been patched back in August 2020 - as I say, low-hanging fruit).
Having established a beachhead on the internal network, the threat actors use living off the land techniques, employing the existing system software, such as PowerShell, the Windows ipconfig, whoami, nltest, and net user, net group and similar commands as well as RDP to pivot to other systems. However, they do install additional tools such as PuTTY, AnyDesk and PowerView, which they use to map the network.
The Rhysida ransomware itself encrypts each file under a 256-bit key using the ChaCha20 algorithm, with the symmetric key in turn protected by 4096-bit RSA and renaming the file to add a .rhysida extension. It simultaneously exfiltrates data, allowing the operators to engage in double extortion: pay the demanded Bitcoin ransom to obtain the decryption key and also prevent the threat actors publishing sensitive exfiltrated data.
Once encryption has been completed, a PowerShell command deletes the ransomware binary and drops a victim-specific PDF file entitled "CriticalBreachDetected", containing a unique code and instructions to contact the operator via a Tor network portal and make payment. The text of the note makes a useful IoC, since it is also embedded in the ransomware binary, allowing easy detection. (I should say, "was also embedded", since it is easily obscured, e.g. by an XOR algorithm, and the operators have almost certainly done this by now).
A long list of suggested mitigations start with the obvious: deploying phishing-resistant multi-factor authentication, removing user access to PowerShell and other command-line tools, restricting the use of RDP and other remote desktop services, application allowlisting, proactive patching, etc. It also advises validation of controls using pen-testing techniques aligned with the specific MITRE ATT&CK techniques identified. The advisory also lists IoC's, and they are downloadable in STIX XML and JSON formats.
CISA, #StopRansomware: Rhysida Ransomware, cybersecurity advisory, 15 November 2023. Available online at https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-319a.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
The Australian Signals Directorate has released its Cyber Threat Report for 2022-2023. While I haven't had a chance to read the 80-page report, there are a few standout points:
- The top3 cybercrimes reported by businesses are:
- Email compromise
- Business email compromise fraud
- Online banking fraud
- Self-reported losses due to BEC fraud totalled almost $A80 million, with an average loss of over $A39,000 per incident
- Ransomware comprised over 10 percent of all incidents, with the highest-reporting sectors, accounting for roughly one-third of reports being:
- Professional, scientific and technical services
- Retail
- Manufacturing
- The average self-reported cost of cybercrume to businesses increased by 14%:
- $46,000 for small business
- $97,200 for medium business
- $71,600 for large business
 State-sponsored actors focused on critical infrastructure, with their objectives being data theft and disruption of business. It is noticeable that cyber perations are increasingly the preferred vector for state actors to conduct espionage and foreign interference. ASD and international partners called out the Russian FSB for its use of the Snake malware for cyber-espionage, and also highlighted activity associated with a People’s Republic of
State-sponsored actors focused on critical infrastructure, with their objectives being data theft and disruption of business. It is noticeable that cyber perations are increasingly the preferred vector for state actors to conduct espionage and foreign interference. ASD and international partners called out the Russian FSB for its use of the Snake malware for cyber-espionage, and also highlighted activity associated with a People’s Republic of
China state-sponsored cyber actor that used ‘living-off-the-land’ techniques to compromise critical
infrastructure organisations.
The connection of operational technology and industrial control systems to the Internet via enterprise networks has provided increased opportunities for threat actors to attack them; ASD responded to 143 incidents related to critical infrastructure.
Proactive patching is increasingly important (today is Windows PatchDay - is your computer fully patched?) One in 5 critical vulnerabilities was exploited within 48 hours, despite patching or mitigation advice being available. Malicious cyber actors used these critical flaws to cause significant incidents and compromise networks, aided by inadequate patching.
Online scams and cybercrime continue to increase: individuals made almost 94,000 reports of cybercrime - an increase of 23% over the previous year. The top four cybercrimes reported by individuals are:
- Identity fraud
- Online banking fraud
- Online shopping fraud
- Investment fraud
The Australian Competition and Consumer Commission’s Targeting Scams report revealed Australians lost over $3 billion to scams in 2022. This is an 80 per cent increase on total losses recorded in 2021.
In short, we cybersecurity professionals are far from being out of a job.
Uncredited, ASD Cyber Threat Report 2022-2023, report, 14 November 2023. Available online at https://www.cyber.gov.au/about-us/reports-and-statistics/asd-cyber-threat-report-july-2022-june-2023.
Upcoming Courses
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 November 2023
- SE221 CISSP Fast Track Review, Sydney, 4 - 8 December 2023
- SE221 CISSP Fast Track Review, Sydney, 11 - 15 March 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 13 - 17 May 2024
- SE221 CISSP Fast Track Review, Virtual/Online, 17 - 21 June 2024
- SE221 CISSP Fast Track Review, Sydney, 22 - 26 July 2024
About this Blog
I produce this blog while updating the course notes for various courses. Links within a story mostly lead to further details in those course notes, and will only be accessible if you are enrolled in the corresponding course. This is a shallow ploy to encourage ongoing study by our students. However, each item ends with a link to the original source.
These blog posts are collected at https://www.lesbell.com.au/blog/index.php?user=3. If you would prefer an RSS feed for your reader, the feed can be found at https://www.lesbell.com.au/rss/file.php/1/dd977d83ae51998b0b79799c822ac0a1/blog/user/3/rss.xml.
![]()
 Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.
Copyright to linked articles is held by their individual authors or publishers. Our commentary is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License and is labeled TLP:CLEAR.